Over the last six months, malware complexity has jumped by 127%, according to OPSWAT’s 2025 Threat Landscape Report. With this increase, cybersecurity practices and compliance with regulatory cybersecurity frameworks have become more critical than ever. For many UK businesses, the Cyber Essentials certification is the foundational step in implementing robust cybersecurity defenses and strengthening their security posture.
What is the Cyber Essentials Certification?
Cyber Essentials is a UK government-backed certification scheme designed to help organizations protect themselves against common cyberthreats. It is recommended by the NCSC (National Cyber Security Center) as the minimum standard of cybersecurity. To comply with this scheme, five key technical controls are required:
- Secure Configuration: Ensuring systems are set up securely to reduce vulnerabilities
- Malware Protection: Defending systems against ransomware, spyware, and viruses
- Firewalls: Protecting internet connections to prevent unauthorized access
- Access Control: Managing who can access systems and data
- Security Update Management: Keeping software up to date with security patches

How MetaDefender Endpoint Supports Cyber Essentials Compliance
MetaDefender Endpoint is a comprehensive endpoint security platform that helps organizations comply with cybersecurity frameworks, including Cyber Essentials. It offers targeted capabilities to strengthen your cyber defenses and simplify compliance efforts.
1. Secure Configuration
Securely configuring devices minimizes exposure to vulnerabilities and unauthorized access. MetaDefender Endpoint offers comprehensive monitoring and configuration checks to ensure that critical endpoints comply with organizations' internal and external security policies and standards:
- Detects and remediates risky configurations in real time, such as disabled encryption or firewall
- Continuously evaluates endpoint risk posture based on enabled security controls and calculates a score for easy review and quick actions
- Automatically detects rooted or jailbroken mobile devices to ensure device integrity
- Provides visibility into the overall security health of devices at a glance
2. Malware Protection
Leveraging industry-leading technologies, such as Metascan Multiscanning™, MetaDefender Endpoint offers malware scanning with over 30 anti-malware engines, achieving detection rates of nearly 100%.
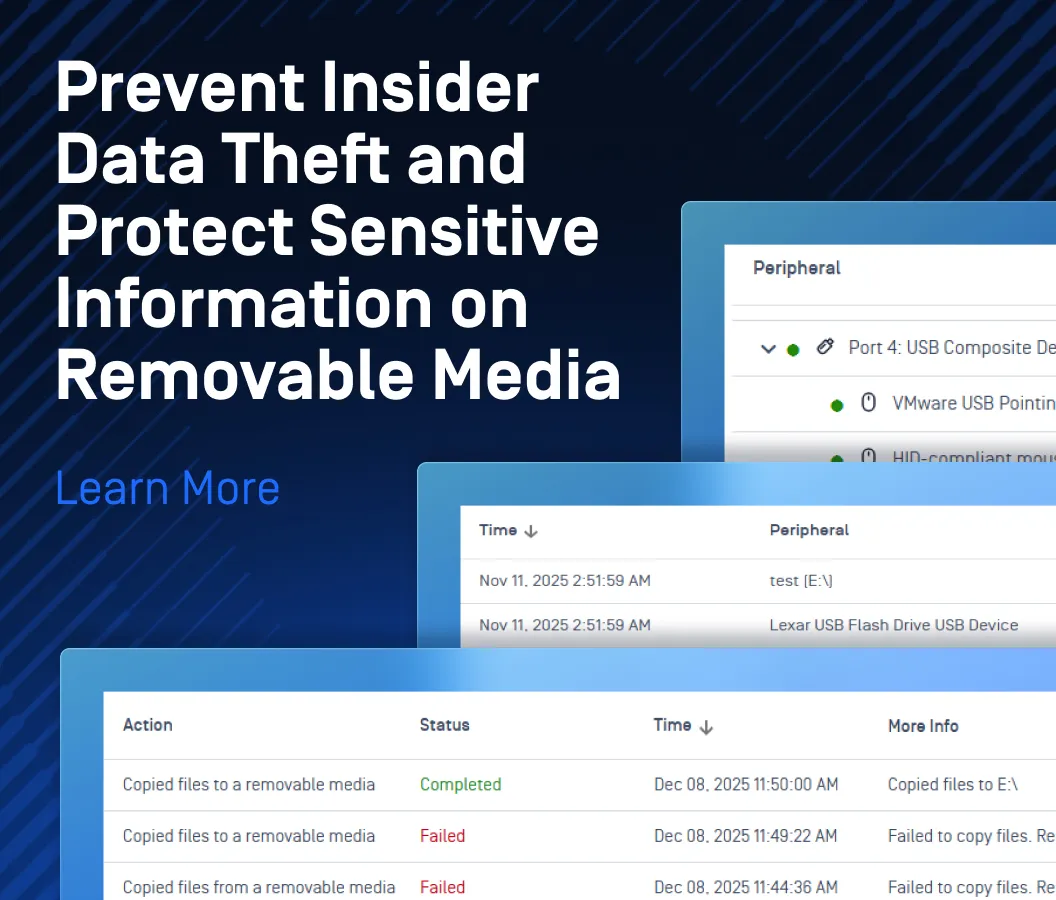
MetaDefender Endpoint offers peripheral and removable media protection by blocking access to removable media devices, such as USB drives, once they are inserted. This ensures that all removable media are thoroughly scanned and verified to be clean before being made accessible to the system.
With the Deep CDR™ Technology, MetaDefender Endpoint sanitizes files to neutralize unknown threats, including zero-day exploits. It also actively scans files and applications for known vulnerabilities, utilizing 3 million data points and 47,000 associated CVEs with the File-Based Vulnerability Assessment technology.
Moreover, MetaDefender Endpoint provides enhanced visibility into the security posture of mobile devices by monitoring and detecting whether a mobile device has at least one recognized mobile security or anti-malware application installed, which is critical for Cyber Essentials compliance.
3. Firewalls
Firewalls serve as a critical first line of defense, blocking unauthorized access to systems and networks. To quickly identify endpoints with disabled or misconfigured firewalls, MetaDefender Endpoint enables monitoring and verifying firewall status across all devices. This level of visibility enables organizations to better identify vulnerabilities and respond more quickly to firewall-related incidents.
4. Access Control
Access control ensures that only authorized users and compliant devices can connect to critical systems and data. MetaDefender Endpoint enhances access control by verifying device compliance, ensuring each endpoint meets security requirements and policies before granting access.
Organizations can also manage the use of peripheral media devices with granular policies and controls to prevent any unauthorized access to critical environments. In addition, SDP and VPN capabilities provide zero-trust network access, protecting connections from the endpoint to the cloud and legacy applications.
The remote wipe capability enables administrators to remotely erase sensitive information from mobile devices. This feature helps protect confidential data when a device is lost, stolen, off-boarded, or intentionally quarantined.
5. Security Update Management
With robust vulnerability detection and patch management capabilities, MetaDefender Endpoint keeps systems and applications up to date, detecting and remediating vulnerabilities before they can be exploited. It continuously scans endpoints to identify missing security updates, outdated software, or unpatched components, providing actionable insights into each device’s patch status and overall risk posture.
MetaDefender Endpoint supports vulnerability detection for over 900 third-party applications and delivers patching for more than 1,100 applications. It also supports:
- Air-gapped Patching: Support patching in air-gapped networks for enhanced security
- Flexible Patch Scheduling: Schedules patch rollouts at specific times for greater control and flexibility
- Reboot Schedule Control: Schedules device restarts at specific times when a patch requires a reboot
- Installed Patch History: Enables clear visibility over all installed patches per device, helping users stay informed and compliant
- Patch Management Admin Audit: Centralizes recording of all patch actions for transparency, security, and compliance support
Why Choose MetaDefender Endpoint?
- Centralized Management: Manage all endpoints from a single management console using My OPSWAT™ Central Management, making it easier to enforce security policies
- Proven Technologies: Comprehensive endpoint protection, powered by industry-leading technologies and patch management capabilities
- Scalability: Meet security needs for small, medium, and large enterprises
- Compliance Aid: Designed with regulatory compliance in mind, including Cyber Essentials
- Expert Support: Access to OPSWAT’s customer experience team, which continuously provides support and helps with deployment and optimization to meet different environmental needs.

Final Thought
Compliance with Cyber Essentials is a critical step to strengthen the cybersecurity posture for UK-based organizations. MetaDefender Endpoint helps better manage device security posture and compliance through secure configuration, malware protection, firewall monitoring, access control, and update management.
Talk to one of our experts today to learn how MetaDefender Endpoint can safeguard your organization's endpoints to help align with the essential controls of the Cyber Essentials certification.