Title
Create new category
Edit page index title
Edit category
Edit link
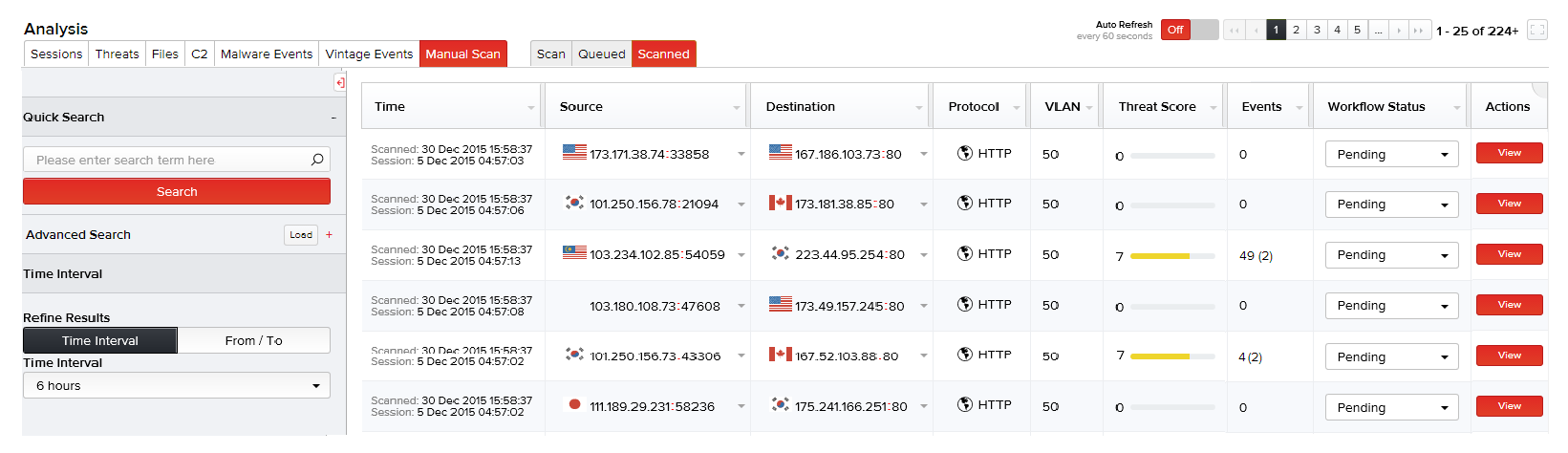
Manual Scan
MetaDefender NDR performs automated file collection, inspection, scanning, and alerting. It may be used to perform centralized scans on files uploaded by analysts too. At a minimum, static analysis and local scanning is available for ad hoc scanning. If additional third-party appliances are integrated into the deployment such as OPSWAT MetaDefender Core, or FireEye AX, the uploaded file can be run against some or all appliances depending on the user preference. See External Integrations in the Administration menu to view a list of third-party scanning appliances.
MetaDefender NDR supports the following compression formats: 7z, ar, arc, arj, bzip2, cab, compress, cpio, deb, flac, gzip, iso, lzma, rar, rpm, tar, xz, zip.
You can upload files or raw traffic dumps through user interface by clicking Analysis > Manual Scan. Click the Upload Files segment of the UI to browse and select the PCAPs or just drag-and-drop the PCAPs to this area for scanning. In the following illustration, multiple PCAP files are being uploaded and queued for scanning.
Note: Groups that have added localhost (127.0.0.1) to their subnet permissions can view pcaps and files that have been manually uploaded by other users
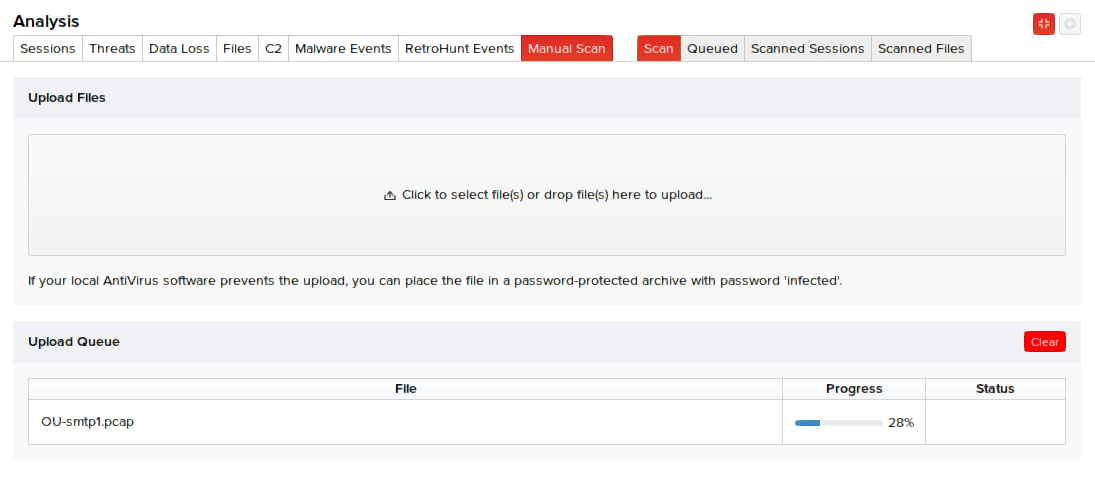
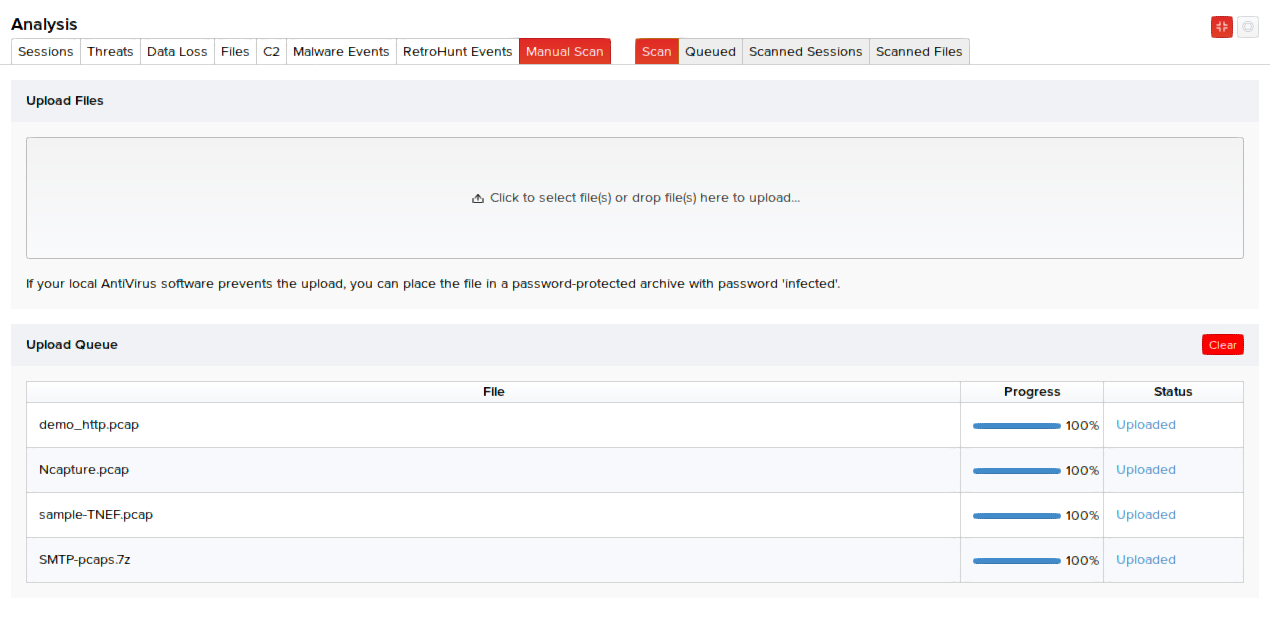
The sessions and respective files will be analyzed, recorded, and displayed in the Scanned tab along with their scanned time and session time. Scanned time refers to the time the PCAPs were scanned by MetaDefender NDR. Session time refers to the time the PCAPs were captured off the session.
To ensure analysts are not exposing their data to unnecessary risk by introducing malicious files to their system, it is advised that they encrypt potentially malicious files on a system where the risk of infection is removed prior to uploading them. Manual scan supports encrypted zip file uploads. When creating encrypted zip files containing the file of interest, use infected as the password. MetaDefender NDR will then decrypt, extract, and process the files.