I think this development was inevitable, but that doesn't make it any less disturbing. Potentially unwanted applications (PUAs) are now borrowing techniques from malware developers.
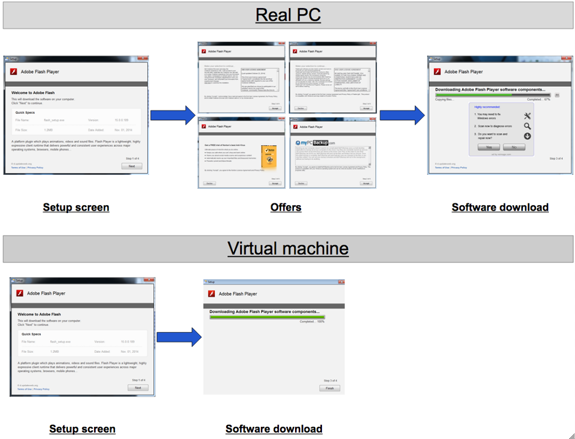
Malwarebytes published an analysis of a third party downloader/installer for Adobe Flash Player. This installer pushes multiple offers to the user, the first of which cannot be declined. By the end of the installer, the user may end up with up to four unwanted programs in addition to the one they actually wanted to download. This innocent attempt to download legal software contrasts quite sharply to users who acquire PUAs through engaging in risky behavior like downloading pirated movies. An unsuspecting user who is just trying to download Adobe Flash Player can easily be fooled by this installer, especially because they had no reason to suspect these unwanted offers would be presented.
The bundling of unwanted applications along with the desired software is a common technique among download management websites, but up until this point they aren't borrowing any techniques from malware developers. So what makes this particular bundler so special? Run the same installer again, this time in a Virtual Machine (VM) instead of a physical machine, and magically all of the product offers go away! The installer behaves quite well when in a virtual environment, skipping right to the Adobe Flash Player install without any of the annoying offers for PUAs. Malwarebytes researchers reverse-engineered the installer and confirmed the presence of the VM detection logic; the same installer, run in a different environment, presents no potentially harmful unwanted applications.
Adam Kujawa, Head of Malware Intelligence at Malwarebytes recently stated, "the use of VM aware code is not a new technique when it comes to Malware. Malware authors are constantly trying to "one-up" researchers and our many methods of identification, classification and detection."
Image Source: Malwarebytes
As noted in the Malwarebytes analysis, it's possible that this logic was added to aid development or prevent skewed installation metrics. But as Kujawa notes, it is more likely that this installer wants to avoid PUA classification when being tested by researchers. This type of 'sandbox aware' behavior is a growing trend in malware. It's part of cat-and-mouse game, or more aptly, an arms war. With techniques ranging from changing code behavior, to stalling code execution and even outright deception by invoking different, but still malicious, behavior while in a sandbox — it's all a challenge for cybersecurity firms to keep up. In this case, the evasive behavior is relatively straightforward and easily caught — but only if someone knows what to look for.
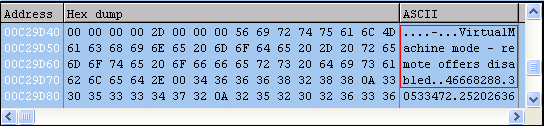
Code defining behavior for a virtual environment.
Image Source: Malwarebytes
Kujawa also commented on his opinion on the future of PUP detection stating, "I think we are very likely that we see PUPs follow suit by moving beyond just VM detection to detecting those security products that look for PUPs (like those made by OPSWAT and Malwarebytes) running in the background. Upon detection of these products, the software is going to change its behavior so it doesn't get caught or doesn't run at all."
OPSWAT actively works on PUA and PUP detection with several of our products. Metascan® and Metascan Online detect PUA and PUP through static code analysis with multiple anti-malware engines. The OESIS Framework's Detection Module reports PUAs according to our analysts' findings (these tags are customizable by the SDK implementer for flexibility.) The OESIS analyst team's PUA identification strategy is available for download.
For those whose system may already be burdened with unwanted applications, Gears has just added AppRemover functionality for easily uninstalling toolbars and peer to peer file sharing software. It can also be used for uninstalling redundant or difficult to remove security software.