In a situation post-malware breach, it may be the case that the malicious file is instantly deleted from the system rather than quarantined. If further investigation on the malicious file is still desired, a network protocol analyzer (such as Wireshark) has been actively running and there is an available PCAP file to retrieve the threat, it is possible for security professionals to extract the malicious file for further evaluation.
In this example we will show how to perform this task using Wireshark with a session where an EICAR test file was downloaded.
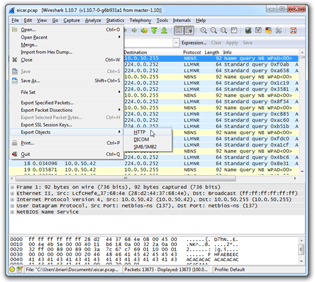
- Launch Wireshark and in the File menu select Open, then open the PCAP file you wish to investigate.
- Open the file menu again and select Export Objects, then HTTP.
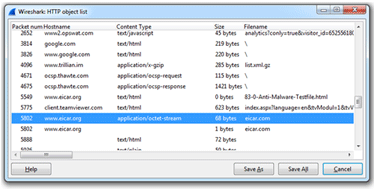
- The resulting window will list all of the HTTP objects from that PCAP file. Highlight the file you wish to extract and click Save As.
- *In this case, we are assuming the user was able to track down the correct file. It is possible to download everything and sort after the fact, or perform analysis on the entire dump.
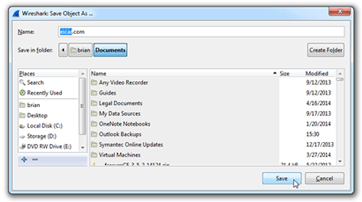
- We can then select a name for the file and click Save.
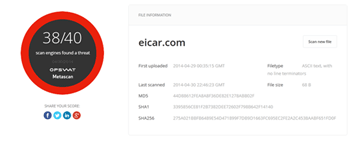
- You will now have an identical file to analyze, similar to had it been acquired from any other source. In this case we can upload the file to Metascan Online for scanning against 40 commercial anti-malware engines.
In the results, we can see that the hashes match up with what the eicar.com test file should be confirming that the file has been extracted properly and is detected as expected by the 40 available anti-malware engines. Another example performing the same steps with a Keylogger shows the following results. There are other tools which can be used for similar analysis such as NetworkMiner which automatically downloads all the objects when a PCAP file is opened.
Further investigating malicious files enables administrators to better understand what type of threats they are up against, allowing them to take the necessary steps to better protect their organization in the future.