Why is MetaDefender MFT file upload failing with 'Processing Failed' status when submitting a known malicious file?
- This article applies to all MFT versions.
Issue: When submitting a file to OPSWAT Managed File Transfer (MFT), the file upload failed with the status "Processing Failed".
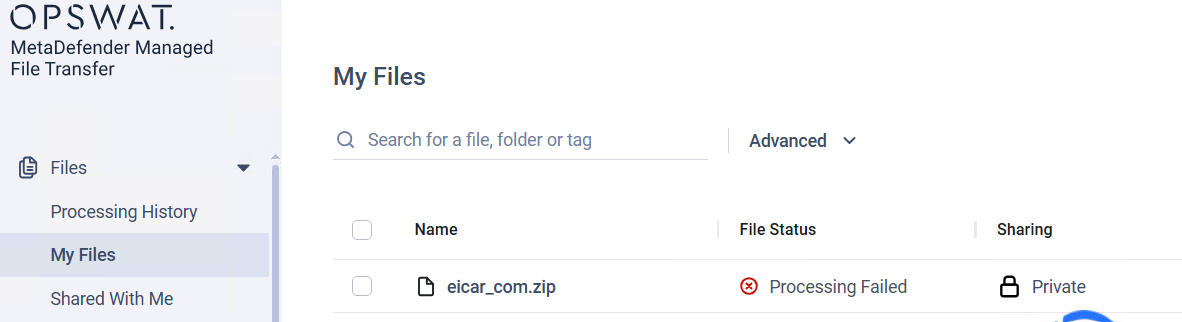
Analysis: Upon reviewing the MFT logs, the following recurring errors were found:
3
ERROR PrioritizedScannerService > scan request failed. job: 18; name: eicar-Copy(1).zip; Operation did not complete successfully because the file contains a virus or potentially unwanted software. ERROR Failed to perform "NewFileScannerJob" job. File id: 18. Message: Operation did not complete successfully because the file contains a virus or potentially unwanted software....The example file above is an EICAR test file (detected by most AV products). Importantly, behavior varies by sample and environment:
- Some malicious files (or test files like EICAR) are detected and blocked/quarantined by Windows Defender (or other endpoint AV) immediately at the OS level. In that case the file is intercepted before MFT/MD Core can read or forward it, causing “Processing Failed”.
- Other malicious files may not be detected by Defender (e.g., new/obfuscated threats) and therefore can be handed to MFT and forwarded to MD Core. In those cases MD Core may be the component that detects and reacts to the sample.
Root Cause:
- OS/Endpoint interception: When Defender (or another endpoint AV) recognizes a file as malicious, it often prevents access (read/write) or quarantines it as soon as it touches the filesystem or memory. MFT cannot handoff or stream the file to MD Core, which leads to scan errors in the application logs and a “Processing Failed” status.
- Detection gaps: Conversely, if Defender does not recognize the malware, the file may reach MFT and MD Core. MD Core (with multiple engines/signatures) may still detect it. Differences in detection are expected because Defender and MD Core use different engines, signature sets, heuristics, and update cadences.
Expected Behavior:
- Endpoint protection preventing the transfer of known-malicious/test files is expected and desirable.
- It is also expected that detection results vary between endpoint AV (Windows Defender) and MD Core for certain samples — no single product catches everything first.
Next Steps / Recommendation:
- Test uploading other malicious files (e.g., standard documents, archives, images) to confirm that the integration works as expected.
- If non malicious files process successfully, no further action is required – the issue is solely due to OS-level security.
- If non malicious files also fail, further investigation is required.
If you require further assistance, please follow these instructions on How to Create Support Package?, before creating a support case or chatting with our support engineer.
Was this page helpful?