Deep Endpoint Compliance
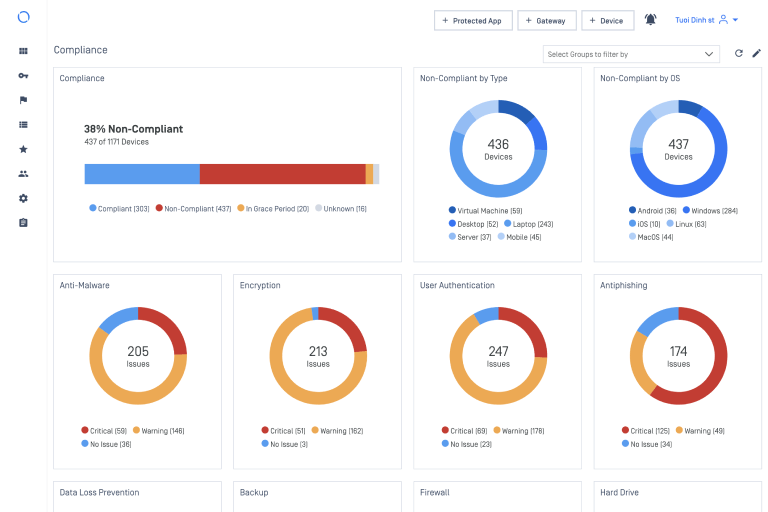
MetaDefender Access Endpoint Compliance, included in the base MetaDefender Access Platform, extends well beyond standard compliance checks to ensure with the highest degree of confidence that your endpoints are secure. It includes checks such as OS level, security software, encryption, geolocation, vulnerabilities, and patch management. When combined with our Advanced Endpoint Compliance module, MetaDefender Access provides the most comprehensive check in the industry.
MetaDefender Access Endpoint Compliance helps your organization stay in compliance by detecting and classifying applications installed on endpoints, enabling your organization to monitor and manage these applications. It helps your organization assess and remediate application-specific settings.
Prevent High-Risk Connections with Accurate Geofencing Capabilities
With geolocation-based controls, administrators have the power to define and regulate device compliance rules based on their geographical location. You can select specific locations as "blocked locations," marking devices from these regions as non-compliant. Consequently, access to designated resources can be restricted based on your secure access configurations.

Ensure That Applications on Any Endpoint Comply with Policy and Regulations
MetaDefender Access provides the ability to either block or remove potentially unwanted applications. You can create features that selectively block or remove over 2,000 versions of popular applications (of both enterprise and consumer software) without any end user interaction. With them, your organization can silently detect such applications on any endpoint and completely remove them. It also detects and removes potentially unwanted applications (PUAs) that can expose sensitive endpoint information without the informed consent of the user (like browser toolbars, public filesharing programs, and backup or cloud-sync apps).

Monitor and Remediate Application and Operating System Updates and Patches
MetaDefender Access Endpoint Compliance detects third-party patch management applications and enables them if necessary. This module also detects which patches are currently installed on any endpoint, generates a list of missing patches, and automatically installs them.

Powerful and Thorough Information Reporting and Remediation
MetaDefender Access Endpoint Compliance supports over 30 different product-specific remediations across all major operating systems. It gathers classified and unclassified application details as well as in-depth configurations of security applications, including anti-malware, personal firewall, hard disk encryption, patch management, browsers, browser plugins, and many others. This enables organizations that must comply with regulatory frameworks to easily gather information from endpoints to help them achieve compliance.

Verify That Endpoints Are Encrypted Per Policy and Regulations
MetaDefender Access Endpoint Compliance detects hard disk encryption software on each device and reports which portions of each disk are encrypted. It leverages our patented method for assessing the encryption status of selected disks (Patent No. 10,229,069) and operates independently of third-party encryption algorithms and configurations. It also supports all popular encryption solutions.
