We are excited to introduce a series of technical analysis blogs focusing on various CVEs (Common Vulnerabilities and Exposures) that can be identified and remediated with our advanced threat detection technologies. All research is done by graduate students who have participated in the OPSWAT Cybersecurity Fellowship program, which launched in December 2023.

In this blog, we will explain the Rockwell Micrologix CVE-2017-14469 and how organizations can defend against CVE- 2017-14469 exploitation attacks.
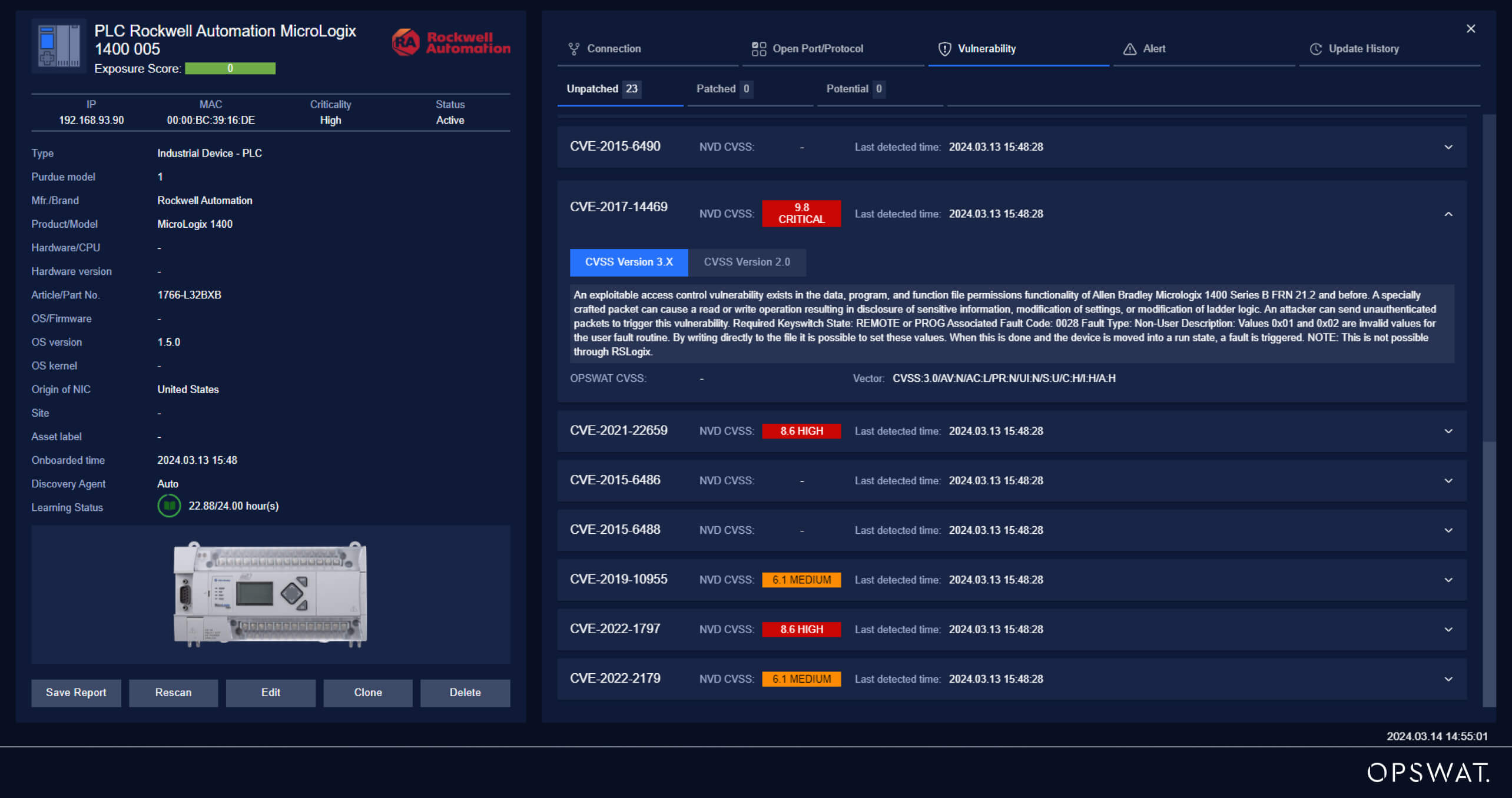
Rockwell Automation MicroLogix 1400 Controller
A PLC (Programmable Logic Controller) is a computer designed specifically for controlling industrial manufacturing processes. It is used in critical infrastructure sectors, such as assembly lines, machine monitoring, process control, etc. The Rockwell Automation MicroLogix 1400 Controller is a modular and extensible PLC featuring a high I/O count, fast high-speed counter, and enhanced network support, which makes it suitable for a wide range of applications.

CVE-2017-14469
A vulnerability in the Rockwell Automation MicroLogix 1400 Series B FRN 21.2 and earlier versions allows an attacker to read and write/overwrite sensitive data on the device. An unauthenticated, specially crafted packet containing a command would lead to the modification of the user-defined fault routine number, leading to an unexpected halt in the device's execution.
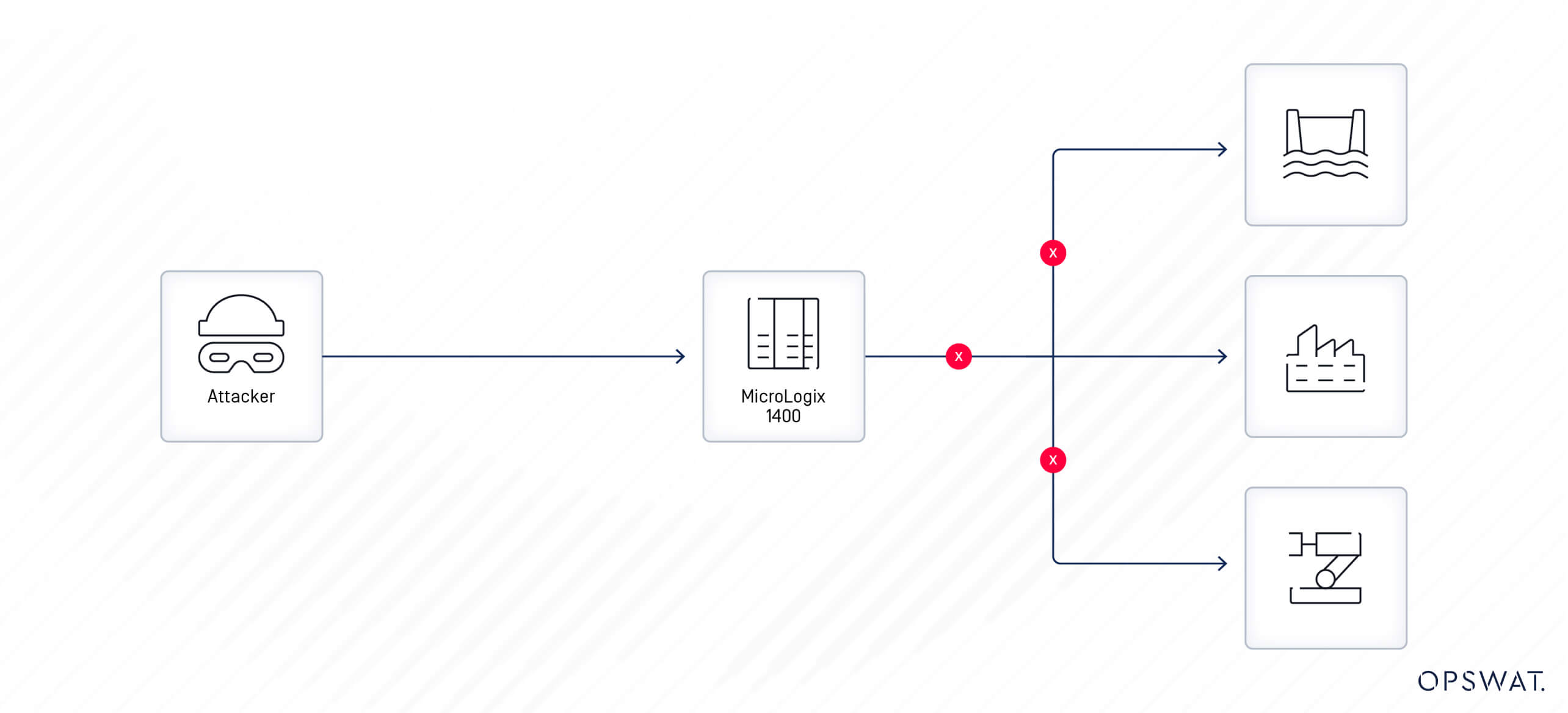
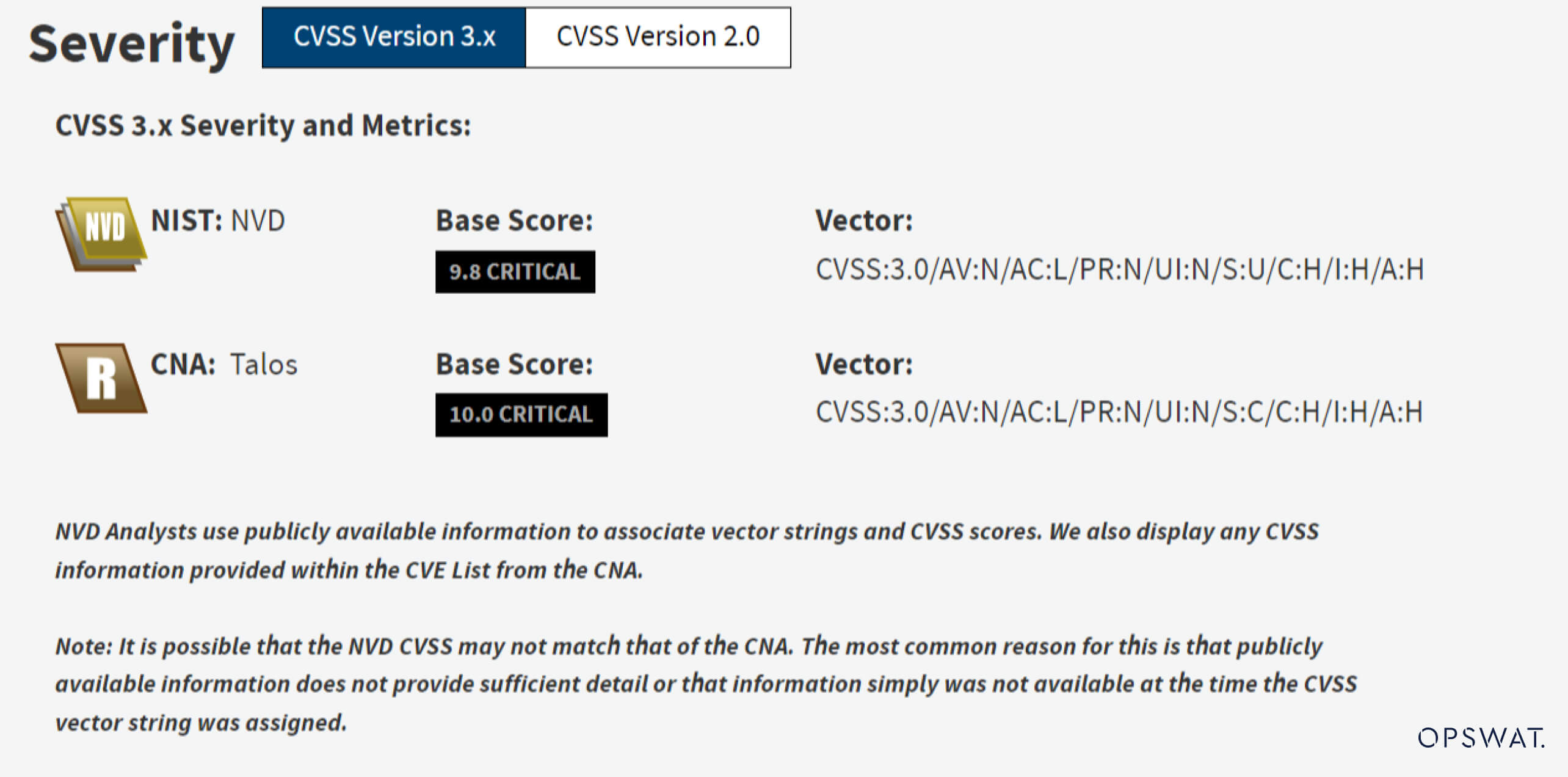
The National Vulnerability Database (NVD) has classified this vulnerability as “Critical” with a maximum CVSS (Common Vulnerability Scoring System) score. Its impact can significantly affect a device’s confidentiality, integrity, and availability without requiring any additional authentications. The system's availability is crucial, especially in critical infrastructure systems, where any disruption or downtime can lead to massive financial losses or even physical damage. This CVE can lead to a halt in the PLC functions by triggering a ‘system fault’ within the controller, thus posing a risk of disrupting critical infrastructure systems.
Vulnerability Analysis
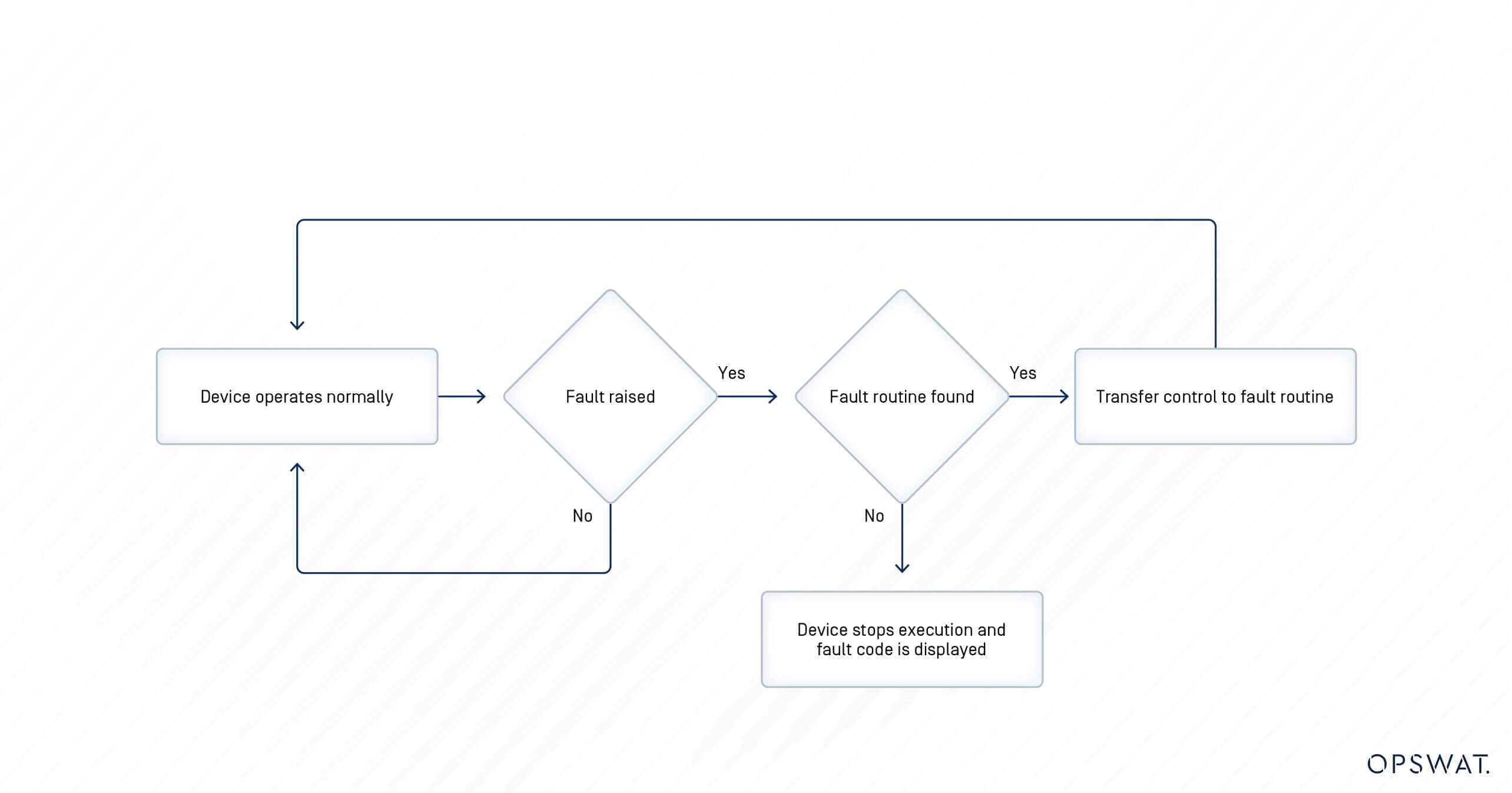
The concept of a fault closely resembles that of an exception in programming. When a fault occurs, the execution of the instruction is halted, leading the device into a fault state. Faults can be categorized into two types: user faults and non-user faults.
There are two mechanisms for clearing faults: by automatically clearing by cycling power to the controller, or by manually clearing with a user fault routine, which is a procedure that can be set to automatically execute in response to a user fault. The CVE-2017-14469 relates to the second mechanism. To prevent the system from shutting down or halting execution unexpectedly by a user fault, a user fault routine is defined to handle assigned faults based on their fault numbers and is executed when the corresponding fault occurs. If there is no routine to handle the fault, the device stops execution and displays the fault number. The value for the user fault routine is set at 0x00 when the device operates normally, and it should only be configured within the range of 0x03 to 0xFF for fault handling.
There are three mode switch positions in Rockwell Automation MicroLogix 1400: PROGRAM, REMOTE, and RUN. Both PROGRAM and REMOTE modes permit program downloads to the device, while also accepting and handling incoming requests. However, in RUN mode, the device only accepts restricted requests. In the context of this vulnerability, exploitation is not possible if the device is in RUN mode.
- Idle mode, used for downloading and editing programs
- Responds to messages on communication port
- Halted execution and no output
- Allows a session from software to control the device
- Responds to messages on communication port
- Normal execution and output
The device communicates via CIP (Common Industrial Protocol) with PCCC extension. The CIP protocol is built on top of Ethernet/IP (Industrial Protocol). The structure of a packet is shown in the figure below:
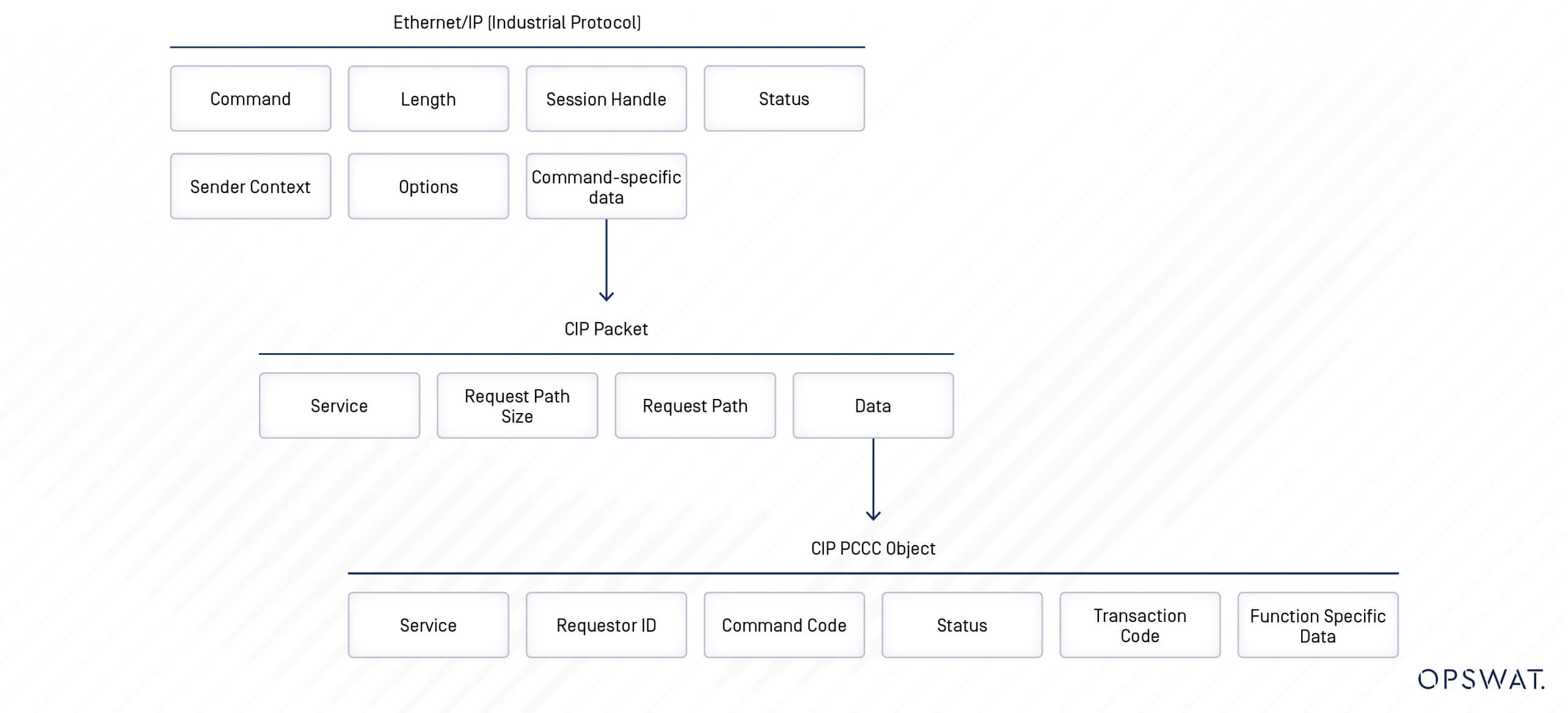
As can be seen from the image above, there is no field designated for authentication. This poses a significant challenge, as the device lacks the ability to differentiate between an attacker's requests and normal traffic from a user.
Typically, an operator can monitor and update the configuration of the device via control software. To communicate with the device, the Control Software sends a corresponding request with a protected typed logical write or read command, filling in the CIP PCCC Object. In the CIP PCCC protocol format, a command is identified by its command code and function code.
Command Code | Function Code | Description |
| 0x0F | 0x80 | Change Mode |
| 0x0F | 0xAA | Protected typed logical write with three address fields |
| 0x0F | 0xA2 | Protected typed logical read with three address fields |
The protected typed logical write command is used to write to sensitive files, such as the Status file, Bit file, Counter file, and other configurations of the device.
The device uses three address fields in the CIP packet to identify the location for reading and writing: file type, file number, and element numbers. Below are some example values to identify the configuration file locations that will be affected by the command:
File Type | File Number | Element Numbers | Description |
| 0x84 | 0x02 | 0x1d | Status file – User Fault Routine number |
| 0x84 | 0x02 | 0x06 | Status file – Major Error Code |
| 0x84 | 0x02 | 0x05 | Status file – Major Error Code |
However, there is a lack of input validation when the device handles the request; the data sent in the write command is not validated and allows being set to any invalid values.
The vulnerability is caused by two main reasons. Firstly, the device cannot authenticate incoming requests, enabling an attacker to send an unauthenticated request to modify sensitive settings. Secondly, the device incorrectly validates incoming data, leading to the settings being changed to an invalid state.
To successfully exploit the vulnerability, an attacker sends a malicious request, abusing the protected typed logical write command to overwrite the fault routine number in the status file with an invalid value, such as 0x01 or 0x02. When the fault routine number is overwritten with an invalid value and the device switches into a RUN mode through another CIP Packet, it triggers a fault and stops the execution.
Vulnerability Exploitation
The attack could be divided into 4 steps.
- Establish a connection to the device over Ethernet/IP to obtain the session handle.
- Send the malicious request to overwrite the fault routine number.
- Craft a malicious CIP packet to switch the PLC back to Run mode to trigger the fault.
- The device encounters a fault and stops execution.

To communicate with the device, an attacker must initiate a connection by registering a session with the device to obtain the session handle and use it for ongoing communication. The following code demonstrates a standard session registration request:
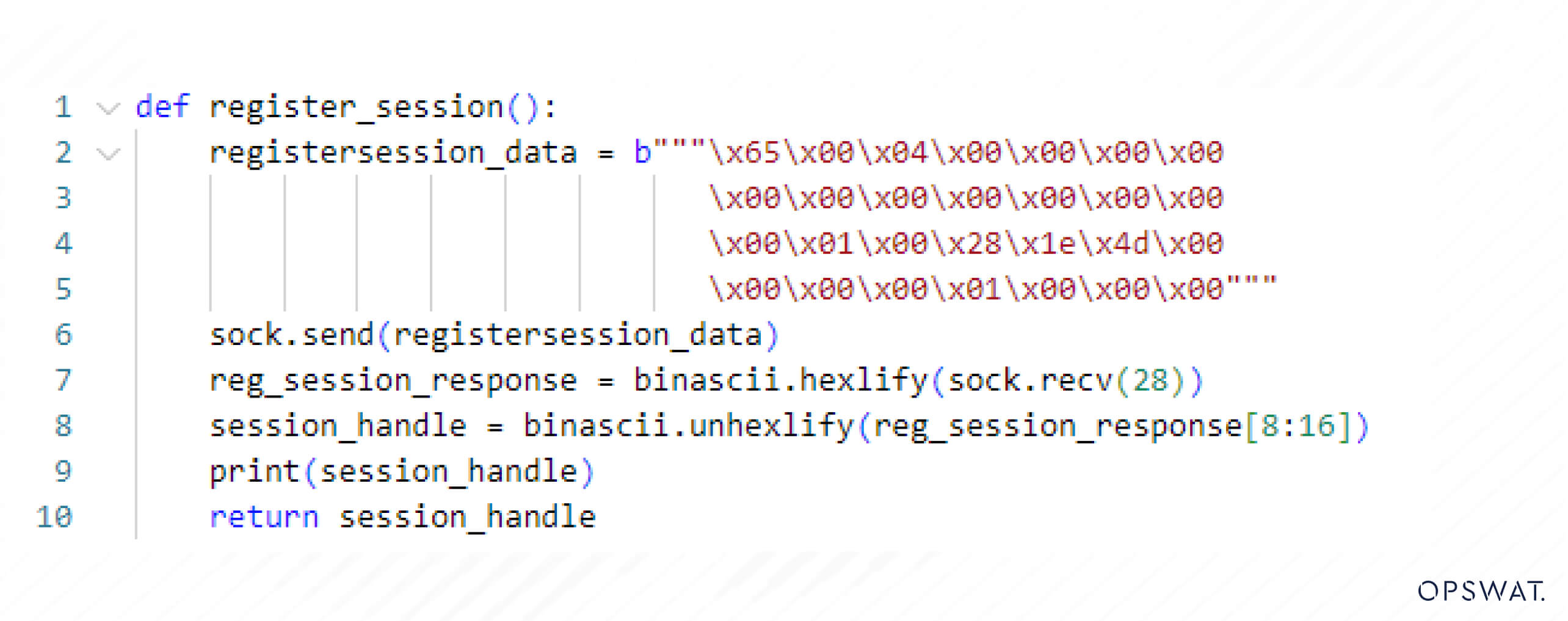
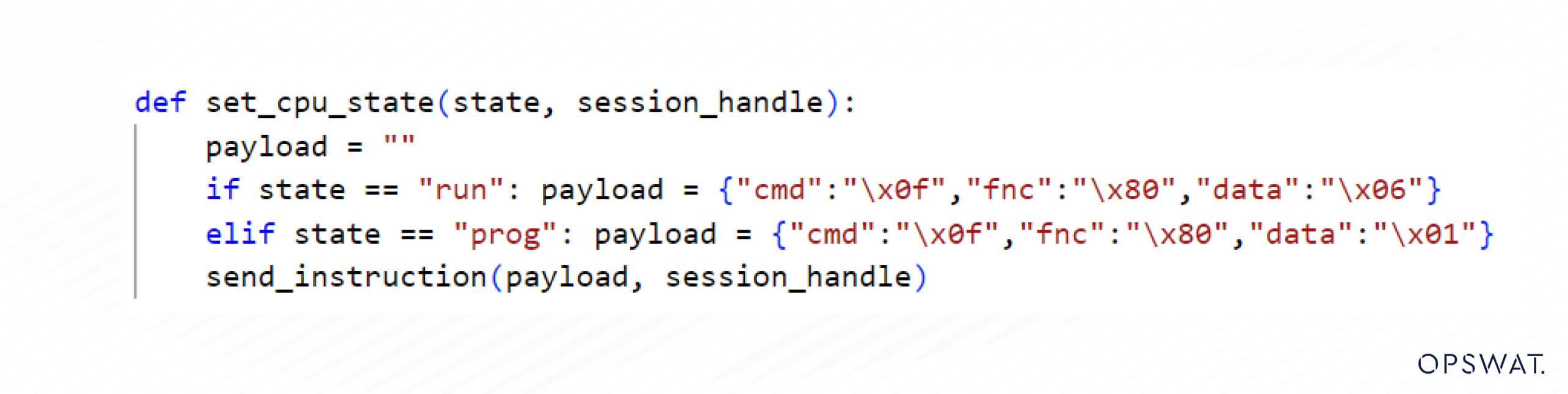
Subsequently, an attacker crafts a request using the previously obtained session handle and includes a payload with a protected typed logical write command to overwrite the fault routine number, encapsulated into a CIP packet.

In the last step, another CIP packet is sent to switch the device to run mode and trigger the fault.
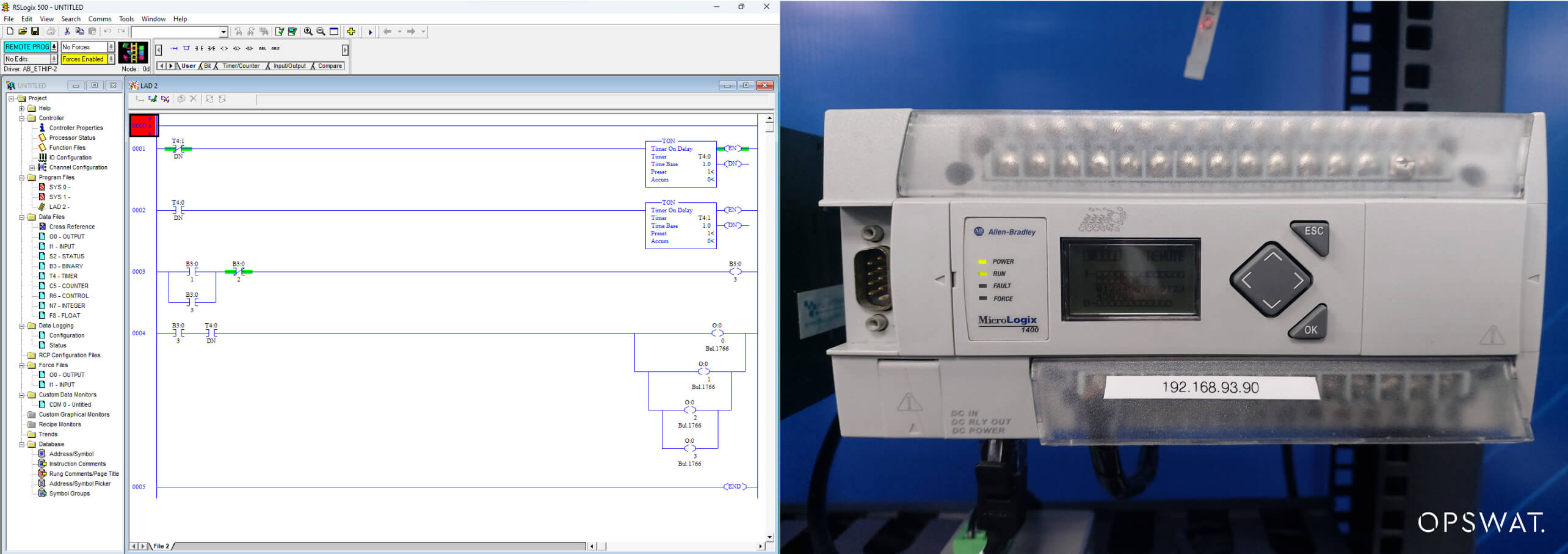
As depicted in the image, the execution of the PLC is halted, and the vulnerability is successfully exploited.
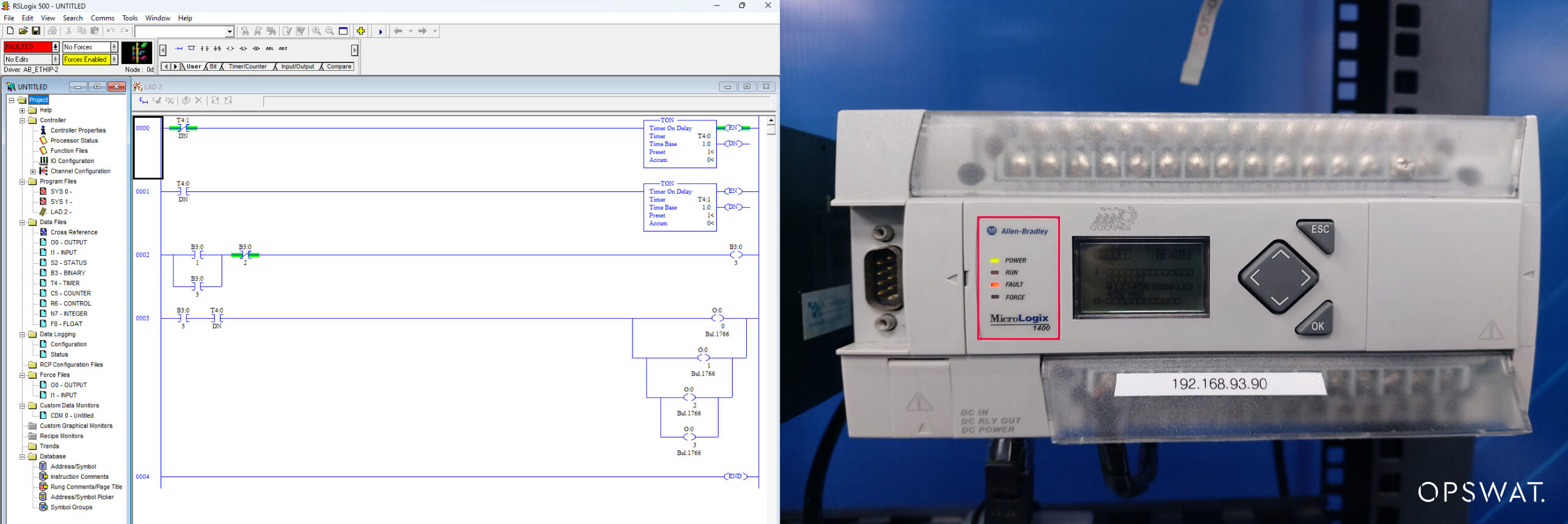
Remediation
OPSWAT’s products for ICS security are designed to withstand these kinds of attacks. MetaDefender OT Security is an AI-powered threat detection and intelligence tool that detects any abnormal requests from attackers, enabling administrators to identify potential threats.
MetaDefender OT Security has the following capabilities to improve the security posture of OT environments:
- Rapidly discovers and builds asset inventory with Smart Asset Profiling
- Actively and passively monitors threats and anomalies
- Remote patch management with centralized, auto-patching capabilities
- Structured and streamlined risk alert workflow managed by a comprehensive & customizable dashboard
- Global, regional and industry regulatory compliance reporting
Additionally, MetaDefender OT Security can also be integrated with MetaDefender Industrial Firewall to prevent malicious requests from impacting devices as detected by OT Security. The MetaDefender Industrial Firewall is the last line of defense protecting mission-critical PLCs, VFDs, RTUs and other industrial assets. It applies highly granular device access policies and enforces device access zones, ensuring no unauthorized access or changes can impact the critical hardware.
The two together create a seamless IDPS (intrusion detection and prevention system) that effectively detects and prevents any anomalous network connections, requests, communications, etc. from affecting the network.
MetaDefender OT Security provides crucial protection for critical infrastructure through its asset visibility and robust threat detection. Beyond its technological prowess, OPSWAT offers exciting career opportunities for individuals passionate about cybersecurity. Join us in shaping the future of security and protecting what matters most. Explore diverse roles and impactful projects at OPSWAT, where your expertise can make a tangible difference. Together, let's safeguard the world's most vital systems.

