Title
Create new category
Edit page index title
Edit category
Edit link
Devices
System Health & Performance
The System Health and Performance section of the Devices page provides information about the resource utilization, hostname, IP address, and system version numbers of managers and collectors. Various system statistics are also displayed in tabular form.
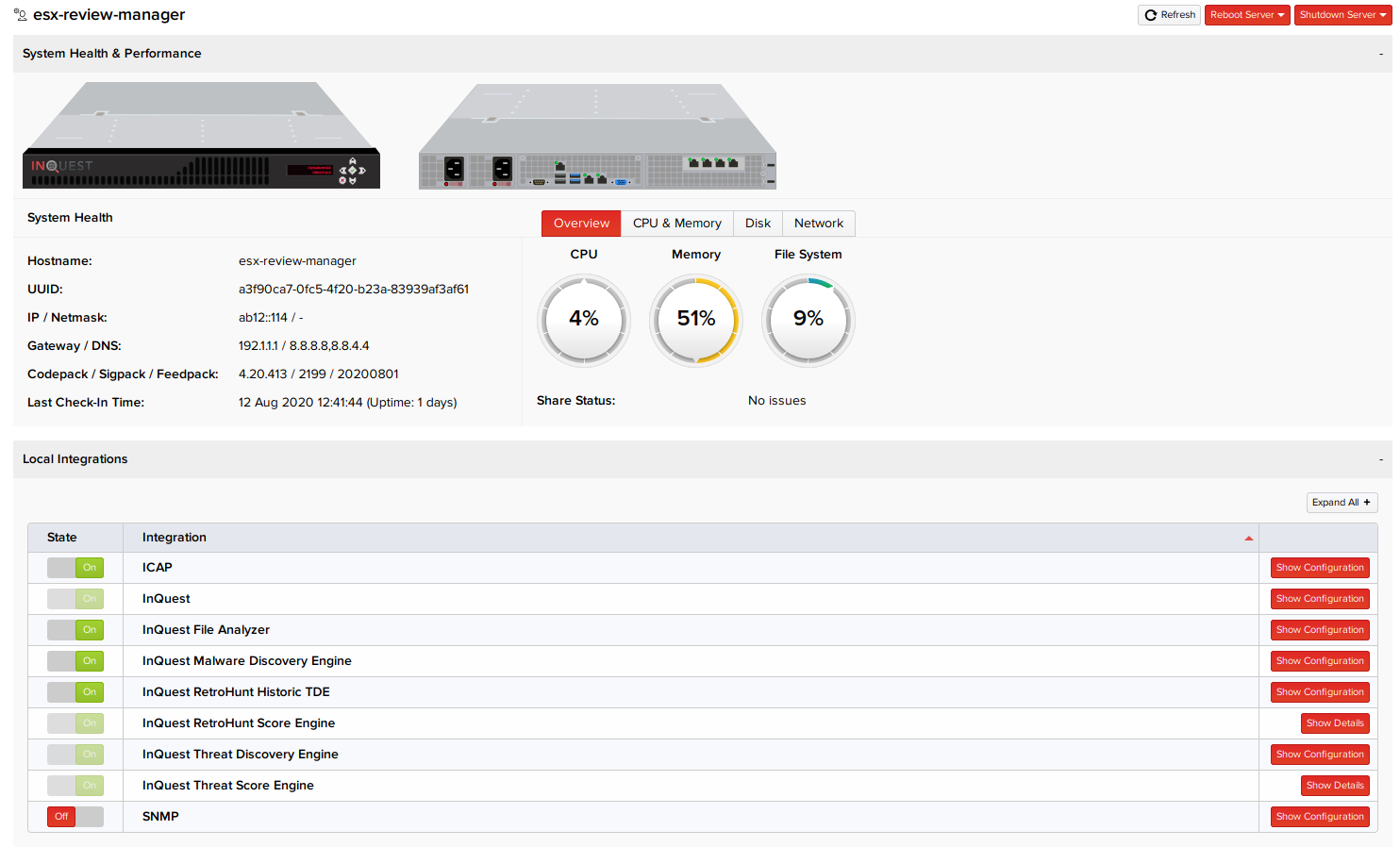
The system control options for each device at the top of the page give you the ability to reboot (or force reboot), and shut down a device instantly or after a selected time interval. There are also global reboot and shutdown options on the left side of the page that will affect every manager or collector in the devices list.
Integrations
There are numerous internal analysis components and external analysis appliances available as optional integrations to the Threat Discovery Engine. Having third-party integrations enabled provides a broader scope of detection and increases the alerting and threat factoring capabilities of the system. MetaDefender NDR leverages the analytic capabilities of third-party technologies through internal integration services that can be configured to interact with those technologies. Those services are designed to communicate with and consume the analysis results from those technologies to perform threat analysis on the content that is captured. They can be configured in the Devices page.
Note__: Integrations can be configured using either IPv4 or IPv6 addresses.
Literal IPv6 addresses are enclosed in square brackets, for example: http://[2001:db8:85a3:8d3:1319:8a2e:370:7348]/
When the URL also contains a port number the notation is: https://[2001:db8:85a3:8d3:1319:8a2e:370:7348]:443/ where the trailing 443 is the example's port number.
Some sections in the UI require brackets around the ipv6 address:
- IPv6 Syslog address
- Admin > Globals > Network > Upstream HTTP Proxy
- Admin > Globals > Devices > OPSWAT > OPSWAT Metadefender Core Hosting: Remote Host
By default, post-processors for the following integration features are active:
- InQuest File Analyzer – Factors variables and data associated with files and their alerts to generate threat scores.
- InQuest Session Header TDE – Provides threat scoring for TCP sessions by assessing scores of the other InQuest post-processors.
- InQuest Threat Discovery Engine – Discovers threats embedded within sessions based on the weekly updated MetaDefender ND proprietary signature pack.
- InQuest Threat Score Engine – Generates and assigns a threat score from 0 to 10 to the sessions using InQuest proprietary scoring algorithms above all configured integrations.
- InQuest URL Analyzer – Performs URL analysis for threat scoring.
- InQuest RetroHunt Historic TDE – Scans files stored 2 weeks ago with the latest signatures. The time interval can be set in the Devices page.
Post-processors for the following integration features can be activated, but the configuration of each integration may be required:
- MetaDefender NDR Automatic Updates – Enables MetaDefender NDR cloud connectivity for automatically retrieving and applying code, signature, and intelligence (C2) updates.
- Cuckoo Sandbox - Sandbox that performs dynamic malware analysis.
- Falcon Sandbox - Automated malware analysis system.
- VMRay Analyzer - Malware sandbox for analysis and reputation.
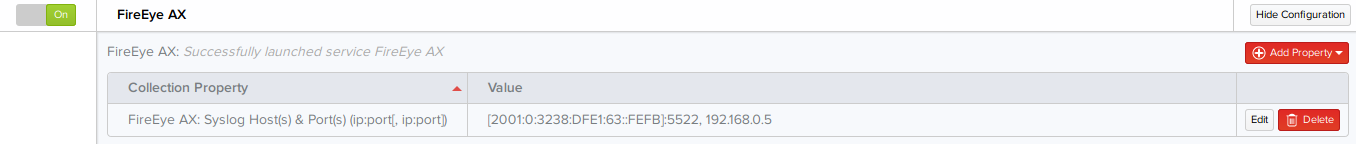
- FireEye AX – Hardware appliance that performs dynamic analysis of files.
- InQuest Eyelet Reputation - Cloud-based reputation database
- InQuest MultiAV – Provides cloud-based hash analysis.
- InQuest Threat Exchange – Enables communication with the MetaDefender NDR cloud reputation database to exchange information on file hashes.
- Joe Sandbox - Sandbox for deep malware analysis
- OPSWAT MetaDefender Core – Hardware appliance that leverages multiple AV engines to scan files.
- OPSWAT MetaDefender Sandbox – Emulation based dynamic analysis platfrom
- VirusTotal – Online service used to look up AV reports for known-bad hashes.
- ICAP – Protocol for submitting files to InQuest.
Note: Activation of MetaDefender NDR MultiAV and VirusTotal are mutually exclusive. We recommend enabling InQuest MultiAV over VirusTotal.
Integration features can be activated or deactivated by clicking Administration > Devices. Software and hardware configuration is generally required for the integration features that are not activated by default. Toggling the activation status will either cause jobs to be created for an integration or prevent jobs from being created for an integration. To activate or deactivate post-processors for an integration feature, toggle the corresponding On or Off buttons.
Each of the integration features have options that can be supplied to the corresponding integration service. For instance, if the VirusTotal integration is enabled, a private API key supplied by VirusTotal has to be added so that MetaDefender NDR can use the service.
Also, external integrations may either require cloud connectivity or can be on-premise. For example: With VirusTotal, only file hashes are submitted to the cloud. However, with OPSWAT Metascan, if there's a hardware product available in the customer environment, we connect to it and send files.
Configuring Collector Properties
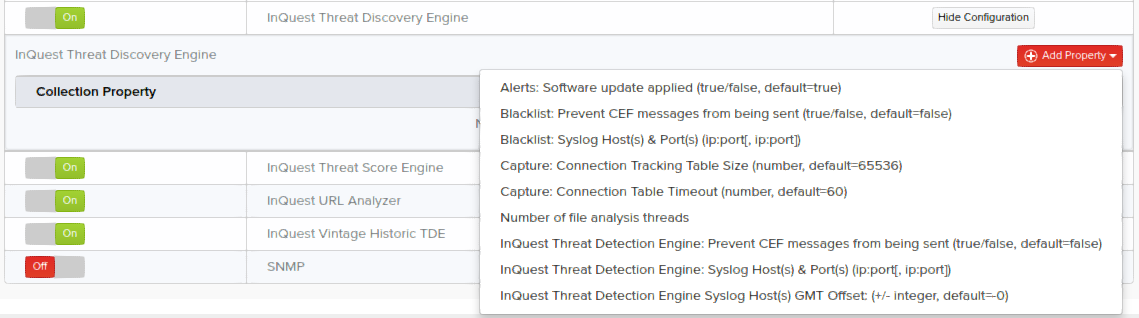
Collector properties (or options) pertain to each collector and are independent. Administration > Devices. By default, MetaDefender NDR Cloud MultiAV has a pre-populated property value. Properties for each collector can be added, modified, or deleted in your deployment. To add new properties pertaining to a particular integration feature on a specific collector:
- Go to Administration > Devices, and click Show Configuration corresponding to an integration option for which you want to configure properties.
Note: To remove a property and its value that is no longer required, click Delete corresponding to that property and then click Save. To modify the value of a property, click Edit corresponding to that property, change the value, and then click Save.
For example, to configure the FireEye AX host:
- Click Show Configuration to open the Add Property menu.
- Select FireEye AX: URL for the FireEye AX API (eg. https://10.10.10.10:443) and under the Value column, specify the host IP as required.
- Click Save. A message appears stating the collector is saved with the configured properties successfully.
Collector Properties and Values
The following are the properties and default values available for the collector configuration on this page. Furthermore, there are several options that can be applied globally across collectors, such as proxies, banners, password complexity requirements and so on by clicking Administration > Globals.
Note: The global MIME exceptions will always take precedence over the sandbox inclusion MIME inclusion lists. If a MIME type is in both the inclusion list for a sandbox as well as the global exclusion list, that MIME type will not be submitted to the sandbox.
For further information on MIME exceptions, see the Performance Tuning Recommendations
cuckoo_auto_submit Cuckoo Sandbox Cuckoo Sandbox: Automatically submit files (true/false, default=false)cuckoo_mime_include Cuckoo Sandbox Cuckoo Sandbox: Only submit these MIME types (comma separated, default=all)cuckoo_no_syslog Cuckoo Sandbox Cuckoo Sandbox: Prevent CEF messages from being sent (true/false, default=false)cuckoo_report_alert Cuckoo Sandbox Alerts: Cuckoo report received (true/false, default=false)cuckoo_syslog_host Cuckoo Sandbox Cuckoo Sandbox: Syslog Host(s) & Port(s) (ip:port[, ip:port])cuckoo_threatscore_eq Cuckoo Sandbox Cuckoo Sandbox: Exclude files that already have a Threat Score equal to this (default=none)cuckoo_threatscore_gt Cuckoo Sandbox Cuckoo Sandbox: Exclude files that already have a Threat Score greater than this (default=10)cuckoo_threatscore_lt Cuckoo Sandbox Cuckoo Sandbox: Exclude files that already have a Threat Score less than this (default=0)cuckoo_url Cuckoo Sandbox Cuckoo Sandbox: URL for the Cuckoo Sandbox API (eg. http://10.0.0.1:8090/)cuckoo_use_proxy Cuckoo Sandbox Cuckoo Sandbox: Use global proxy settings (true/false, default=false)cuckoo_vlan_include Cuckoo Sandbox Cuckoo Sandbox: Only submit from these VLAN IDs or ranges (comma separated, default=all)falcon_auto_submit Falcon Sandbox Falcon Sandbox: Automatically submit files (true/false, default=false)falcon_env_id Falcon Sandbox Falcon Sandbox: Environment ID (integer, default=100)falcon_key Falcon Sandbox Falcon Sandbox: Auth key for the Falcon Sandbox API (Must have 'elevated' or higher privilege)falcon_mime_include Falcon Sandbox Falcon Sandbox: Only submit these MIME types (comma separated, default=all)falcon_no_syslog Falcon Sandbox Falcon Sandbox: Prevent CEF messages from being sent (true/false, default=false)falcon_report_alert Falcon Sandbox Alerts: Falcon Sandbox report received (true/false, default=false)falcon_syslog_host Falcon Sandbox Falcon Sandbox: Syslog Host(s) & Port(s) (ip:port[, ip:port])falcon_threatscore_eq Falcon Sandbox Falcon Sandbox: Exclude files that already have a Threat Score equal to this (default=none)falcon_threatscore_gt Falcon Sandbox Falcon Sandbox: Exclude files that already have a Threat Score greater than this (default=10)falcon_threatscore_lt Falcon Sandbox Falcon Sandbox: Exclude files that already have a Threat Score less than this (default=0)falcon_url Falcon Sandbox Falcon Sandbox: URL for the Falcon Sandbox API (default=https://www.reverse.it/api/v2)falcon_use_proxy Falcon Sandbox Falcon Sandbox: Use global proxy settings (true/false, default=false)falcon_vlan_include Falcon Sandbox Falcon Sandbox: Only submit from these VLAN IDs or ranges (comma separated, default=all)fireeye_auto_submit FireEye AX FireEye AX: Automatically submit files (true/false, default=false)fireeye_legacy_api FireEye AX FireEye AX: Use the legacy (v1.1.0) FireEye API, for v7.x FireEye appliances (default=0)fireeye_mime_include FireEye AX FireEye AX: Only submit these MIME types (comma separated, default=all)fireeye_no_syslog FireEye AX FireEye AX: Prevent CEF messages from being sent (true/false, default=false)fireeye_password FireEye AX FireEye AX: Password for the FireEye AX APIfireeye_profile FireEye AX FireEye AX: Profile (profile name, default=winxp-sp3)fireeye_report_alert FireEye AX Alerts: FireEye report received (true/false, default=false)fireeye_syslog_host FireEye AX FireEye AX: Syslog Host(s) & Port(s) (ip:port[, ip:port])fireeye_threatscore_eq FireEye AX FireEye AX: Exclude files that already have a Threat Score equal to this (default=none)fireeye_threatscore_gt FireEye AX FireEye AX: Exclude files that already have a Threat Score greater than this (default=10)fireeye_threatscore_lt FireEye AX FireEye AX: Exclude files that already have a Threat Score less than this (default=0)fireeye_url FireEye AX FireEye AX: URL for the FireEye AX API (eg. https://10.10.10.10:443)fireeye_username FireEye AX FireEye AX: Username for the FireEye AX APIfireeye_use_proxy FireEye AX FireEye AX: Use global proxy settings (true/false, default=false)fireeye_vlan_include FireEye AX FireEye AX: Only submit from these VLAN IDs or ranges (comma separated, default=all)icap_allowed_networks ICAP ICAP: Source networks (default none)icap_block_c2_hosts ICAP ICAP: Block C2 hosts (0 = allow, 1 = block, default = 1)icap_block_header_alerts ICAP ICAP: Block on header threat (0 = allow, 1 = block, default = 1)icap_block_score ICAP ICAP: Score for blocked ICAP sessions (integer, default=10)icap_cache_timeout ICAP ICAP: Cache timeout in seconds (default 3600)icap_enable_rejection ICAP ICAP: Block on file threat (0 = allow, 1 = block, default = 1)icap_log_requests ICAP ICAP: Log requests (0 = no, 1 = yes, default = 0)icap_max_connections ICAP ICAP: Maximum simultaneous proxy connections (default 100)icap_max_file_size ICAP ICAP: Maximum file size in bytes (default 100MB)icap_min_threat_score ICAP ICAP: Minimum threat score for file threat blocking (default 6)icap_no_syslog ICAP ICAP: Prevent CEF messages from being sent (true/false, default=false)icap_preview_size ICAP ICAP: Preview size in bytes (default 4KB)icap_reject_message ICAP ICAP: Rejection message (default "Content blocked by InQuest")icap_scan_timeout ICAP ICAP: Scan timeout in seconds (default 60)icap_syslog_host ICAP ICAP: Syslog Host(s) & Port(s) (ip:port,[ip:port])icap_timeout_action ICAP ICAP: Timeout action (0 = allow, 1 = block, default = 0)blob_size InQuest Capture: Capture buffer size in gigabytesconnection_table_size InQuest Capture: Connection Tracking Table Size (number, default=65536)flee_count InQuest Capture: Number of capture threads per interfaceflee_disable_fast_csums InQuest Capture: Disable fast checksumming (0/1 default=0)flee_enable_ssl InQuest Capture: Capture SSL certificatesflee_frame_size InQuest Capture: Packet group sizeflee_ooo_syn InQuest Capture: Support OOO SYN packetsflee_split_vlans InQuest Capture: Allow split VLANshandle_split_http InQuest Capture: Capture half-open HTTP sessionshomenets InQuest HomeNets: Networks considered potential targets for attacks and potential sources for data leakage (comma separated list of IPs or subnets, default=none)http_ports InQuest HTTP: Listen ports for hosted HTTP servers (tcp ports, default 80,8080,8000)kill_date_smtp_days InQuest Alerts: Days before license expiration (default=60,30,15,3,2,1)max_protocol_window InQuest Capture: Protocol detection windowmax_session_size InQuest Capture: Maximum Stream Size (number, default=10485760)memory_blobs InQuest Capture: Use memory-backed blobsmin_session_size InQuest Capture: Minimum Stream Size (number, default=8)retain_all_email InQuest Capture: Retain all emailretain_uris InQuest Capture: Retain URIsrx_queue_count InQuest Capture: Receive queue countsmtp_extract_links InQuest SMTP: Extract Links (true/false, default=true)smtp_no_syslog InQuest SMTP: Prevent CEF messages from being sent (true/false, default=false)smtp_syslog_host InQuest SMTP: Syslog Host(s) & Port(s) (ip:port[, ip:port])smtp_tz_offset InQuest SMTP Syslog Host(s) GMT Offset: (+/- integer, default=-0)splitter_count InQuest Capture: Number of protocol analysis threadsswap_vlans InQuest Capture: Reverse carrier/customer VLANthreat_score_threshold InQuest Alerts: Session score threshold GREATER than (default=8)usage_cpu_threshold InQuest Alerts: CPU Usage Threshold % (default: 85)usage_disk_threshold InQuest Alerts: Disk Usage Threshold % (default: 85)usage_five_minutes_threshold InQuest Alerts: Five Minutes Load Average Threshold % (default: 85)usage_inode_threshold InQuest Alerts: Inode Usage Threshold % (default: 85)usage_mem_threshold InQuest Alerts: Memory Usage Threshold in kb (default: 85)c2dns_syslog_host InQuest C2 Monitor C2 DNS: Syslog Host(s) & Port(s) (ip:port[, ip:port])c2ip_syslog_host InQuest C2 Monitor C2 IP: Syslog Host(s) & Port(s) (ip:port[, ip:port])c2_slow_vlan InQuest C2 Monitor C2: Slow VLAN processingrep_query_count InQuest Eyelet Reputation Eyelet Reputation InQuest Controls: Process Count (integer, default=3, max=10)rep_query_debug InQuest Eyelet Reputation Eyelet Reputation InQuest Controls: Debug Logging (0/1, default=0)file_analyzer_count InQuest File Analyzer Number of file analysis threadsmde_cache_days InQuest Malware Discovery Engine InQuest MDE: Cache Scans - Days (integer, default=3)mde_count InQuest Malware Discovery Engine InQuest MDE: Process Count (integer, default=10, max=20)mde_debug InQuest Malware Discovery Engine InQuest MDE: Debug Logging (0/1, default=0)mde_engine_filters InQuest Malware Discovery Engine InQuest MDE Filters: Disable Engine Filters (0/1 default=0)mde_global_filters InQuest Malware Discovery Engine InQuest MDE Filters: Disable Global Filters (0/1 default=0)mde_syslog_host InQuest Malware Discovery Engine InQuest MDE: Syslog Host(s) & Port(s) (ip:port[, ip:port])mde_tz_offset InQuest Malware Discovery Engine InQuest MDE Controls: Syslog Host(s) GMT Offset (+/- integer, default=-0)inquestmultiav_api InQuest MultiAV Eyelet MultiAV Hosting: API Key (api key, default=none)inquestmultiav_cache_days InQuest MultiAV Eyelet MultiAV InQuest Controls: Cache Scans - Days (integer, default=3)inquestmultiav_count InQuest MultiAV Eyelet MultiAV InQuest Controls: Process Count (integer, default=10, max=20)inquestmultiav_debug InQuest MultiAV Eyelet MultiAV InQuest Controls: Debug Logging (0/1, default=0)inquestmultiav_engine_disqualifiers InQuest MultiAV Eyelet MultiAV InQuest Filters: Disable Engine Disqualifiers (0/1 default=0)inquestmultiav_engine_filters InQuest MultiAV Eyelet MultiAV InQuest Filters: Disable Engine Filters (0/1 default=0)inquestmultiav_global_filters InQuest MultiAV Eyelet MultiAV InQuest Filters: Disable Global Filters (0/1 default=0)inquestmultiav_hash_per_request InQuest MultiAV Eyelet MultiAV InQuest Controls: Hashes per Request (integer, default=20)inquestmultiav_max_queue InQuest MultiAV Eyelet MultiAV InQuest Controls: Max Queue Size - Alert Threshold (integer, default=5000)inquestmultiav_no_syslog InQuest MultiAV Eyelet MultiAV InQuest Controls: Disable CEF Messages (0/1, default=0)inquestmultiav_protocol InQuest MultiAV Eyelet MultiAV Hosting: Remote Protocol (http/https default=https)inquestmultiav_remote_host InQuest MultiAV Eyelet MultiAV Hosting: Remote Host (default=eyelet.inquest.net)inquestmultiav_remote_port InQuest MultiAV Eyelet MultiAV Hosting: Remote Port (default=443)inquestmultiav_syslog_host InQuest MultiAV Eyelet MultiAV InQuest Controls: Syslog Host(s) & Port(s) (ip:port[, ip:port])inquestmultiav_tz_offset InQuest MultiAV Eyelet MultiAV InQuest Controls: Syslog Host(s) GMT Offset (+/- integer, default=-0)retrohunt_no_syslog InQuest RetroHunt Historic TDE RetroHunt: Prevent CEF messages from being sent (true/false, default=false)retrohunt_syslog_host InQuest RetroHunt Historic TDE RetroHunt: Syslog Host(s) & Port(s) (ip:port[, ip:port])retrohunt_tz_offset InQuest RetroHunt Historic TDE RetroHunt Syslog Host(s) GMT Offset: (+/- integer, default=-0)retrohunt_weeks InQuest RetroHunt Historic TDE RetroHunt: Number of weeks to historically analyze (integer, default=2)apply_codepack_alert InQuest Threat Discovery Engine Alerts: Software update applied (true/false, default=true)blacklist_no_syslog InQuest Threat Discovery Engine Blacklist: Prevent CEF messages from being sent (true/false, default=false)blacklist_syslog_host InQuest Threat Discovery Engine Blacklist: Syslog Host(s) & Port(s) (ip:port[, ip:port])connection_timeout InQuest Threat Discovery Engine Capture: Connection Table Timeout (number, default=60)tde_count InQuest Threat Discovery Engine InQuest Threat Discovery Engine: Number of file analysis threadsyara_no_syslog InQuest Threat Discovery Engine InQuest Threat Detection Engine: Prevent CEF messages from being sent (true/false, default=false)yara_syslog_host InQuest Threat Discovery Engine InQuest Threat Detection Engine: Syslog Host(s) & Port(s) (ip:port[, ip:port])yara_tz_offset InQuest Threat Discovery Engine InQuest Threat Detection Engine: Syslog Host(s) GMT Offset: (+/- integer, default=-0)threat_exchange_debug InQuest Threat Exchange Eyelet Threat Exchange InQuest Controls: Debug Logging (0/1, default=0)threat_post_count InQuest Threat Exchange Eyelet Threat Push InQuest Controls: Process Count (integer, default=2, max=10)threat_query_count InQuest Threat Exchange Eyelet Threat Query InQuest Controls: Process Count (integer, default=3, max=10)joe_auto_submit Joe Sandbox Joe Sandbox: Automatically submit files (true/false, default=false)joe_key Joe Sandbox Joe Sandbox: API Key for authenticationjoe_mime_include Joe Sandbox Joe Sandbox: Only submit these MIME types (comma separated, default=all)joe_no_syslog Joe Sandbox Joe Sandbox: Prevent CEF messages from being sent (true/false, default=false)joe_report_alert Joe Sandbox Alerts: Joe report received (true/false, default=false)joe_syslog_host Joe Sandbox Joe Sandbox: Syslog Host(s) & Port(s) (ip:port[, ip:port])joe_threatscore_eq Joe Sandbox Joe Sandbox: Exclude files that already have a Threat Score equal to this (default=none)joe_threatscore_gt Joe Sandbox Joe Sandbox: Exclude files that already have a Threat Score greater than this (default=10)joe_threatscore_lt Joe Sandbox Joe Sandbox: Exclude files that already have a Threat Score less than this (default=0)joe_url Joe Sandbox Joe Sandbox: URL for the Joe Sandbox API (eg. http://10.0.0.10/joesandbox/index.php/api, default=Joe Cloud)joe_use_proxy Joe Sandbox Joe Sandbox: Use global proxy settings (true/false, default=false)joe_vlan_include Joe Sandbox Joe Sandbox: Only submit from these VLAN IDs or ranges (comma separated, default=all)opswat_apikey OPSWAT Metadefender Core OPSWAT Metadefender Core Hosting: API Key (api key, default=none)opswat_cache_days OPSWAT Metadefender Core OPSWAT InQuest Controls: Cache Scans - Days (integer, default=3)opswat_count OPSWAT Metadefender Core OPSWAT InQuest Controls: Process Count (integer, default=10, max=20)opswat_debug OPSWAT Metadefender Core OPSWAT InQuest Controls: Debug Logging (0/1, default=0)opswat_enable_proxies OPSWAT Metadefender Core OPSWAT InQuest Controls: Use global proxy settings (0/1 default=0)opswat_engine_disqualifiers OPSWAT Metadefender Core OPSWAT InQuest Filters: Disable Engine Disqualifiers (0/1 default=0)opswat_engine_filters OPSWAT Metadefender Core OPSWAT InQuest Filters: Disable Engine Filters (0/1 default=0)opswat_engine_weights OPSWAT Metadefender Core OPSWAT InQuest Filters: Disable Engine Weights (0/1 default=0)opswat_global_filters OPSWAT Metadefender Core OPSWAT InQuest Filters: Disable Global Filters (0/1 default=0)opswat_host OPSWAT Metadefender Core OPSWAT Metadefender Core Hosting: Remote Host (ip/hostname, default=none)opswat_max_queue OPSWAT Metadefender Core OPSWAT InQuest Controls: Max Queue Size - Alert Threshold (integer, default=5000)opswat_metascan_uri OPSWAT Metadefender Core OPSWAT Metadefender Core Hosting: Remote URI (uri, default=/metascan_rest)opswat_port OPSWAT Metadefender Core OPSWAT Metadefender Core Hosting: Remote Port (port, default=8008)opswat_protocol OPSWAT Metadefender Core OPSWAT Metadefender Core Hosting: Remote Protocol (http/https, default=https)opswat_syslog_host OPSWAT Metadefender Core OPSWAT InQuest Controls: Syslog Host(s) & Port(s) (ip:port[, ip:port])opswat_tz_offset OPSWAT Metadefender Core OPSWAT InQuest Controls: Syslog Host(s) GMT Offset (+/- integer, default=-0)snmpv3_algorithm SNMP SNMPv3: Encryption Algorithm (DES or AES, default=DES)snmpv3_digest SNMP SNMPv3: Digest Algorithm (MD5 or SHA, default=MD5)snmpv3_password SNMP SNMPv3: Password (string, default=none)snmpv3_security_level SNMP SNMPv3: Trap Security Levelsnmpv3_user SNMP SNMPv3: Username (string, default=none)snmp_community SNMP SNMP: Community Name (string, default=none)snmp_source SNMP SNMP: Allowed Source Networks (comma separated list of IPs or subnets, default=none)snmp_trap_address SNMP SNMP: Trap Destination Address (address, default=none)snmp_trap_community SNMP SNMP: Trap Community (string, default=none)snmp_trap_digest SNMP SNMPv3: Trap Digest Algorithm (MD5 or SHA, default=MD5)snmp_trap_engine_id SNMP SNMPv3: Trap Local Engine ID (any, default=none)snmp_trap_pass SNMP SNMPv3: Trap Password (string, default=none)snmp_trap_port SNMP SNMP: Trap Destination Port (port, default=none)snmp_trap_privpass SNMP SNMPv3: Trap privacy password (string, default=same as trap password)snmp_trap_user SNMP SNMPv3: Trap User (string, default=none)system_contact SNMP SNMP: System Maintenance Contact (string, default=none)system_location SNMP SNMP: System Physical Location (string, default=none)tippingpoint_api_key TippingPoint SMS TippingPoint SMS: API key for the TippingPoint SMS API.tippingpoint_url TippingPoint SMS TippingPoint SMS: URL for the TippingPoint SMS API (eg. https://10.10.10.10:443)tippingpoint_use_proxy TippingPoint SMS TippingPoint SMS: Use global proxy settings (true/false, default=false)virustotal_api VirusTotal VirusTotal Hosting: API Key (private api key, default=none)virustotal_cache_days VirusTotal VT InQuest Controls: Cache Scans - Days (integer, default=3)virustotal_count VirusTotal VirusTotal InQuest Controls: Process Count (integer, default=10, max=20)virustotal_debug VirusTotal VT InQuest Controls: Debug Logging (0/1, default=0)virustotal_engine_disqualifiers VirusTotal VT InQuest Filters: Disable Engine Disqualifiers (0/1 default=0)virustotal_engine_filters VirusTotal VT InQuest Filters: Disable Engine Filters (0/1 default=0)virustotal_engine_weights VirusTotal VT InQuest Filters: Disable Engine Weights (0/1 default=0)virustotal_global_filters VirusTotal VT InQuest Filters: Disable Global Filters (0/1 default=0)virustotal_hash_per_request VirusTotal VT InQuest Controls: Hashes per Request (integer, default=20)virustotal_max_queue VirusTotal VT InQuest Controls: Max Queue Size - Alert Threshold (integer, default=5000)virustotal_no_syslog VirusTotal VT InQuest Controls: Disable CEF Messages (0/1, default=0)virustotal_protocol VirusTotal VirusTotal Hosting: Remote Protocol (http/https default=https)virustotal_remote_host VirusTotal VirusTotal Hosting: Remote Host (hostname, default=api.vtapi.net)virustotal_syslog_host VirusTotal VT InQuest Controls: Syslog Host(s) & Port(s) (ip:port[, ip:port])virustotal_tz_offset VirusTotal VT InQuest Controls: Syslog Host(s) GMT Offset (+/- integer, default=-0)vmray_api_key VMRay Analyzer VMRay Analyzer: API key for the VMRay Analyzer APIvmray_auto_submit VMRay Analyzer VMRay Analyzer: Automatically submit files (true/false, default=false)vmray_mime_include VMRay Analyzer VMRay Analyzer: Only submit these MIME types (comma separated, default=all)vmray_no_syslog VMRay Analyzer VMRay Analyzer: Prevent CEF messages from being sent (true/false, default=false)vmray_report_alert VMRay Analyzer Alerts: VMRay report received (true/false, default=false)vmray_syslog_host VMRay Analyzer VMRay Analyzer: Syslog Host(s) & Port(s) (ip:port[, ip:port])vmray_threatscore_eq VMRay Analyzer VMRay Analyzer: Exclude files that already have a Threat Score equal to this (default=none)vmray_threatscore_gt VMRay Analyzer VMRay Analyzer: Exclude files that already have a Threat Score greater than this (default=10)vmray_threatscore_lt VMRay Analyzer VMRay Analyzer: Exclude files that already have a Threat Score less than this (default=0)vmray_url VMRay Analyzer VMRay Analyzer: URL for the VMRay Analyzer API (default: https://cloud.vmray.com)vmray_use_proxy VMRay Analyzer VMRay Analyzer: Use global proxy settings (true/false, default=false)vmray_vlan_include VMRay Analyzer VMRay Analyzer: Only submit from these VLAN IDs or ranges (comma separated, default=all)wildfire_api_key WildFire Sandbox WildFire Sandbox: API key for the WildFire Sandbox API.wildfire_auto_submit WildFire Sandbox WildFire Sandbox: Automatically submit files (true/false, default=false)wildfire_mime_include WildFire Sandbox WildFire Sandbox: Only submit these MIME types (comma separated, default=all)wildfire_no_syslog WildFire Sandbox WildFire Sandbox: Prevent CEF messages from being sent (true/false, default=false)wildfire_report_alert WildFire Sandbox Alerts: WildFire report received (true/false, default=false)wildfire_syslog_host WildFire Sandbox WildFire Sandbox: Syslog Host(s) & Port(s) (ip:port[, ip:port])wildfire_threatscore_eq WildFire Sandbox WildFire Sandbox: Exclude files that already have a Threat Score equal to this (default=none)wildfire_threatscore_gt WildFire Sandbox WildFire Sandbox: Exclude files that already have a Threat Score greater than this (default=10)wildfire_threatscore_lt WildFire Sandbox WildFire Sandbox: Exclude files that already have a Threat Score less than this (default=0)wildfire_url WildFire Sandbox WildFire Sandbox: URL for the WildFire Sandbox API (eg. https://10.10.10.10:443)wildfire_use_proxy WildFire Sandbox WildFire Sandbox: Use global proxy settings (true/false, default=false)wildfire_vlan_include WildFire Sandbox WildFire Sandbox: Only submit from these VLAN IDs or ranges (comma separated, default=all)Note: In order for CEF messages to be generated, at least one user group other than the default Administrators group must be configured. The "Syslog" toggle on the edit user groups page will prevent CEF messages from being generated for a policy, provided that this option is disabled for every group associated with that policy. This option is enabled by default. For further information on editing user groups, see the Users and User Group Management guide

