The Growing Concern with Power Grid Cyberattacks
The threat of cyberattacks that can lead to a total shutdown of critical infrastructure facilities or entire power grids isn’t just speculation. Events like the 2015 Ukraine power grid hack, which left nearly 230,000 people without electricity, and the 2016 cyberattack on Kyiv's transmission station, which plunged parts of the city into darkness, highlight the devastating potential of such breaches.
Besides power grids, other critical infrastructure facilities are constantly at risk of cyberattacks. For instance, the Colonial Pipeline hack (2021) was considered a national security threat and led to the declaration of a state of emergency. This incident was caused due to a leaked password.
Challenges with Securing Transient Devices
The air-gapped renewable energy sites and the remote control centers operated by our client required constant access from transient devices. These devices included third-party vendor laptops and internet-connected company employees’ laptops. The company had a set of internal compliance rules for vendors' and employees' laptops that included installing a specific live AV (antivirus) scanning solution on the transient devices. Using such solutions to scan vendors’ devices before using them in secure zones wasn’t sufficient to detect certain types of malware that can be well disguised. The security of the remote employees' personal devices was also a matter of concern since many control center employees were permitted to use their own devices while working remotely.
Introducing Bare Metal Scanning to Secure Renewable Energy Supply Chains
Prior to implementing MetaDefender Drive into their existing cybersecurity operations, the live AV scanning solutions used by our client included a single antivirus engine. In addition, these live scanners ran their scans after booting the device’s operating system, giving certain types of malware the ability to avoid detection. The incorporation of bare metal scanning, the ability to detect files with sensitive data, and the ability to scan hidden areas, such as boot sectors, were fairly new to the organization’s cybersecurity procedures. As a result, an initial 3-month pilot was conducted in one of the company’s wind power facilities, with a new policy to perform a bare metal scan on every transient device entering the facility. The aim of the pilot was to decide how MetaDefender Drive could be utilized within the company’s cybersecurity operations.
| Category | Scanned Area | Typical Malware Classification(s) Detection | MetaDefender Drive | Live Scanning |
| User Space (applications and data) | Applications files User files Services patches | Macro Spyware Trojan Horse Exploit | ||
| Kernel / OS | Deep OS / Kernel | Binary Rootkit Kernel Rootkit Rootkit Library Rootkit Database Rootkit Kernel Patches Backdoor Stealth Virus | Partial | |
| Hypervisor Kernel | VM Kernel and OS | Rootkit of VMDK or VHDX | Partial | |
| PSR | Partition Boot Sector Record | Boot Virus | ||
| MBR | Master Boot Sector Record | Boot Virus | ||
| EUFI / BIOS | EUFI and BIOS partition sector | Boot Virus | ||
| Device Hardware | EPROMs FPGAs NICs Storage controllers | Embedded Programmable Bit Streams or Drivers | ||
| Global Use Case | Supply Chain Security | Identify Country of Origin for Embedded Hardware |
The ability to run bare metal scans and to detect files that include sensitive data enabled us to mitigate various cybersecurity risks, including early malware detection and preventing sensitive data leakage.
IT Security Operations Manager
Enhancing the Defense-In-Depth Strategy and Increasing the Malware Detection Rate

After the three months, MetaDefender Drive had a significantly higher detection rate than the previous solution. The main concern was the slow process of scanning devices using MetaDefender Drive and another AV scanning solution. However, it was only needed during the three-month pilot to validate the deployment of MetaDefender Drive as a robust security protocol that can replace the need for a single-engine solution.
The high increase in the malware detection rate led to relying on MetaDefender Drive as the primary scanning solution for transient device safety. To optimize the scanning process performance, the requirement to use a live AV scanning solution to scan a transient device was abolished at the pilot location, but the requirement to have it installed remained. The deployment of MetaDefender Drive was seen as a major enhancement to the company’s defense-in-depth cybersecurity strategy and a major leap forward in their supply chain security posture.
Strengthening BYOD Security
The organization had an established BYOD policy enabling employees to perform specific duties remotely using their own devices. The policy granted personal devices access to some of the organization’s critical systems. According to the BYOD policy, those devices were advised to be periodically scanned on-premises.
With the introduction of MetaDefender Drive into the organization, another layer of defense was added to its BYOD policy. It has become a requirement to perform monthly or bi-monthly on-premises scans, depending on the remote employee’s schedule, on every device granted remote access to the company’s internal systems.
MetaDefender Drive’s ability to detect files with sensitive data and Proactive DLP™ technology have proven to be a crucial enhancement to the company’s BYOD policy. The deployed configuration with 7 malware scanning engines has been tested and validated to achieve an 88.9% malware detection rate, offering a significant improvement over single engine anti-malware solutions.
The number of sensitive data leakage and malware threat detection we have addressed after using MetaDefender Drive was beyond the capabilities of any scanning software we used in the past.
IT Security Operations Manager
Future Expansion of MetaDefender Drive Applications
Following the company-wide satisfaction with the pilot results and the initial success of the BYOD policy enhancement, a decision has been made to expand the deployment of MetaDefender Drive to 26 additional locations across its global operations within 2 months. In addition, further considerations have been made to utilize more of MetaDefender Drive’s capabilities, particularly, the Country of Origin detection.
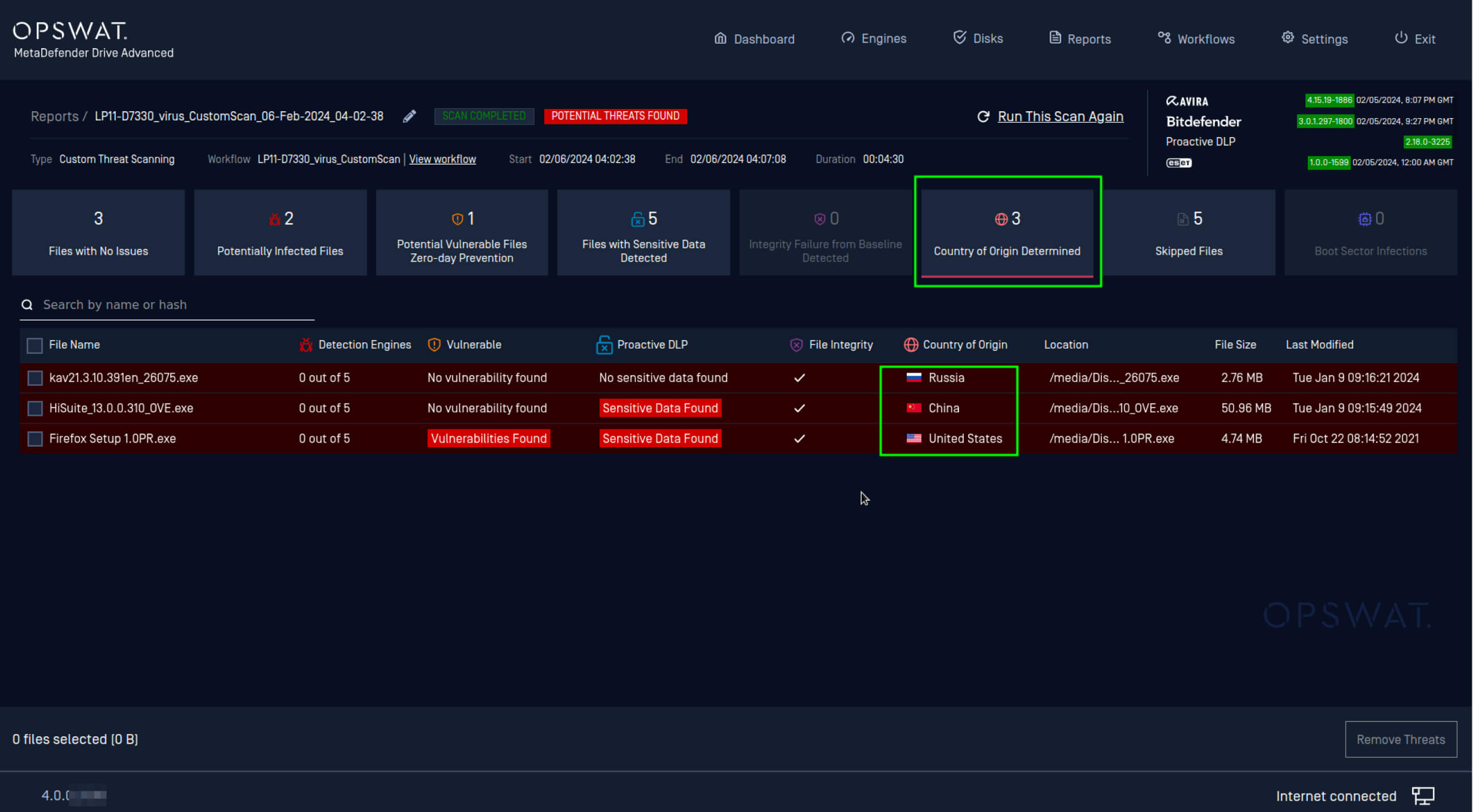
Our client was actively seeking a solution that could detect the origin and the authenticity of the transient devices’ software and firmware. Country of Origin detection is crucial to ensure that the organization isn’t directly or indirectly dealing with a sanctioned entity. Since MetaDefender Drive was used effectively to identify these critical details, its use has been expanded to be the main Country of Origin detection solution in future deployments.
To learn more about how OPSWAT can protect your critical infrastructure and discover more about MetaDefender Drive’s capabilities, reach out to an OPSWAT expert today.





