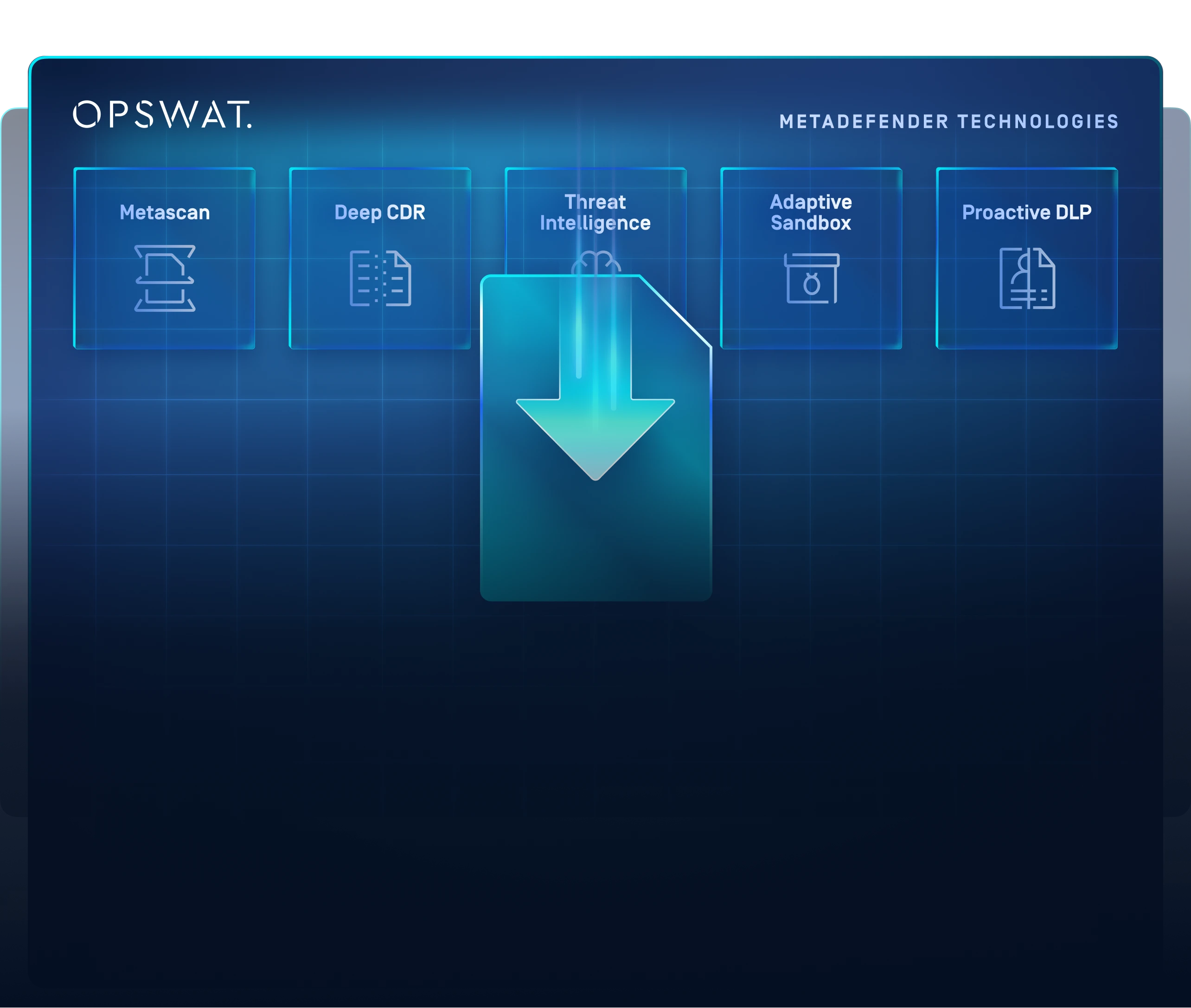
File Download Security Beyond the Browser
MetaDefender Core™ is an open platform that seamlessly integrates with Remote Browser Isolation (RBI) solutions to provide robust security for files that can't be rendered in a browser or require access to internal systems, ensuring comprehensive protection for all file types.
File Download Security Risks
Download Restrictions
Restricting access to essential files reduces productivity and limits collaboration, making secure alternatives a necessity.
RBI Gaps
RBI solutions alone cannot securely handle all file types, leaving gaps for complex files like executables and rich media.
File Complexity
Advanced files often fail to operate in browser-rendered environments, impacting usability and functionality.
Transfer Risks
Moving files from RBI environments to internal networks creates risks like malware infiltration and malicious links.
Workflow Failures
Traditional security tools overlook workflow needs, requiring open platforms for secure and seamless file handling.
The OPSWAT Solution
Organizations rely on OPSWAT to strengthen their RBI implementations by protecting against file-borne malware as it moves across security domains. With MetaDefender Core, an open platform that enables API integration with any RBI tool, OPSWAT ensures secure user downloads from browser-isolated environments to corporate networks.
Open Platform Integration
MetaDefender Core REST API integration with RBI solutions for a seamless download user experience.
Detect More without Impacting SLAs
Metascan™ Multiscanning leverages 30+ commercial anti-virus engines to deliver over 99% detection rates.
Prevention through File Regeneration
Deep CDR™ eliminates evasive advanced threats, disarming and regenerating safe-to-use downloaded files.
Adaptive Threat Detection at Speed
Adaptive Sandbox Module detects complex and evasive threats in 50+ file types for deeper analysis of downloaded file-borne threats.
Open Platform Implementation
IT Administrators use MetaDefender Core to augment their RBI capabilities, extending the security of a file beyond the isolated browser environment. It is important that the users’ experience is unchanged, with minimal to no impact on usability. Implementing MetaDefender Core to support secure file downloads includes the following steps:
Integrate With Your RBI Solution
Select OPSWAT MetaDefender integration from the RBI's admin console, add the URL for the MetaDefender server and the desired workflow name and/or API key. Make sure MetaDefender API can be reached by the RBI.

Build a Custom File Download Workflow
Define file analysis for downloaded files using MetaDefender Core’s Workflow configuration to define file archive extraction limits, file type verification, and blocked and allowed file types and sizes.
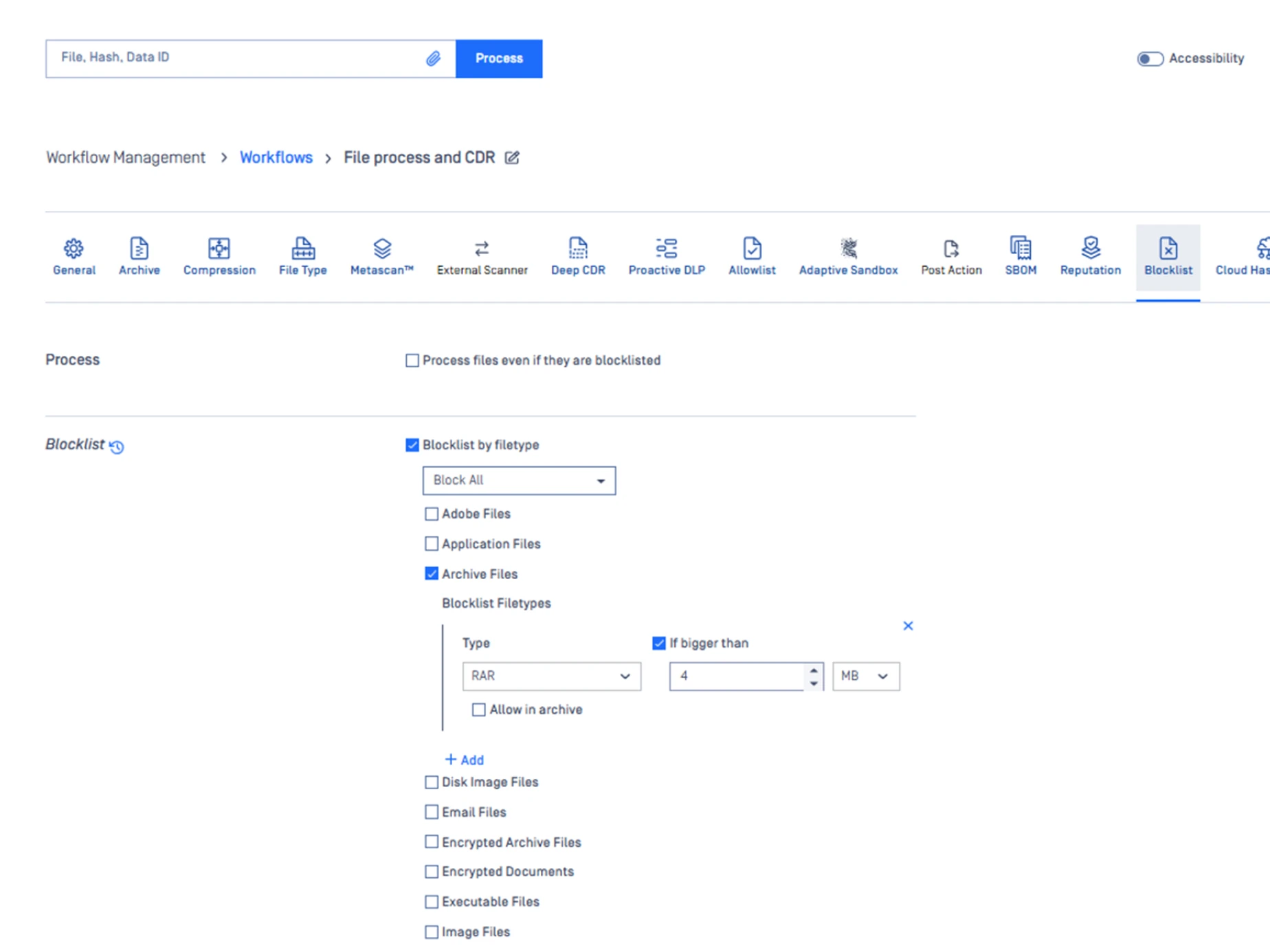
Tune to Optimize Infrastructure
Optimize MetaDefender Core for file download workflows that typically consist of 3 to 4 downloads per user, per day. Tuning includes setting the MetaDefender Core queue size, MetaDefender engine parallel count and file analysis and engine timeouts.
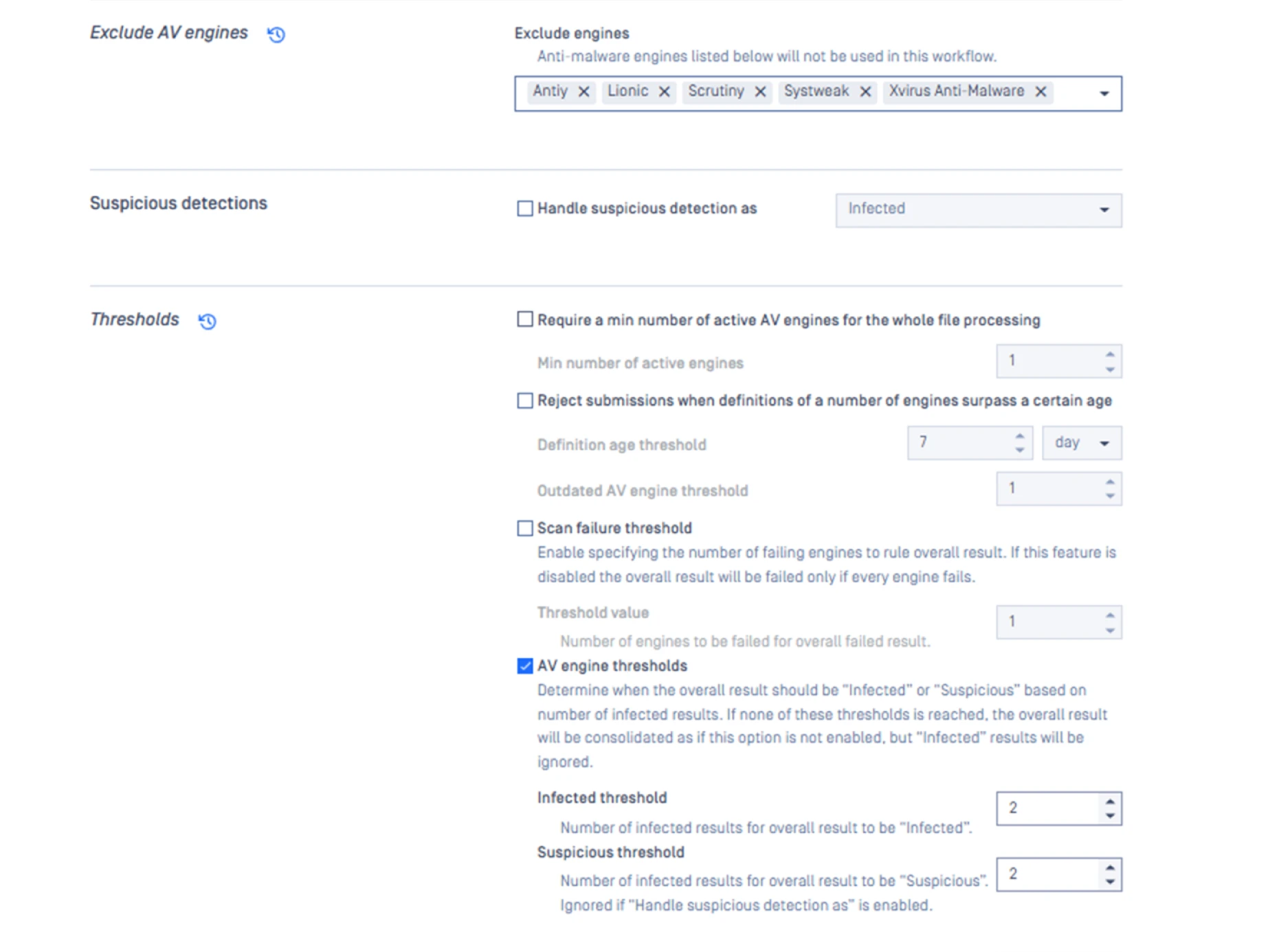
Create a Unified File Security Policy
Define a policy for files downloaded and processed through an RBI including:
- Define handling by file type for a greater degree of file level control. Configurations to consider include removing macros, recursive level of sanitization, and image processing.
- Determine the Metascan antivirus engine threshold for the number of “infected” results required for the overall results to be considered “infected”. This policy is used for the file download use case where the threshold level for unknown files should be low.
- Per file type, define events where a file would be blocked, including invalid file structures or the inclusion of scripts, hyperlinks, and embedded objects. Define the output file type for the sanitized, usable file that will be returned to the user.
- Define configurations for the Adaptive Sandbox Module, including enabling OSINT lookups on extracted artifacts, enable file visualization, and YARA rule matching on incoming files.
Get Started with OPSWAT Today
OPSWAT is a leader in cybersecurity solutions because we understand the risks and challenges that modern organizations face. We've developed threat intelligence capabilities that enable your team to understand threats and respond faster than ever.
Get started with our team today to discover our file security solutions.
