Ping Identity + OPSWAT
Ping Identity and OPSWAT have integrated their secured access solutions to offer both identification and device compliance before granting access to cloud applications. Secure your cloud access control framework from unmanaged, risky, and noncompliant devices. This includes devices within your network, guest devices, and devices attempting to access your network. MetaDefender Access empowers organizations to enforce internal security standards and meet security and regulatory compliance across all devices accessing corporate data, whether the devices are corporate-owned or not. MetaDefender Access works seamlessly with PingOne DaVinci to provide a complete device security profile before the user gains access to critical digital assets. MetaDefender Access acts on the essential role of allowing or disallowing access by running the device posture check and making sure the device complies with the organization's policy.
“The partnership with OPSWAT really uses the MetaDefender Access capability to deliver a connector into the PingOne DaVinci orchestration tool to enable deep compliance checks and security capabilities to be integrated into the flows for your users.”
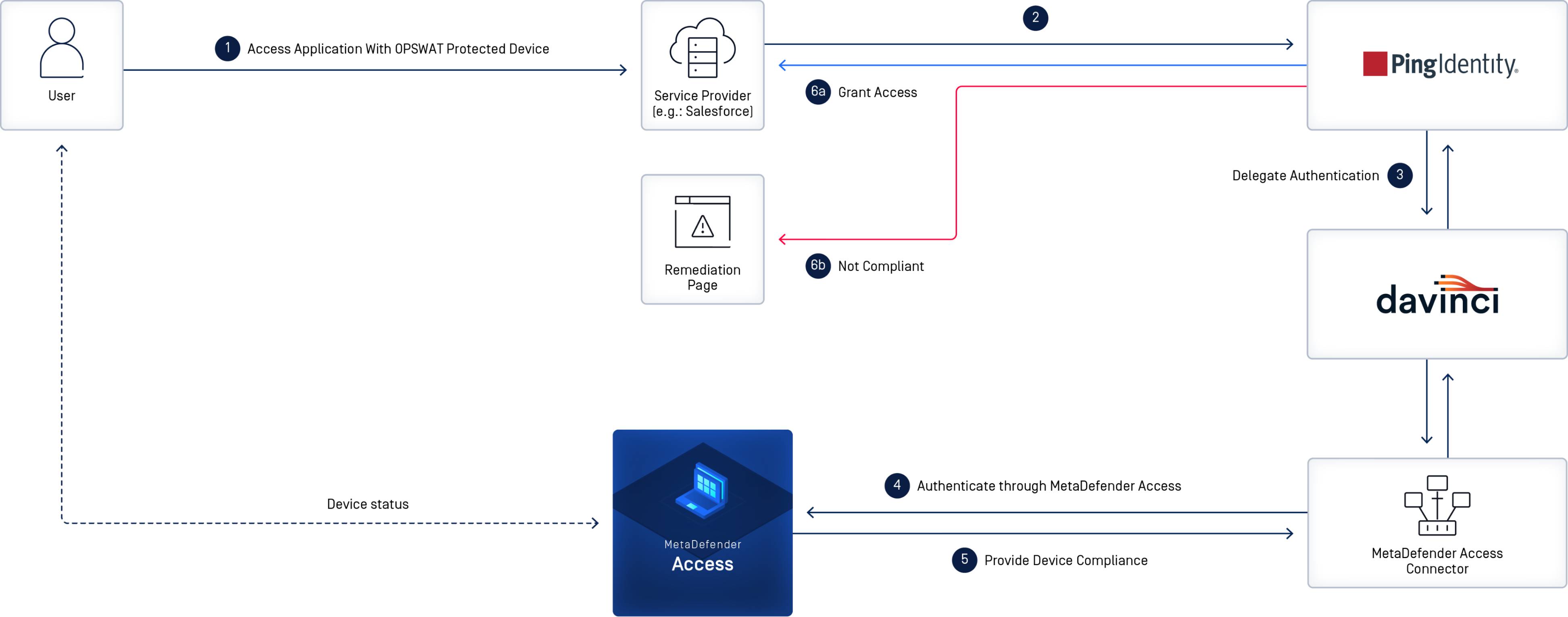
Joint Solution Components
Benefits
By deploying the joint solution by OPSWAT and Ping, users benefit from OPSWAT’s deep experience in identifying and remediating endpoint security and compliance issues.
- Endpoint infection detection with up to 35+ anti-malware engines using MetaDefender platform
- Comprehensive anti-malware compliance verification
- Detection and fingerprinting of over 5000 third-party applications
- Disk encryption status check using OPSWAT patented technology
- User authentication and screen lock check
- Endpoint vulnerabilities detection
About Partner
Ping provides intelligent access for customers, employees and partners so they can securely connect to cloud, mobile, SaaS and on-premises applications and APIs. Their cloud identity, private cloud identity and on-premises software solutions help you prevent security breaches, manage sensitive data and improve user engagement by optimizing both security and convenience.