Title
Create new category
Edit page index title
Edit category
Edit link
What is OPSWAT Severity Score in our Vulnerability Scanning Technology?
This article applies to the current My OPSWAT Central Management Console and all component product releases deployed on Windows, macOS, Linux, Android and iOS systems.
The Common Vulnerability Scoring System (CVSS) score
When classifying the impact of a vulnerability, we usually apply the Common Vulnerability Scoring System, or CVSS.
The CVSS is a free and open industry standard that helps administrators and security professionals assess the severity of computer system security vulnerabilities.
By assigning CVSS scores to vulnerabilities, responders can prioritize their resources according to the severity of the threat.
Scores are calculated based on a formula that relies on several metrics that approximate the ease of exploiting the vulnerability, and the impacts thereof.
The first version of CVSS is known as CVSSv1 and was introduced in 2005, while the second version, CVSSv2 was launched in 2007, and the third, CVSSv3 was released in 2015.
The OPSWAT Severity Score
Although CVSSv3 features improvements over previous versions, it still has its limitations. CVE life-cycle has become increasingly essential as an input parameter, yet it is not among the input metrics considered in the CVSSv3.
There are other parameters that are not included in the CVSS but that are equally essential to the big picture. For example, if a CVE has a high CVSS score but a limited number of systems are exploitable - this should be factored in.
Understanding that CVSSv3 is limited in terms of big-picture metrics, OPSWAT developed a more comprehensive scoring system that combines CVSS with big data - this is known as the OPSWAT Severity Score.
The OPSWAT Severity Score is a dynamic score, ranging from 0 to 100, that is calculated based on the four parameters illustrated below.
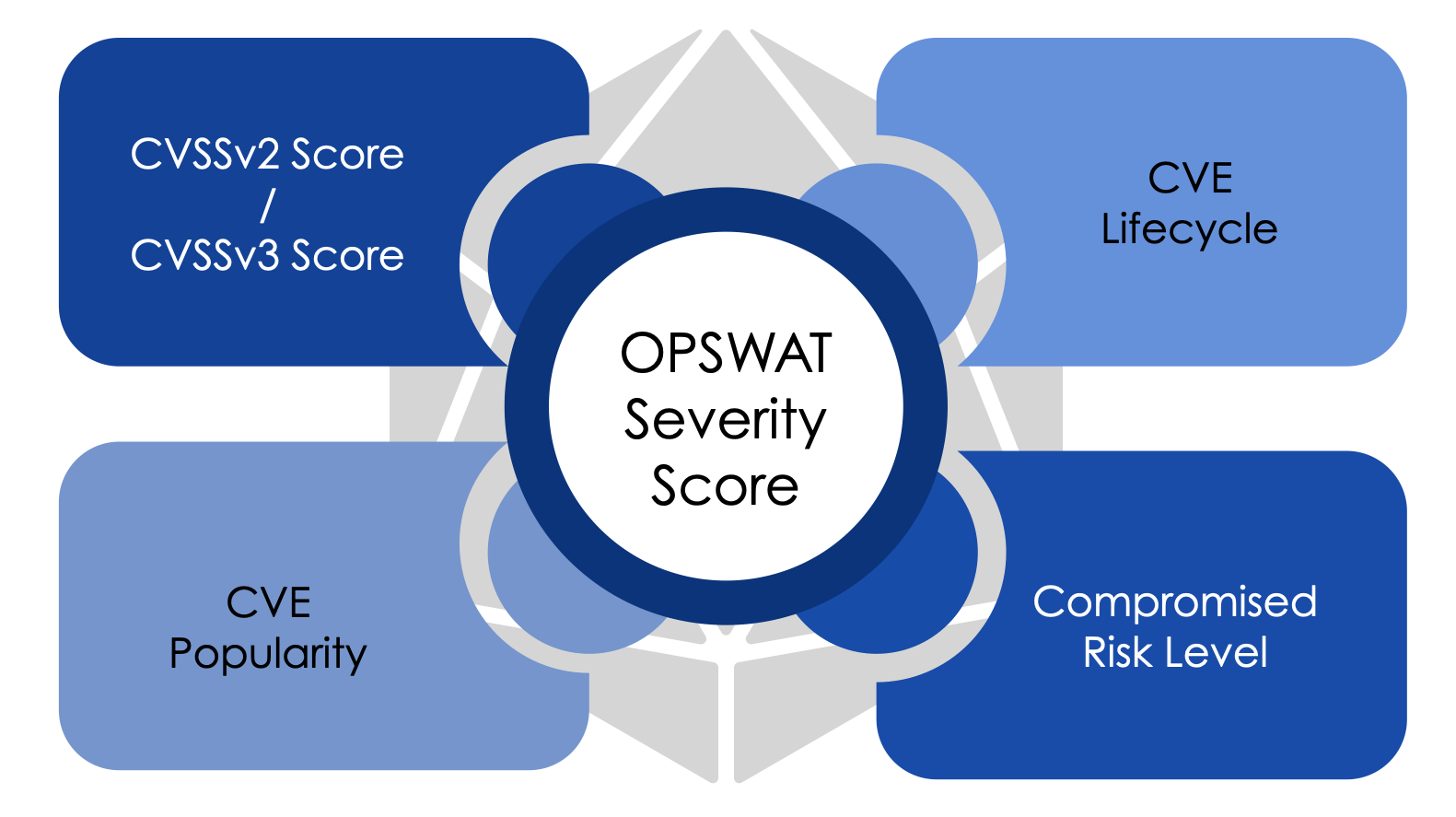
| CVSSv2/CVSSv3 | CVSS score is still a primary input. |
| CVE Popularity | Indicating the activity level of the vulnerability. |
| Compromised Risk Rate | Indicating the number of devices on which the vulnerability has been confirmed - sourced from real life machine data. |
| CVE Lifecycle | Indicating the time elapsed since this vulnerability was first reported (case 0). |
Let us consider two CVEs to exemplify the OPSWAT Severity Score system, namely:
- CVE-2016-2052 (Chrome)
- CVE-2016-2826 (Firefox)
CVE 2 has a CVSSv3 score of 7.8, which is higher than CVE 1’s score of 7.6.
Yet, by factoring in our big-picture data, we observe that people searched for CVE 1 more than 510 times, while they only searched for CVE 2 480 times over an equal period.
Additionally, we see that the risk rate for CVE 1 is 5.7%, while the risk rate for CVE 2 is only 4.4%.
Applying our algorithm, it follows that the OPSWAT Severity Score for CVE 1 is 76, while the OPSWAT Severity Score for CVE 2 is only 73.
As you can see, the impression gathered from the CVSS score alone is vastly altered when we consider the OPSWAT Severity Score.
With OPSWAT’s comprehensive Severity Score system, we aim to provide our users with the most accurate summary information available.
This is particularly useful to IT administrators and cyber-security professionals who spend hours reviewing CVEs on a daily basis.
The OPSWAT Severity Score allows these users to filter out old and low priority cases, considering only the CVEs that count.
For further queries, concerns or issues regarding the OPSWAT Severity Score, please open a Support Case with the OPSWAT team via phone, online chat or form, or feel free to ask the community on our OPSWAT Expert Forum.

