Title
Create new category
Edit page index title
Edit category
Edit link
Performance Tuning Recommendations
For general performance tuning and system resource preservation, OPSWAT recommends you to perform the following:
- Exclude specific MIME Types when a large number of files of a specific file type are constantly waiting to be scanned. A good example of this occurring are in environments where a good portion of the traffic is streaming video. Also exclude file types that may not be a threat to your computing environment.
- Exclude sites that pose little to no threat to your environment such as those that provide reputable streaming media services that are regularly visited by your users.
- Whitelist specific hashes at the traffic collection-level which are known good.
- Activate the whitenoise hashes with the highest tallies.
MIME Exceptions
When third-party integrations are enabled, they are provided all files captured by the MetaDefender NDR engine from both HTTP and SMTP sessions. If you see any indication in the host status that the integrations are unable to process the number of files being sent to them, it is recommended to filter those MIME Types from being analyzed to ensure the system does not become oversubscribed.
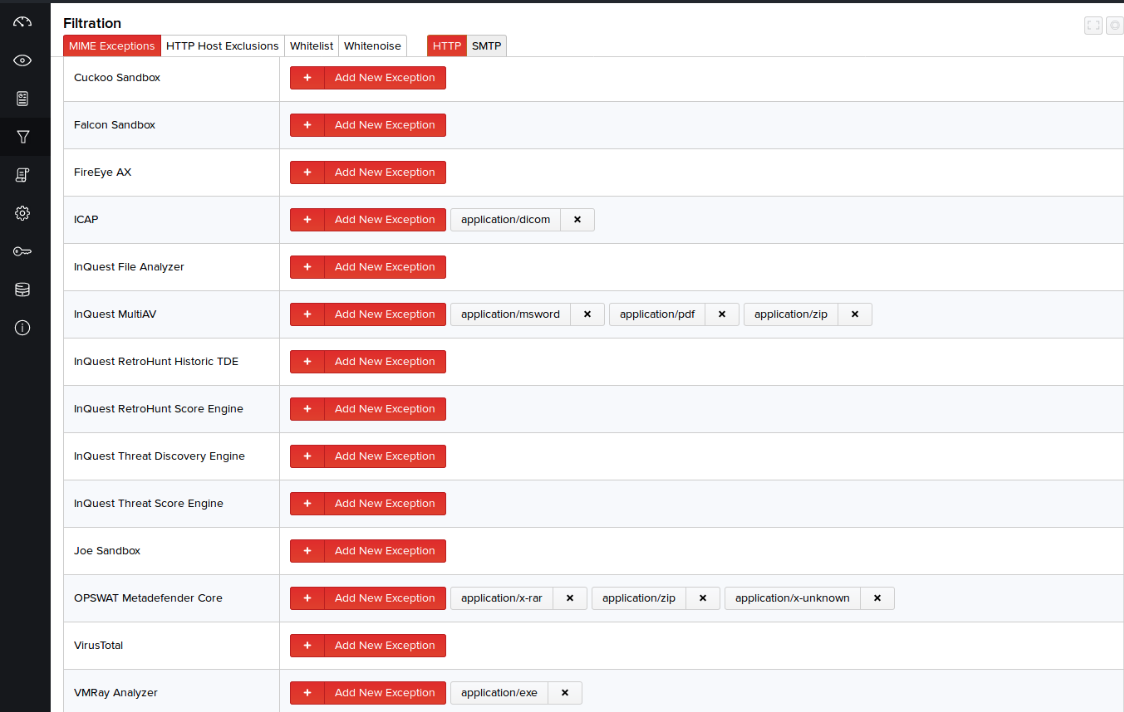
- Click Filtration > MIME Exceptions.
- Click the HTTP or SMTP protocol tab as required. By default, integrations for MetaDefender NDR File Threat Discovery Engine and MetaDefender NDR File Analyzer are enabled.
- Click Add New Exception and select the MIME Type corresponding to specific integrations/suppliers. Files with those MIME Type received over the selected protocol will no longer be scanned by those suppliers.
HTTP Host Exclusions
As traffic is captured and the file content is extracted and analyzed, it may become apparent based on the host status measures that heavily trafficked sites, such as those that provide streaming media services, may be causing a significant amount of system resource consumption. In situations where that is the case, it may be necessary to exclude such hosts from collection.
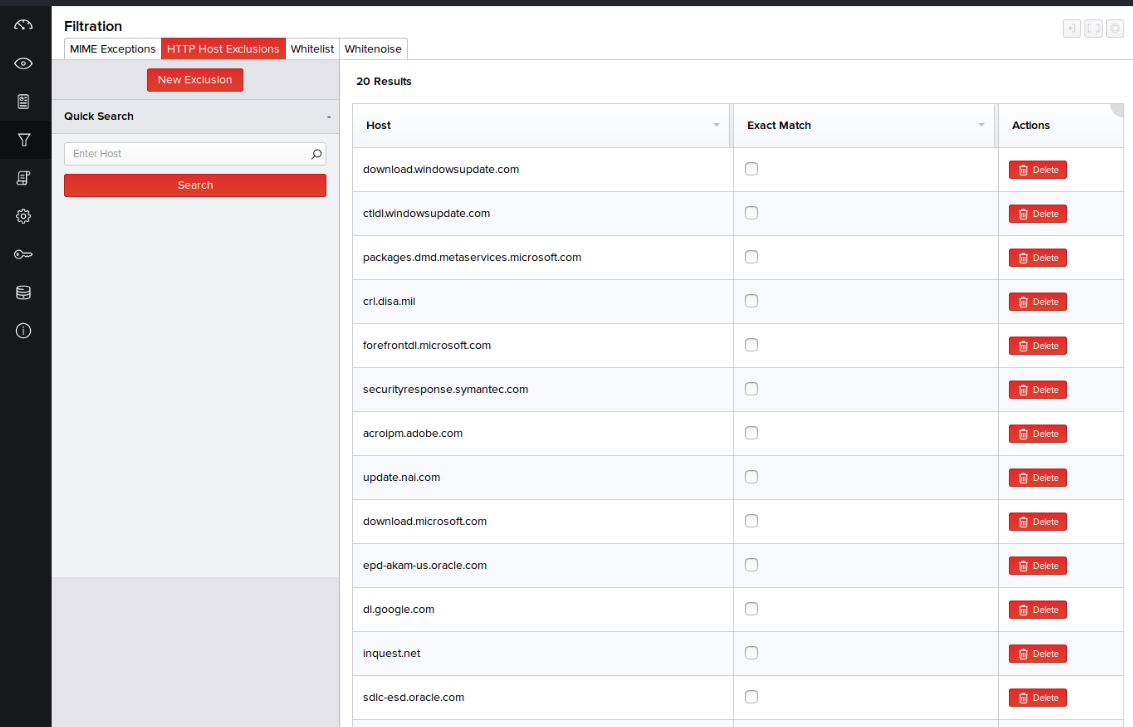
- Click Filtration > HTTP Host Exclusions.
- Click New Exclusion on the left pane.
- In the right pane, enter the host or TLD to be excluded from scan, and click Add. The collection services re-launch and ignore content from sites containing the TLD entered.
By default, MetaDefender NDR Managers will exclude the following hosts from analysis:
- acroipm.adobe.com
- agsupdate.adobe.com
- crl.disa.mil
- ctldl.windowsupdate.com
- dl.google.com
- download.mcafee.com
- downloadcenter.mcafee.com
- download.microsoft.com
- download.nai.com
- download.windowsupdate.com
- epd-akam-us.oracle.com
- forefrontdl.microsoft.com
- inquest.net
- packages.dmd.metaservices.microsoft.com
- sdlc-esd.oracle.com
- securityresponse.symantec.com
- sync.bigfix.com
- update.nai.com
- crl.godaddy.com
- crl3.digicert.com
- crl.startssl.com
- crl.usertrust.com
- gtssl-crl.geotrust.com
- crl.comodoca.com
- crl.omniroot.com
- SVRSecure-G3-crl.verisign.com
- gtssl2-crl.geotrust.com
- EVIntl-crl.verisign.com
- SVRIntl-G3-crl.verisign.com
- EVSecure-crl.verisign.com
- crl.globalsign.com
- crl4.digicert.com
- pki.google.com
- crl-ssl.certificat2.com
- crl.microsoft.com
- mscrl.microsoft.com
- sd.symcb.com
- svr-sgc-crl.thawte.com
- crl.entrust.net
- crl.netsolssl.com
- crl2.netsolssl.com
- crl.certum.pl
- rapidssl-crl.geotrust.com
- crl.globessl.com
- crl.e-szigno.hu
- crl.trustwave.com
- crl.tcs.terena.org
- crl.starfieldtech.com
- gtssldv-crl.geotrust.com
- crl.siteblindadocerts.com
- crl.ssl.com
- svr-dv-crl.thawte.com
- svr-ov-crl.thawte.com
- repo1.secomtrust.net
- crl.incommon.org
- certificates.godaddy.com
- crl.ca.vodafone.com
- crl.cacert.org
- SVRIntl-crl.verisign.com
- hasbro.com
- intel.com
- postsignum.cz
- sureseries-crl.cybertrust.ne.jp
- crl.comodo.net
- crl.cs.auscert.org.au
- crl.csctrustedsecure.com
- crl.europeanssl.eu
- crl.gandi.net
- crl.geotrust.com
- crl.quovadisglobal.com
- crl.register.com
- crl.securetrust.com
- crl.serverpass.telesec.de
- crl.thawte.com
- crl.trendmicro.com
- crl.xi.tcclass2-ii.trustcenter.de
- crl2.alphassl.com
- evssl-crl.geotrust.com
- SVRSecure-G2-crl.verisign.com
- crl.pki.goog
- crl.apple.com
- crls.yandex.net
- crls1.wosign.com
- gn.symcb.com
- gv.symcb.com
- ss.symcb.com
- yandex.crl.certum.pl
- crl.securebusinessservices.com
- startssl.com
- crl.verisign.com
- crl.globalsign.net
- public-trust.com
- crl1.netlock.hu
- EVSecure-crl.geotrust.com
- trustcenter-crl.certificat2.com
- certplus.com
- crl.webspace-forum.de
- crl.swisssign.net
- crl.tcclass2-ii.trustcenter.de
- telstra-crl.pki.telstra.com.au
- repository.secomtrust.net
- crl.sgssl.net
- SVRSecure-crl.verisign.com
- cdp1.public-trust.com
- certificates.starfieldtech.com
- crl1.hongkongpost.gov.hk
- crl.crosstrust.net
- ldap2.sheca.com
- ssignadcrl01.jcsinc.co.jp
- netrustconnector.netrust.net
- cnnic.cn
- gca.nat.gov.tw
- grca.nat.gov.tw
- crl.globalSign.net
- crl.identrust.com
- trustcenter.de
- crl.ford.com
- crl.rsasecurity.com
- pks.experian.com
- crl.pki.abb.com
- crl.pki.wellsfargo.com
- crl.aetna.com
- pki.saic.com
- ch.siemens.com
- tcs-ca.tcs.com
- cadence.com
- crl.tbs-internet.com
- cdp1.pca.dfn.de
- cdp2.pca.dfn.de
- pki.telesec.de
- crl.pki.fraunhofer.de
- cdp1.com-strong-id.net
- crl.camerfirma.com
- a-cert.at
- igc.application.developpement-durable.gouv.fr
- lsu.edu
- crl.pkioverheid.nl
- portal.actalis.it
- proxy.fineid.fi
- caps.fujixerox.co.jp
- crl.digi-sign.com
- swissdigicert.ch
- crl.pki.saic.com
- crl.vodafone-pki.com
- epscd.catcert.net
- epscd2.catcert.net
- fedir.comsign.co.il
- sertifikati.ca.posta.rs
- ac.siger.gob.mx
- certificadodigital.com.br
- accv.es
- SVRSecure-T1-crl.verisign.com
- crl.globaltrust.it
- crl.pki.belgium.be
- crl.firmasicura.it
- justice.gouv.fr
- pki.admin.ch
- pki1.sempra.com
- igccrl.sante.gouv.fr
- correo.com.uy
- repository.publicca.hinet.net
- epki.com.tw
- multicert.com
- sigen-ca.si
- repositorio.icpbrasil.gov.br
- lcr.certificados.com.br
- crl.e-trust.be
- globaltrust.eu
- crl.firmaprofesional.com
- scrldp1.ica.cz
- cert.managedpki.com
- certicamara.com
- public.wisekey.com
- kamusm.gov.tr
- cert.fnmt.es
- crl.ix.tcclass3.tcuniversal-i.trustcenter.de
- crl.tcuniversal-I.trustcenter.de
- sigov-ca.gov.si
- gdcrl.gi-de.com
- e-szigno.hu
- crls.ecce.gov.pt
- crls.ecee.gov.pt
- postarca.posta.si
- certification.tn
- sbca.telesec.de
- crl.e-tugra.com
- ca.intesasanpaolo.com
- www2.postsignum.cz
- postsignum.ttc.cz
- crl.tcuniversal-III.trustcenter.de
- crl.certsign.ro
- pki.kasbank.com
- crl.marketware.eu
- fokozott.e-szigno.hu
- ra2a.ssc.lt
- ssc.lt
- qcrldp1.ica.cz
- e-me.lv
- eme.lv
- crl.izenpe.com
- crl.I.tcclass4.tcuniversal-III.trustcenter.de
- crl.oces.certifikat.dk
- crl.certigna.fr
- sk.ee
- crl.infonotary.com
- crl1.camerfirma.com
- csupdate.earthlink.net
- trustis.com
- vnec3.jcsinc.co.jp
- pki.dimc.dhs.gov
- fpkia.gsa.gov
- pki.nalco.com
- liberty.edu
- validation-trustcenter-crl.certificat2.com
- pki.registradores.org
- RootCA.twca.com.tw
- sslserver.twca.com.tw
- crl.affirmtrust.com
- ecar.parlamento.pt
- acabogacia.org
- cert-services.e-control.at
- sil.e-guven.com
- sr.symcb.com
- crl.sca1b.amazontrust.com
- cdp.rapidssl.com
- cdp.thawte.com
- gp.symcb.com
- cdp1.digicert.com
- cdp.geotrust.com
- tm.symcb.com
- clients1.google.com
- ocsp.ca.vodafone.com
- ocsp.gandi.net
- ocsp.incommon-rsa.org
- ocsp.msocsp.com
- ocsp.sca1b.amazontrust.com
- ocsp.trendmicro.com
- ocsp2.globalsign.com
- rapidssl-ocsp.geotrust.com
- yandex.ocsp-responder.com
- gn.symcd.com
- gp.symcd.com
- gt.symcd.com
- gu.symcd.com
- gv.symcd.com
- gz.symcd.com
- s2.symcb.com
- sd.symcd.com
- sh.symcd.com
- sr.symcd.com
- ss.symcd.com
- tg.symcd.com
- ti.symcd.com
- tj.symcd.com
- tn.symcd.com
- ocsp5.wosign.com
- ocsp6.wosign.com
- ocsp8.wosign.com
- ocsp.int-x1.letsencrypt.org
- ocsp.int-x2.letsencrypt.org
- ocsp.int-x3.letsencrypt.org
- ocsp.int-x4.letsencrypt.org
- ctrootsha2.ocsp.omniroot.com
- vassg141.ocsp.omniroot.com
- vassg142.ocsp.omniroot.com
- vpssg142.ocsp.omniroot.com
- commercial.ocsp.identrust.com
- ocsp.affirmtrust.com
- ocsp.comodoca.com
- ocsp.comodoca2.com
- ocsp.comodoca3.com
- ocsp.comodoca4.com
- ocsp.digicert.com
- ocsp.entrust.net
- ocsp.geotrust.com
- ocsp.globalsign.com
- ocsp.godaddy.com
- ocsp.netsolssl.com
- ocsp.omniroot.com
- ocsp.quovadisglobal.com
- ocsp.root-x1.letsencrypt.org
- ocsp.starfieldtech.com
- ocsp.startssl.com
- ocsp.swisssign.net
- ocsp.thawte.com
- ocsp.trust-provider.com
- ocsp.trustwave.com
- ocsp.usertrust.com
- ocsp.verisign.com
- ocsp.wosign.com
- ocsp.ws.symantec.com
- ocsp1.wosign.com
- ocsp2.wosign.cn
- detectportal.firefox.com
- msftconnecttest.com
- msftncsi.com
- captive.apple.com
- clients2.google.com
- clients3.google.com
- clients4.google.com
- clients5.google.com
- clients6.google.com
- gstatic.com
- ssl.gstatic.com
Whitelist
A set of common files that are deemed safe by analysts can be prevented from being examined or queued for scanning by the active integrations. In such cases, analysts may not want to see alerts generated for that file in the future and hence can whitelist them.
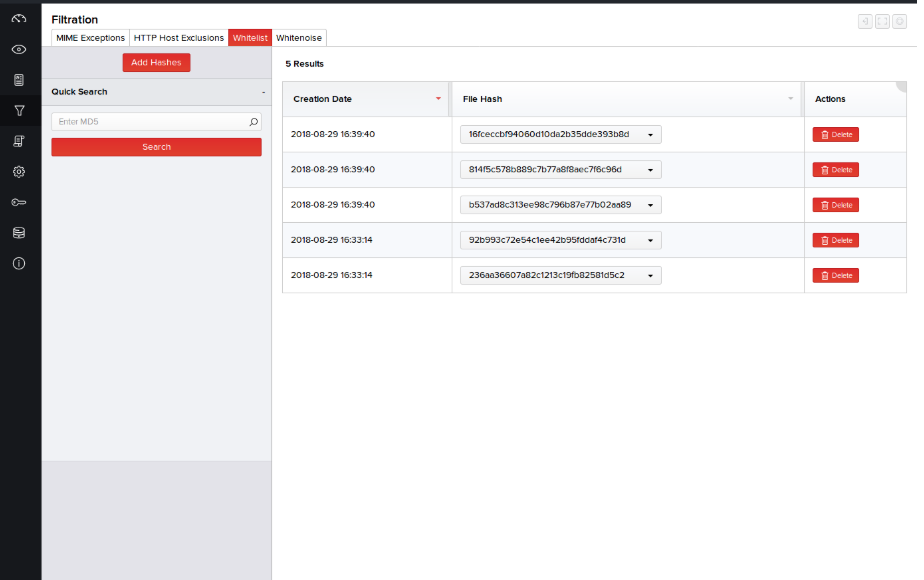
To add and activate one or more MD5 to the whitelist, perform the following steps:
- Click Filtration > Whitelist.
- Click Add Hashes on the left pane.
- Type the list of hashes to be excluded from scan; each separated by a comma, and click Add. Files with the specified MD5 are added to the whitelist and are displayed in the top row of the list.
Whitenoise
Whitenoise file entries can be observed and activated for general performance tuning which will reduce system load. For tuning purposes, MetaDefender NDR automatically maintains a tallied list of reoccurring hashes captured and creates entries for them on the Whitenoise tab of the Filtration page with an Inactive status. These MD5s/files must be manually reviewed before activation. The entries are automatically created based on the number of times files are seen in network traffic.
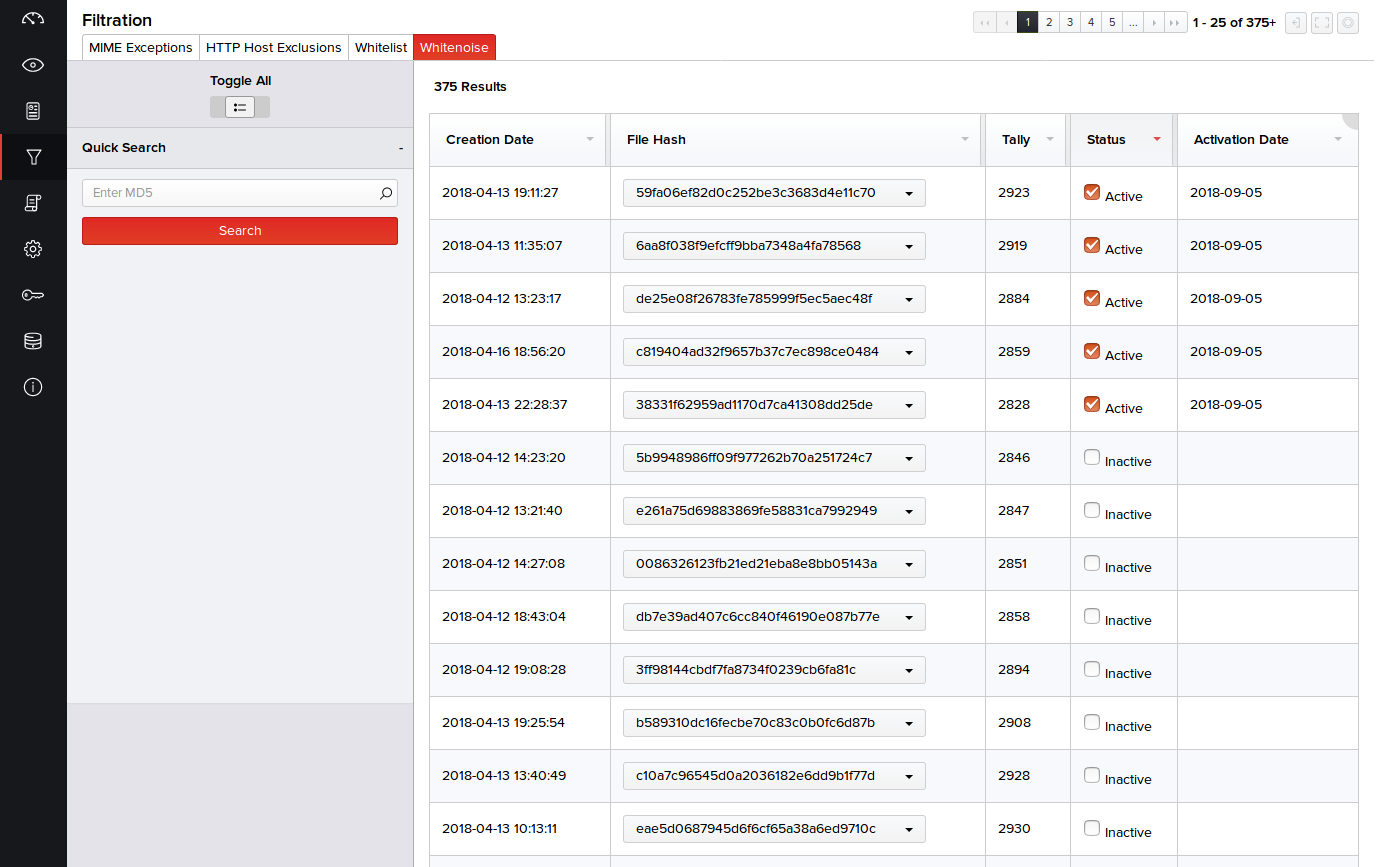
- Click Filtration > Whitenoise.
- Enable the Inactive status of the files by clicking their respective check boxes. The status instantly changes to Active and displays the activation date.
Once an MD5 is actively whitelisted, future occurrences of receipt will no longer be recorded by the system.
Tip: You can turn the Toggle All button on the left pane to On or Off to activate or deactivate the statuses of all MD5's respectively.

