Summary
In July 2021, there was a sophisticated cyber intrusion utilizing a link to Google’s Feed Proxy service to download a harmful Microsoft Word file to the victims’ device. Once the macros were innocently enabled by users, a Hancitor payload dynamic-link library (DLL) was executed and called the ubiquitous Cobalt Strike tool, which dropped multiple payloads after profiling a compromised network. Within an hour, the attacker can gain domain admin privileges and full control over the domain. In this blog, we describe how OPSWAT Multiscanning solution - Metascan and Deep CDR (Content Disarm and Reconstruction) found the potential threat and prevented this advanced attack.
The Attack
Like many cyber-attacks nowadays, the intrusion started with a spear-phishing email to one or more users in the target network. We’re familiar with attack tactics using hidden macros in files to download malicious payloads. This attack is even more evasive and sophisticated as the embedded macro doesn’t download the payloads directly, but it extracts and runs a shellcode (OLE object) inside the document to download the harmful payloads.
A Microsoft Word document with malicious macros capable of installing embedded copies of the Hancitor trojan downloader[1] was sent to the users. When the users opened and enabled the concealed macros in the file, it wrote and executed a DLL file from the victims’ appdata folder. Then the Hancitor DLL downloaded and delivered various payloads containing Cobalt Strike[2] and Ficker Stealer[3].
How OPSWAT can help you prevent this advanced attack
Scanning the malicious MS Word file with OPSWAT MetaDefender, only 17/35 anti-virus engines found the threat. This is definite evidence that scanning with a single or a few AV engine(s) is not enough to protect your organization and users. Advanced malware with evasive tactics can bypass traditional defenses. A single antivirus engine can detect 40%-80% of malware. OPSWAT Metascan allows you to quickly scan files with over 30 anti-malware engines on-premises and in the cloud to achieve detection rates greater than 99%.
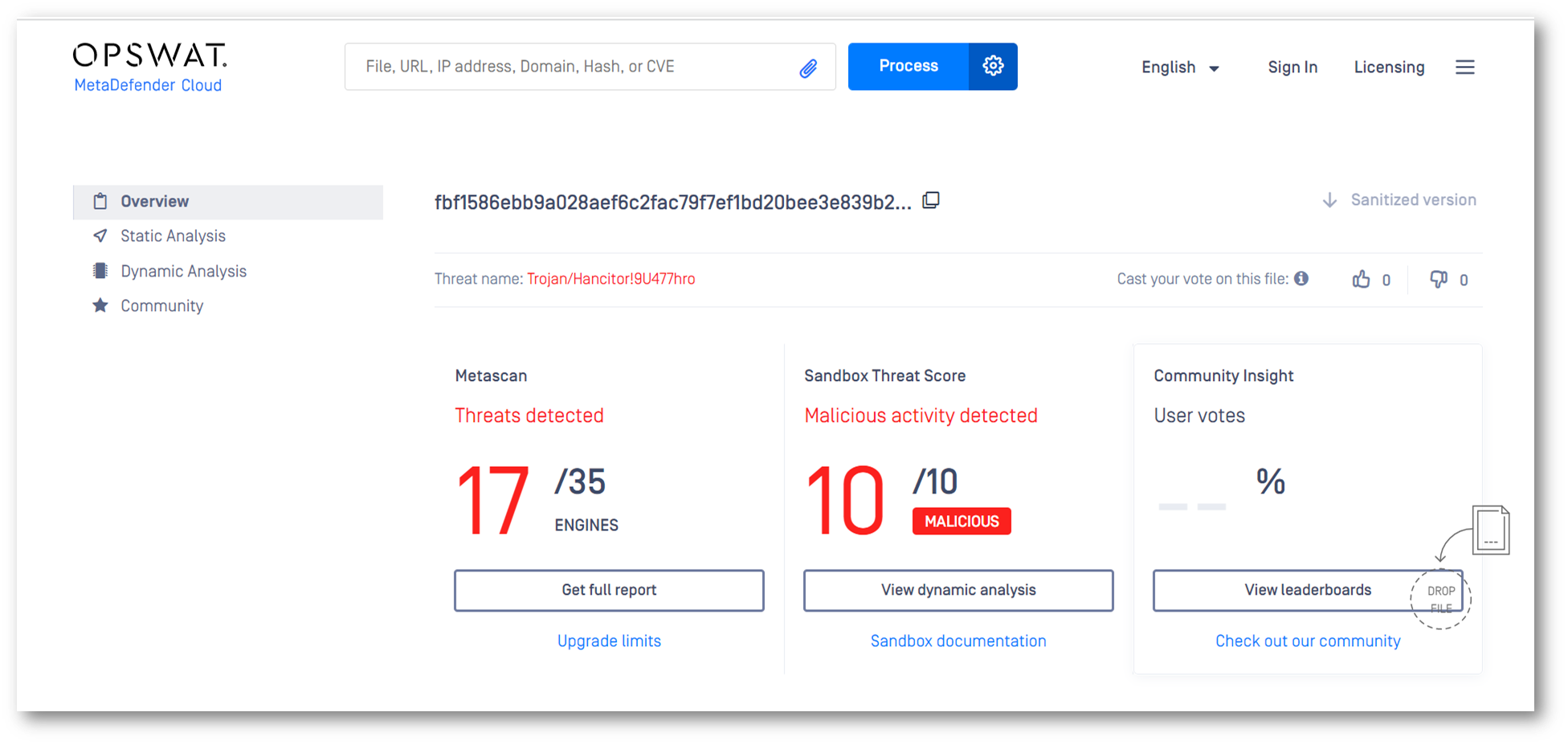
However, the best approach to ensure your organization and users are protected from sophisticated and zero-day attacks is to sanitize all files with Deep CDR. Files are evaluated and verified as they enter the sanitization system to ensure file type and consistency. Then, all file elements are separated into discrete components and potentially malicious elements are removed or sanitized. By providing a detailed sanitization report, Deep CDR also enables administrators to analyze the malware behavior without any additional analysis tool. We demonstrate hereunder how Deep CDR removed all potential threats in the file and provided a safe-to-consume file to users.
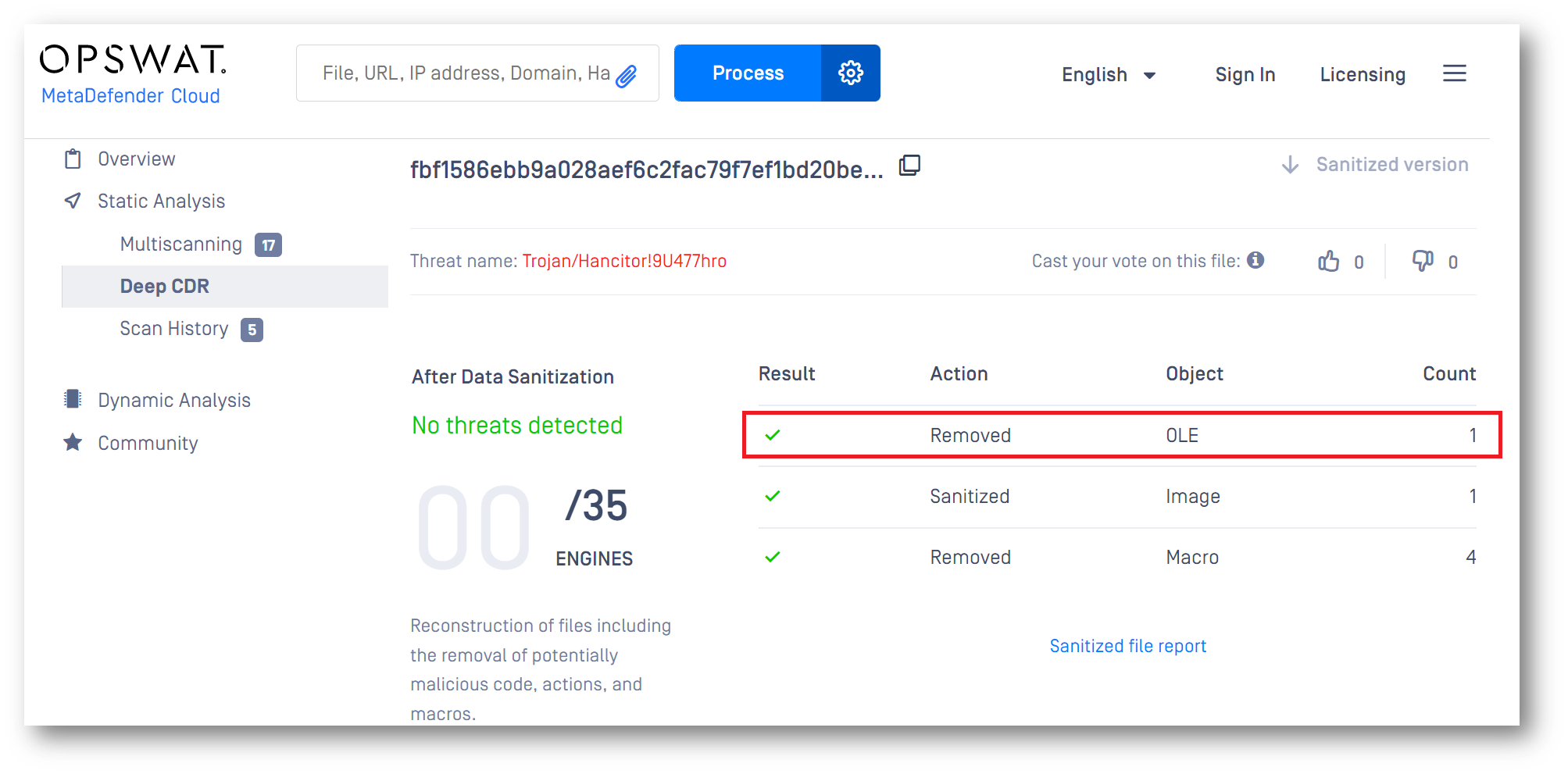
Processing the malevolent Word document with Deep CDR, we found several active components, including an OLE object and four macros. We deobfuscated the code and saw that it tried to run (C:\Windows\System32\rundll32.exe C:\users\admin\appdata\roaming\microsoft\templates\ier.dll,HEEPUBQQNOG).
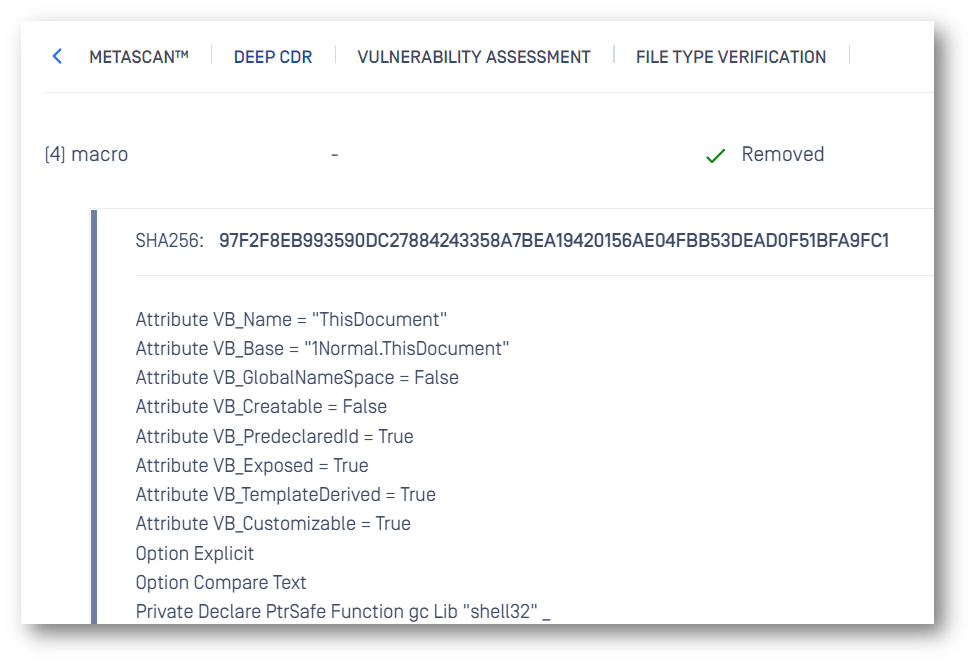
As shown in the sanitization result, all active content in the document was removed from the file. One of the embedded objects (the OLE object) would install the Hancitor trojan (ier.dll file) to the users’ machine (once they unintentionally activated it) if it wasn’t neutralized before reaching them.
To protect their network, it’s vital for any organization to make sure that all files/ emails sent to their internal employees are safe, while simultaneously assuring file usability. We deliver safe files with maximum usability within milliseconds, so your workflow is not interrupted.
By sanitizing each file and removing any potential embedded threats, Deep CDR effectively ‘disarms’ all file-based threats including - known and unknown threats; complex and sandbox aware threats; and threats that are equipped with malware evasion technology such as Fully Undetectable malware, VMware detection, obfuscation and many others.
Learn more about Deep CDR or talk to an OPSWAT technical expert to discover the best security solution to prevent zero-day and advanced evasive malware.
1. Hancitor is a malware downloader that opens ‘backdoors’ for other viruses to infiltrate.
2. Cobalt Strike is a remote access tool that has been co-opted by cybercriminals to deliver follow-up malware.
3. FickerStealer is an information-stealer malware designed to extract sensitive information.

