Cybersecurity Awareness Month is an annual collaboration between governments and private industries to raise awareness about digital cybersecurity and empower everyone to protect their personal data from cybercrime.
As a global leader in IT/OT cybersecurity, OPSWAT is trusted to protect some of the world’s most critical environments. Here are four attack vectors we think you should focus on when protecting personal information from exploitation.
Emails: Public Enemy Number One
Email remains the most common vector for malware distribution, often taking the form of Microsoft Office documents or seemingly innocent attachments. Phishing emails, in particular, have gained notoriety, constituting 44% of all social engineering attacks, as reported in the 2023 Verizon Data Breach Investigations Report.
Web Applications: A Double-Edged Sword
Many organizations heavily rely on web applications for sharing and transferring critical documents necessary for their daily operations. However, productivity files like word processing documents, spreadsheets, or PDFs can also serve as vectors for cybercriminals to exploit. They may embed malware within these files and deliver malicious payloads to unsuspecting users.
According to OPSWAT's 2023 State of Web Application Security Report, data breaches remain the top concern associated with unsecured file uploads (73%), followed by concerns like reputation damage (67%) and loss in business revenue (58%).

Network Traffic: A Vulnerable Pathway
Malicious actors employ various techniques to exploit vulnerabilities or weaknesses in a network's infrastructure or its connected devices. This can lead to data breaches, service disruptions, and other forms of cyberattacks that can have severe consequences.
Portable Media: Judge Them by Their Size, Do You?
Even something as seemingly innocuous as a USB drive or a SD card can be a source of data leakage or a means to deliver malware, spyware, or viruses. Portable and removable media are essential for increasing data mobility and productivity across various environments, including IT, OT, and SCADA. However, they can also introduce significant security risks.
How OPSWAT Can Help
In a constantly evolving landscape where cyberthreats can come from any angle, it's essential to have robust cybersecurity measures in place. OPSWAT offers industrial OT and enterprise IT solutions to help mitigate these threats. If you aren’t sure where to start, here are two resources you can leverage today to enhance your cybersecurity posture:
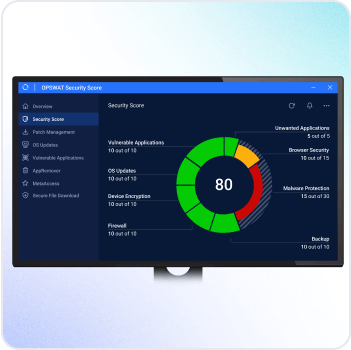
OPSWAT Security Score
This complimentary, enterprise-grade tool allows end users to check their cybersecurity posture on their computers and tablets. It's a "click-to-run" app that requires no installation or registration. OPSWAT Security Score informs users of potential security risks and vulnerabilities, providing easy-to-follow recommendations to address these issues—all without any upfront or hidden costs.

OPSWAT Academy
OPSWAT Academy helps to solve the shortage of cybersecurity professionals by offering practical courses promoting best practices and the latest advances in Critical Infrastructure Protection (CIP). All courses are created by industry leaders with a proven track record, and they include easy-to-understand examples of cybersecurity measures that translate to real world scenarios.
Cyberthreats are constantly evolving, and a proactive, defense-in-depth approach to cybersecurity is the key to safeguarding your digital assets and personal information. By staying informed and leveraging resources like OPSWAT's solutions, we can all contribute to a safer, more secure tomorrow.
Discover why OPSWAT is the critical advantage in cybersecurity—talk to one of our experts today.

