OPSWAT in the News

OPSWAT and SentinelOne Enter OEM Partnership to Further Strengthen Multi-Layered Malware Detection with AI
The integration of SentinelOne®’s industry-leading AI-powered detection capabilities into OPSWAT’s MetascanTM Multiscanning technology elevates malware detection across platforms, empowering enterprises to combat modern cyber threats with even greater precision and speed.

Why Companies Must Solve the IT/OT Challenge
SANS Research found that IT and OT responsibilities are converging, but applying traditional IT security methods in OT can disrupt operations and cause safety risks. Organizations need to adopt cybersecurity practices tailored to modern critical infrastructure.
Why Document-Borne Malware Needs to Be Back on the Radar for Organizations
Document security often takes a back seat to network and endpoint protection, leaving a critical gap. Seemingly routine files can carry sophisticated threats that slip past standard defenses and put organizations at risk.

Beware the CyberAv3ngers
Iranian threat group CyberAv3ngers has targeted U.S. critical infrastructure by exploiting internet-exposed operational technology systems with weak security. Although their recent activity has declined, experts including OPSWAT’s Chief Strategy Officer Mike Arcamone warn they remain a persistent threat, evolving their tactics and possibly shifting to more covert operations.

Zero Trust Security is Transforming Cyber Defense in the Digital Age
As digital ecosystems expand and threats grow more sophisticated, organizations are embracing the Zero Trust model, which rejects the idea of a secure internal perimeter and requires continuous verification of all users and devices. Saif AlRefai, Solution Engineering Manager at OPSWAT, and other experts discuss why this approach is quickly gaining traction in the Middle East as businesses move away from legacy security strategies toward more proactive, adaptive defenses.

USB-basierte Angriffe: Wie Unternehmen diesem Sicherheitsrisiko begegnen
In this byline for German media outlet Datensicherheite.de, Holger Fischer, Director of Sales EMEA Central at OPSWAT, discusses the importance of realizing the threat of removable media to critical infrastructure and how to address it.
Check out our recent global and media coverage highlights at OPSWAT in the News and Press Releases to see how we are continuing our commitment to protect the world’s critical infrastructure.
Product Spotlight
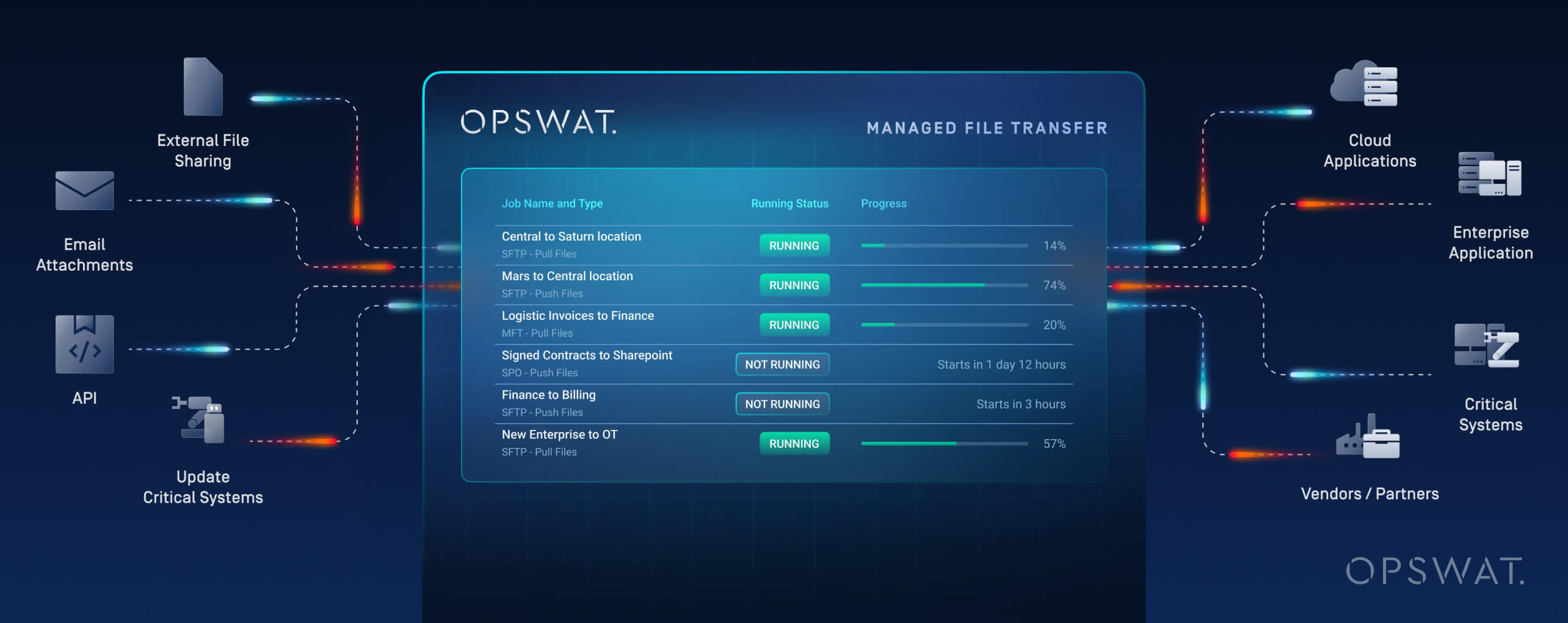
MetaDefender Managed File Transfer: Why Secure Managed File Transfer is Critical for Manufacturing in the Age of AI
Manufacturers are adopting AI to boost production, streamline design, and enable predictive maintenance—but all this depends on secure, efficient data exchange, which is exactly what this blog explores. Outdated methods like USB drives, ad hoc SFTP, and email attachments create serious security and visibility gaps.
Critical Infrastructure Resources

File Security Proven Deployments in Banking and Financial Services
This webinar explores how leading global financial institutions deploy file security solutions that work without compromising operational continuity.

Proven Deployments in Energy and Utilities
Struggling with downtime, audit pressures, and inconsistent security enforcement across energy sites? Join our webinar to discover real-world strategies successfully used by operators in nuclear, fossil fuel, and renewable energy sectors to strengthen OT security and stay ahead of evolving threats.

SBOM in 2025: A Strategic Asset, Not Just a List
The rising wave of software supply chain attacks has made SBOMs essential for ensuring transparency, integrity, and security across increasingly complex software ecosystems. This guide explains SBOM fundamentals, outlines new 2025 regulations, and offers practical steps for integrating SBOMs into your security strategy.
As a leader in critical infrastructure protection, OPSWAT brings innovative technologies and products to your existing security portfolio. Our solutions are available through our exclusive community of distributors and resellers across the globe. To locate a distributor or reseller in your region please visit our reseller locator.

