Security researchers have once again demonstrated why Microsoft acknowledges that “unexpected macros can pose a significant security risk.” In a recent blog post, security researchers explain how attackers are using macros to download and execute ZLoader, a malicious banking Trojan, without any malicious code present in the initial file.
The anatomy of the attack begins with an innocuous Microsoft Word document, which leverages macros to download a Microsoft Excel document. This subsequently creates a new macro in the XLS file and updates a registry policy to Disable Excel Macro Warning. Consequently, the Excel file can execute its malicious macro to download ZLoader without any warning.
Like so many other attacks, the initial Microsoft Word document is delivered as a phishing email. However, this particular attack chain is novel because the initial macro is unlikely to be detected by any anti-virus or anti-malware engine. Of course, many organizations disable macros as a default policy, but this initial Microsoft Word document is formatted in a way that urges users to “Enable Editing” and “Enable Content.”
This combination of social engineering and technical exploit is what makes this sort of attack so effective.
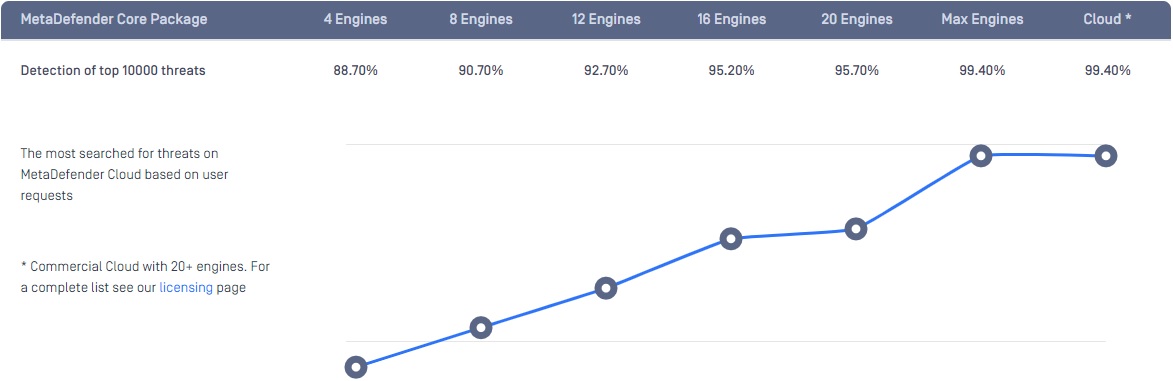
Even on a good day, anti-virus and anti-malware engines struggle to keep pace with the volume of new threats and are extremely vulnerable to zero-day threats. OPSWAT research reveals that it takes more than 30 anti-virus and anti-malware engines to reach detection rates greater than 99 percent, thus multiscanning solutions can significantly reduce dwell times for latent malware. Even traditional sandboxes can be evaded as malware becomes increasingly sophisticated. Novel threats, such as this ZLoader macro, are notably effective at avoiding detection.
Trust No File
The zero-trust security model has become an increasingly popular method of securing users and devices with its wisdom to “trust no one,” yet this same wisdom is rarely extended to file security. It should be apparent by now, as anti-virus and anti-malware engines continue to struggle with their detection rates, that organizations should also “trust no file.”
If an organization assumes that all files are malicious, then it can inspect, and then sanitize its data with Content Disarm and Reconstruction (CDR) technology.
First, CDR decomposes all files into discrete components, where all elements are identified. Typically high risk macros are removed, thereby eliminating any potentially malicious content. Next, CDR quickly and securely reconstructs the file from the sanitized components, preserving its metadata and file characteristics. Additionally, customers have the ability to allowlist specific macros they want to retain. The reconstructed files, with their file structure integrity intact, are delivered to the end users without the loss of usability. .
Deep CDR sanitizes and reconstructs more than 100 common file types, and verifies more than 4,500 file types. On average, Deep CDR is 30 times faster than most dynamic analysis technologies and can block malware designed to evade traditional sandbox environments. Deep CDR also integrates with OPSWAT Multiscanning, proactive data loss prevention (DLP), and file-based vulnerability assessment technologies.
It doesn’t matter if organizations scan for malicious files when attackers can evade detection with macros. It doesn’t matter if Microsoft warns users about the security risk of macros when attackers can disable those warnings. It doesn’t matter if organizations disable macros when attackers can leverage savvy social engineering to get users to re-enable the macros.
What really matters is embracing the mentality of “trust no file” and having the policies and controls in place to realize this philosophy.
OPSWAT can help. Contact one of our cybersecurity experts today to learn more about how to sanitize data with Deep CDR.

