The growing sophistication of modern threats can’t be ignored, especially AI-powered ones.
Artificial intelligence is no longer confined to academic papers and futuristic speculation, as it’s being embedded into malware.
Given that attackers can now use AI to build malicious code that adapts in real time, learns its environment, and can navigate around weakly implemented defenses, a natural question arises:
Can AI-powered malware outsmart a data diode?
This question reveals a deeper tension in industrial cybersecurity: the assumption that smarter software can always beat smarter malware.
But what happens when the barrier isn’t software at all? What happens when the barrier is physical?
Data Diodes: Security at the Physical Layer
A data diode is a hardware device designed for unidirectional data transfer, allowing information to flow in only one direction between networks, preventing data from flowing back into a protected network.
In most architectures, a diode consists of a transmitter and a receiver, typically based on fiber-optic isolation.
Light can only pass in a single direction: from an internal (high-security) source to an external (lower-security) destination, with no return channel for the other way around.
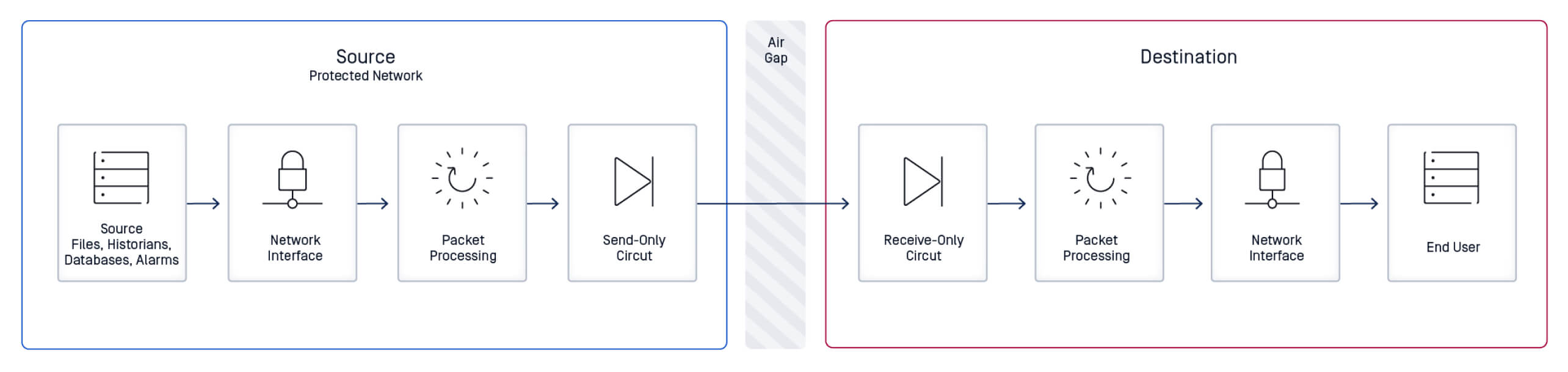
There’s a deceptively simple concept at the core of data diodes: data can only travel one way.
This isn’t a matter of policy, rulesets, or firmware.
It’s enforced by hardware.
As far as cybersecurity goes, diodes don’t just minimize risks; they eliminate entire categories of risk by design.
Modern diodes have been around since the 20th century; but can they still handle threats based on cutting-edge technologies?
AI Malware: Smart Enough to Adapt — But Still Confined to System Layers
AI-driven malware is real, and it’s dangerous.
These programs can profile host systems, blend into network traffic, evade traditional detection, and even auto-select exploits based on environmental cues.
But here’s what’s often misunderstood: no matter how advanced it is, AI malware still operates within the constraints of the OSI model — typically between Layers 3 and 7.
That means it depends on the logical and software layers to function. It still requires:
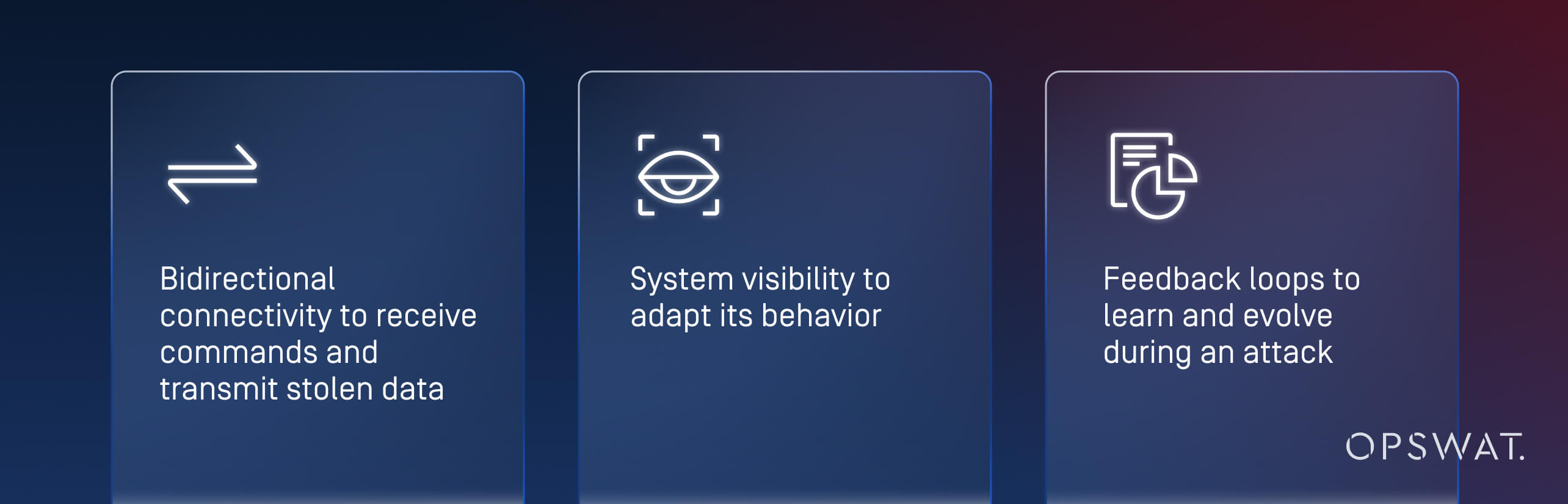
A data diode removes that feedback loop entirely.
There is no control channel, and no way for the malware to test or refine its actions.
In other words, data diodes don't focus on outsmarting the malware, but on denying it a channel to operate at all.
How the Data Diode Actually Blocks Malware
A well-deployed diode doesn’t just block data, but prevents any two-way communication between networks:
- Command and Control traffic is physically blocked from entering the secure network, so attackers cannot send commands to the malware, effectively cutting off their ability to manipulate infected systems.
- Exfiltration attempts hit a physical dead end.
- Backdoor channels never form to begin with as there’s simply no return path for malware to exploit.
- Phishing payloads that enter the OT zone through other endpoints are rendered ineffective at exfiltration; there’s no outbound route for them to report back.
- Real-time reconnaissance tools lose visibility into their impact.
In well-isolated OT networks, this model of enforcement is often the last line of defense when detection-based tools inevitably fail against novel or AI-generated threats.
Can the Diode Be Circumvented by AI?
No technology is infallible when improperly implemented.
The biggest risks to data diodes deployments typically come from:
- Human error, if connecting temporary bidirectional links “just to troubleshoot”
- Side-channel abuse coming out of secondary paths (like cellular modems or USBs) usage, not covered by diode policies
- Improper logical segmentation if layering software replication on top of diode links happen without proper isolation
However, these are architectural, preventable issues, not diode failures.
The strength of a diode lies in its simplicity.
As long as the data path is physically unidirectional and the receiving network is properly segmented, the diode cannot be bypassed by any malware — AI or not — without bypassing physics itself.
MetaDefender NetWall: Hardware-Enforced, Mission-Proven
To truly take advantage of a diode’s segmenting capabilities, organizations need a solution that combines uncompromising physical security with proven performance in the most demanding environments.
OPSWAT's MetaDefender Netwall™ is built for critical infrastructure environments, where the cost of compromise is measured not just in dollars but in downtime, safety, and compliance violations.
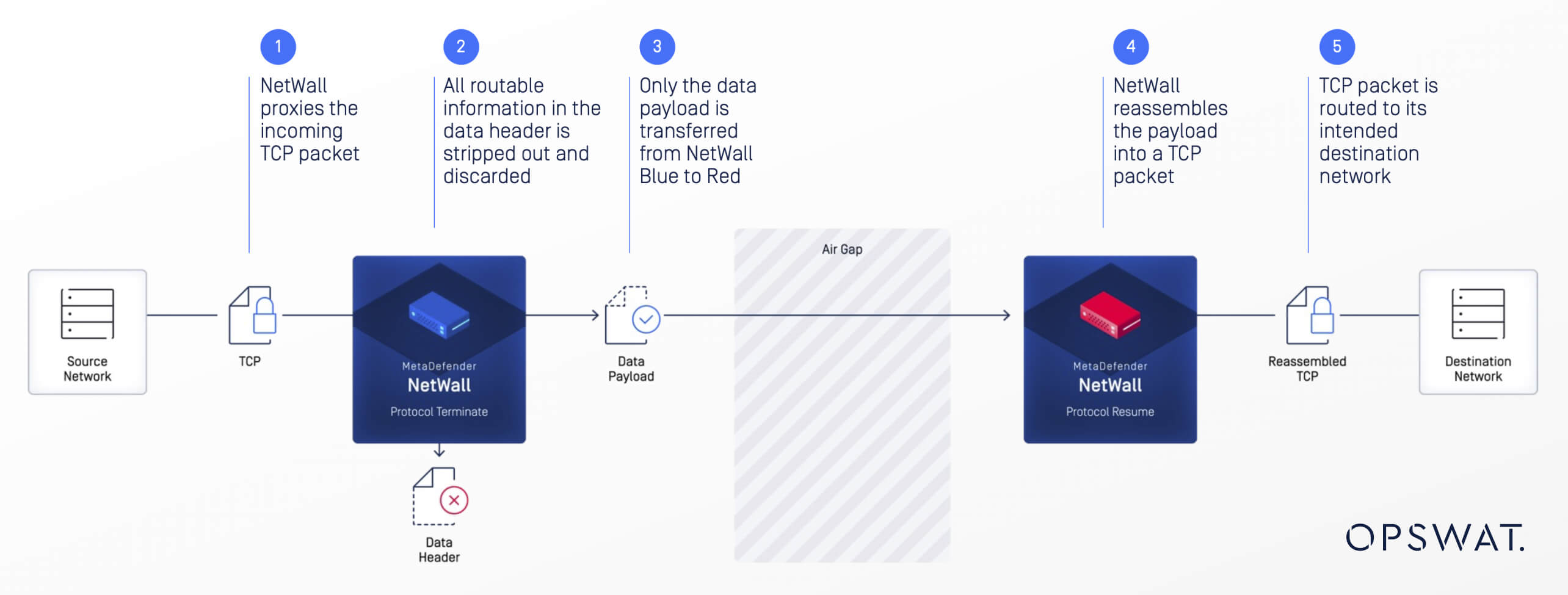
OPSWAT's MetaDefender NetWall offers:
Security through hardware enforcement
By enforcing unidirectional data flow at the hardware level, the system guarantees that data cannot leak back, eliminating risks of software-level bypasses or malware exploits.
Seamless integration with OT Systems
Support for key operational technology protocols (OPC UA, AVEVA PI, Syslog, MQTT) ensures compatibility with critical industrial environments without disrupting existing workflows.
High performance without sacrificing security
Designed for high-bandwidth environments, it enables efficient data transfer while maintaining strict network isolation and security.
Trusted compliance and assurance
Achieves Common Criteria EAL4+ certification and aligns with industry security standards like IEC 62443 and NERC CIP, providing confidence that it meets rigorous regulatory and cybersecurity requirements.
Where other tools attempt to detect or respond, MetaDefender NetWall takes a preventive position.
It enforces a security boundary that’s not subject to patch cycles, not dependent on threat intelligence feeds, and not vulnerable to the evolving logic of AI-based malware.
Final Takeaway: Security based on Hardwired Principles
When we are faced with increasingly intelligent threats, we often assume that the solution must also be complex.
But sometimes the strongest defenses are the simplest, and the most absolute.
A diode doesn’t need to inspect traffic or detect anomalies. It doesn’t need to understand the threat.
It just doesn’t let the threat in.
When deployed correctly, a data diode becomes more than a best practice.
It becomes a boundary that sophisticated malware — even malware powered by AI — simply cannot cross.
Ready to strengthen your security with proven simplicity? Talk to a MetaDefender NetWall expert today to see how a hardware-enforced diode can protect your critical infrastructure.

