Advanced Malware Detection Module
The OESIS Framework Malware Detection module uses process scanning, connection scanning, and repeated threat reporting to provide an additional layer of security for the endpoint. This module complements protection provided by anti-malware applications installed on the endpoint and provides a fall-back check for devices not complying with security policies and regulations of the end user organization, for example not having an enabled and up-to-date anti-malware application installed.
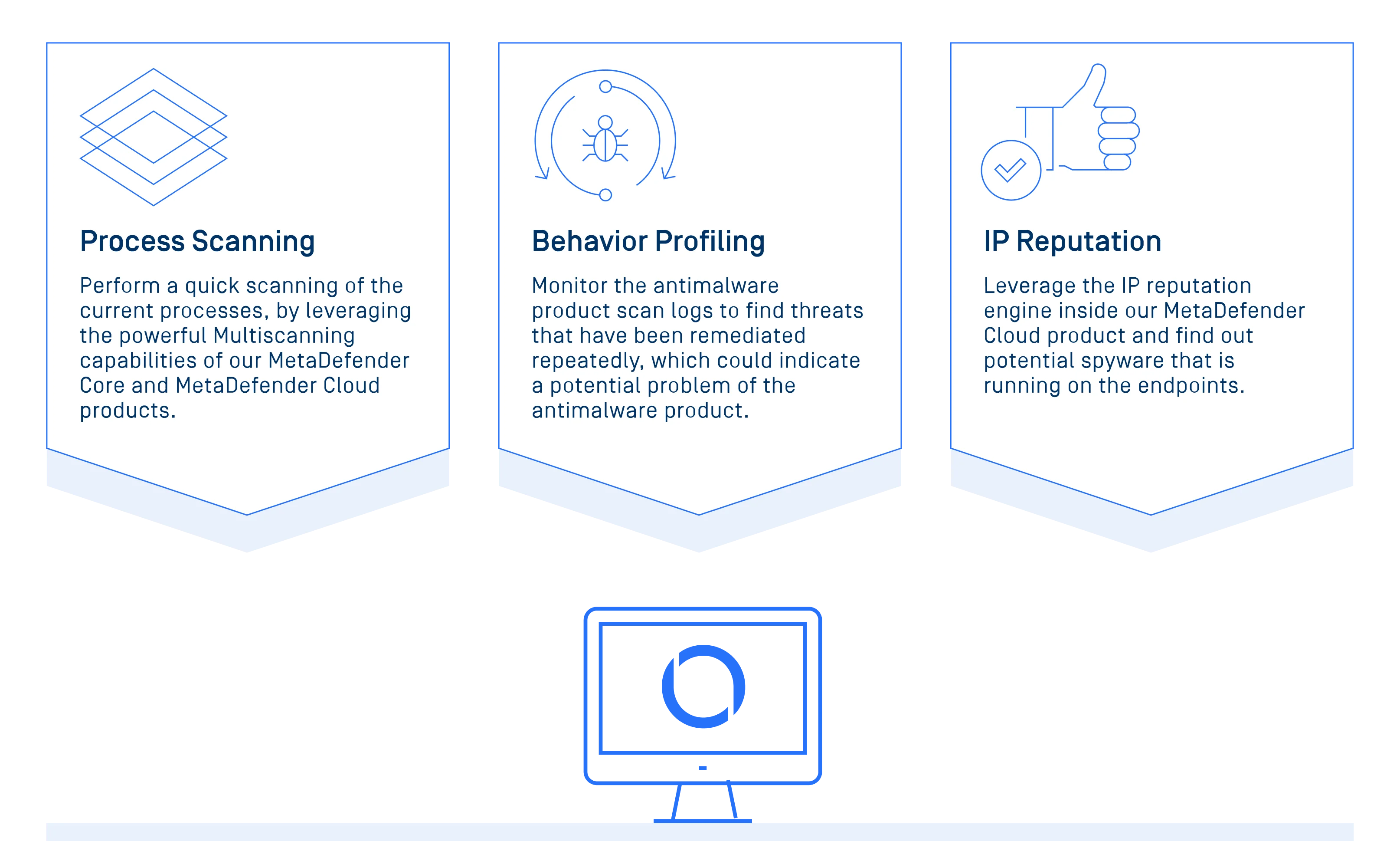
Process Scanning
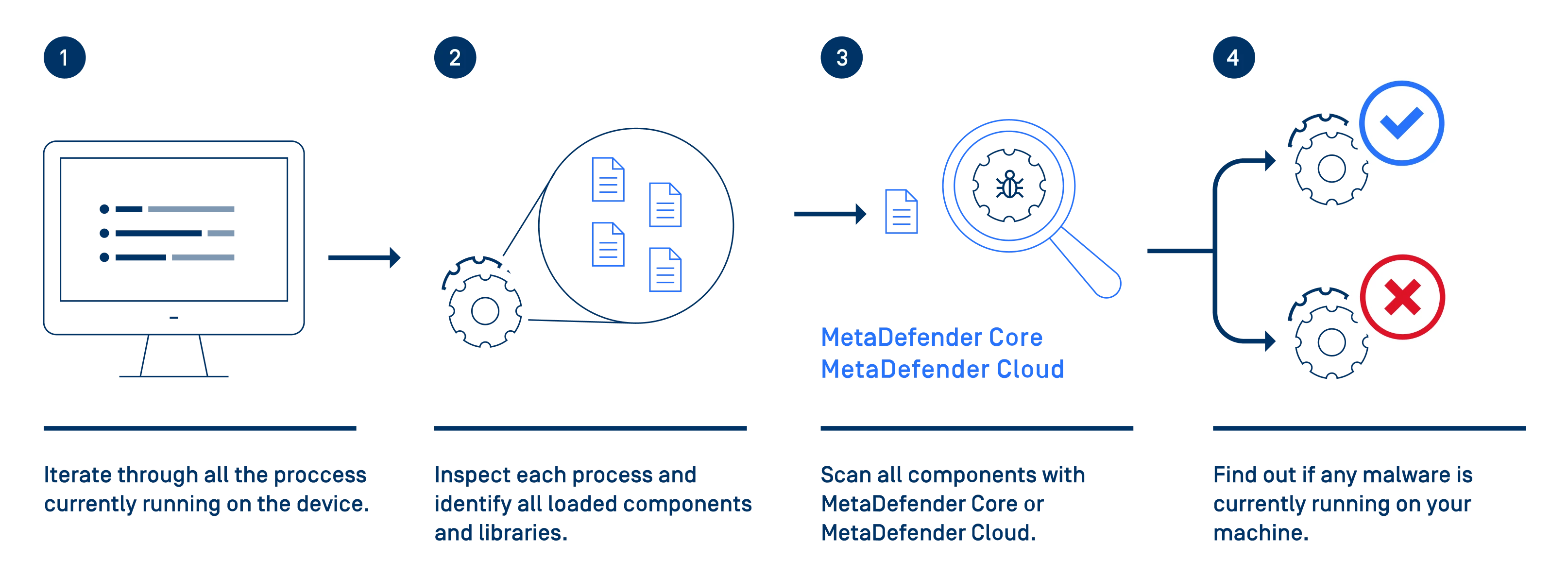
Enables end user organizations to through your integration with OESIS Framework quickly scan all running processes and their loaded libraries, using the top 30+ antivirus engines available in the MetaDefender Core or MetaDefender Cloud products. This approach may identify threats which the installed anti-malware product missed.
IP Reputation
Allows scanning of all active network connections of the endpoint, by leveraging the IP Reputation services embedded in MetaDefender Cloud. Using the results provided by aggregating multiple IP reputation sources, this functionality allows for a thorough and exact detection of malicious connections.
Behavior Profiling
Identifies repeated endpoint threats, which occur when users perform the same actions that create the threat, in multiple occasions, or when anti-malware applications struggle and fail to remove a malware. Discovering these incidents quickly is critical when responding to potential security breaches.
Technical Insights
Understand how the Advanced Malware Detection module performs the scanning of the running processes and loaded libraries.