Keeping the same usability while stripping out unexpected objects is one of the most challenging tasks in the CDR process. Especially, in the email use case, a phishing email usually includes a malicious hyperlink, however, a normal email also contains many hyperlinks. Keep or remove them? It's a hard question to answer, it depends on several things such as company policy, what protection solution they have. So, flexible CDR configurations are necessary for an administrator.
In this release, Deep CDR 5.7, we are proud to announce that we've added three more options to HTML sanitization with respect to hyperlinks.
We also improved sanitization details for malware analysis use case, the module now returns the entire macro content and the URLs that were excluded from the sanitized file. A new UI configuration is also available in this version. Last but not least, we added support for four new filetypes.
New Configurations to Sanitize Hyperlinks in HTML
Return Hyperlinks Without Processing Them
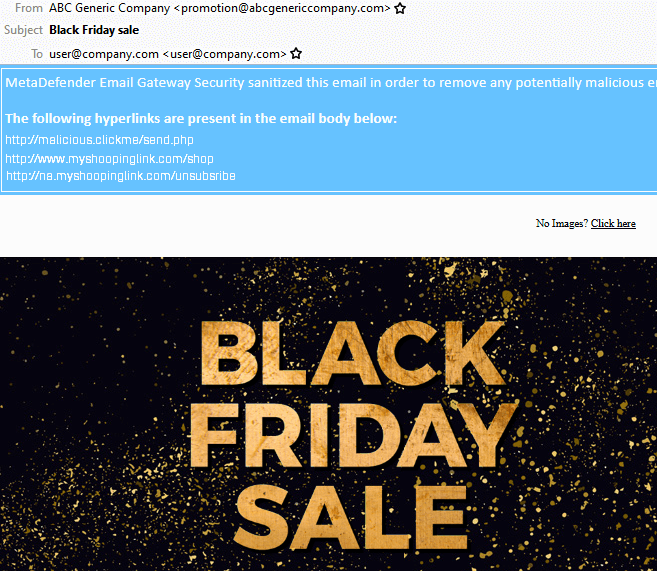
When you enable this option, the hyperlink will not be sanitized, however the Deep CDR will return the list of available links in sanitization details. Therefore, this option will have no impact on email usability. but will provide visibility on the content of the email. A phishing email can now be identified easier by 'weird' links. This is an example with OPSWAT MetaDefender Email Security Gateway integration
Replace with Text
This is a simple option, but gives the highest security to users. All hyperlinks will be replaced by a static text, this text is set through Deep CDR configuration. For example, "Please click here to contact us" will become "Please click [A hyperlink was removed] to contact us". However, even though this option removes entirely the risk, this will create the highest discomfort for the users, since all hyperlinks (even non-malicious) will be removed.
Redirect the URL to the URL inspection service for time-of-click analysis protection
This option is the best choice when you have a URL scanning service. Deep CDR will add a prefix hyperlink to current hyperlinks. When the user clicks on a hyperlink, your inspection service will scan the link and redirect them to the original URL. From the users' perspective, they don't recognize any change in the sanitized file/email. This is an example when integrating with MetaDefender Cloud Safe URL Redirect:
Original: "Please click here to contact us"
Sanitized: "Please click here to contact us"
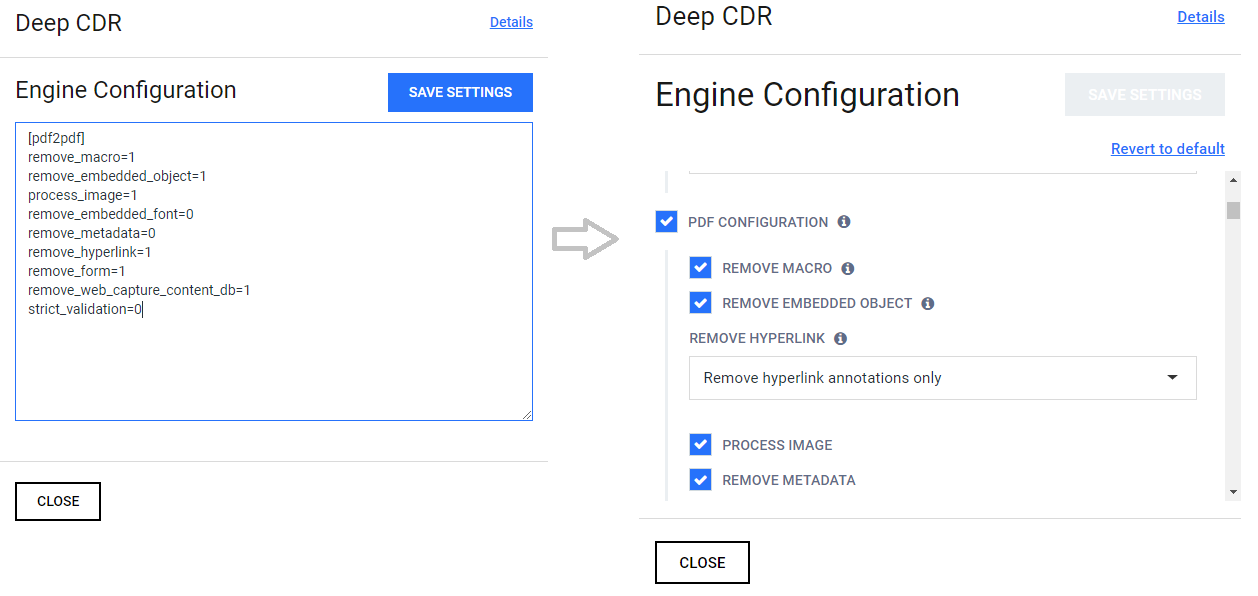
Easy to Configure
The current INI base configuration doesn't provide the best experience and can result even in frustration: it can cause many typos, wrong configurations, have to remember names, values etc. We understand the pain, so, Deep CDR configuration now can be done through the UI. No copy-paste, no need to remember, just tick and save, everything is in the UI!
Deep CDR Details
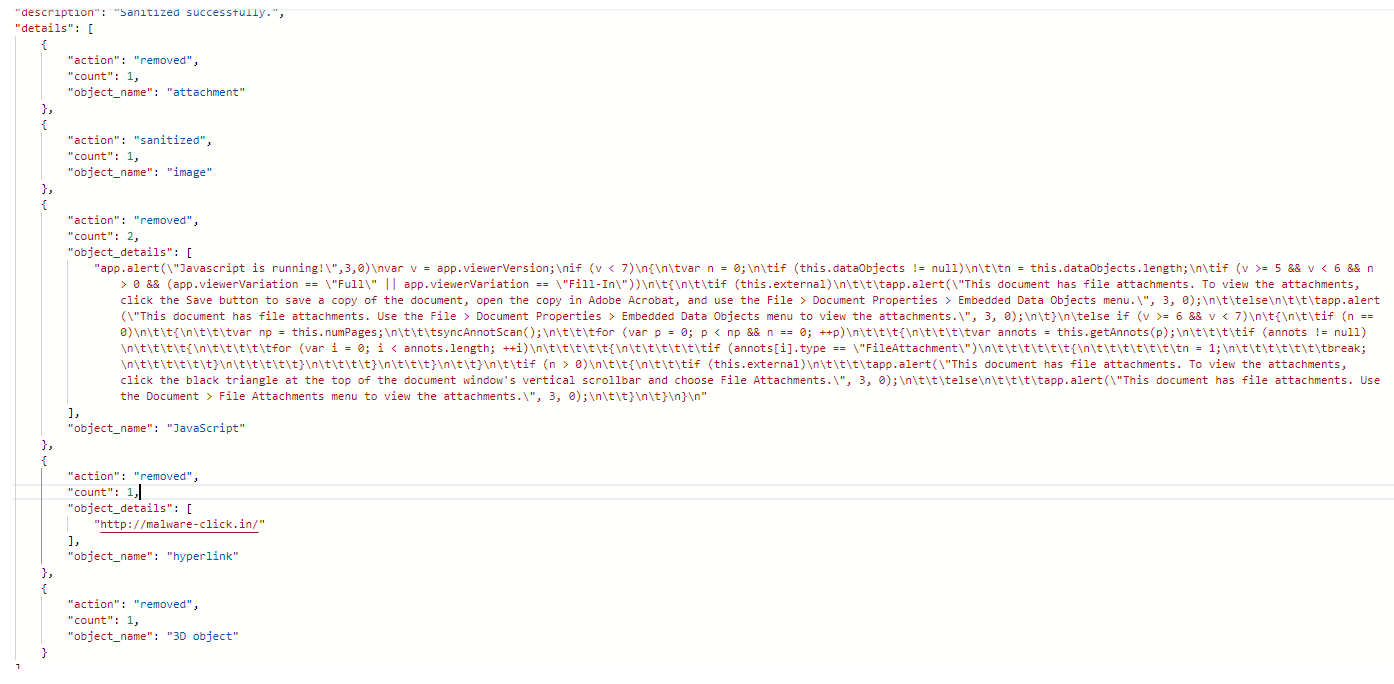
The Deep CDR details were introduced from DS 5.2.7, this feature was improved in every release to cover more file types and object types.
In this release, we extend the information to have more details about the sanitized objects. You will be able to consume the scripts (VBA Script Macros, Javascript in PDF, etc. ), but also a list of all hyperlinks that are in the original file (regardless of the sanitization method selected). This information will provide a better report with respect to the potential malicious intent of the file and will fasten any analysis, or decision to release original file.
Newly Supported File Types
- Icon file format (.ico)
- Cursor file format (.cur)
- Hancom Cell (.cell)
- Hancom Show (.show)

