- This article applies to all MetaDefender Core v5 and Email Gateway Security versions
Summary:
When updating OPSWAT MDCore modules, SSL handshake failures related to certificate chain issues may occur while accessing the update server https://update.dl.opswat.com. This article explains the cause and how to permanently resolve the issue.
Problem:
During failed update attempts, you may see logs like:
[WARNING] 2025.04.24 11:21:42.871: (common.communication) Certificate chain item, index='1', digest='""', issuerOrganization='QList("Amazon")', issuerOrganizationalUnitName='QList()', issuerCommonName='QList("Amazon Root CA 1")', subjectOrganization='QList("Amazon")', subjectOrganizationalUnitName='QList()', subjectCommonName='QList("Amazon RSA 2048 M02")' [msgid: 1221][WARNING] 2025.04.24 11:21:42.871: (common.communication) Certificate chain item, index='2', digest='""', issuerOrganization='QList("Starfield Technologies, Inc.")', issuerOrganizationalUnitName='QList()', issuerCommonName='QList("Starfield Services Root Certificate Authority - G2")', subjectOrganization='QList("Amazon")', subjectOrganizationalUnitName='QList()', subjectCommonName='QList("Amazon Root CA 1")' [msgid: 1221][WARNING] 2025.04.24 11:21:42.871: (common.communication) SSL error, error='The issuer certificate of a locally looked up certificate could not be found', errorCode='"The issuer certificate of a locally looked up certificate could not be found"' [msgid: 497]The server (update.dl.opswat.com) uses SSL certificates issued by Amazon's Certificate Authority (CA), typically Amazon Root CA 1 and possibly intermediates like Amazon RSA 2048 M02.
Since our update server utilizes a Content Delivery Network (CDN), the certificate chain presented at your geographic location may differ slightly from the one seen at OPSWAT Support.
Example:
| Location | Certificate Chain |
|---|---|
| Customer's Location | Amazon RSA 2048 M02 → Amazon Root CA 1 → Starfield Services Root CA G2 |
| OPSWAT Support Location | Amazon RSA 2048 M02 → Amazon Root CA 1 |
Because of this difference, your system might require trusting additional certificates such as the Starfield Services Root Certificate Authority - G2 to complete the SSL chain verification. This leads to consistent SSL handshake errors unless manually corrected.
Solution:
You must export the correct certificate chain from your environment and manually import the certificates into your local Trusted Root Certification Authorities store.
Step-by-Step Instructions
- Access the Update Server in Your Browser
- Open a browser (e.g., Microsoft Edge or Chrome).
- Visit: https://update.dl.opswat.com

- Export the Certificates
- Click on the security lock icon next to the address bar.
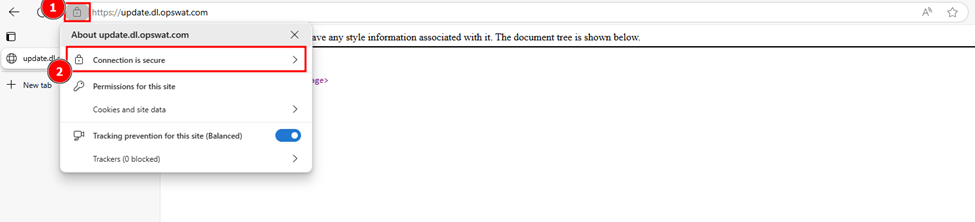
- View Certificate details.
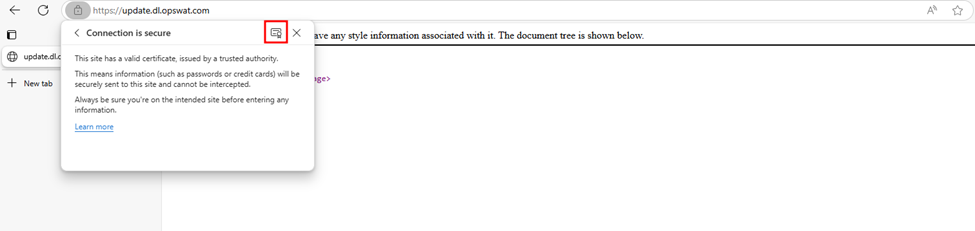
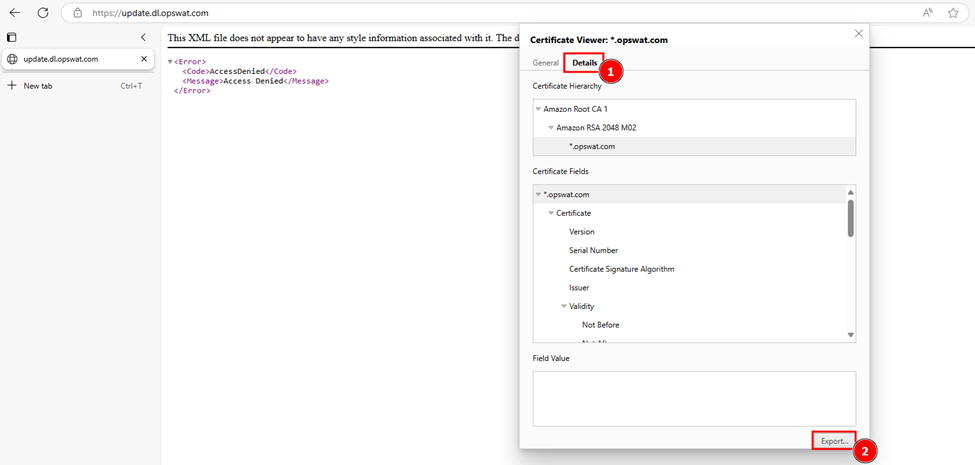
- Export the first certificate (subject certificate):
- Save it as
_.opswat.com.crt.
- Save it as
- Open the exported certificate file.
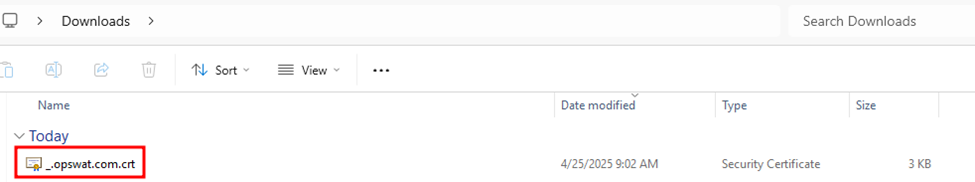
- Export the first certificate (subject certificate):
- In the certificate viewer, go to the Certification Path tab.
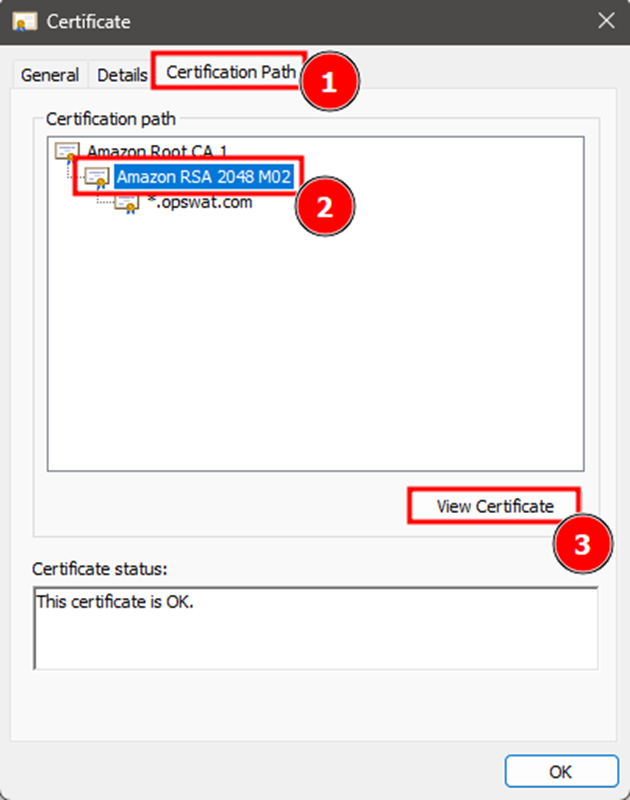
- Select the second certificate (the intermediate CA), then click View Certificate.
- Go to Details → Copy to File.
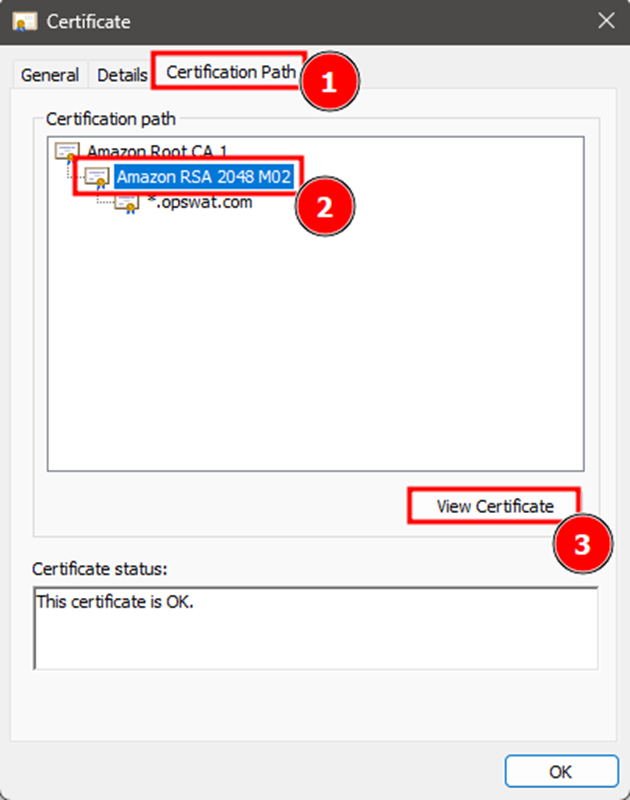
- Select Base-64 encoded X.509 (.CER) format.
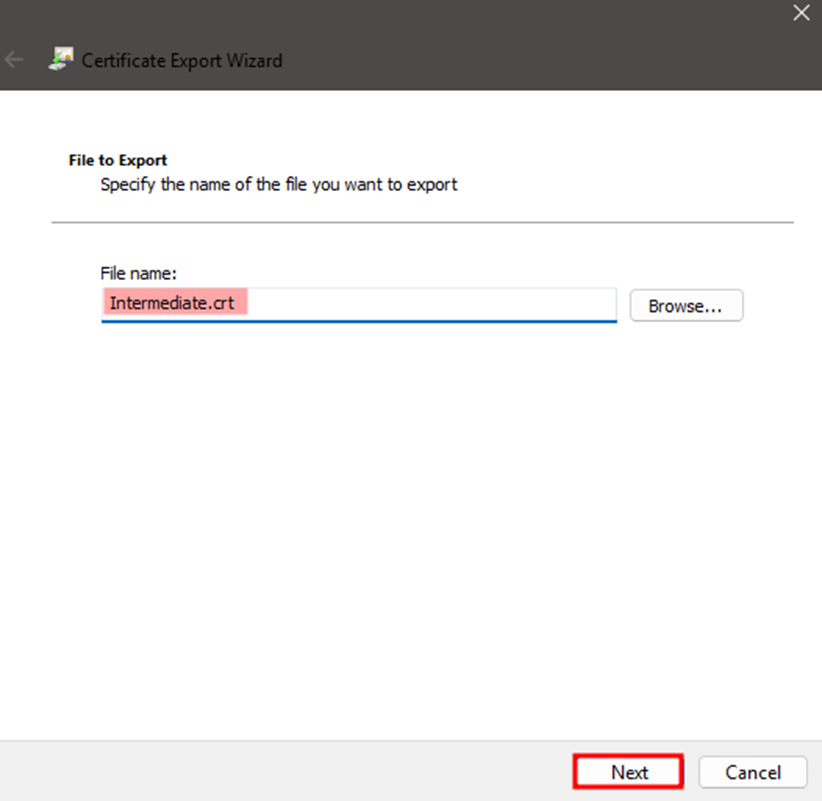
- Save it as
Intermediate.crt.
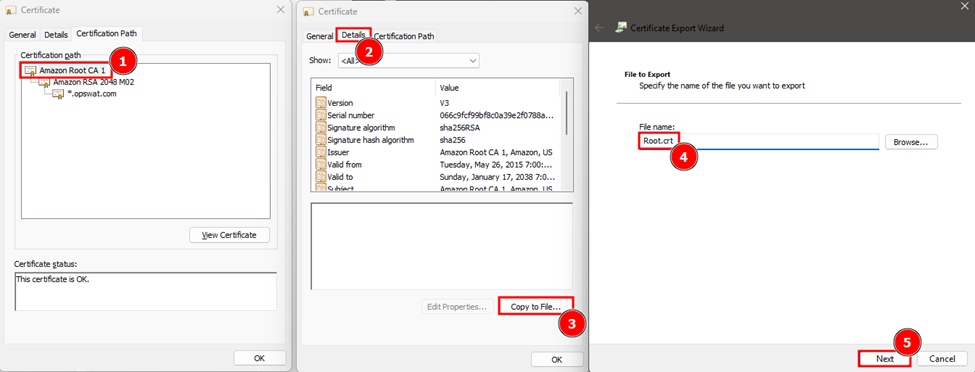
- Repeat the same process for the root certificate:
- Save it as
Root.crt.
- Save it as
You should now have three certificate files:
_.opswat.com.crt(subject/leaf)Intermediate.crt(intermediate CA)Root.crt(root CA)
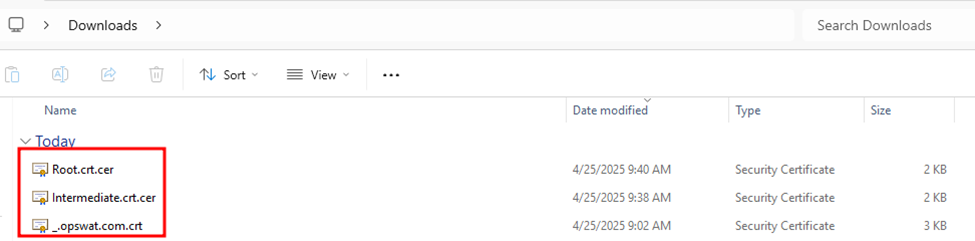
- Import Certificates into Trusted Root Certification Authorities
For each of the three certificates:
- Double-click the
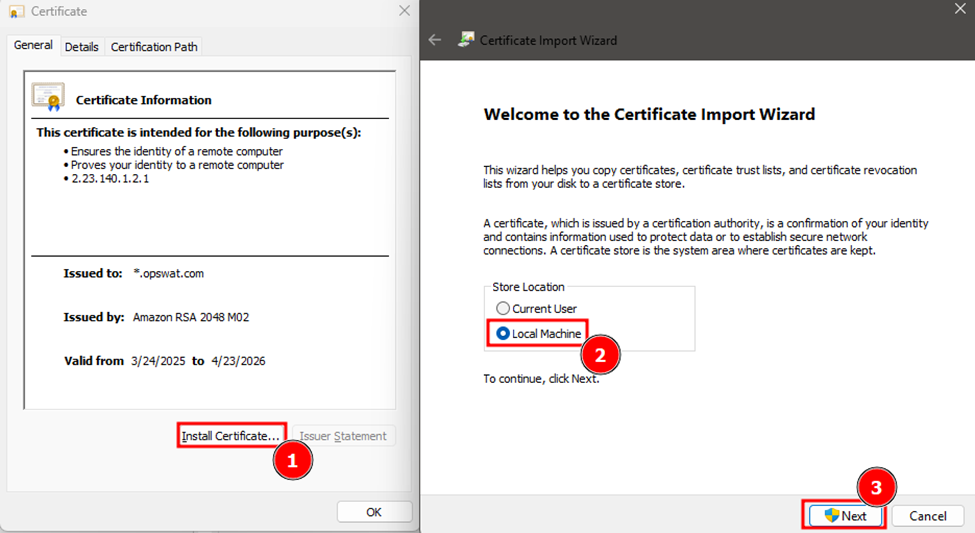
.crtfile to open it. - In the General tab, click Install Certificate.
- Choose Local Machine → Next.
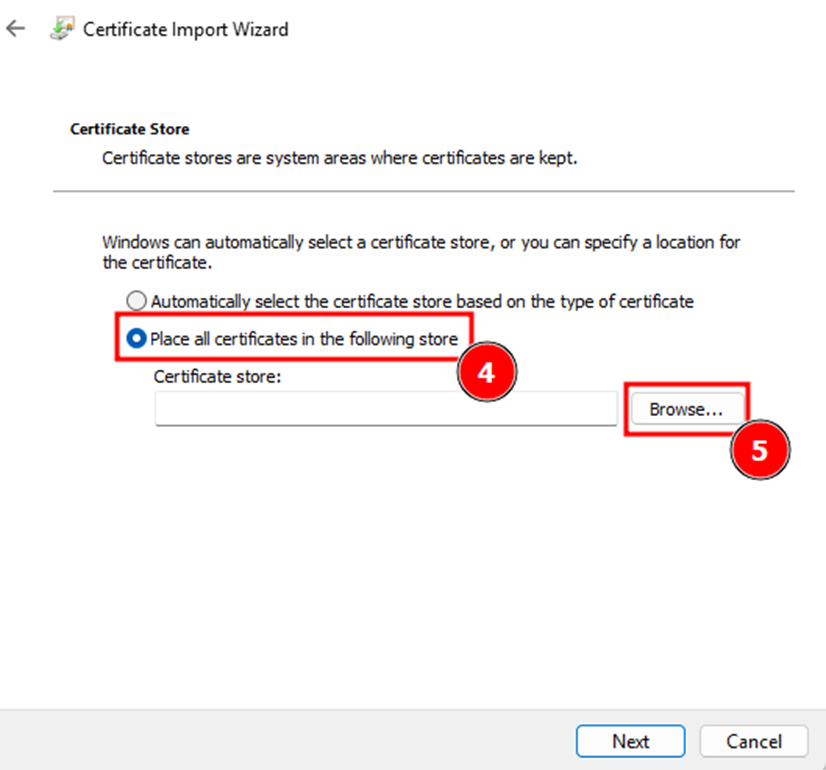
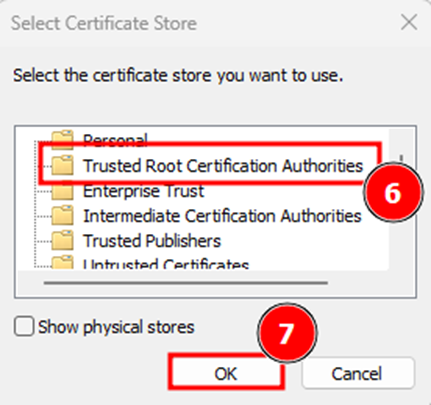
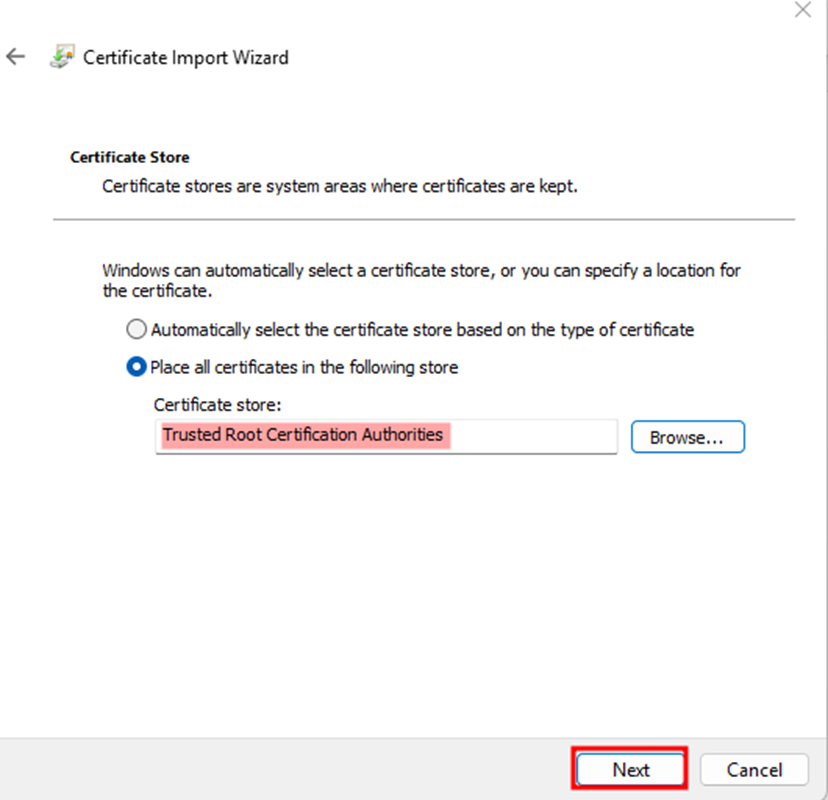
- Select Place all certificates in the following store → Browse → Trusted Root Certification Authorities.
- Click Next, then Finish.
If your certificate chain includes a fourth certificate (e.g., Starfield Services Root Certificate Authority - G2), repeat the export and import steps for it as well.
- Restart OPSWAT MetaDefender Core Service
After importing the certificates, restart the OPSWAT MDCore service.
Additional Notes:
- Certificates must be trusted system-wide for all OPSWAT services to function correctly.
- You only need to perform this process once unless there are major future changes to the certificate authorities.
- Always export the certificate chain from your own environment to match what your CDN edge location provides.
If you require further assistance, please follow these instructions on How to Create Support Package?, before creating a support case or chatting with our support engineer.

