We live in a digital world, that rapidly changes the needs in terms of operating tools and communication channels. There is an increased need of working remotely, which will probably grow in the future, even after COVID-19 is under control. People are looking for ways to simplify their work in order to keep a healthy balance between professional and personal time. This new reality forces organizations to adapt and find new ways to answer the correlated risks:
- People who are new to working from home are the ones that have the least IT knowledge on how to be careful in terms of security incidents,
- Personal-use software is more likely to contain code that hackers can use to hijack the endpoint,
- Spikes in VPN use greatly increases the risk of ransomware and malware spreading
- Privileged or highly empowered accounts are attractive targets for attackers – hacking these accounts for PII on the black market; ransomware attacks; creating breacheswhich may lead to zero-day attacks; system shut down; loss of business;reputation damage.
IT Professionals and Security Specialists are more challenged than ever. Whether they give privileges rights or not, without a security strategy and privileged access management solution (PAM), the situation will lead to time and money loss, tension, and frustration. They need a complex solution that makes everyone’s work more efficient and safer, empowering people to install and use the best software for their needs without compromising the system’s security. This is why OPSWAT’s MetaDefender Cloud was integrated with FastTrack Software’s Admin by Request. The result: a GDPR compliant cloud-based PAM solution designed for the administrators' peace-of-mind so they can focus on their main activities.
Fast Track Admin by Request
User Experience
People utilize the software for various reasons, such as a communication tool, for instance. They are not interested in mastering the software, nor to be expert in installing it on different operating systems. They only want to use it in order to do their business or for personal purposes. The ideal situation is when users can install the software when they need it, with as few responsibilities possible, especially in terms of managing installs or the security risks that may come along. Removing local admin rights from managed endpoints mitigates critical vulnerabilities but does not allow users to run trusted tasks that require privileged elevation. Here is where Admin by Requests makes the difference: the solution takes away admins rights, but the user experience is the same as before. Users’ admin rights are revoked, but the user can still install software, even the type that needs admin rights, such as WebEx, Adobe Reader, or TeamViewer. The only thing the users must do is to search for and download the install file. Admin by Request takes over from here. The video shows the user experience with IT approval enabled.

The solution identifies the users who request software installs based on the organization’s Active Directory Groups / Organizational Units / Azure AD Groups with single sign-on. It monitors and audits behavior to reveal risky users and assets through the thread and behavioral analytics to combat malware attacks.
Installs & Administrator Rights Approval Flow
The admin needs to permanently keep the balance between making users happy and protecting the systems. Without a PAM solution, there are two possible scenarios that admins must face in any organization, both leading to stressful situations and security risks:
- If the company allows users to maintain local administrator rights, untrusted software may be installed, meaning increased security incidents (malware, breaches, zero-day/ransomware attacks) and business risks (sensitive data/PII, bad reputation, business loss, etc.),
- If the company does not allow users to maintain local administrator rights, countless remote installs will need to be done, which means less time and focus for the most important tasks. Also, they will have to implement whitelisting solutions. It is impossible to foresee all the solutions the users might need, so users may not have the required software available when they need it. Also, whitelisting files does not mean the files are safe, which leads to further security risks.
Admin by Request supports both scenarios, allowing users to install software while taking away the admin rights. It controls the users' actions and intentions, providing administrators' a simple approval process: when the user requests approval for an install, the install is logged to the Auditlog menu in the portal. When the installing starts, the process is intercepted and sandboxed without the user being the administrator and with a full audit in the app and the portal for future documentation. The user must give a reason why this software is needed, and credentials (email and phone number) in order to continue.

The admin decides whether each interception should be reviewed or use auto-approval. Watch this video for the full approval flow. The files never reside or pass the Admin by Request cloud service in any form. They are directed to MetaDefender, where they are not stored, but only scanned – they exist there only if they are scanned. The easiest and fastest way to approve a “Run As Admin“ or “Admin Session“ request is to use the mobile app or an Apple Watch. It is a real-time push and the reaction will be fast. When the Admin presses the Approve or Deny button, the user will receive an email with instruction. Admins can also use the portal for approving requests. In order to save time, an email notification to all users that can approve requests is recommended. The entire approval flow is described here.

Admin by Request is also designed for the roles that need broader privilege rights, such as developers, for instance, who have to do more than installing software or running applications as administrators. Watch this video to understand the user experience of an administrator session with IT approval enabled.
Malware Detection with MetaDefender Cloud
How do administrators assure tight security among an organization where users need privileged rights and the dynamic of software installs is increasing? Uploading files, especially using personal endpoints, connected to personal internet networks from all kinds of resources, may lead to many security incidents scenarios.
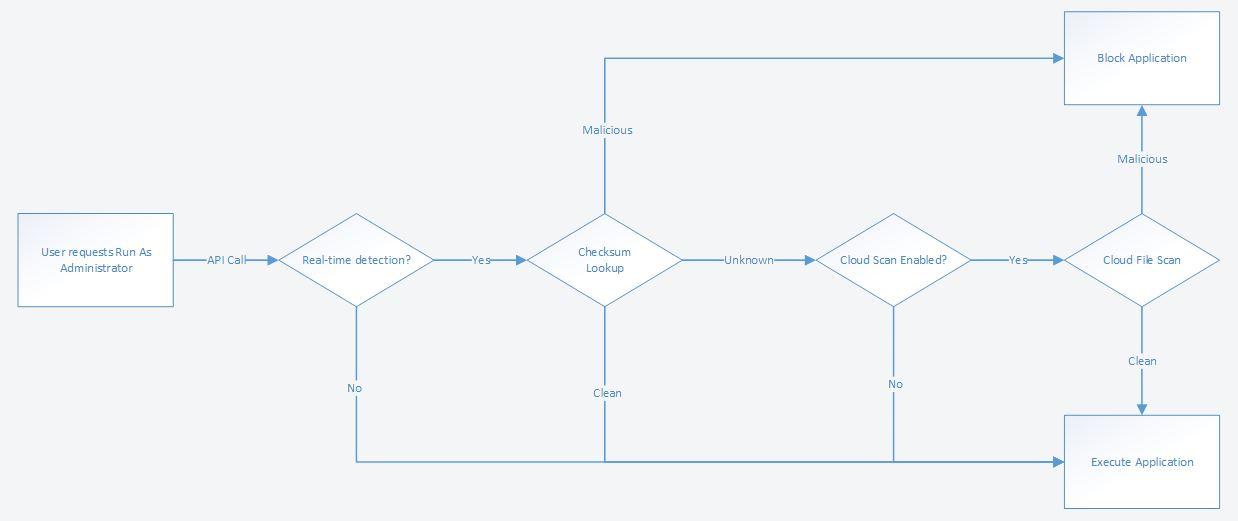
Admin by Request has integrated MetaDefender Cloud to provide the malware detection admins need before allowing any new file to enter the system. When a user requests to run a file with administrative privileges, the file is scanned in real-time by our anti-virus engines. The malware detection proceeds without any performance or waiting penalty and it doesn’t conflict with any security software customers may have on their endpoints, as it happens in the cloud.

When a user attempts to run a file with administrative privileges using Run As Administrator feature, the file is scanned on MetaDefender Cloud and if it is flagged as malicious, the endpoint blocks the file and stops the process, like in this video. An entry is added in the auditlog that the file was blocked, and which engines flagged it.
If unchecking "Cloud scan unknown files" but leaving "Real-time detection" on, only checksum lookup for the known 75% is performed and the rest must be handled by the local endpoint anti-virus product. If a file is flagged as malicious, the administrators decide what happens next, in their “Action” setting. There are two options:
- Send files to quarantine, allowing IT staff to look at the reported data, and manage the judgment, if this file should be allowed or not,
- Block the file by choosing “Permanently block”. In this case, the file cannot be approved to run at all.
Conclusion
Admin by Request and MetaDefender Cloud have joined forces to offer a simple, quick and safe file journey, with a single purpose: to provide all necessary information for the administrators to decide whether the software will enter the system or not: user credentials, the reason for using, and the malware analysis.
For more insights visit the Admin by Request dedicated pageor MetaDefender Cloudpage. Contact the team if you want to explore the user’s and the administrator's experience or you are interested in any further details.