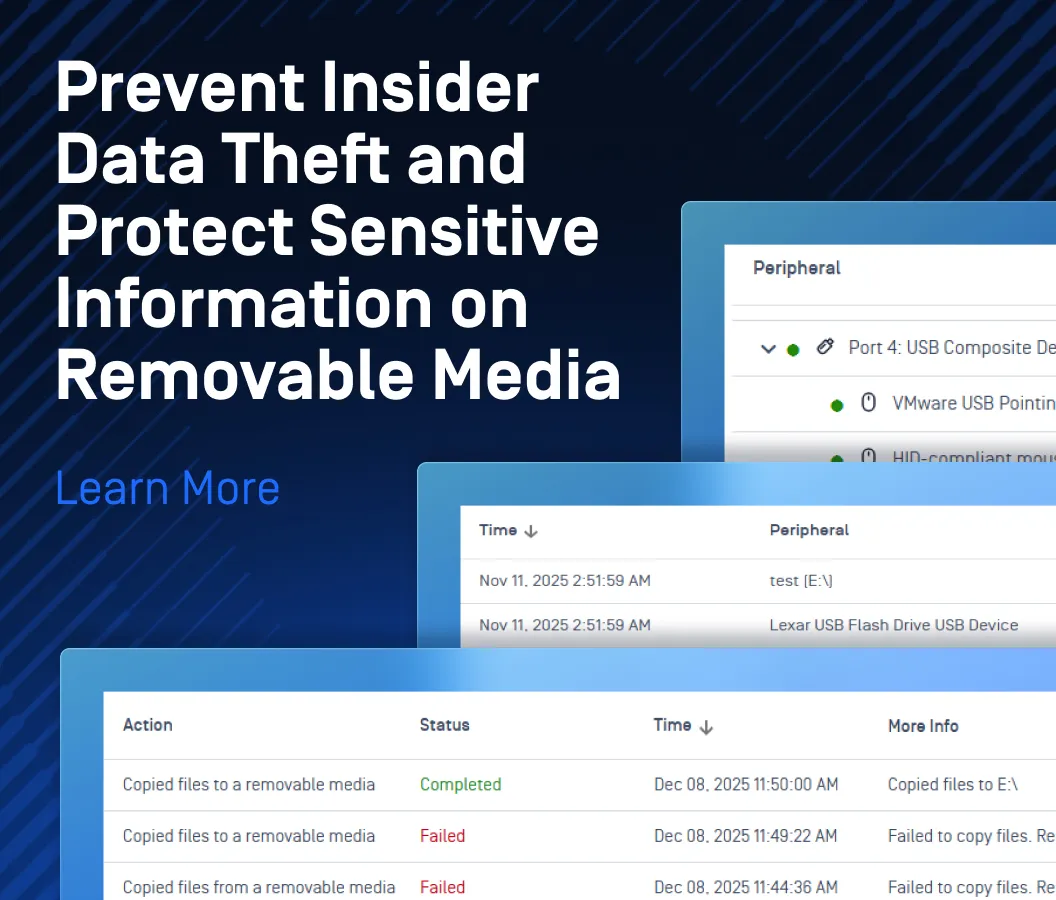
A recent wave of ransomware attacks is powered by a two-year-old VMWare vulnerability. The attacks affected thousands of organizations around the world, especially in Europe and North America.
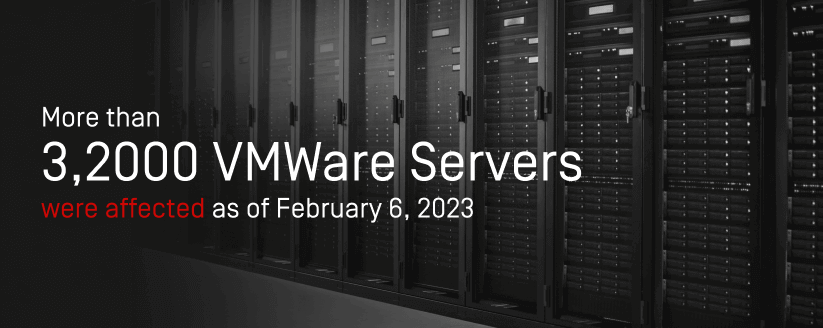
Reports are coming in from around the world about a new ransomware called EXSIArgs. By exploiting a two-year-old vulnerability in the EXSI hypervisor software, bad actors are able to delete important files within the system of infected workstations. More than 3,200 VMWare servers were affected as of February 6, 2023.
The incident drew immediate responses from authorities in affected areas. A spokesperson for the American Cybersecurity and Infrastructure Security Agency, also known as CISA, announced that the organization is aware of the issue. CISA is working extensively with private and public partners to assess the impacts of the attacks and provide assistance where necessary. Italy’s National Cybersecurity Agency has also issued warnings to organizations, urging them to take immediate action.
How It Happened
This attack began with a two-year-old vulnerability in VMWare EXSI servers. EXSI is a technology that the company employs to host and coordinate multiple machines on a single server. The vulnerability in question is related to the OpenSLP Service, which is available on older versions of EXSI. If malicious actors exploit this vulnerability, they could execute code that deletes files on your system.
This vulnerability is not an unknown one, however. It was disclosed in 2021 and has been tracked as CVE-2021-21974. The company recommended that organizations should start updating their vSphere components to the latest versions, as they contain the patch for this vulnerability.
Vulnerabilities: The Hidden Daggers
Malicious actors have been using software vulnerabilities for a long time, with some particularly notorious cases such as CVE-2018-8174, also known as Double Kill, and the ProxyLogon exploit. Because vulnerabilities can be points of entry for malware, experts recommend that they should be patched as soon as an update is available.
Governments and other regulations regarding vulnerabilities are becoming more prevalent and stricter. For example, in October of 2022, the aforementioned CISA issued a Binding Operational Directive (BOD 23-01) for improving asset visibility and vulnerability detection on Federal networks. By April 3, 2023, all Federal agencies are required to comply with the need to perform automated asset discovery every 7 days and to initiate vulnerability enumeration across all discovered assets (including endpoints such as laptops) every 14 days.
While essential for all organizations and now required for Federal Agencies, it doesn’t mean that this is an easy task. Organizations can have as many as thousands of devices that need to be updated at a time, and it is also a colossal effort to ensure every single device is updated. Remember, just one infected device can set off a chain of infection that causes a massive data breach.
How SDP and Zero-Trust Can Protect Your Network
OPSWAT’s MetaDefender Access Zero-Trust Access Platform is a comprehensive solution that delivers security compliance, visibility, and control to every device and user accessing organizational resources.

Compliance
MetaDefender Access conducts the most comprehensive device posture check in the industry (15 categories of checks), including executing a risk and vulnerability evaluation. It detects over 35,000 CVEs and can automatically patch more than 150 third party applications.
Access Control
After MetaDefender Access ensures that the endpoint device is both compliant and secure, users are authorized to access the network through an integrated IAM (identity authorization management) solution. They will then be given access via a Software Defined Perimeter (SDP) to organizational resources based on a least-privilege policy.

Visibility
The protection goes even deeper. With MetaDefender Access, in the case of the EXSI software, hackers would never be able to connect to it in the first place as resources and applications behind the SDP are invisible to all devices; thus, hackers would never know they were there. Furthermore, only trusted devices that have gone through rigorous compliance and security checks as described above can access resources via SDP.
Organizations don’t have to be defenseless when malicious actors exploit a vulnerability. By regularly patching their applications and endpoints, organizations can minimize the risk of attacks, preventing costly ransomware incidents. Solutions such as OPSWAT MetaDefender Access Zero-Trust Access platform empower organizations to speed up the process in a compliant, secure, and cost-effective manner.
Read more about our MetaDefender Access Zero-Trust Access platform.