Title
Create new category
Edit page index title
Edit category
Edit link
Blacklist
Blacklisting refers to a basic access control mechanism you can configure to block content from the network because they are deemed to be suspicious by the analysts. To use the blacklisting feature, add one or more hashes and set their threat scores. Even if there are no other suspicious indicators from these files, threat scores are applied as a base for the entire session and alerts are displayed.
Adding Hashes to the Blacklist
- Click Policy > Blacklist.
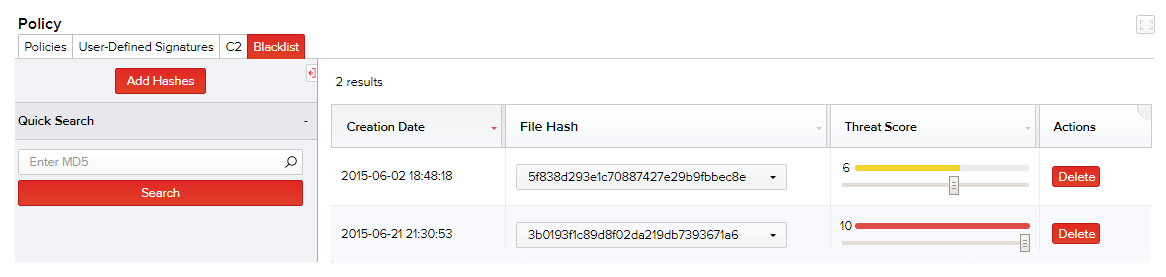
- To add one or more MD5s to the blacklist, click Add Hashes. Enter the hash(es) and click Add.
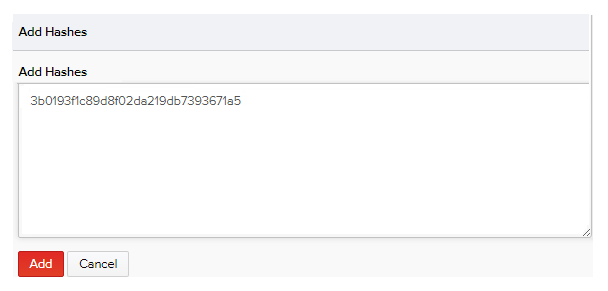
Files with the specified hash/MD5 are added blacklisted and are displayed in the top row of the list with threat score as 10 by default.
- Drag the threat score bar to set the threat score as required.
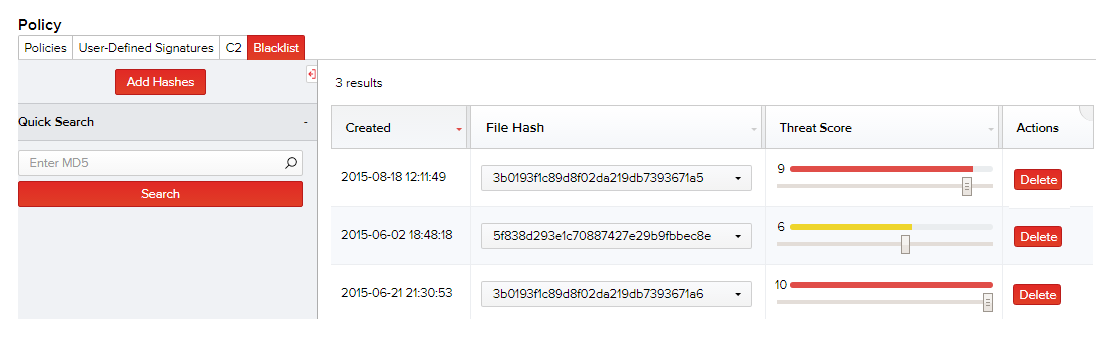
You can use the Quick Search feature to search and locate specific hashes and blacklist them, by typing partial or full text of the hash. For more information on using this feature, refer the Session Analysis section.
To remove a hash from the blacklist, click the Delete button of that hash, then click Delete again.

