Protecting Critical OT
& Cyber-Physical Systems
Enabling resilient, smarter and safer operations with comprehensive, industrial security solutions.
10,000+Assets Protected
The World's 1st & ONLY Fully-Integrated
Cybersecurity Platform developed exclusively
for Critical OT & CPS
100+Industrial Protocols
Active Protection Against Misuse
and Misconfigurations
Easy Deployment in 15 Minutes
Seamless Integrated and Virtual
Patching
Suitable for All Industries and
Environments
The Cyber-Physical Kill Chain
Explore the interactive diagram to see how OPSWAT can help disrupt the cyber-physical kill chain.
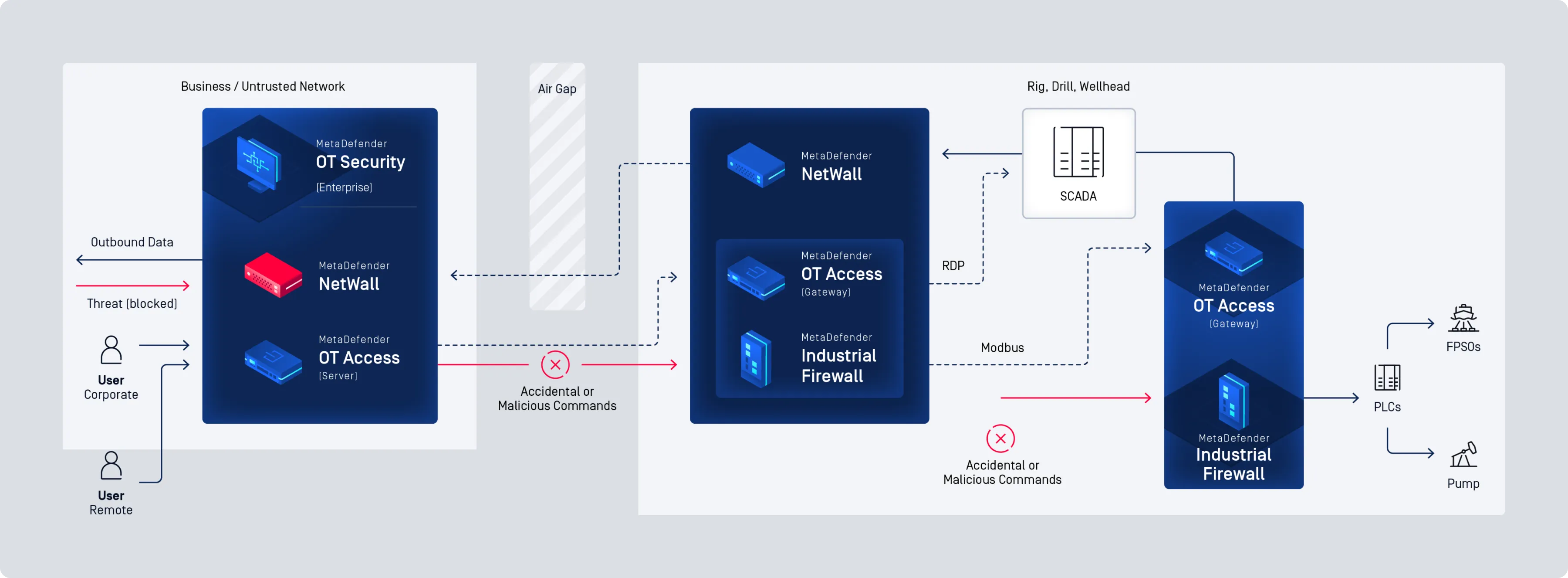
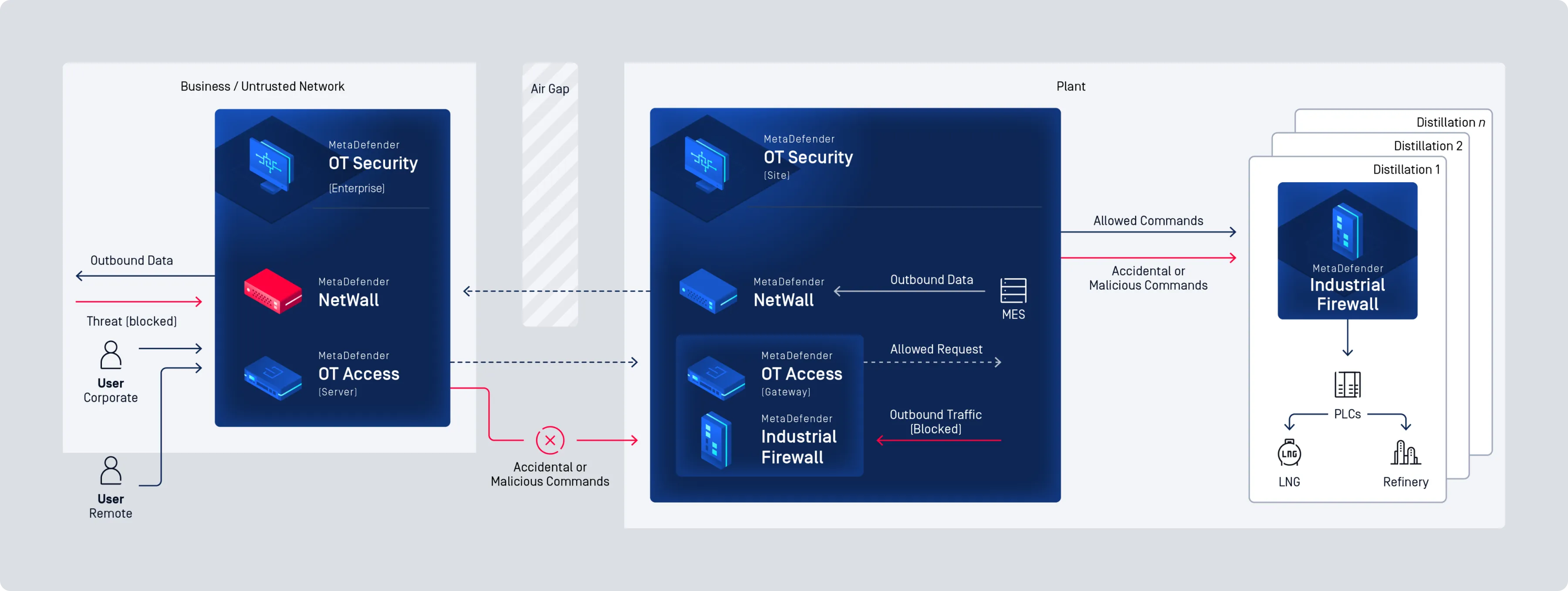
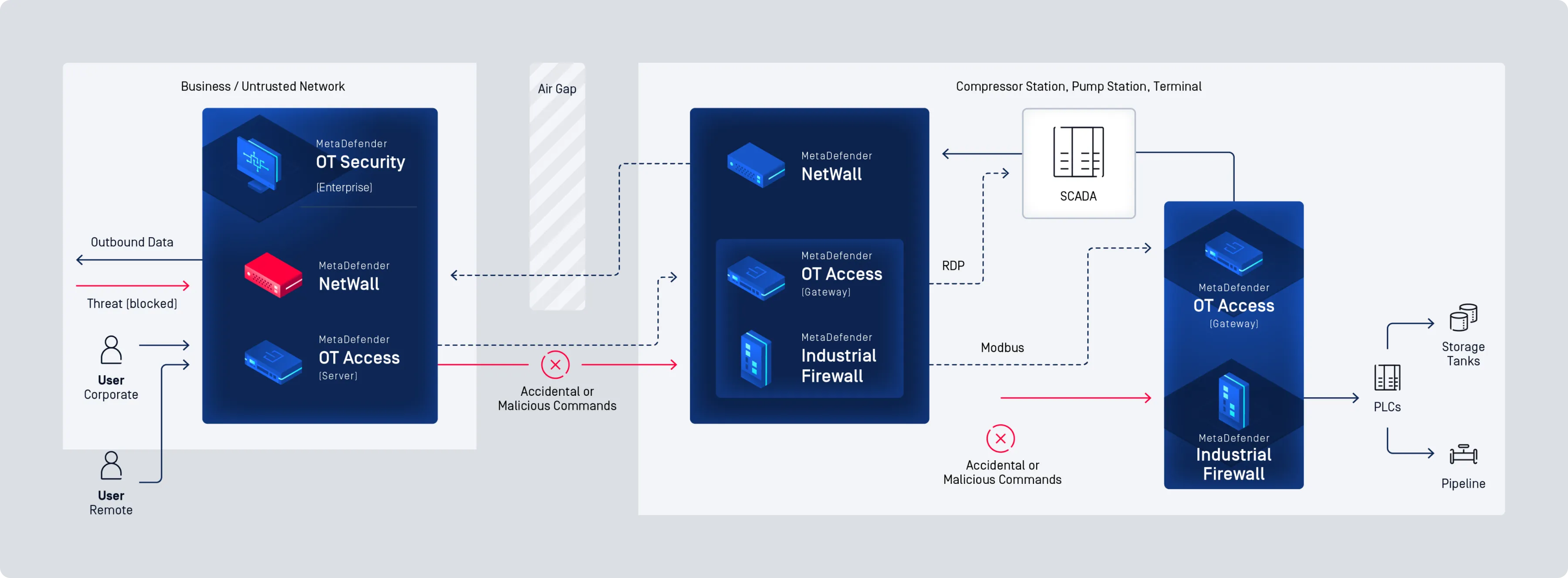
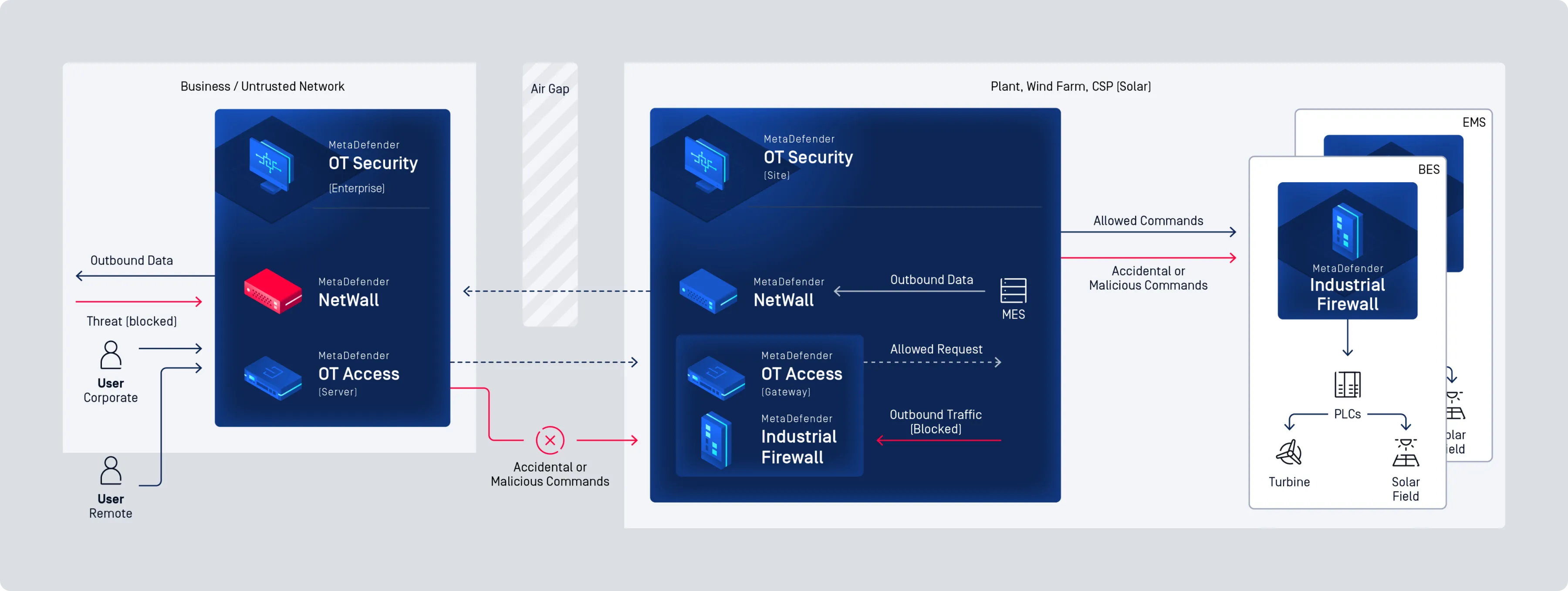
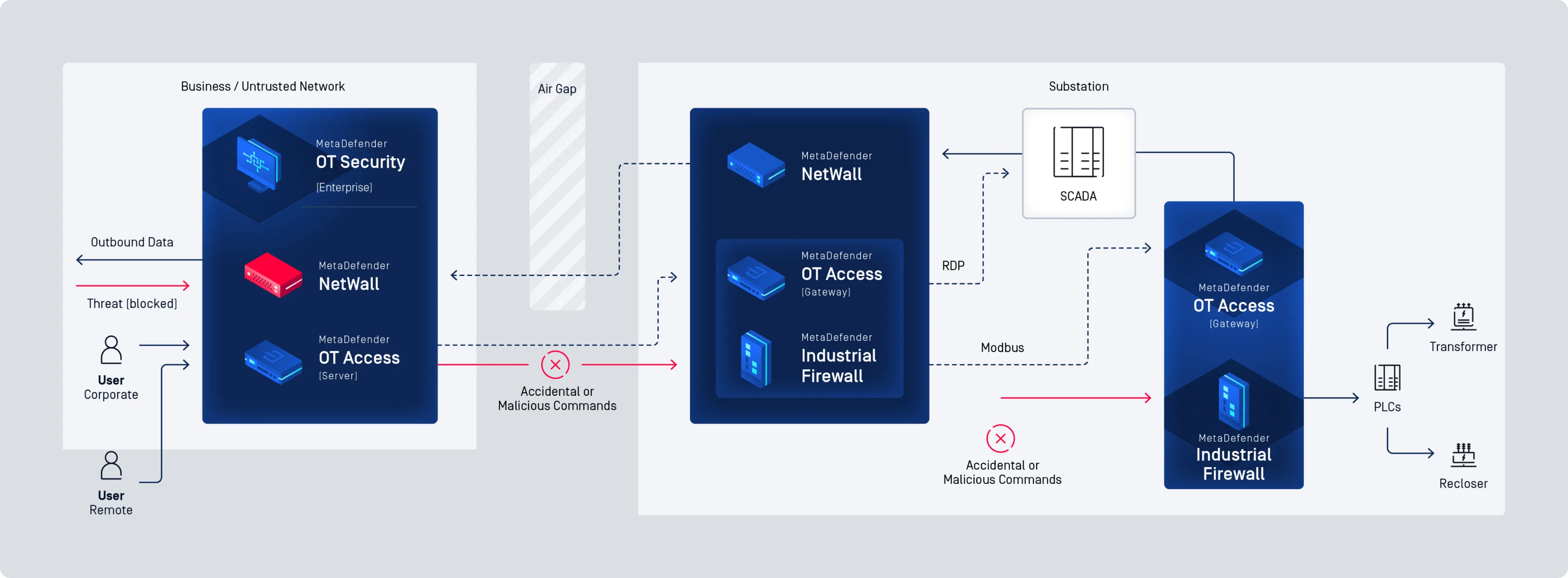
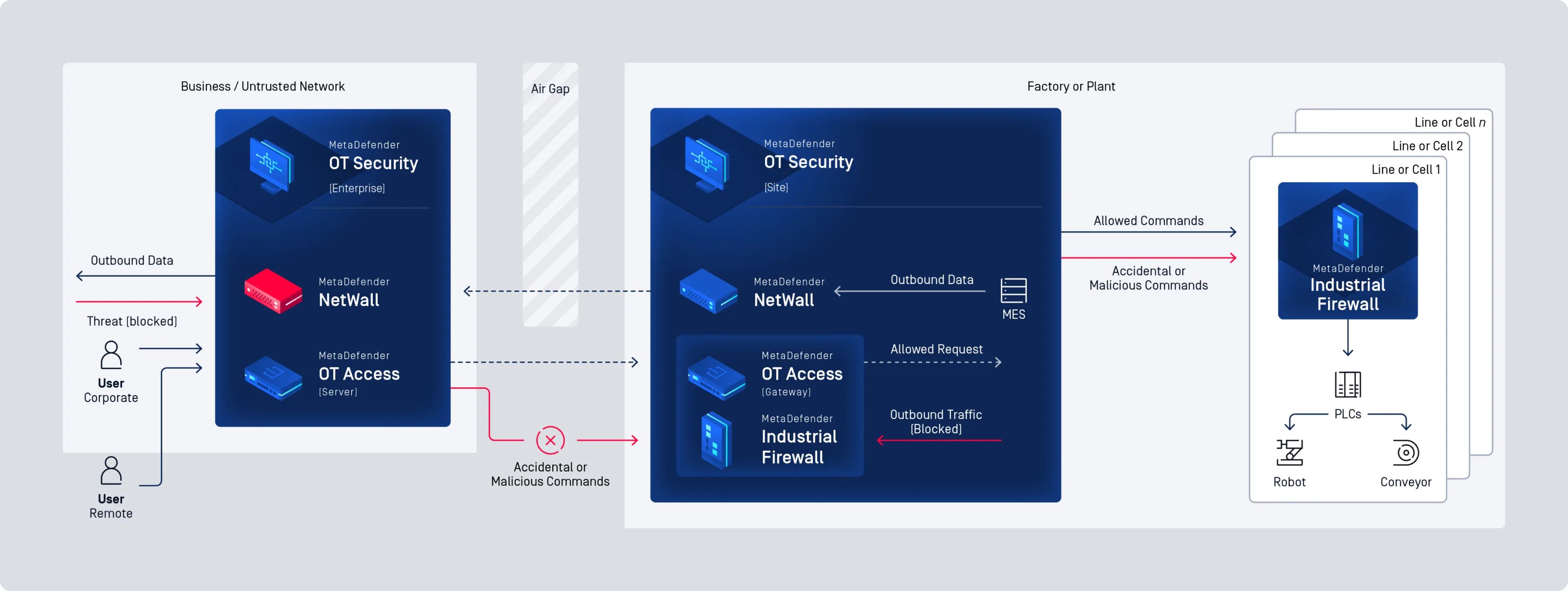
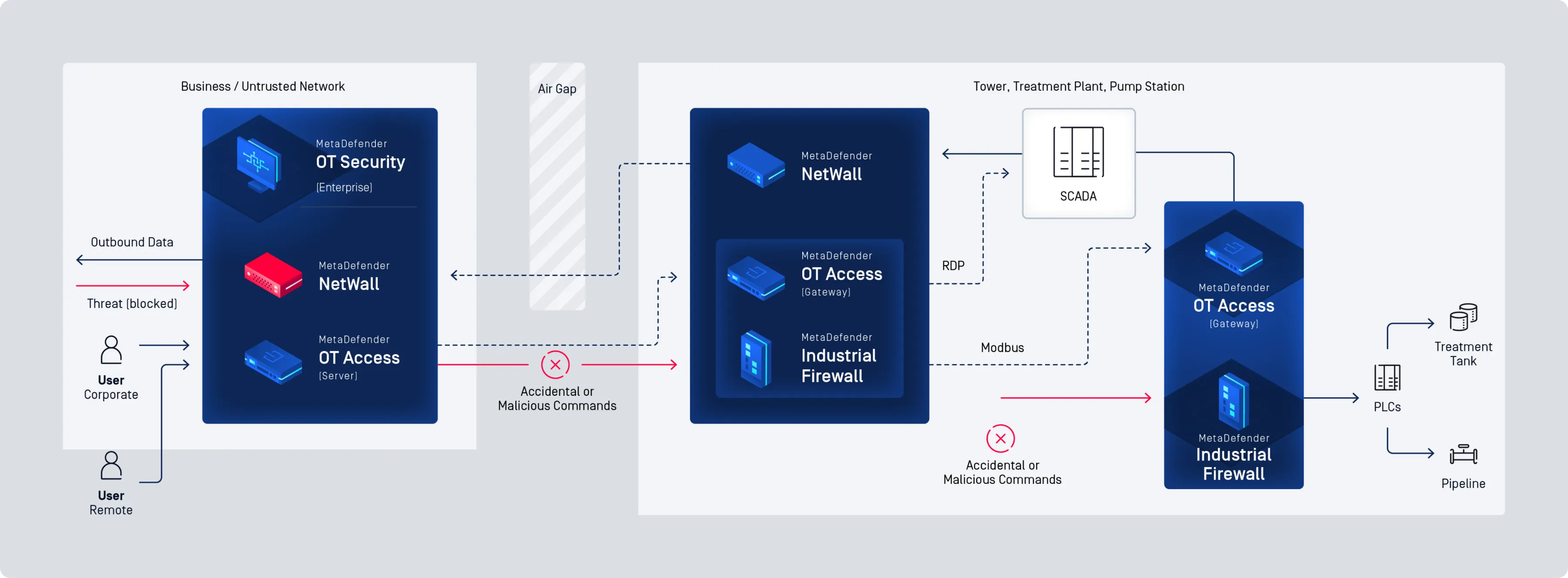
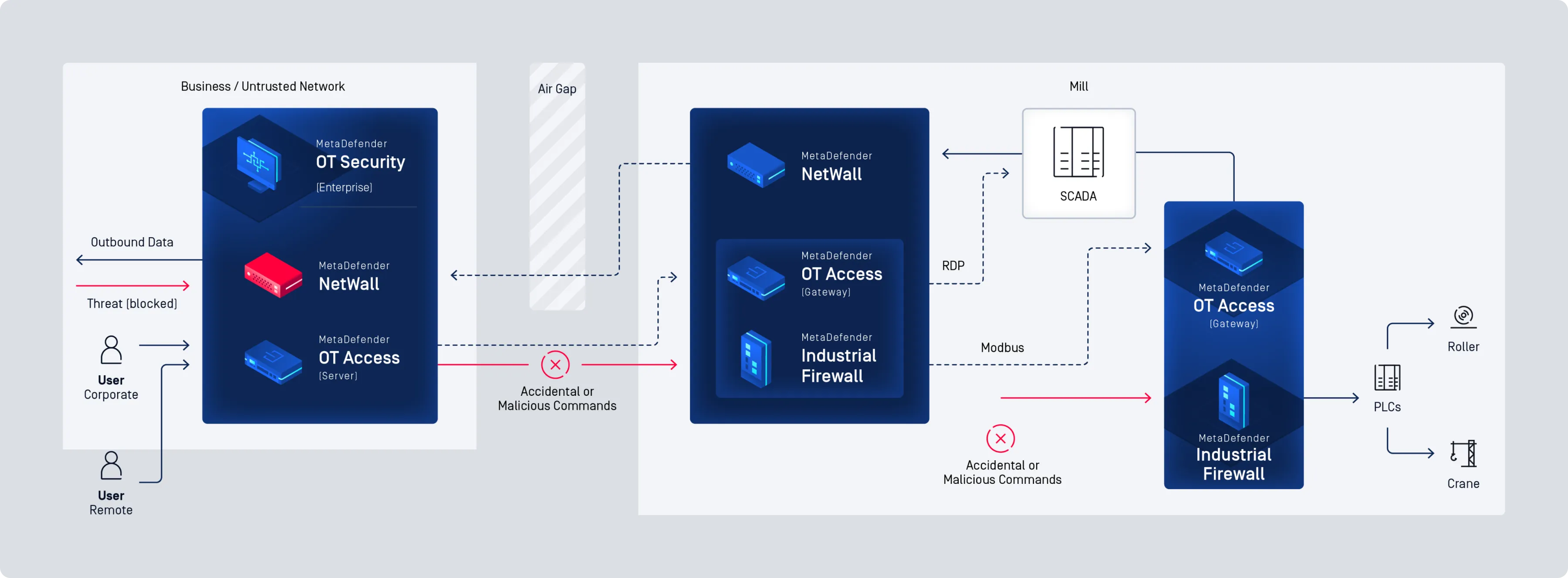
Secure Your OT Environment with Comprehensive, Industry-Leading Cybersecurity
MetaDefender OT Security
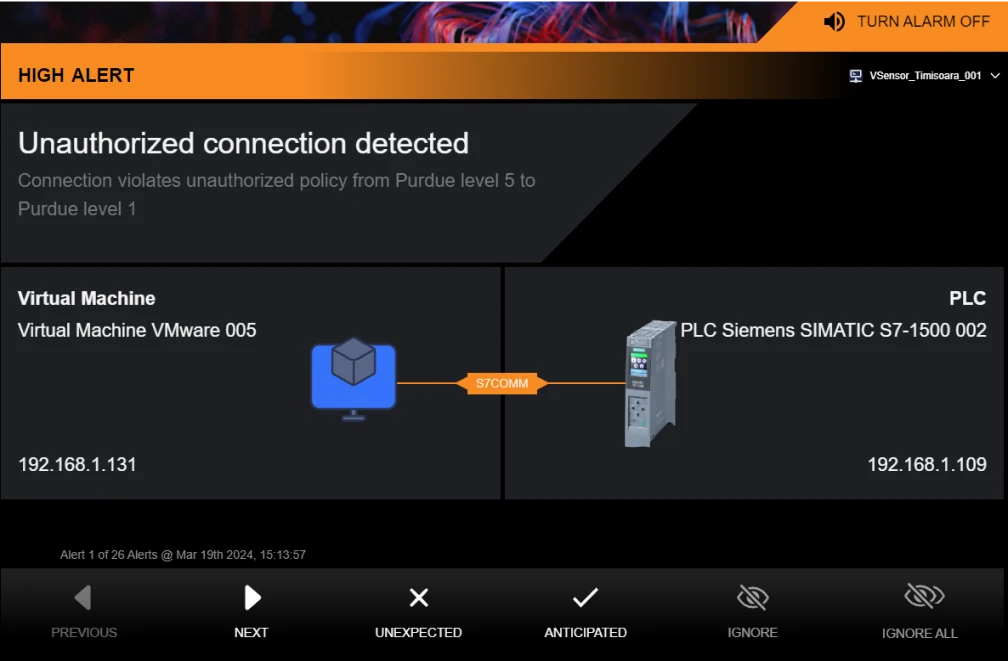
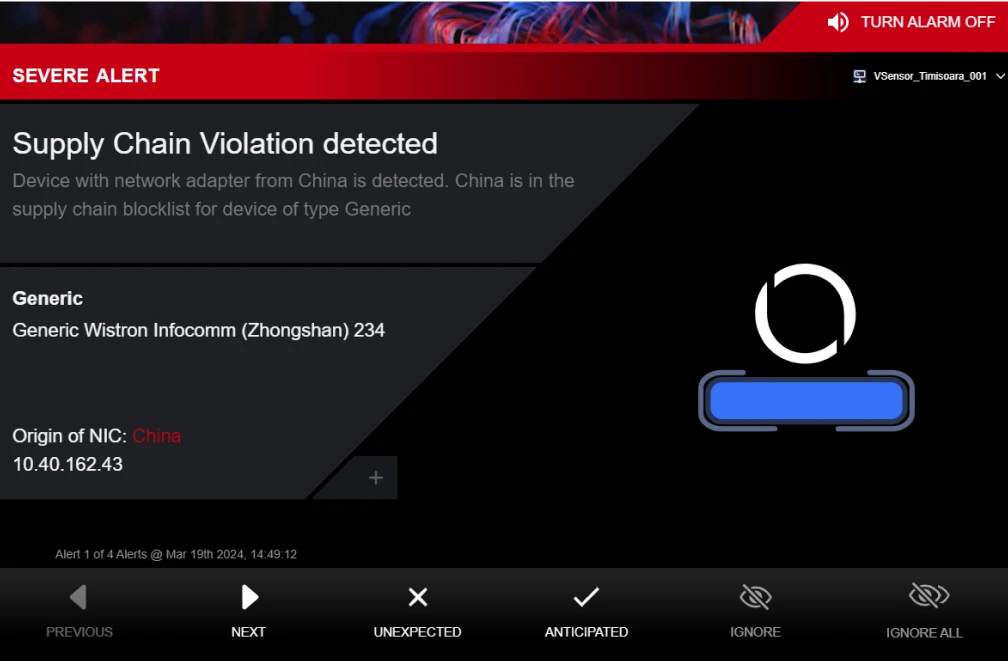
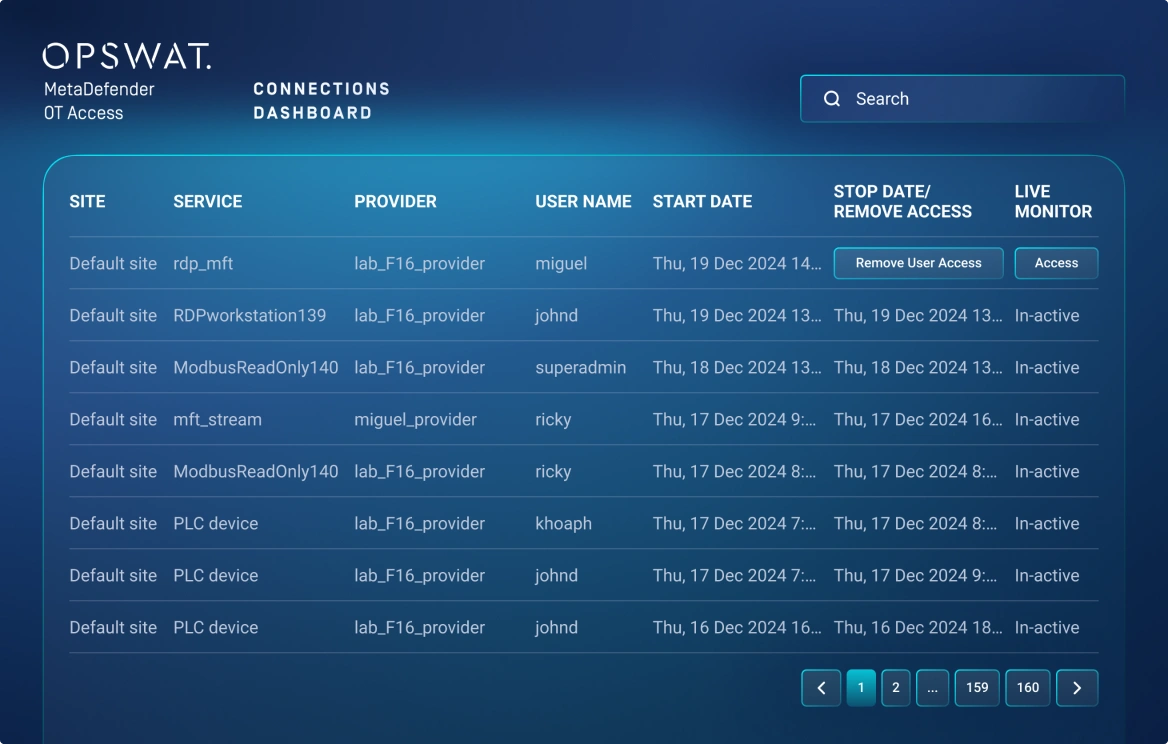
Cross Domain and Network Perimeter Security
Easy Deployment, Even in the Harshest Environments
Solutions That Speak Your Language
Our frontline OT solutions offer a wide coverage of industrial protocols like BACNet, EtherNet/IP, Modbus, S7COMM, GE Proprietary protocols, Profinet, DNP3, Common IT protocols and many more.
Protocols coverage for:
- Smart Discovery
- Network Monitoring
- Active Protection
- Full Deep Packet Inspection and Function Code Exposition
OT & Cyber-Physical Systems Protection that Helps You Stay Compliant
With continuous network monitoring, in-depth asset inventory, secure data transfers, active network protection, and intuitive remote access control, our OPSWAT OT and CPS security solutions help your organization stay ahead of regulatory requirements. This proactive approach not only mitigates the risk of cyber incidents but also safeguards operations, reputation, and the bottom line, while avoiding potential legal and financial repercussions in the evolving OT landscape.