Title
Create new category
Edit page index title
Edit category
Edit link
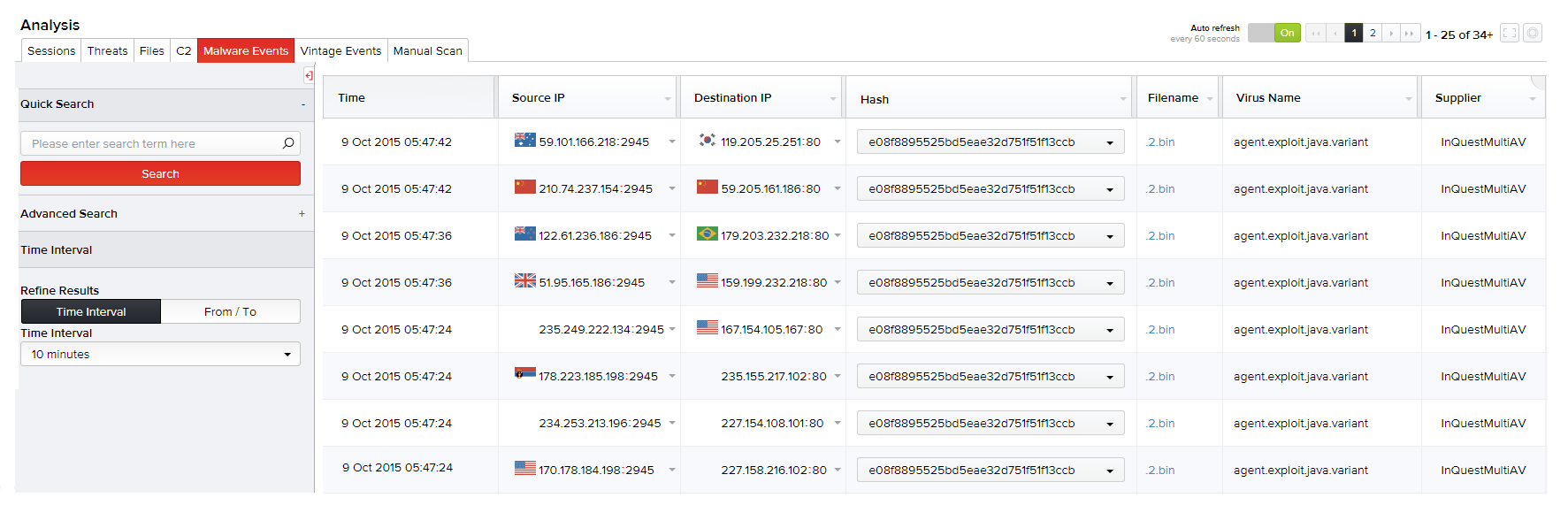
Malware Events
The Malware Events page allows you to search for files that were triggered either by InQuest MultiAV, VirusTotal, or OPSWAT MetaDefender Core. To view these files, select Analysis > Malware Events.
Columns available in the Advanced Search menu for the Malware Events page are:
- Source IP
- Source Port
- Destination IP
- Destination Port
- Filename
- MD5
- SHA1
- SHA256
- SHA512
Select the column(s) and specify their criteria. You can also specify the session time from the Time Interval drop-down menu or select a date range from the built-in calendars by clicking the From/To option. Click Search. Results appear on the right pane displaying the instance of the files triggered, source IP, destination IP, MD5, filename, virus name and the supplier.
Note: Quick search does not search for vendor name or virus name, only file name. If you wish to search for vendor name or virus name, use the advanced search.
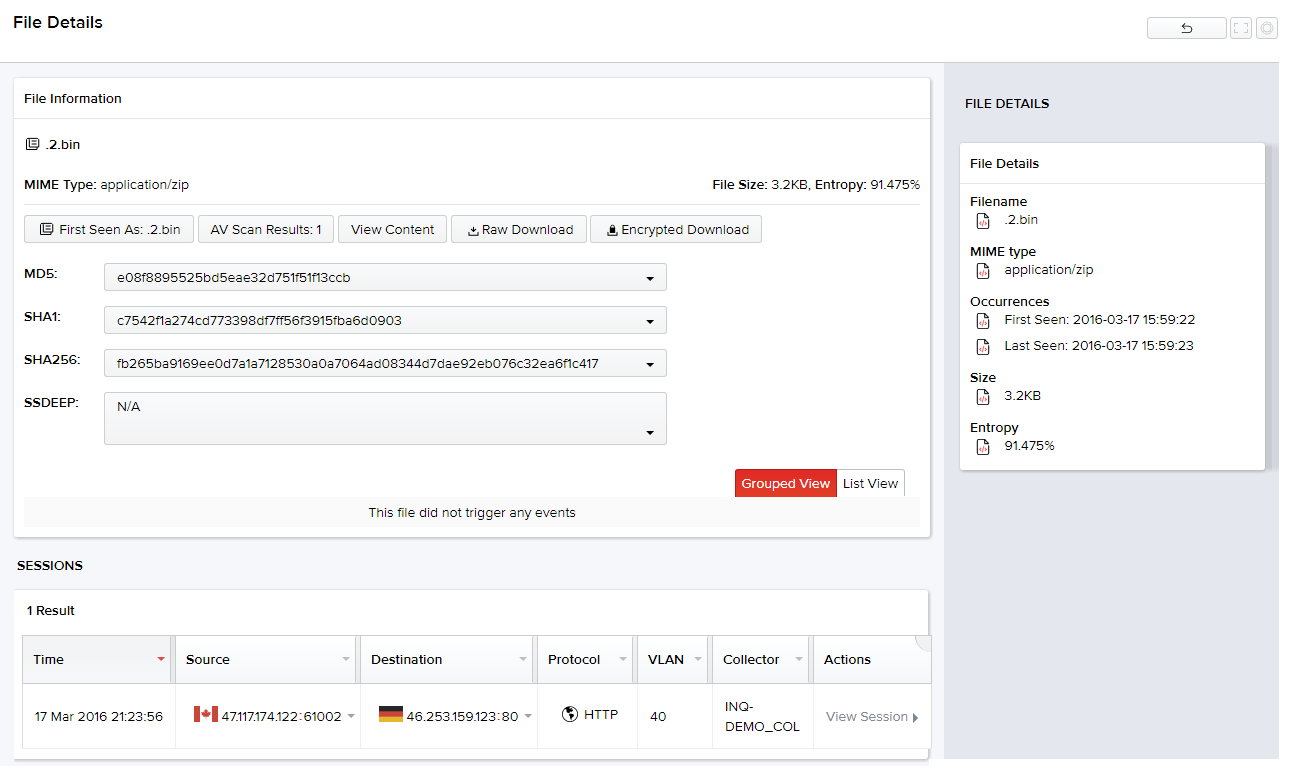
VIEWING FILE DETAILS
Click the file name link to view its details. The resulting page displays the transferred file information along with the option to view their content and download them as raw or encrypted file(s). Details of a TCP sessions containing the file can be viewed in a tabular form.
On the right pane of this page, you can view the fie name, MIME type, file size, and entropy.