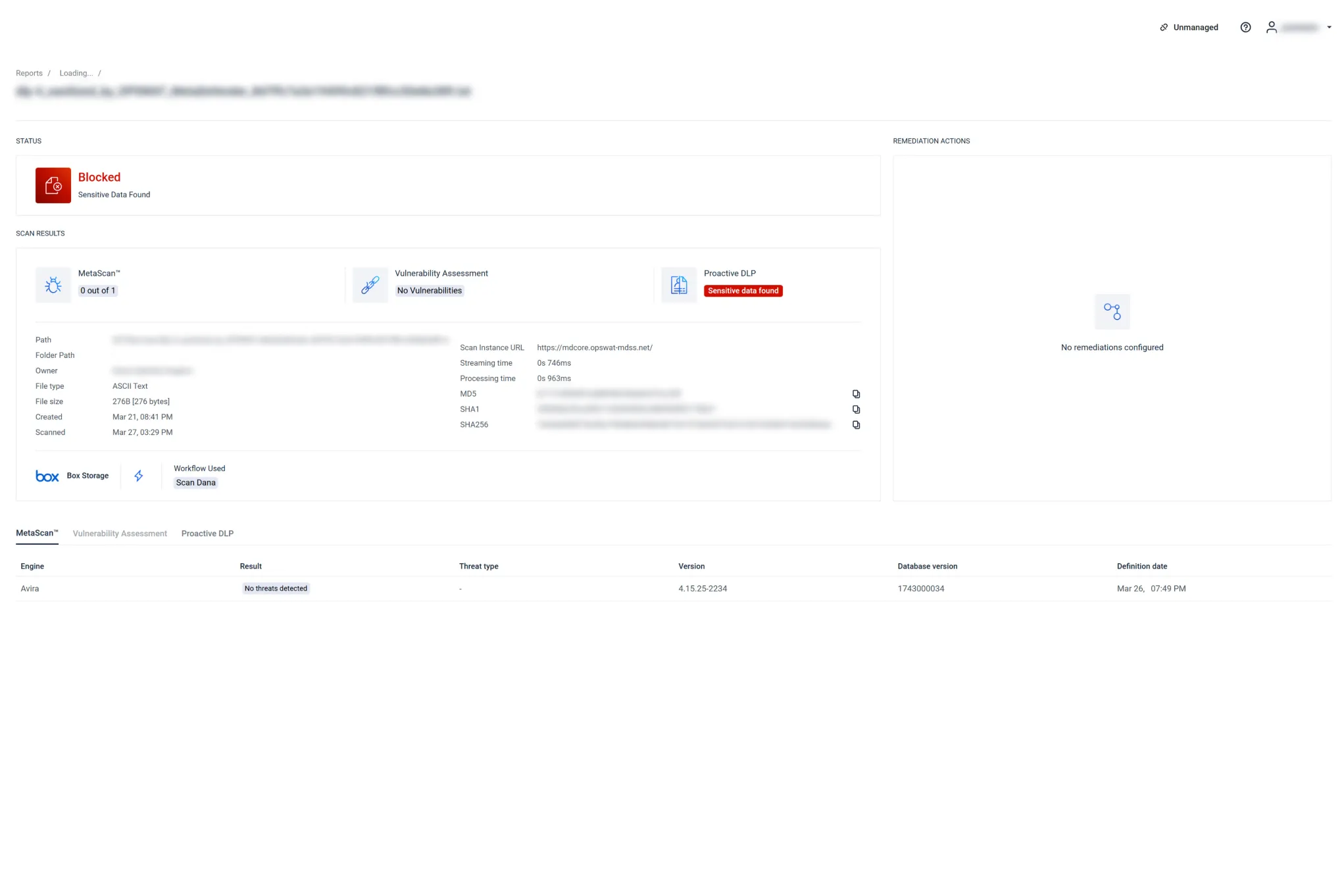
Data Breach Prevention
MetaDefender Storage Security offers a comprehensive solution to protect on-premises and cloud-based storage by integrating multiple proprietary technologies like anti-malware Multiscanning, data sanitization with Deep CDR (Content Disarm and Reconstruction), and file-based vulnerability assessment in one easy-to-implement solution.
Advanced Threat Prevention
Simultaneous analysis using multiple anti-malware engines is an advanced threat detection and prevention technology that increases detection rates, decreases outbreak detection times and provides resiliency to anti-malware vendor issues.
Proactively detects 99%+ of malware threats by using signatures, heuristics and machine learning.
Advanced Prevention of Known and Unknown Threats
98%
Malware used at least one evasive tactic
32%
Malware was “Hyper-evasive” (6 evasive tactics or more)
27%
Malware evaded detection from a single sandbox
Malware is growing in complexity and becoming increasingly successful at evading traditional anti-malware engines and sandboxes.
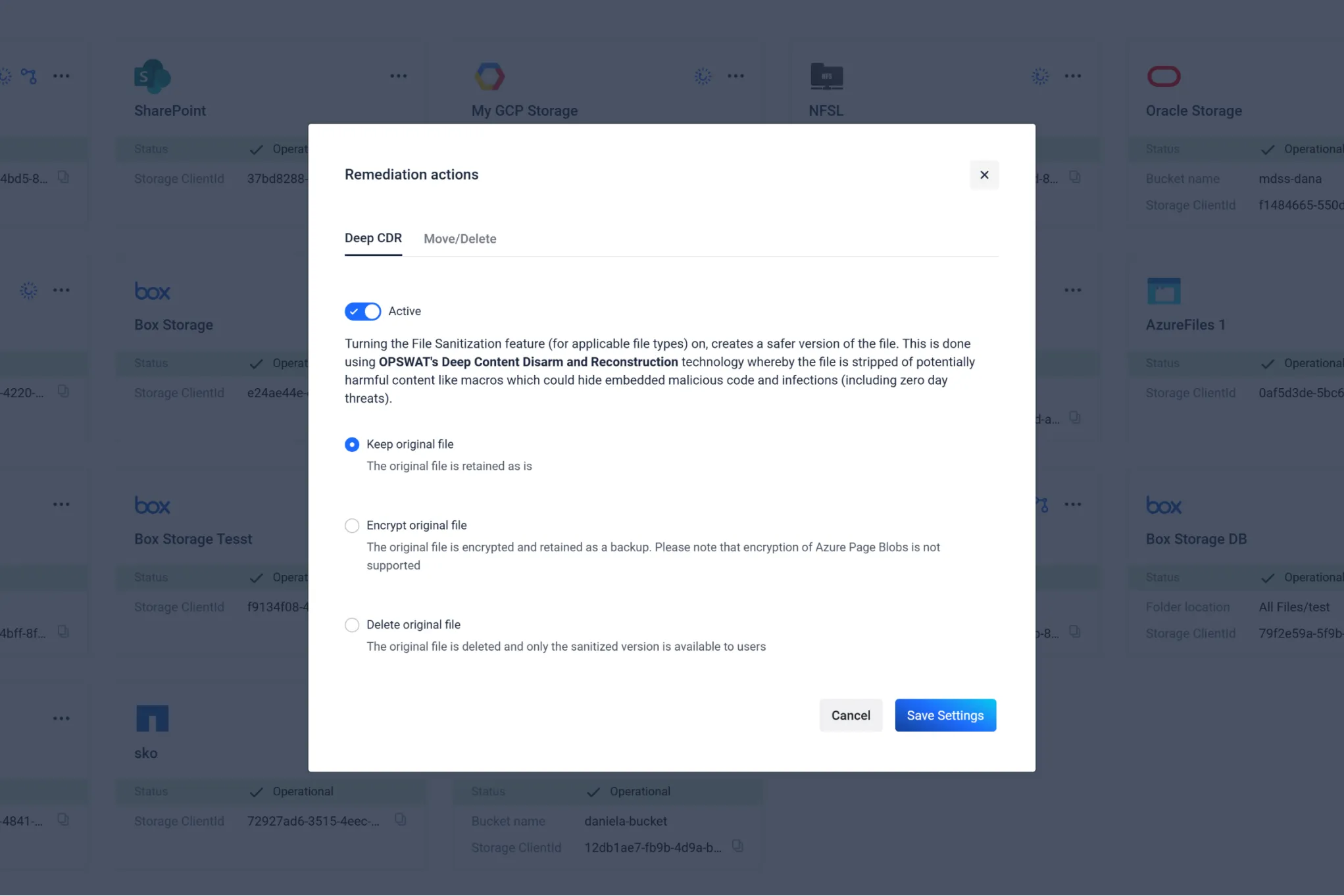
Prevent Zero-Day attacks, Advanced Persistent Threats (APT), and other targeted attacks using OPSWAT’s industry leading Deep CDR (Content Disarm and Reconstruction) technology for preventing both known and unknown threats.
Sanitize over 100 common file types, ensuring maximum usability with safe content. Hundreds of file reconstruction options are available.
File-Based Vulnerability Assessment
Detect Application and File-Based Vulnerabilities with OPSWAT’s File-Based Vulnerability Assessment technology that scans and analyzes binaries and installers to detect known application vulnerabilities before they are installed.
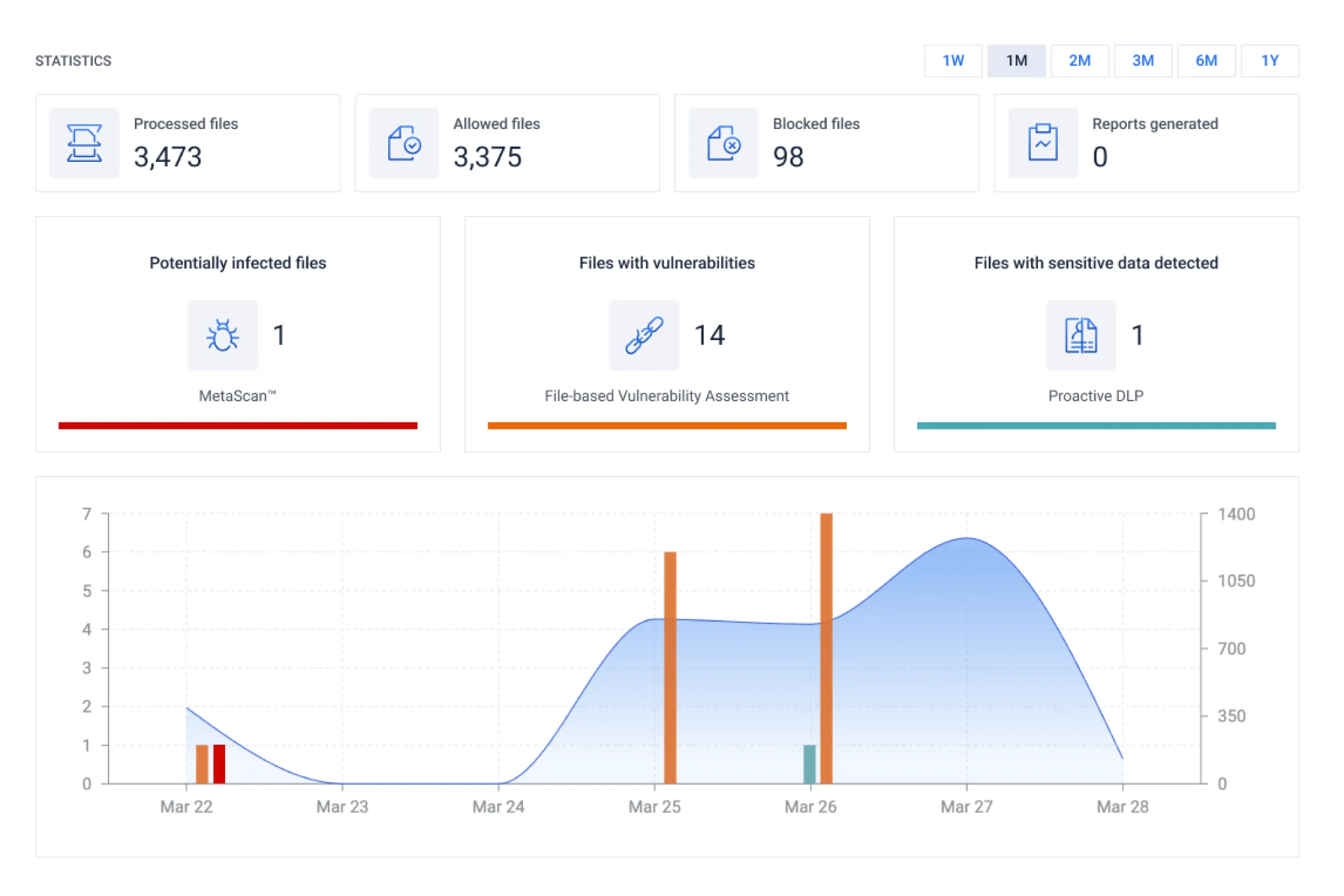
File-based vulnerabilities is one of the fastest growing categories of vulnerability types in recent years.
Millions of users are exposed to attacks that leverage vulnerabilities. Detecting and preventing installation programs from getting into your network and being used to propagate vulnerabilities is one of the top cybersecurity best practices.
Recommended Resources
MetaDefender Storage Security Datasheet
Fundamental details such as benefits, key features and specifications of MetaDefender Storage Security
MetaDefender Storage Security Documentation
Step by step instructions on installation, configuration, and daily operations of MetaDefender Storage Security
MetaDefender Storage Security Blog
A perspective on next generation cybersecurity, vulnerabilities, and the cloud
