Industry Context & Threat Landscape
According to ENISA’s 2024 Report on the State of Cybersecurity in the Union, the EU experienced a sustained rise in cyber incidents throughout 2023 and 2024, with ransomware and DDoS (distributed denial-of-service) attacks comprising over half of the reported events.
These attacks often targeted infrastructure deemed essential under the NIS2 Directive, such as telecom operators, whose disruption could destabilize both national and cross-border services.
The World Economic Forum reports that the complexity of cybersecurity is rising due to intersecting risks, including:
- Fragmented global regulatory requirements
- Increasing supply chain interdependencies
- AI-driven cybercrime, including phishing and deepfakes
The reliance on real-time data exchange, secure partner integration, and uninterrupted services creates a persistent threat landscape. Telecommunications companies require more than generic file-handling tools to provide uninterrupted service and secure collaboration with external partners.
This telecom company recognized the need to govern file transfers across segmented environments with precision. For them, compliance obligations, operational variance, and the threat of file-borne malware rendered traditional, one-size-fits-all models insufficient.
Reducing Security & Compliance Risks with Secure File Transfers
The organization’s core operations depend heavily on the timely, policy-compliant movement of files between internal systems, employee devices, and external business partners. These file transfers occur across environments with varying security levels, ranging from third-party user portals to protected administrative workstations.
A key operational requirement was to facilitate bidirectional file flows between segmented low-security and high-security environments, without compromising threat prevention, auditability, or regulatory compliance.
3 Main needs that prompted the decision:
Ensure policy-compliant transfers
Files needed to be transferred between low- and high-security environments given they satisfy preconfigured security and routing conditions
Manage data flows across segmented networks
Transfers had to support both low-to-high (external to internal) and high-to-low (internal to external) directions
Support varied operational use cases
Different functions required distinct file transfer workflows with specific policy controls and routing conditions
As a result, the organization sought a new solution that could apply filtering rules, ensure consistent scanning at every zone boundary, and simplify control over metadata-driven decisions.
Compliance requirements such as NIS2, internal data governance policies, and telecom-specific operational frameworks demanded full audit trails, granular access control, and zero tolerance for unverified content.
By embedding security controls into the file transfer process, the organization aimed to prevent the entry of malware and zero-day threats, reduce manual interventions, and avoid accidental data disclosures.
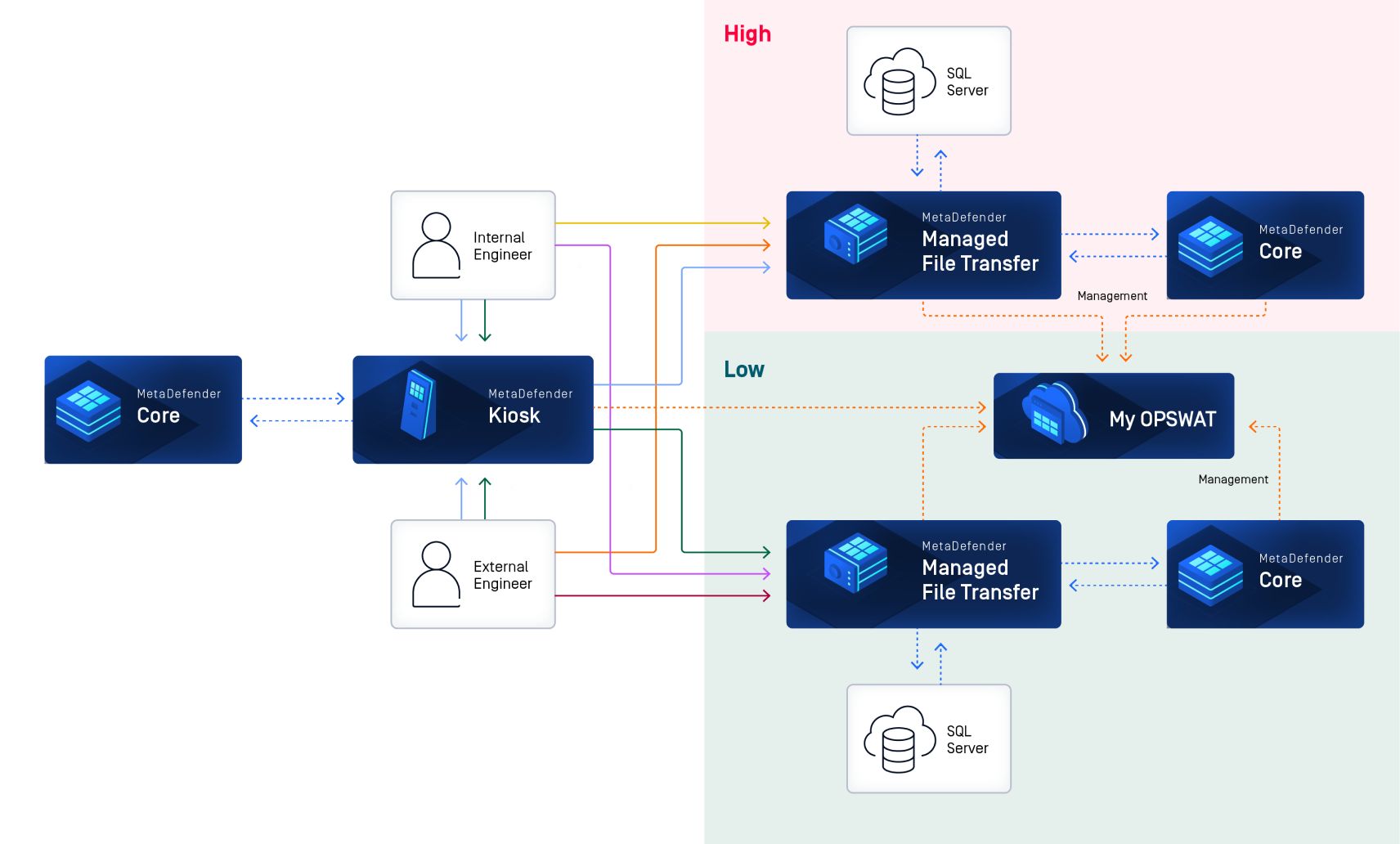
Policy-Driven File Transfer Control Across Networks
To address these operational and security demands, the organization selected OPSWAT’s MetaDefender Managed File Transfer (MFT) with MetaDefender Core as the foundation for a controlled, security-first file transfer framework.
The deployment introduced a policy-driven setup centered around a key governance feature: the Transfer Policy Framework for MFT-to-MFT transfers. This framework ensures that files are synchronized between low-security and high-security environments only if they meet predefined security and metadata-based criteria.
It is important to note that the Transfer Policy Framework differs from transfer conditions. While the framework represents the set of policies that determines whether a file is eligible for transfer, transfer conditions govern how the file is routed once eligibility is confirmed. Each destination MFT instance can apply its own conditions, allowing for customized file routing under a unified governance structure.

5 Key Components
1. Policy-Based File Transfer Framework
Administrators are provided with an intuitive rule builder that supports ‘AND’/‘OR’ logic and grouped condition sets (policies), simplifying the creation of complex rules without scripting.
2. Logic-based Filtering Policies
Customizable rules determine file movement based on filename, file size, type, group membership, Active Directory, Entra ID group attributes, and content-based dynamic routing. This ensures files are sent only to appropriate destination systems.
3. Metadata-Based File Transfer Conditions
Routing decisions are made using content analysis results. For example, after analyzing a file by identifying and classifying unstructured text into predefined categories using AI, a file labeled with the property “Priority=High” would only be transferred to high-security destinations if explicitly allowed by the applicable transfer policy.
4. Integrated Scanning with MetaDefender Core
Every file is passed through 30+ antivirus engines, CDR technology, and optional sandbox analysis. This ensures that only sanitized and trusted content can move into or out of segmented zones.
5. Centralized Audit and Visibility
All transfer activity is logged, searchable, and mapped to user identity, supporting both internal audit requirements and external compliance obligations.
This policy framework transforms traditional file transfer into a conditional, security-enforced process that responds dynamically to each file’s context.
Cutting-Edge Security Against Emerging Threats
Faced with the dual pressure of operational complexity and an evolving threat landscape, the organization decided to shift from reactive controls to a zero-trust, security-first approach to file transfer.
The deployment of MetaDefender Managed File Transfer (MFT), coupled with MetaDefender Core, positioned the organization to meet its evolving security and compliance requirements without introducing friction into business-critical workflows.
Rather than relying on manual routing, email-based exchange, or general-purpose file sharing platforms, the telecom provider now performs its file transfers within a framework that prioritizes prevention, precision, and auditability.
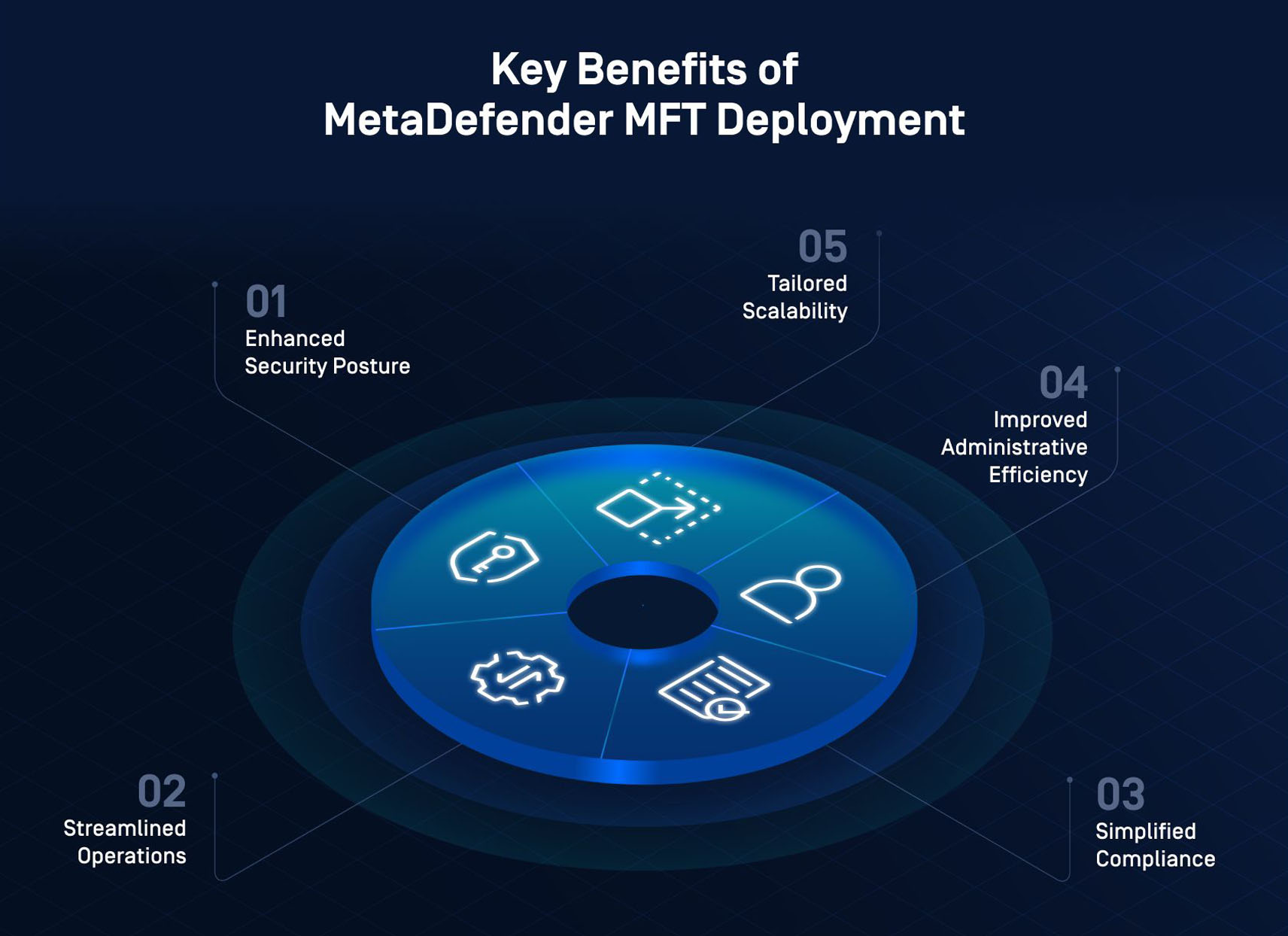
5 Key Outcomes
1. Enhanced Security Posture
Files are transferred only after passing a strict multi-stage security check involving CDR, DLP enforcement, and metadata-based validation. This reduces the risk of malware propagation, accidental disclosures, and policy violations.
2. Streamlined Operations
Transfer workflows are dynamically routed using embedded tags and group membership, eliminating the need for batch transfers, directory polling, or manual processing. Granular rules allow for real-time decision-making without additional overhead for IT teams.
3. Simplified Compliance
File transfers are governed by policies aligned with sectoral frameworks, including NIS2 and internal security standards. Full audit trails, encryption, and role-based approvals ensure that each transfer meets both operational and legal requirements.
4. Improved Administrative Efficiency
The introduction of the Transfer Policy Framework significantly reduced the workload of system administrators. Logic-based rules and tagging remove the need to maintain scripted workflows or manage redundant destination rules across multiple MFT instances.
5. Tailored Scalability
Each MFT destination now operates with its own set of transfer conditions, enabling the organization to adapt the infrastructure as new business units or partner workflows are onboarded. This flexibility allows for growth without restructuring.
Moving File Security into Telecom Operations
As threat actors adapt and regulatory scrutiny intensifies, telecommunications providers face mounting pressure to modernize file handling processes without compromising performance or trust. This organization’s deployment of MetaDefender Managed File Transfer (MFT) represents a strategic move toward security-first file governance.
Instead of simply moving data across networks, the system now evaluates, controls, and documents each transaction according to defined governance rules. This approach ensures that each file movement, regardless of source, direction, or destination, is aligned with threat prevention measures, data protection mandates, and operational integrity.
Critical systems must be protected against zero-day threats and malicious software. Integrated, policy-driven file transfer solutions are essential for ensuring that only verified content is allowed to move across security boundaries.
To learn how MetaDefender Managed File Transfer (MFT) can strengthen file security in complex, low- and high-security environments.





