Advanced Endpoint Protection Module
Trust Endpoint Access to Your Cloud and Local Networks
The Advanced Endpoint Protection Module goes beyond standard compliance checks to provide unique technologies to increase your security posture.
Go Beyond Standard Compliance Checks
Multi-scanning is an endpoint protection technology, leveraging the ability to use multiple anti-malware engines for hash lookups and file scanning, greatly increasing the odds of near zero-day detection of malicious activity.
Anti-Keylogger prevents keystrokes, while Screen Capture Protection ensures no one would be able to capture the content on a screen.
Together, these technologies add the following capabilities to the MetaDefender Access Platform: compliance, advanced malware detection, vulnerability and patch management, managing both potentially unwanted applications and removable media, for a comprehensive approach.

Endpoint Protection
Multi-scanning is an advanced threat detection and prevention technology that increases detection rates, decreases outbreak detection time, and provides resiliency to anti-malware vendor issues. OPSWAT pioneered the concept of multi-scanning files with over 20 anti-malware engines available to deliver enhanced protection from a variety of cyber threats.
Signature-based, heuristics-based, and machine learning detection methods are not perfect. Single antimalware engines detect at best up to 91.8 percent of common cyber threats, and the majority of them only have a 40 to 80 percent detection rate.

How It Works
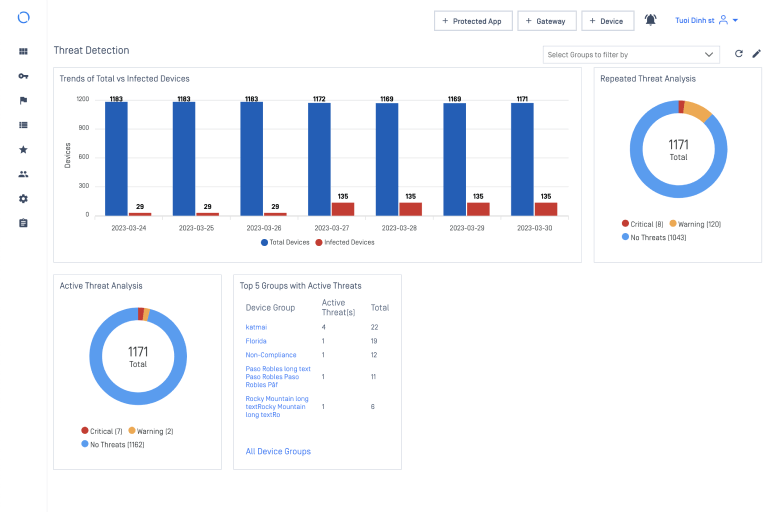
Research shows that as more anti-malware engines are added, malware detection rates improve, since each engine may not detect certain types of threats. Each individual engine specializes in different categories. Since each anti-malware engine uses different algorithms, malware analysts are in different time zones and different geographically based labs, the value of combining multiple anti-malware engines significantly increases detection.
As shown in our Multi-scanning test of more than 10,000 of the most active threats, we achieved over 95 percent detection with 12 combined engines, over 97 percent detection with 16 engines, and over 99 percent detection with 20 or more engines.
Benefits
With MetaDefender Access Endpoint Protection, organizations gain increased protection near zero-day detection, reduce outbreak exposure times and false positives with minimal performance impact. Because Multi-scanning requires multiple anti-malware engines from various vendors, cost is a factor. However, we partner with vendors to deliver optimized Multi-scanning engine package options to provide beneficial Total Cost of Ownership (TCO) over time.
Serving as a single point of contact, we reduce complexity in multiple scanning deployments for our global client base of government entities and organizations in virtually every industry, including other security firms, aerospace and defense, healthcare services, critical infrastructure, and supply chain manufacturing.
Advanced Malware Protection
MetaDefender Access uses process scanning, connection scanning, and repeated threat reporting to provide an additional layer of malware detection. In addition, its multi-engine anti-malware service greatly increases odds of near zero-day malware detection. These comprehensive features may find malware that endpoint anti-malware applications have missed or could not remediate. This capability looks for indications of whether an endpoint is infected, even though it complies with security policies and regulations. MetaDefender Access can greatly increase malware detection with Anti-Malware Multi-Engine Scanning.
Process Scanning
MetaDefender Access scans all running processes and their loaded libraries. This may identify threats that the anti-malware product installed on the endpoint missed, by checking much more than installed applications. Your organization can accelerate process scanning by configuring the caching feature to only scan binaries that have not yet been analyzed.
Repeated Endpoint Threat Reporting
Repeated endpoint threats occur when users repeat the same behaviors that create the threat and when anti-malware applications fail to remove malware. MetaDefender Access looks for repeated threats within each endpoint device to uncover persistent threats that the anti-malware application was not able to permanently remove.
Connection Scanning
MetaDefender Access enables your organization to scan all active network connections. It can detect all remote IP addresses connected to a device and compare those IPs to results that many IP reputation sources have reported. Each IP reputation source compares and categorizes the addresses according to the confidence rating of the IP.
Anti-Keylogger
Keystroke loggers are designed to steal the high-value information that the user inputs for nefarious purposes. MetaDefender Access Advanced Endpoint Protection prevents keyloggers and advanced malware from accessing sensitive data by intercepting and encrypting keystrokes and providing real-time protection against monitoring programs, trojans and spyware. This technology can protect against malicious behavior for both on-premises and remote workers.
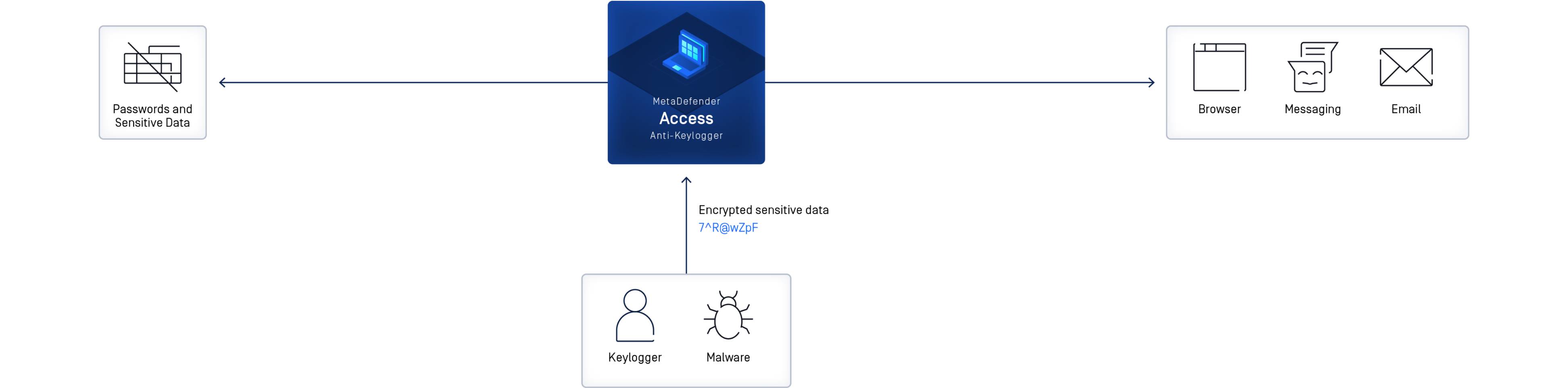
How it works
It works with an Anti-Keylogger Driver which intercepts low-level keyboard events, encrypts them, and then uses an anti-keylogger decryption hook for decoding before it sends the keystrokes to the application. The Driver encrypts the keystrokes and sends the events to the operating system event bus where the Decryption Hook decodes the keystrokes and sends the keystrokes to the application.
User Experience
There is no delay for the user when typing with this feature turned on. This solution is an overlay without any configuration changes. Most importantly, it supports current and future cyber security risks.
Screen Capture Protection
MetaDefender Access prevents malicious and unauthorized or accidental screenshots as well as recordings by users, VDI, web collaboration tools, and malicious applications.
When a process tries to capture or record the screen, this protection hook will block the request, which can optionally allow only certain windows to be captured. Screen Capture Protection supports current and future malware threats as well as data loss issues from web collaboration tools such as Zoom, Microsoft Teams, Cisco WebEx, and others.
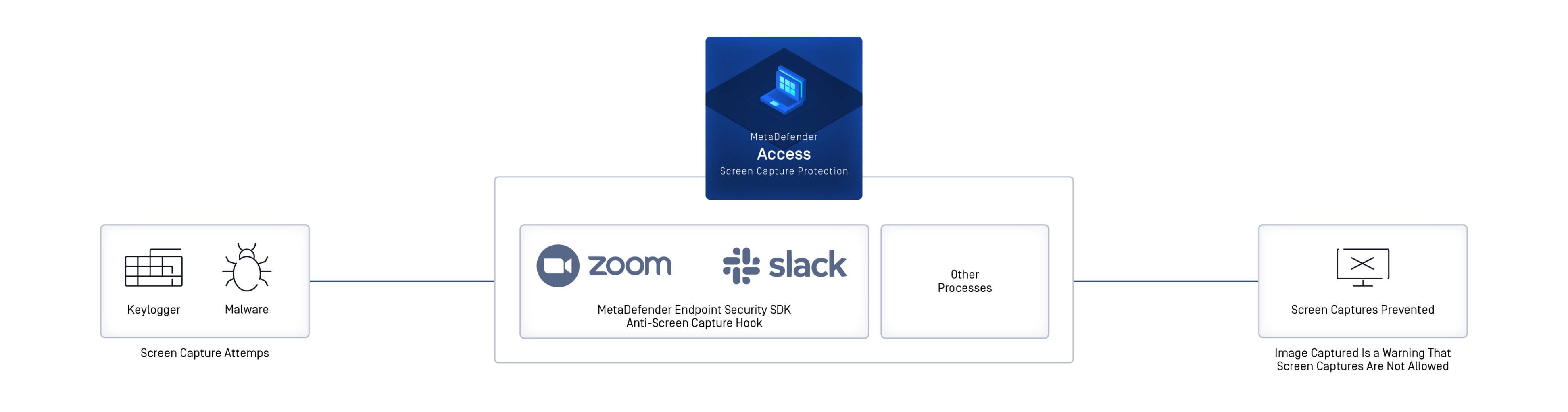
How it works
MetaDefender Access monitors each running process. When a process tries to capture or record the screen, the Screen Capture Protection hook will block the request. This hook can, optionally, allow only certain windows to be captured.
Benefits
This function is a small footprint on the device (less than 10 MB on disk) and supports current and future malware threats. It protects against data loss issues from web collaboration tools such as Zoom, Microsoft Teams, Cisco WebEx, and others.
Removable Media Protection Module
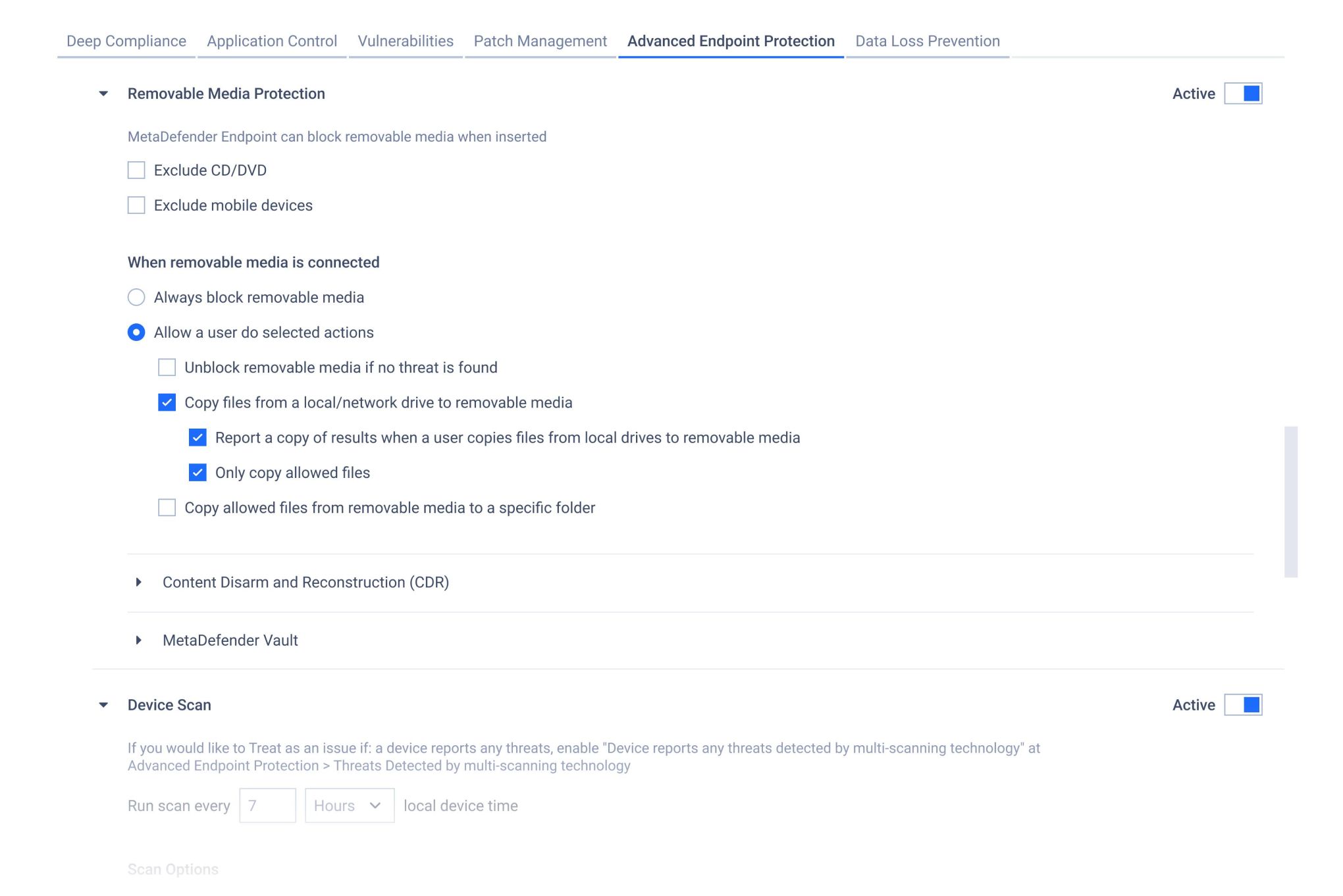
Block. Protect. Secure.
MetaDefender Access can block any connection the media tries to make with an endpoint, and it can block all connections, except those processes your organization specifies. It blocks all access to the media, while allowing this service to pass the content through advanced content security technologies, which verifies and sanitizes the data.
Highly Configurable
MetaDefender Access has highly configurable features to customize this solution to help organizations ensure that any data coming onto their environment is clean and safe to use.
Manage Potentially Unwanted Applications
MetaDefender Access can manage, block and even remove non-compliant or vulnerable applications. MetaDefender Access enables your organization to cleanly remove over 2,000 versions of popular applications (of both enterprise and consumer software) without any end user interaction. With it, your organization can silently detect such applications on any endpoint and completely remove them.
Comprehensive Removal
MetaDefender Access detects and removes anti-malware, personal firewall, and anti-phishing programs that conflict with your organization’s security policy as well as known vulnerable applications like Java, Adobe software (like Flash and Acrobat), browsers, and popular office software.
Automated Application Cleanup
MetaDefender Access automates the application cleanup process for difficult-to-uninstall applications and provides an easy way to terminate or remove these applications and remove all their files from any endpoint.
Works Silently without User Interactions
MetaDefender Access detects and removes potentially unwanted applications (PUAs) that can expose sensitive endpoint information without informed consent of the user (like browser toolbars, public filesharing programs, and backup or cloud-sync apps). This capability can be configured based upon the organization’s preferences to allow, block or remove the application.
Simplified Global Scanning
MetaDefender Access is undeterred even under adverse conditions. It works when the program password is not known or has been forgotten and removes applications that the uninstaller has partially removed or requires forced end user interaction. Finally, it removes applications that no longer function or could not otherwise be uninstalled because required files or registry settings are missing or corrupted.
Block Copy and Paste
MetaDefender Access protects confidential data and helps ensure privacy by blocking copy/paste.
It prevents unauthorized or accidental copy/paste of private or confidential data by users, for example from/to VDI, web collaboration tools, and malicious application (RATS).
When a process tries to copy to the clipboard, this protection hook blocks the clipboard, preventing pasting.
Two modes:
- Always block copy/paste between all applications
- Only block when a specific application is running
