Free Endpoint Security Scan
MetaDefender Endpoint for Endpoint Vulnerability and Application Patching
MetaDefender Endpoint Helps You To Identify and Remediate
- If your device is running any vulnerable applications
- If your device is running any out-of-date applications
Additional checks are done automatically, and an alert report will be displayed via your web browser if the client detects issues, such as:
- Your anti-malware protection is not configured properly
- Your hard disk is not encrypted
- Your operating system is not up to date
- Your device is infected by malware
- Your device has not been backed up correctly
Follow the steps below to start using MetaDefender Endpoint and make sure your device is up to date and secure.

Download and Install MetaDefender Endpoint
- Click here to download an installer for your Windows device.
- Open a Windows Explorer window and navigate to the folder that contains the MetaDefender Endpoint installer you just downloaded.
- Double-click the installer file. The installation wizard will appear. Follow instructions on the wizard to install MetaDefender Endpoint.
- To confirm that MetaDefender Endpoint is running, click the Show Hidden Icons arrow and look for the (
 )MetaDefender Endpoint icon in the system.
)MetaDefender Endpoint icon in the system. - The MetaDefender Endpoint will launch the user interface (UI) after installation is complete.
Review at-risk Applications
You can launch the MetaDefender Endpoint UI by clicking on "Open MetaDefender Endpoint" option from the tray icon's menu.
Alternatively, you can launch the MetaDefender Endpoint from the Windows Start Menu.
From within MetaDefender Endpoint UI, vulnerable and out-of-date applications can be viewed.
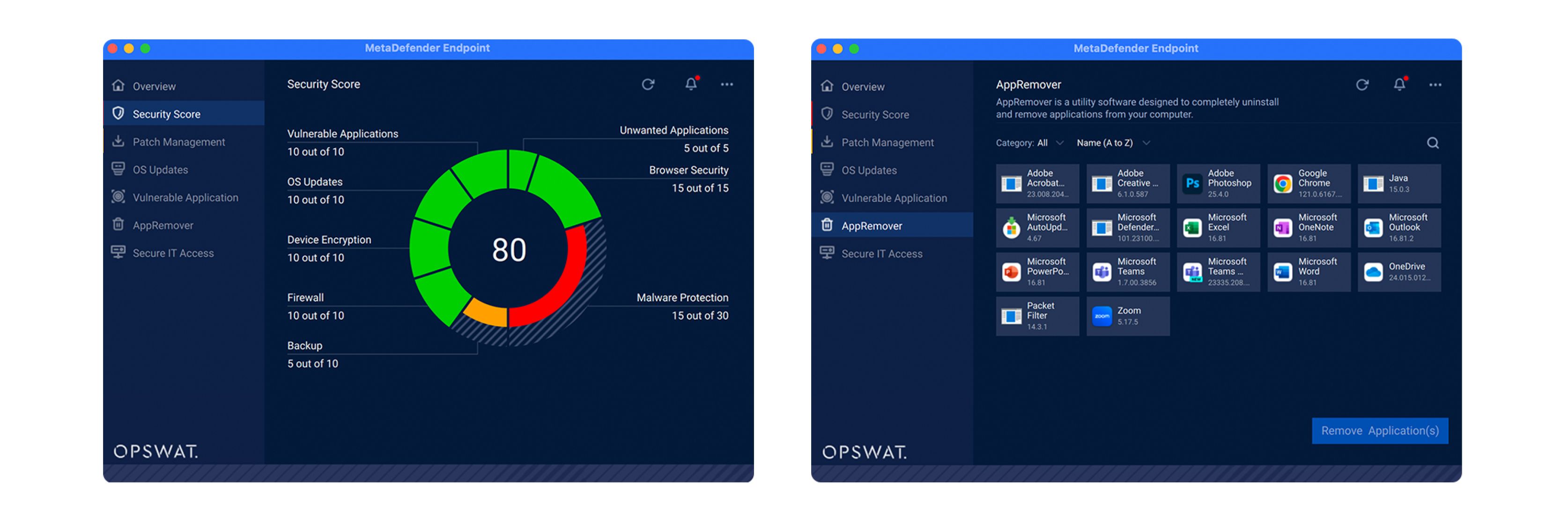
Remediate Your Vulnerable and/or Out-of-date Applications
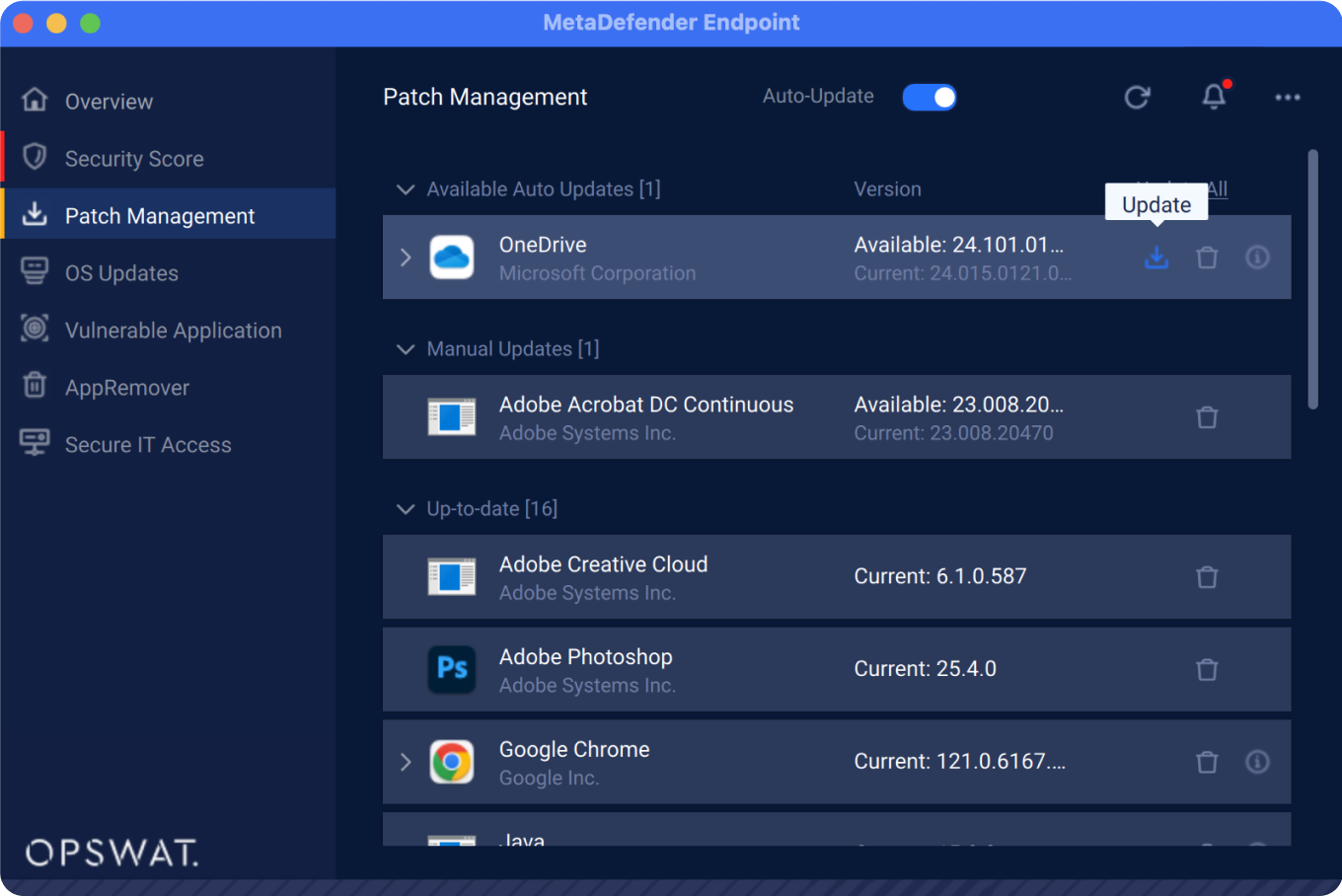
You can update out-of-date applications by selecting the applications and clicking on the "Update" option. MetaDefender Endpoint will update the selected applications to the newest version it finds and will notify you when it has completed.
For vulnerable applications, you may choose to update them (if an update is available) or choose to uninstall them. MetaDefender Endpoint will take care of that even if the application is broken. By selecting the "Uninstall" option, MetaDefender Endpoint will try to remove the applications and their related components. The MetaDefender Endpoint may prompt with an uninstall wizard if needed. You should follow the wizard instructions to finish the uninstallation process.
Aside from being used as a standalone client, users may register (for free!) with our cloud service MetaDefender Access to manage multiple devices and gain additional features, such as:
- Check that your anti-malware protection is configured properly
- Ensure your hard disk is encrypted
- Verify the operating system is up to date
- Confirm that your device is free from malware
- Report if your device has performed a recent backup
- and more!
We hope you enjoy using our free tools and feedback is always welcome.
