Installation
nac_v8.2.0
Search this version
Installation
Installation
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Dell Wired (URL redirect + ACL)
Copy Markdown
Open in ChatGPT
Open in Claude
Dell OS6 supports Dynamic ACLs with Redirect-ACLs and URL-Redirect starting with version 6.6.3.0. This can allow devices to be blocked and redirected to remediation pages without the need for a quarantine VLAN.
Below are example configuration commands for Dell OS6 switch:
Note – In this example the NAC RADIUS Server / Policy Server is <NAC-IP> (replace this <NAC-IP> with the IP of your NAC VM)
Note – Replace the VLAN number on the example port configuration with the desired default VLAN for the port.
x
####################################### Layer 3 DHCP prerequisites #######################################interface vlanX (Layer 3 interface for enforced network)ip helper-address X.X.X.X (DHCP server)ip helper-address <NAC-IP> (IP address of NAC Enforcer)!####################################### Layer 2 Switch Configuration ######################################## ACL configip access-list sc_initial_acl1000 permit everyexitip access-list sc_quarantine_acldeny udp any any eq domaindeny udp any any eq 67deny tcp any <NAC-IP> 0.0.0.0 eq httpdeny tcp any <NAC-IP> 0.0.0.0 eq 443deny tcp any <NAC-IP> 0.0.0.0 eq 8443deny tcp any 198.31.193.211 0.0.0.0 eq httpdeny tcp any 198.31.193.211 0.0.0.0 eq 443deny tcp any 198.31.193.211 0.0.0.0 eq 8443permit everyexit# RADIUS configaaa accounting dot1x default start-stop radiusaaa accounting update periodic 5authentication enableauthentication dynamic-vlan enabledot1x system-auth-controlaaa authentication dot1x default radiusaaa authorization network default radius!aaa server radius dynamic-authorclient <NAC-IP> server-key XXXXauth-type anyexit!radius server auth <NAC-IP>name "Default-RADIUS-Server"usage authmgrkey XXXXexit!radius server acct <NAC-IP>name "Default-RADIUS-Server"key XXXXexit!radius server vsa send authentication!ip device tracking!# HTTP/HTTPS Must be enabled for url-redirect VSAs from the NAC to have desired effect.ip http serverip http secure-server# Uplink ports and other ports except for test port (NAC enforcement will not be applied)interface GiX/X/Xdot1x port-control force-authorizedauthentication port-control force-authorizedexit!# Port for initial test client and later for other clients (NAC enforcement will be applied)interface GiY/Y/Y (client test port)switchport mode generalauthentication port-control autoauthentication host-mode multi-authauthentication max-users 2authentication periodicdot1x timeout tx-period 15dot1x max-reauth-req 1authentication order dot1xexitcopy running-config startup-config##################################################################### Examples of other types of ACL exceptions (if required): #####################################################################remark allow PXE bootdeny udp any host x.x.x.x eq tftpdeny udp any host x.x.x.x range 1025 5000remark allow authentication to domain controllerdeny tcp any host x.x.x.x eq 53deny udp any host x.x.x.x eq 53deny tcp any host x.x.x.x eq 88deny udp any host x.x.x.x eq 88deny udp any host x.x.x.x eq 123deny tcp any host x.x.x.x eq 135deny udp any host x.x.x.x eq 137deny tcp any host x.x.x.x eq 139deny tcp any host x.x.x.x eq 389deny udp any host x.x.x.x eq 389deny tcp any host x.x.x.x eq 445deny udp any host x.x.x.x eq 445deny tcp any host x.x.x.x eq 3268We can use the command below to check that a device connected to a given port is having the Redirect ACL applied properly.
console# show authentication clients gigabitethernet 1/0/24Interface...................................... Gi1/0/24Mac Address.................................... EC:F4:BB:D3:3C:DBUser Name...................................... Tester1VLAN Assigned Reason........................... RADIUS Assigned VLAN (1774)Host Mode...................................... multi-authMethod......................................... 802.1XControl Mode................................... autoSession time................................... 37484Session timeout ............................... 0Session Termination Action..................... DefaultFilter ID......................................RADIUS Framed IPv4/IPv6 address................DACL...........................................Redirect ACL................................... IP-REDIRECT-IN-00000004#dRedirect URL................................... https://portal.myweblogon.com:8443/deniedAccess.!^Acct SessionId................................. Tester1:1800000004From NAC:
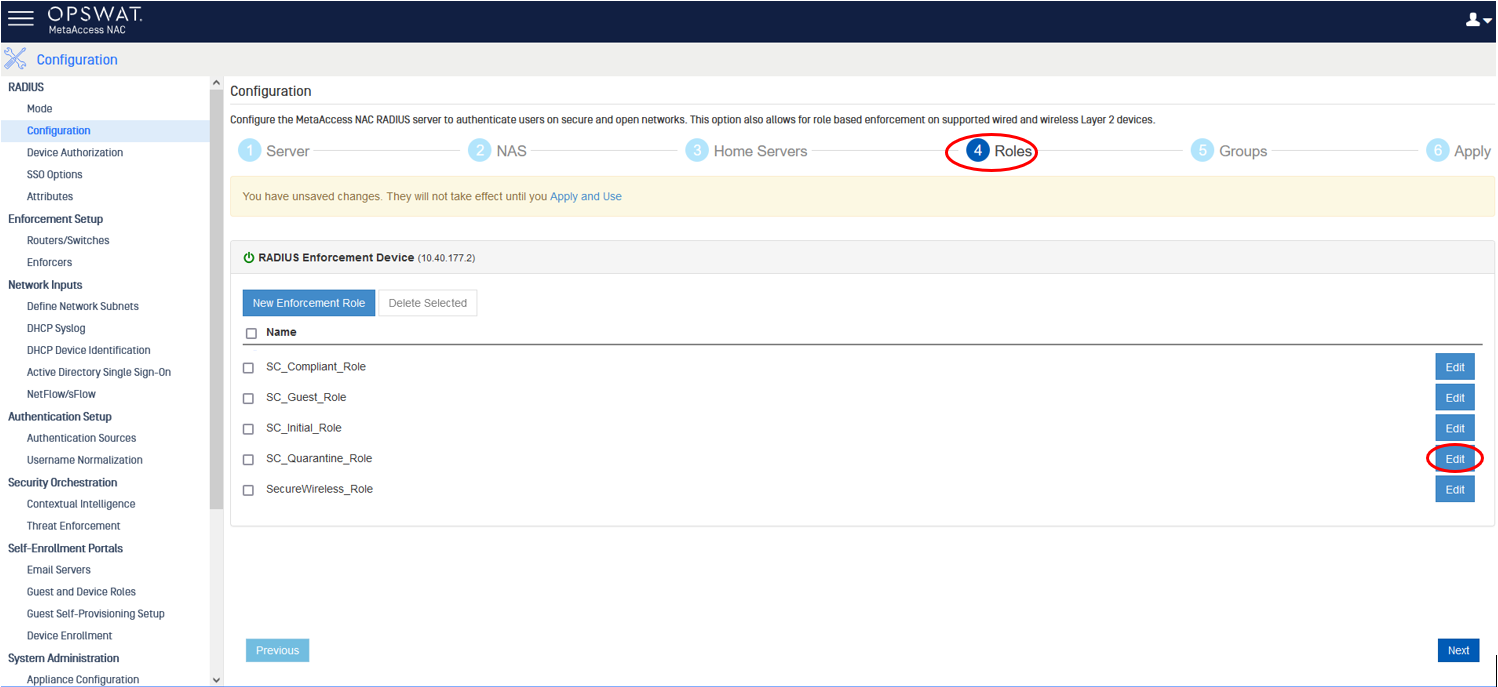
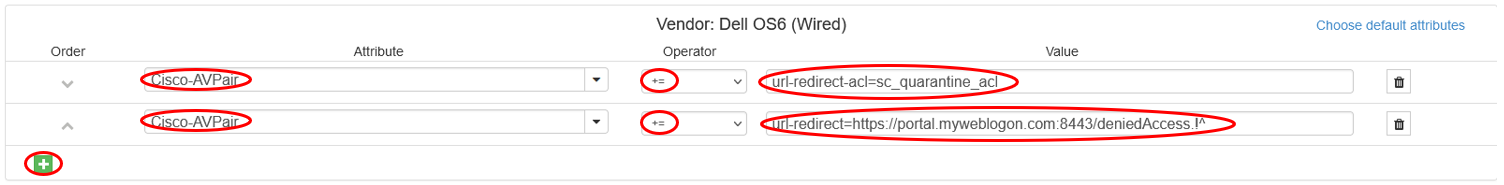
We can manually input Cisco-AVPair and the value.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
Aruba Wireless Controller ArubaOS 8Discard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

