Achieve OWASP
File Upload Standards with MetaDefender Core
Turn OWASP File Upload Cheat Sheet Standards
into Real-World Protection
File uploads are a security blind spot. Threat actors routinely bypass traditional security measures to infiltrate file systems with malware and exfiltrate data. OWASP defines how to secure this critical vector, and OPSWAT delivers industry-leading solutions.
OWASP Cheat Sheet Overview
Recognized globally, OWASP is a nonprofit foundation that provides authoritative guidance to help organizations identify and mitigate critical security risks. The OWASP File Upload Cheat Sheet offers a clear, practical framework for reducing the risk of compromised file uploads. By following its guidance, organizations can enforce safer file handling at every step, from file validation to storage, and prevent malware from reaching critical infrastructure.

File Upload Blind Spots
These gaps are often overlooked when handling uploaded files or designing a file upload application:
- Weak validation (unsafe extensions, spoofed headers, filename manipulation)
- Resource abuse (oversized, malformed, or excessive uploads)
- Poor access control (anonymous users, public/exploitable storage paths)
- Missing threat prevention (no malware scanning or CDR)
- Neglected hygiene (outdated libraries, unprotected endpoints like CSRF

Secure File Upload Solution Mapped to
OWASP Recommendations
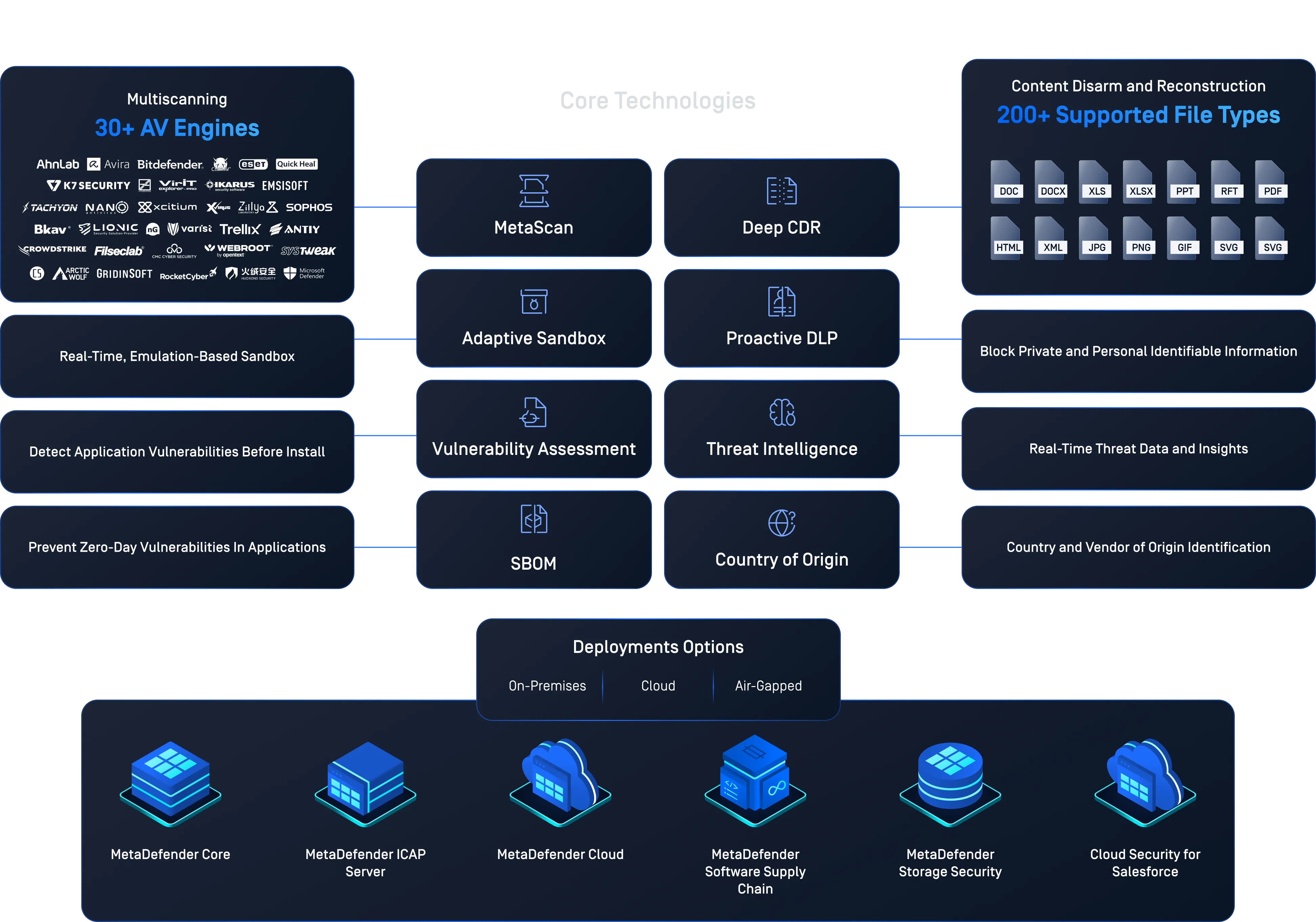
This table shows how OPSWAT implements a defense-in-depth strategy for file uploads, enabling organizations to close critical gaps and align with OWASP secure file upload implementation. Explore how each OWASP recommendation maps to specific MetaDefender solutions and technologies, including Deep CDR™ Technology, Metascan™ Multiscanning, and Adaptive Sandbox.
OWASP Recommendation | Why It Matters | How OPSWAT Helps |
|---|---|---|
Validate file extension and true file type | Prevents spoofed files (e.g., .jpg.exe) from bypassing filters | Detects mismatches between extension, MIME type, and true content; enforces policy with AI-driven validation |
Change file names; limit length and characters | Prevents injection, traversal, and overwrite attacks | Recommends using unique identifiers; allows custom naming policies with validation guidance |
Set file size limits | Avoids resource constraints; prevents denial-of-service via large files or ZIP bombs | Blocks oversized files, limits recursion depth, and inspects archives before processing |
Require authentication and authorization | Blocks unauthorized uploads and reduces attack surface | Supports client/IP-level restrictions. |
Store files on a separate server | Prevents direct execution or public access to uploaded files | Scans and sanitizes files before storage; integrates with user-defined storage workflows |
Scan files with antivirus and sandboxing | Detects known, unknown and evasive malware | Combines 30+ anti-malware engines with emulation-based sandboxing to identify threats and indicators of compromise |
Use Content Disarm and Reconstruction (CDR) | Removes unknown/zero-day threats without relying on detection | Deep CDR™ Technology neutralizes scripts, macros, and embedded threats while preserving usability |
Keep third-party libraries up to date | Reduces risk from vulnerable components in the software supply chain | Detects vulnerable libraries and outdated licenses, provides SBOM visibility, and highlights affected components |
Protect uploads from CSRF attacks | Prevents unauthorized uploads via forged requests | Recommends CSRF token use; integrates with WAFs for secure front-end defense |
Built-In Technologies that Enforce
OWASP Guidance
Proven Effective by
Third-Party Testing
Deep CDR™ Technology received a 100% Protection and Accuracy score in SE Labs’ independent CDR testing. This validates MetaDefender Core’s ability to remove embedded threats while preserving usability, supporting OWASP’s call for CDR solutions and zero-trust file inspection.
Secure File Uploads Start with the Right Framework
The OWASP File Upload Cheat Sheet provides a proven foundation for securing file uploads, from validation to malware scanning to sanitization and safe storage. MetaDefender Core is purpose-built to help security teams apply these best practices quickly and effectively, making OWASP-aligned file upload solutions simple to implement.
- Aligns with OWASP’s trusted best practices for secure file handling
- Addresses blind spots in file validation, sanitization, and zero-day threat detection
- Supports compliance with internal and external security frameworks
- Reinforces architecture decisions for risk, audit, and GRC teams
- Streamlines Zero Trust implementation for file uploads and storage
- Minimizes the risk of file-borne threats across web portals, applications and storage systems

FAQs
The OWASP Top 10 is a regularly updated list of the most critical web application security risks. It includes threats like injection, broken access control, insecure design, and security misconfigurations. These are common vulnerabilities attackers exploit to compromise systems.
OWASP cheat sheets are concise best-practice guides covering specific security topics, including secure file uploads, authentication, input validation, and more. They offer actionable steps to reduce risk in common application components.
OWASP standards provide a blueprint for embedding security into web application design. By following them, organizations can proactively mitigate threats like file-based attacks, code injection, and broken access controls, strengthening both compliance and resilience.
Look for solutions that offer file type validation, file size enforcement, antivirus and CDR integration, and support for access control and secure storage. The solution should map directly to OWASP file upload cheat sheet standards and integrate with your infrastructure (REST API, ICAP, etc.).
MetaDefender applies multi-layered security technologies, including true file type detection, Deep CDR™ Technology, Metascan Multiscanning with 30+ anti-malware engines, archive extraction controls, and size restrictions. It aligns with all OWASP file upload recommendations to prevent known and unknown threats.
Organizations that implement OWASP file upload cheat sheet standards must enforce strict validation (type, size, name), require authenticated users, inspect and sanitize files before storage, and isolate uploads from the webroot. They should also integrate critical systems with WAFs and use defense-in-depth techniques like CDR and sandboxing.
Use a solution like MetaDefender Core that detects true file types, rejects mismatches, and applies Deep CDR™ Technology to remove out-of-policy content. Validation should happen before processing; sanitization ensures the file is safe even if malware evades detection.
Key features include multiscannning, CDR, SBOM generation, audit logging, policy-based scanning, and compliance with frameworks like ISO 27001, HIPAA, and NIST. The solution must align with OWASP and enforce zero-trust principles.
Yes. Deep CDR™ Technology disarms known and unknown threats by removing scripts, macros, and embedded objects, without relying on threat signatures. It enables compliance with OWASP, ISO, and NIST by ensuring only safe, functional files enter your systems.
