Title
Create new category
Edit page index title
Edit category
Edit link
Threat Scoring
The MetaDefender NDR Threat Score Engine is a proprietary engine responsible for weighting a variety of inputs and outputting a single threat score along with a detailed "threat receipt" that provides an at-a-glance view of what subsystems provided intelligence that was or was not factored into the threat score.
Regardless of deployment (virtual, SaaS, appliance, mixed) the MetaDefender NDR Threat Score Engine receives and considers inputs from a variety of sources as depicted in the following example on-premise / appliance-based data-flow diagram:
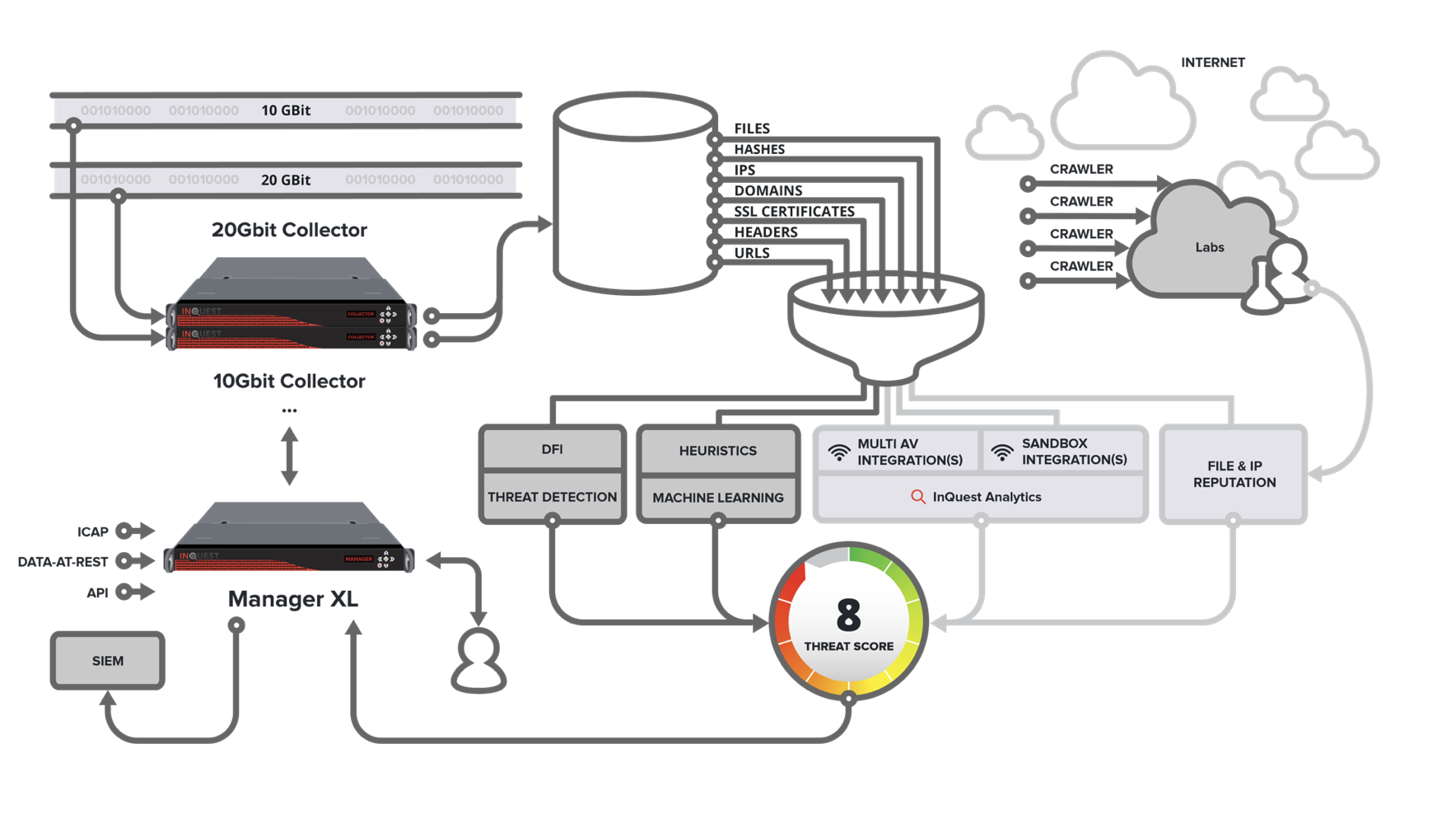
The source of inputs include:
- InQuest Deep File Inspection (DFI) and Threat Discovery Engine (TDE).
- InQuest heuristics extraction and machine learning.
- InQuest Malware Discovery Engine (MDE).
- Optional MultiAV integrations (OPSWAT, VirusTotal, InQuest Cloud MultiAV).
- Optional sandbox integrations (CrowdStrike Falcon, Cuckoo, FireEye AX, Joe Security, Palo Alto WildFire, VMRay Analyzer).
- Optional InQuest Cloud Reputation on IPs, domains, URLs, and file hashes.
As depicted in the diagram above, artifacts (files, hashes, IPs, domains, URLs, SSL certs, HTTP/SMTP headers) are processed by a number of onboard, optional cloud, and optional third-party subsystems. The results from each of these subsystems is then analyzed and processed by the MetaDefender NDR Threat Score Engine.
Administrators should note that there are a variety of configuration options, reachable from the devices and filtration panels that can be leveraged to tune the file types (by MIME) each of the subsystems accepts. Additionally, some integrations, such as MultiAV offer tunables for disabling the default-on InQuest analytics layer. Weighing each AV vendor and their named results based on empirical observations made by InQuest Labs over the year.
The threat score is accompanied by a detailed receipt that outlines, at a glance, what subsystems provided intelligence that was factored into the resulting threat or exposure score for the underlying session and files. There are green and yellow flags, as depicted here:
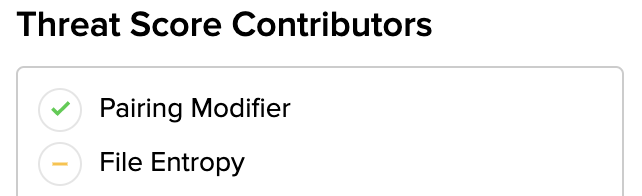
Green indicates that the subsystem provided intelligence that moved the threat score in either in a positive or negative direction. Yellow, indicates that the subsystem provided intelligence but it did not affect the over-arching threat score. Rather, that subsystem provided supporting evidence. A more robust threat receipt is a good indicator of a true positive. Subsystems that did no provide any pertinent information are flagged as Red, seen here:
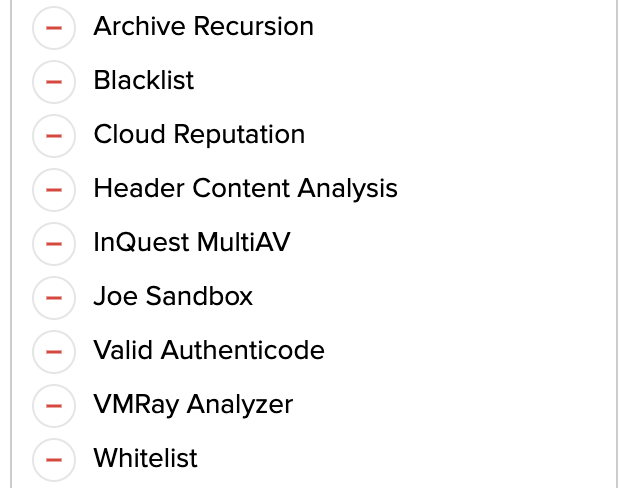
Finally, a Grey indicator is used to denote that the subsystem is either not enabled or was not available at the time of scanning the underlying session and files. Note that the Red and Grey indicators are hidden by default but can be expanded on click.