Vulnerability Management Module
Modern Vulnerability Management with OPSWAT
The MetaDefender Access Vulnerability Management Module enables the MetaDefender Access Platform to detect and report vulnerabilities in installed software on the device including third-party applications and critical OS security patches. The module supports multiple versions of the Windows, Linux and macOS operating systems and currently detects over 27,000 Common Vulnerabilities and Exposures (CVEs) in endpoint applications such as Adobe Acrobat, Mozilla Firefox and Zoom Client. As the number of CVEs grows, so does the depth and breadth of the MetaDefender Access Vulnerability Management Module.
Challenges in Vulnerability Management
Vulnerability management is a critical process that often falls behind in organizations without the right tools. Some of the core challenges in this area include:
No Unified View
To effectively manage vulnerabilities, cybersecurity teams need to understand what threats they are facing. Often, these teams develop an awareness of different vulnerabilities through different channels. For example, network vulnerabilities are found through network scanning, while application vulnerabilities might be discovered through penetration testing. With the increasing complexity of IT-OT systems, vulnerabilities can emerge from numerous sources, making it challenging for teams to identify all risks and grasp the full picture of cybersecurity vulnerabilities.
Outdated Methods
Many organizations rely on manual methods for vulnerability scanning, which can be time-consuming and inaccurate for the pace of modern threats. These outdated methods tend to lead to a weaker remediation strategy because there is a higher rate of redundancy, false positives, and human error.
Ineffective Reporting
Vulnerability assessment is key for effective decision-making and remediation. A thorough vulnerability report can reveal patterns that allow you to strengthen response strategies. Conversely, inaccurate or confusing reports can hinder communication and coordination between teams within an organization.
Exploring New Solutions for Vulnerability Assessment
The Common Vulnerability Scoring System (CVSS) is an industry standard for assessing the severity of computer system security vulnerabilities. CVSS assigns severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to the threat level. These scores are calculated based on a formula that depends on several metrics reflecting the ease and the impact of exploitation.
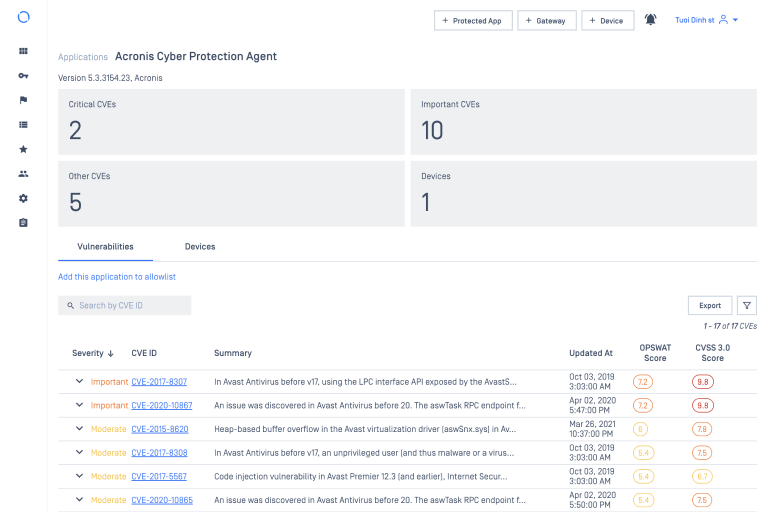
While the Common Vulnerability Scoring System (CVSS) broadly assesses vulnerabilities, it does not reflect real-time risks or the unique impact on individual organizations. OPSWAT enhances the utility of CVSS by introducing the OPSWAT Severity Score, a dynamic metric ranging from 0 to 100. Combining CVSS principles with extensive big data analytics, it filters out outdated or less critical CVEs, streamlining vulnerability management for greater efficiency. Develop an optimized prioritization system for addressing issues based on this metric and rest assured that our vulnerability management module provides the intelligence you need for effective risk mitigation.
In 2022, a record 26,448 new vulnerabilities were discovered and assigned a CVE identifier, averaging more than 72 unique vulnerabilities per day.
Strengthening End-to-End Vulnerability Management with an Intuitive Solution
With increasing cybersecurity challenges, effective vulnerability management is crucial and needs to be as seamless as possible. Your organization may operate with disjointed systems and limited visibility now, but our vulnerability management module takes your practices to a new level.
A Unified View
Many teams use multiple sources to identify different types of vulnerabilities, and information can get lost among the many moving parts. Our vulnerability management module is a part of MetaDefender Access, providing a unified interface to maintain a broad scope of current vulnerabilities and follow through with remediation steps.
Built-in Policy Management
Every organization is unique when it comes to cybersecurity policies. Whether you have unique device management practices or specific internal policies you would like to align with, you can adapt the vulnerability management module to meet them. Manage these configurable settings through MetaDefender Access to meet all of your requirements for vulnerability management.
Active Updates
Applications and vendors develop new vulnerabilities as they iterate their product releases. With the rapid pace of modern cybercrime, these weak points may be exploited if they go unnoticed for too long. We have developed our vulnerability management system to actively update with known vulnerabilities to ensure your organization is always informed about weak endpoints. Stay informed and manage risk more effectively with our proactive approach.
Vulnerability
Our list of known vulnerabilities continues to grow. MetaDefender Access refers to this list to inform your organization of relevant concerns based on the vendors and products you use. Explore our list below.
Please select the platform and the version.
Experience Seamless Endpoint Vulnerability Management With OPSWAT
OPSWAT has a heightened awareness of the many challenges organizations face in managing vulnerabilities. We have developed our module for MetaDefender Access to help teams overcome these hurdles with enhanced visibility, reporting, and severity scoring. Build effective priorities for remediation and keep your data safe with OPSWAT. Get started with MetaDefender today.