Title
Create new category
Edit page index title
Edit category
Edit link
How to configure Role Mapping per groups in SSO Integration with Entra ID
Overview
When integrating MetaDefender Core with Microsoft Entra ID for Single Sign-On (SSO) authentication over SAML, user roles can be mapped in two primary ways:
- Assigning a default role to all users
- Configuring custom role mappings to support multiple roles across various user groups
This guide demonstrates how to assign specific MetaDefender Core roles to Entra ID groups.
Prerequisites
Before proceeding, ensure the following configurations are in place:
- Entra ID user-group mappings are already configured
- Groups are assigned to the SSO application
- MetaDefender Core SAML integration is completed
Step-by-Step Instructions
Step 1: Add a Group Claim in the SSO Application
Go to:
SAML Application → Single sign-on → Attributes & Claims → Edit
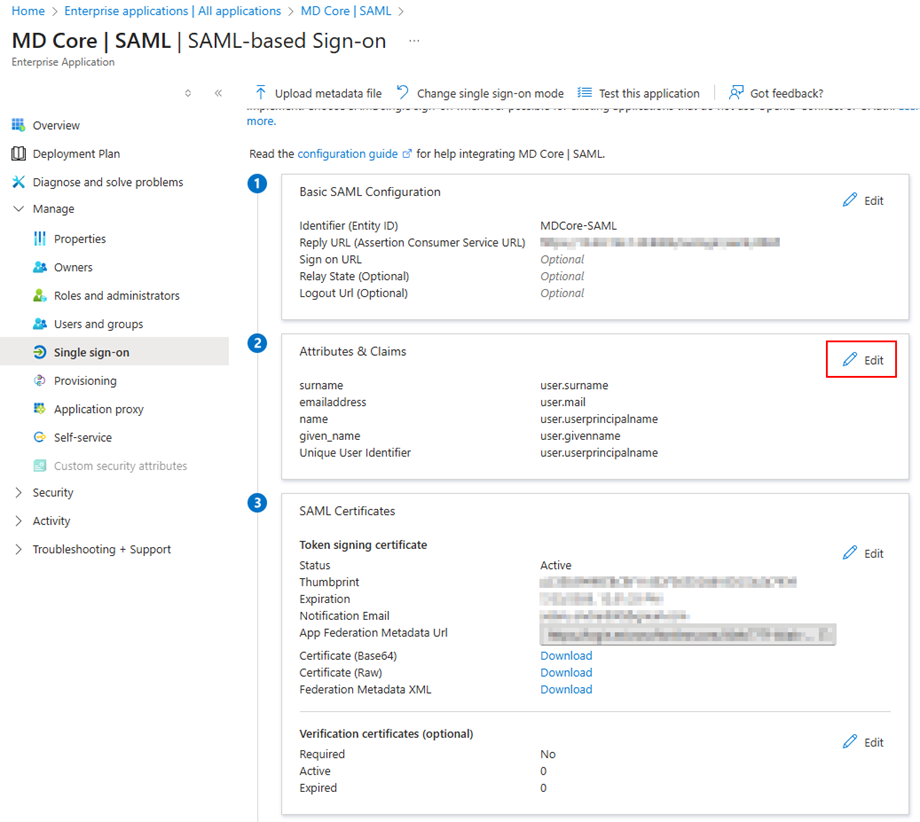
Then:
- Click Add a group claim
- Select All groups
- Click Save
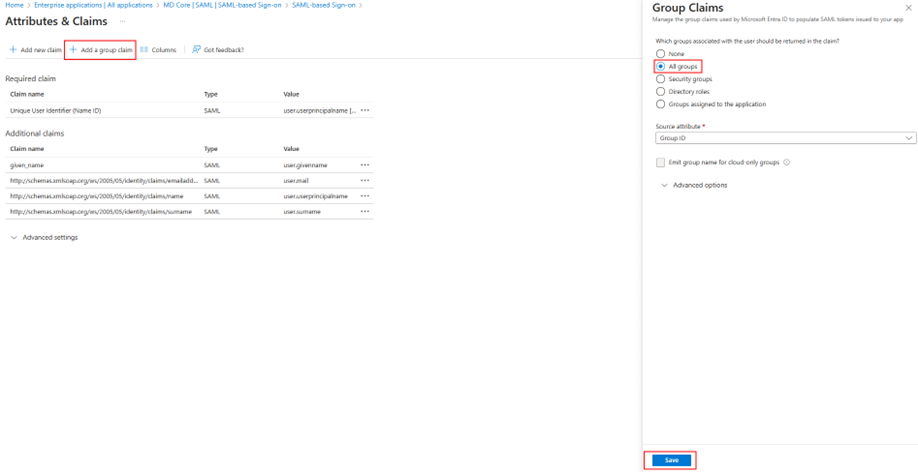
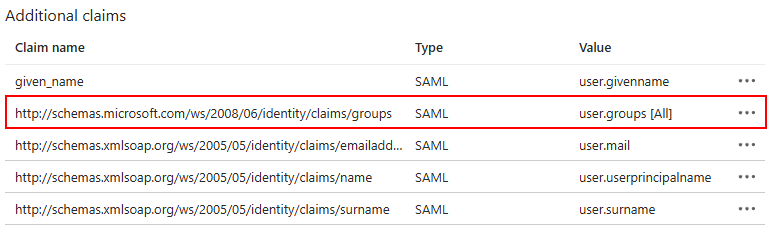
This creates the user.groups [All] claim, which provides a Claim URL. This URL will be used as the Key in the MetaDefender Core configuration.
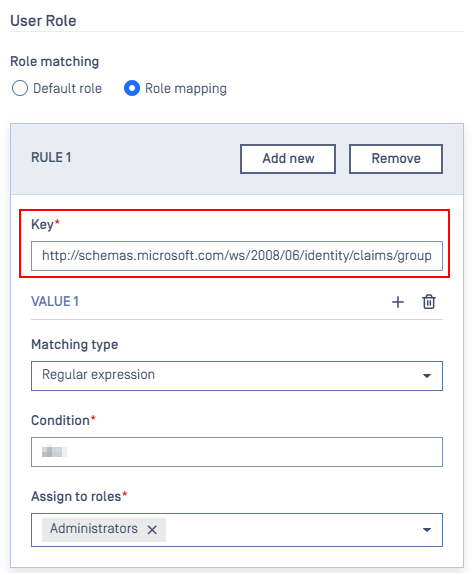
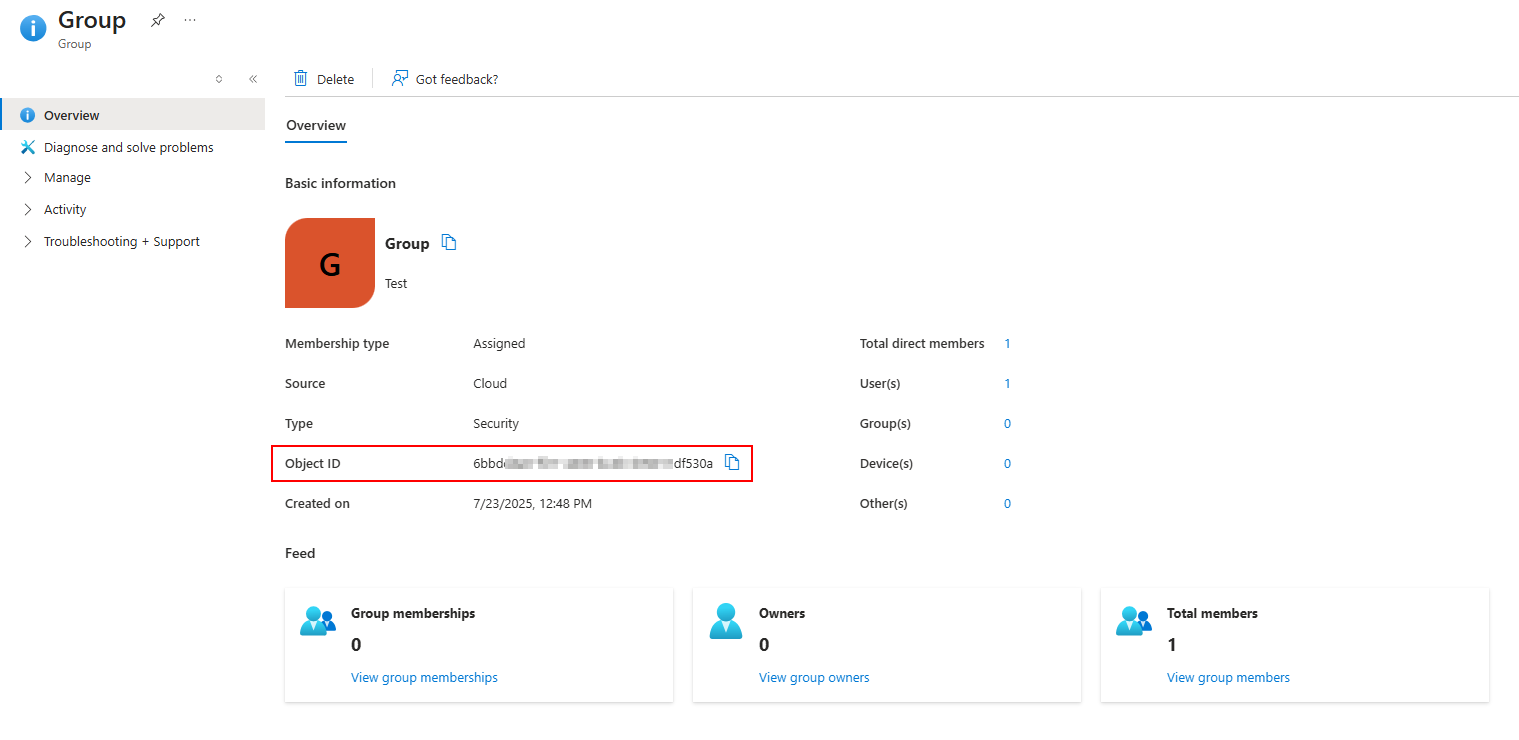
Step 2: Retrieve the Group’s Object ID
Return to the configured SAML application and select one of the assigned groups to view its details. This displays the group’s Object ID, which is needed to map roles in MetaDefender Core.
Use the following format in the Condition field to match the group by its Object ID:
^object_id$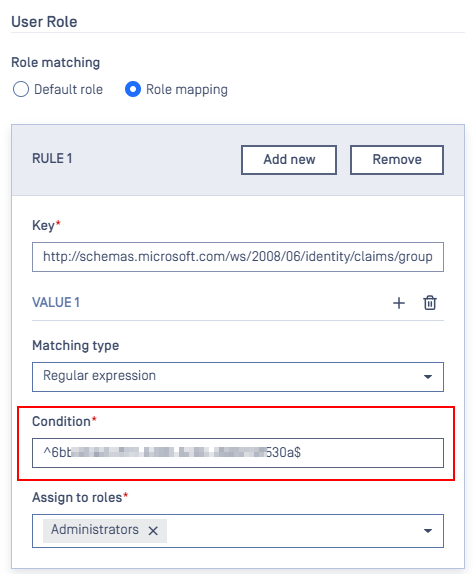
This pattern ensures only users from that specific group are matched.
Role Assignment Example
Using this configuration, all users in an Entra ID group (e.g., named Group) will be assigned the Administrator role in MetaDefender Core.
If a user belongs to multiple groups, and we have multiple role mappings, it will prioritize the first matching condition.
You can add more role-mapping rules using the same Key (the Claim URL) and different Conditions (Object IDs) to map additional groups to different roles.S
If Further Assistance is required, please proceed to log a support case or chatting with our support engineer.

