Author: Randy Abrams, Sr. Security Analyst, OPSWAT.
We all have a fairly good idea of what IoT is. Depending upon who you talk to, IoT is the Internet of Things, the Insecurity of Things, or the Internet of Terror. If you work in an industrial control system (ICS) environment, you know it as the Internet of Terror.
For years IT departments have grappled with shadow IT. Shadow IT refers to devices that are unauthorized on the network and/or managed outside of the IT organization. Shadow IoT is pretty much the same thing as shadow IT, except it sounds cooler when you say IoT. Even when IoT devices on a network are accounted for, they may not be managed or properly secured. The implications to network security are often not fully understood.
If you work in an ICS facility you are probably familiar with IIoT devices such as those connected to remote terminal units (RTUs) and control units (CUs). Hopefully these devices are known to the IT department, and the IT department understands the criticality of keeping these systems secure.
However, these are not the IoT devices I am going to talk about today. Today I am talking about the insidious shadow IoT devices that hide in plain sight. IoT devices are becoming increasingly common in corporate environments, but their presence in the critical infrastructure is particularly worrisome.
Make yourself a cup of coffee, using the dumbest coffee maker you can find, and enjoy it as you listen to a tale of an IoT hot water kettle. In a 2018 TEDx presentation, Ken Munro of Pentest Partners LLC demonstrated how a Wi-Fi enabled water kettle could be exploited in order to gain network access. You can listen to Ken’s TEDx talk here.
IoT kettles are not the only innocuous looking IoT device threats. There maybe a network security threat lurking in the fish aquarium too. In 2017, Forbes reported a casino had been hacked via an internet connected thermometer in a lobby fish aquarium. Although the casino’s security team noticed unusual traffic coming from the thermometer, 10 gigabytes of data had been exfiltrated before the attack was stopped. The leaked data included information about the casino’s high rollers. Did the convenience of the IoT thermometer warrant the risk? Not as it was deployed, but hey, it’s just a thermometer... that added an attack vector.
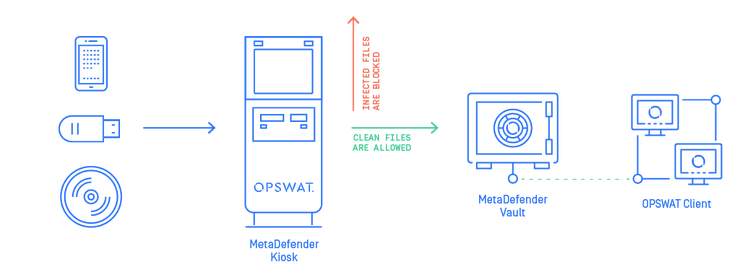
The threats IoT devices present to networks are not as well understood as the risks associated with USB devices. Policies and procedures concerning USB devices are common. USB devices can be scanned by solutions such as MetaDefender Kiosk to identify known threats, apply content disarm and reconstruct (CDR) technologies to files to neutralize unknown threats, and to perform data loss prevention (DLP) – a technology the casino could have used to mitigate the damage. The need for IoT policies is not commonly recognized and when they do exist, they may not be as all-encompassing as they should be.
IoT is a bit more problematic. People walk past IoT refrigerators all the time without thinking “Gee wiz, that’s an IoT device that can pose a threat to the network.” That new coffee maker in the reception lounge may be flying under the radar. Nobody ever called IT to say “We’ve installed an IoT coffee maker in the lobby, can you send a tech down to secure it?” Why would they? After all, it’s a coffee maker, not a backdoor. It’s a refrigerator not an attack vector, right? Policies around IoT devices rarely exist. Most IoT device manufacturers have no clue that they need to build security into their devices. Fun fact: Blizzards are more common to Singapore than security is in the design lifecycle of most IoT devices.
I recently spoke with Jake Brodsky, a 30+ year veteran of the ICS industry. Jake is very concerned about the trend of putting IoT devices into critical infrastructure environments. I asked Jake if there are washing machines in ICS facilities. Jake indicated that in a facility he had worked at there were washing machines. So, I asked Jake what he would do if he discovered an IoT washing machine in his facility? Without missing a beat Jake replied, “I would remove the Wi-Fi module.” Jake has done that to several network-oriented printers.
IoT smoke detectors present an intriguing concept. I have smoke detectors in my home that “talk” to each other. If one smoke detector is triggered, it tells the other smoke detectors to sound off as well. Some smoke detectors also have network/Internet connectivity. When the technologies are combined, we have IoT devices with network connectivity and wireless peer-to-peer communications. Consider this configuration. One smoke alarm is on one network segment. Another is connected to a different (air gapped) network. Using peer-to-peer communications they talk to each other. Now a situation has been created where our smoke detectors have jumped an air-gapped network. Can arbitrary data communications be established between the two devices? It is not inconceivable that one day this will be the case.
IoT device vulnerabilities are commonplace. CVE-2019-13473 addresses undocumented Telnet services in some IoT devices. CVE-2019-13474 documented devices having insufficient access control. CVE-2015-2880 addresses a backdoor in a baby monitor – password “admin”. In 2017 Cisco Talus identified 32 vulnerabilities affecting Foscam cameras alone. At Black Hat 2019 Microsoft researchers revealed that a VOIP phone, an office printer, and a video decoder had been used by malicious actors to gain access to a corporate network. An improper SSL implementation in Samsung smart refrigerators enabled an MiTM attack that could compromise Gmail credentials. Never mind Uber Eats, Gmail can deliver SPAM direct to your refrigerator!
Near the end of Ken’s TEDx talk he offered the following advice. “IoT, you can put it on a separate network at home. If you don’t know how to do that, go read up. If you don’t want to do that, don’t buy IoT.” As the casino found out, fish do not need access to corporate databases. Segment those networks.
Conclusion
- All IoT devices must be identified as such and properly secured. This may require physically surveying the facilities as some of these devices might not be online.
- Put IoT devices on their own network.
- Eliminate all IoT devices that are not required for business continuity.
- Keep IoT devices current with software/firmware and other security patches. Note: IIoT devices cannot always be patched and may require other mitigations.
- Pray. A lot. It may be your last line of defense.
Unless you can prove a device with batteries, solar panels, or a power cord is not IoT, it is. Trust no file. Trust no device.
Randy Abrams is a veteran of the cybersecurity industry with over 20 years of experience, he holds the position of Sr. Security Analyst at OPSWAT.
For more information on how organizations are successfully protecting their critical infrastructure using OPSWAT visit https://www.opswat.com. Or, request to be contacted about technology partnerships, channel partnerships, media inquiries, or general product questions here.

