The video tutorial will walk you through how this innovative solution can detect and eliminate threats, ensuring your systems remain secure and compliant. To fortify system integrity, availability, and compliance with OT mandates, adopting a comprehensive approach to security is crucial for protecting your critical infrastructure.
Even in highly secure environments, there is a need to provide network access to transient cyber assets (TCAs) such as laptops for daily operation. In some cases, due to device technology complexity, ensuring transient devices are secure before bringing into secure zone can be challenging, especially when some devices using specialized applications preinstalled on laptop. Watch MetaDefender Drive in action on how it helps to secure your critical infrastructure in 3 simple steps.
Understanding the Risk of Transient Cyber Assets
Transient devices pose special challenges for OT air-gapped environments, such as:
Compliance requirements
Sensitive data leakage
Device technology complexity
End-to-end supply chain security
The Role of MetaDefender Drive in Securing your Supply Chain Security
MetaDefender Drive by OPSWAT is a powerful tool specifically designed to protect your supply chain, ensure transient cyber assets are safe for use. It is design with all-in-one MetaDefender core sitting on its own. The Drive completely self-contained that boot a laptop using the separated operating system and performs a bare metal scan on the device to detect threats that traditional scanning methods miss.
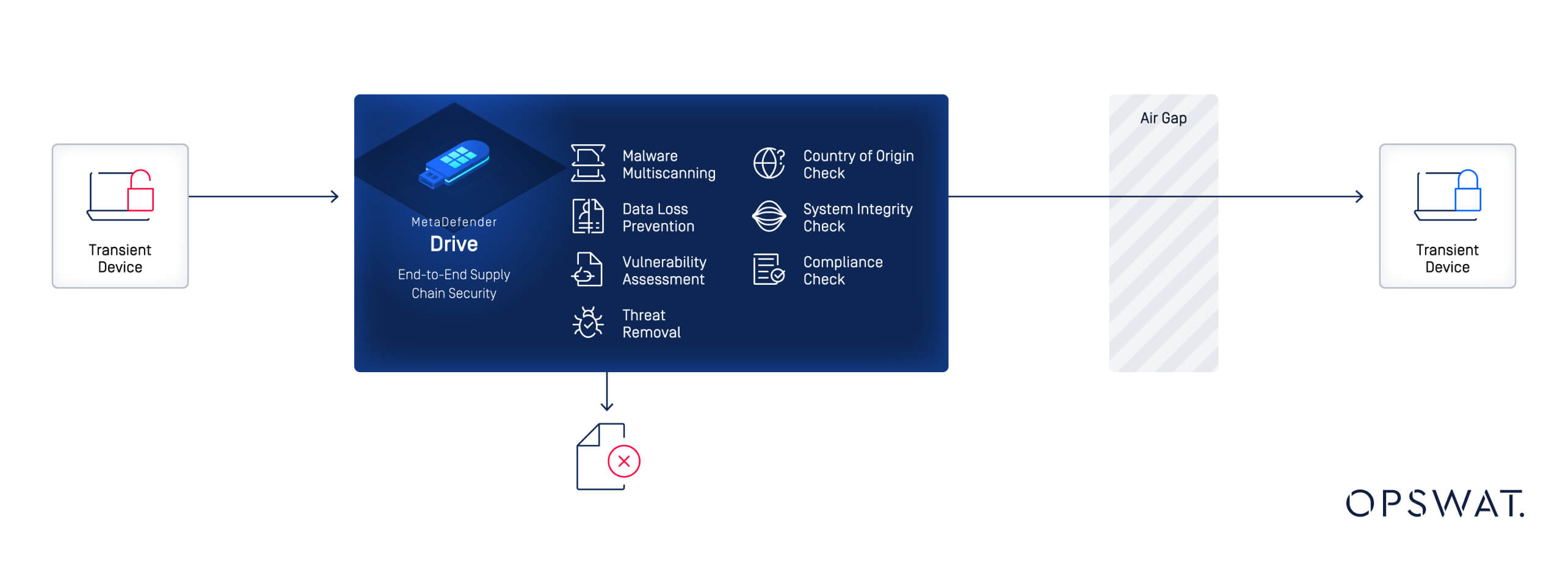
Zero-Trust secure bare metal scan boot
Easy-to-use
Support for UEFI, GPT, Legacy BIOS
Security Compliance ready
No software installation required
Threat removal
End-to-end supply chain security
File-Based vulnerability assessment
Country of Origin Check
OPSWAT’s MetaDefender Drive is an end-to-end supply chain security solution that protects critical infrastructure air gapped networks by securing both transient devices, such as vendor laptops, and stationary IDS components, like engineering workstations and servers, while maintaining essential security and compliance for air gapped networks.

