
MetaDefender OT Access
Industrial Secure Remote Access Appliance
Operate more precisely than a VPN while enforcing granular access control and minimizing the OT attack surface.
Better than VPNs
Most VPNs do not provide enough granularity to limit remote user activity or apply other security restrictions once access is granted. This puts your OT environment at risk.
With MetaDefender OT Access, remote users are permitted to touch only what they can see across their connection, and absolutely nothing else.
MetaDefender OT Access provides the most secure method for remote employees or third-party vendors to access OT endpoints.

Product Overview
Learn how MetaDefender OT Access provides secure, tightly controlled remote access to OT and IT environments
while eliminating lateral movement and maintaining operational efficiency.
Intuitive.
Automated.
Precise.
- Remote access control per protocol + per activity + per seat + per OT endpoint, with end-to-end encryption
- OT assets and network cannot be manipulated beyond the remote “line of sight”
- No holes through firewall required
- Ideal for central control of third-party risk management
Uncompromised Critical Infrastructure Security
Secure, Policy Driven Remote Access to OT Environments
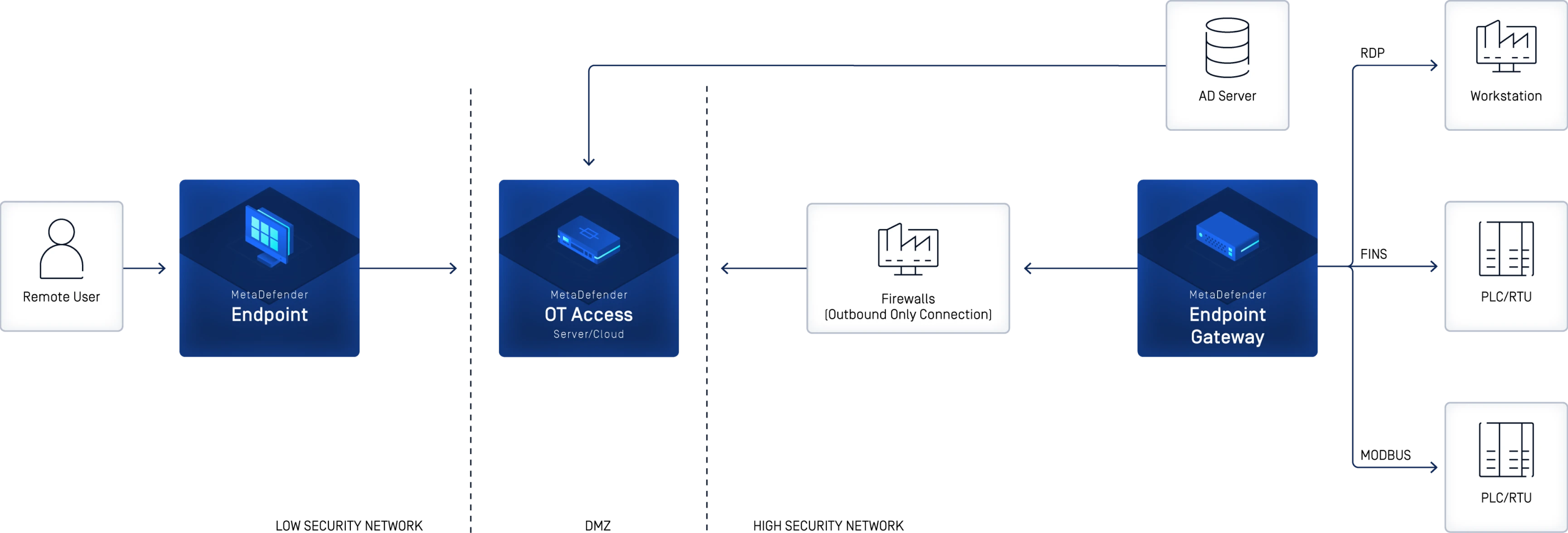
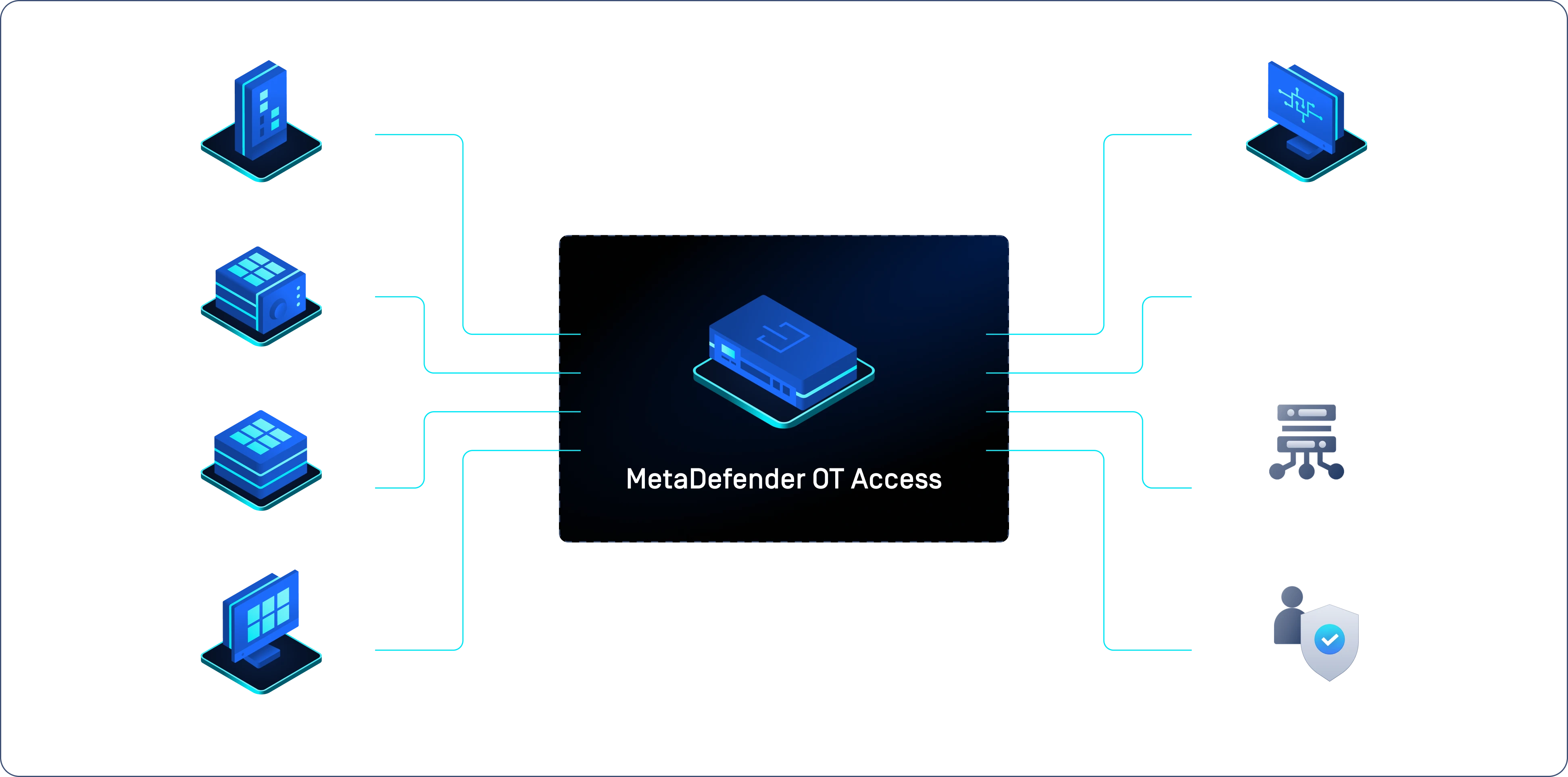
Powerful Integrations for Complete Security
Integrate to secure file transfers, sanitize threats, and harden your OT network
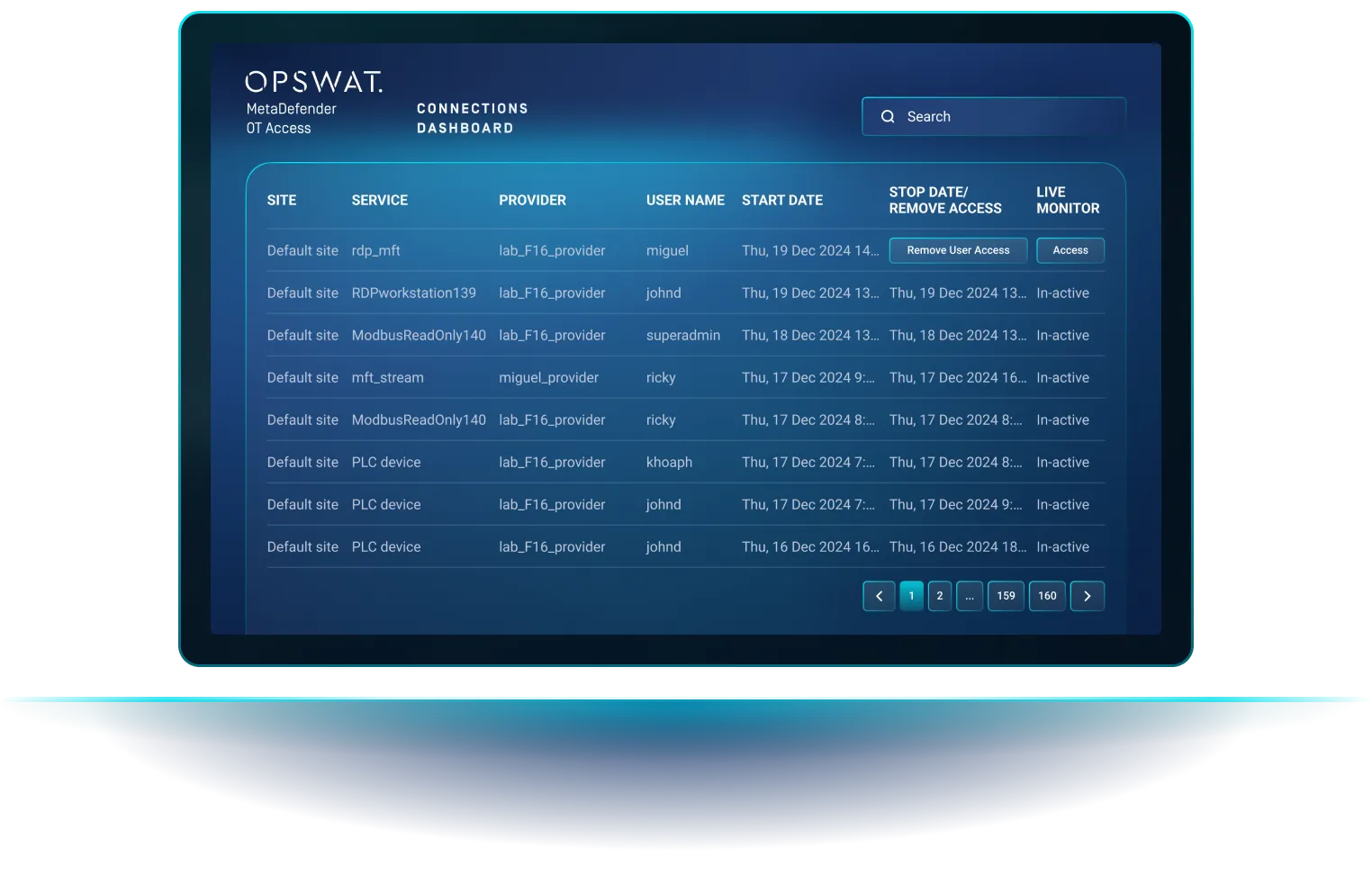
Take Control of Your
Remote Access Policy
Secure Your OT Network and Assets Against
Unwanted Changes and Unknown Threats
Have Granular Access Control From Anywhere
MetaDefender OT Access On-Premises
The On-premises solution uses a standard 1U industrial server with separate management and administrative interfaces. MetaDefender OT Access may also be deployed as a VMWare ESXi virtual appliance.

Cloud Hosted
The Cloud Hosted service uses a customer-dedicated AWS cloud instance for maximum reliability, uptime, and performance.
Native OT Protocols Support
Built-in support for native OT protocols lets you enforce highly granular and configurable access control policies across your OT environment.






Technical Documentation
Getting Started
Deployment & Usage
Support
Unlock the Full Potential of Our Products

Go In-Depth on MetaDefender OT Access

MetaDefender OT Access Brochure


