Configuration
v5.16.0
Search this version
Configuration
Configuration
Settings Section
Title
Message
Create new category
What is the title of your new category?
Edit page index title
What is the title of the page index?
Edit category
What is the new title of your category?
Edit link
What is the new title and URL of your link?
Configuring OIDC Single Sign-on
Copy Markdown
Open in ChatGPT
Open in Claude
Create OIDC directory in MetaDefender Core
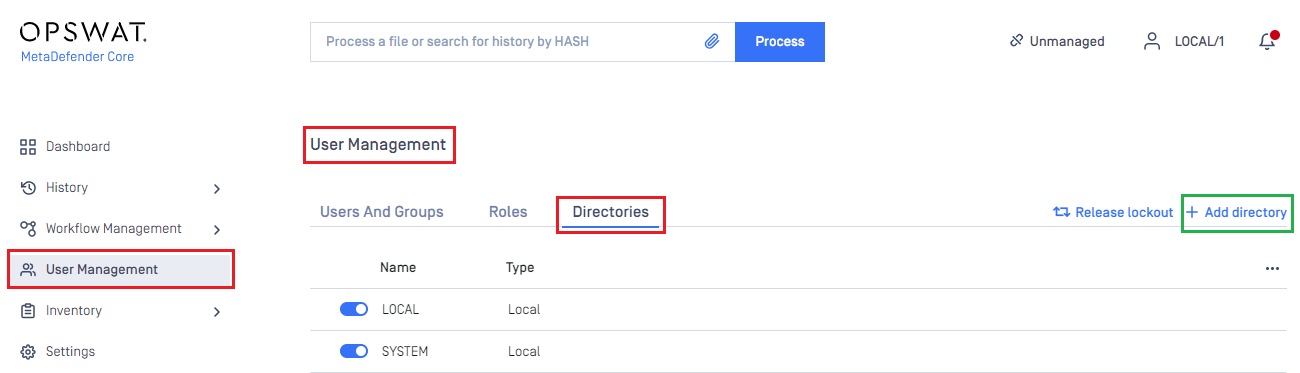
- Sign in to MetaDefender Core.
- In the dashboard, click on
User Managementin the left sidebar. - On
User Managementpage, selectDirectoriestab and clickAdd Directoryin the top right corner.
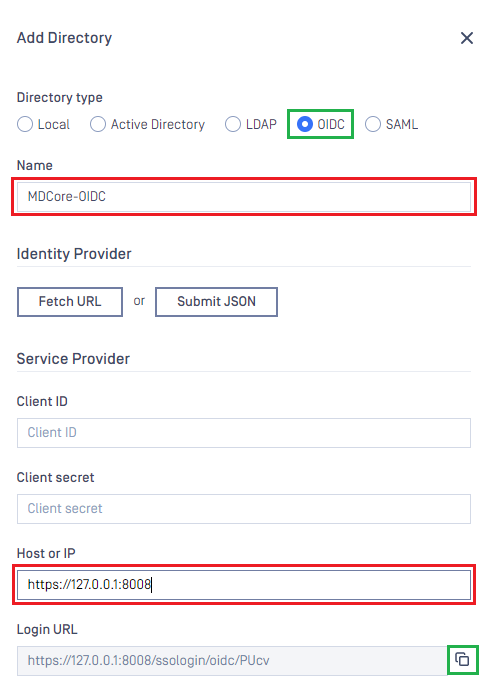
- In
Add Directorypage, select OIDC asDirectory type, and enter a name for the new directory, such as MDCore-OIDC. - Enter
Host or IPwhere MetaDefender Core is hosted, for this example use https://127.0.0.1:8008. - Copy the string generated under
Login URLand store it as reply_uri.
Create and configure OIDC application in PingOne
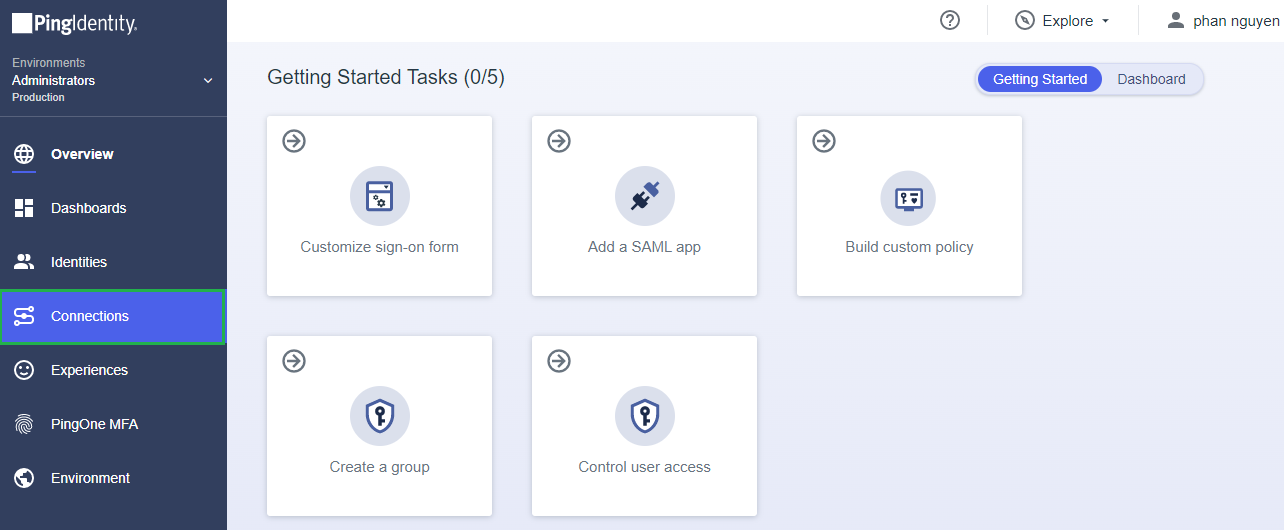
- In the PingOne Overview page, navigate to
Connectionson the sidebar.
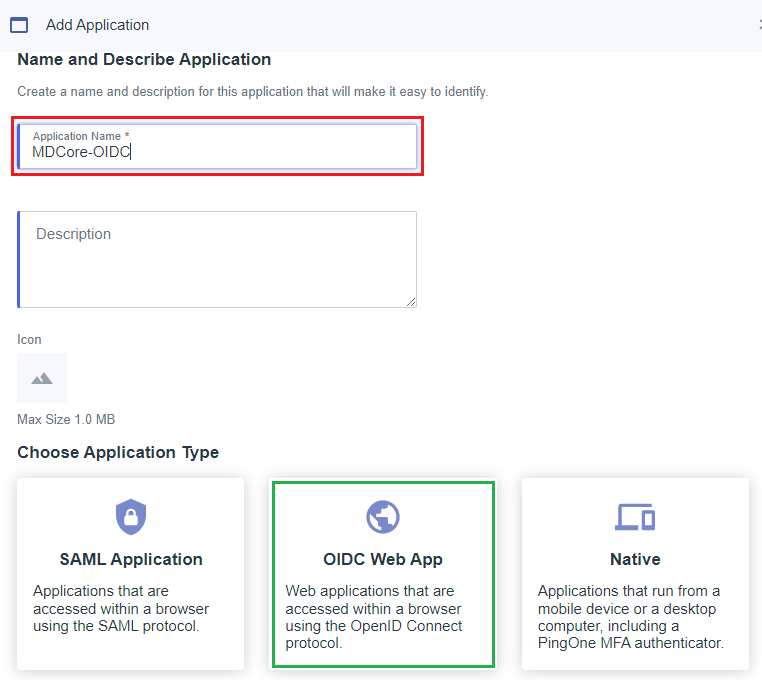
- Click the plus button to add a new application.

- Enter the application name, MDCore-OIDC as an example, choose
OIDC Web AppforApplication Type, and clickSave.
- Select
Configurationtab, then click Edit button.
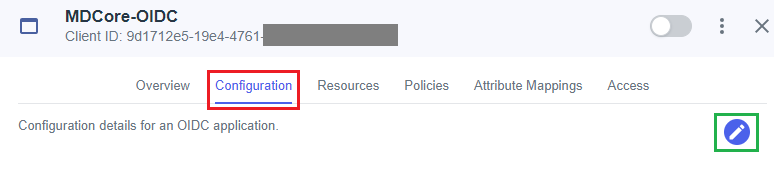
- In
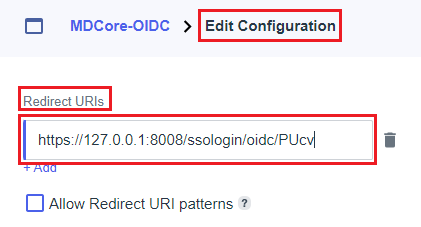
Edit Configurationpage, navigate toRedirect URIs, paste redirect_uri into the box below, and then clickSave.
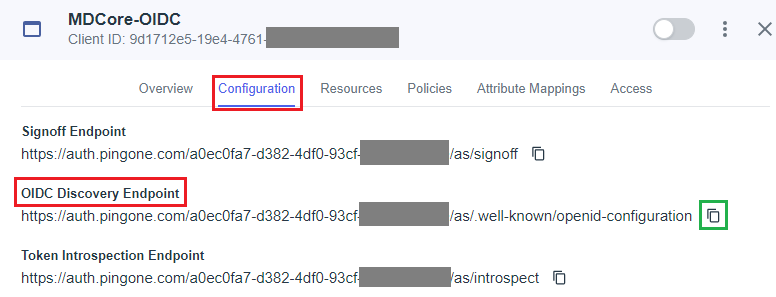
- Back in
Configurationtab, navigate toOIDC Discovery Endpoint, copy the link below, and save it as metadata_url.
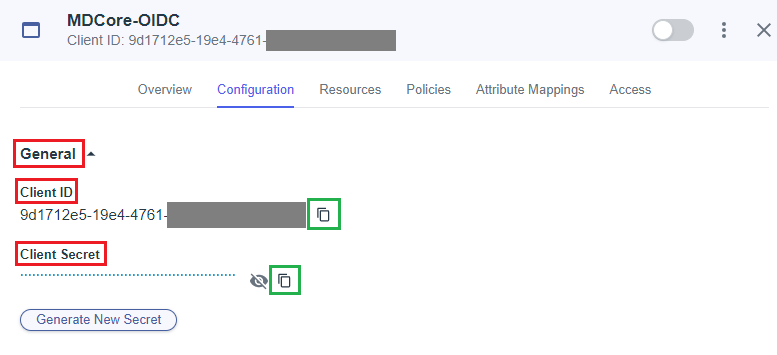
- Expand
Generalsection, navigate toClient IDandClient Secret, and copy and save them as client_id and client_secret, respectively.
- Select
Attribute Mappingstab and click Edit button.
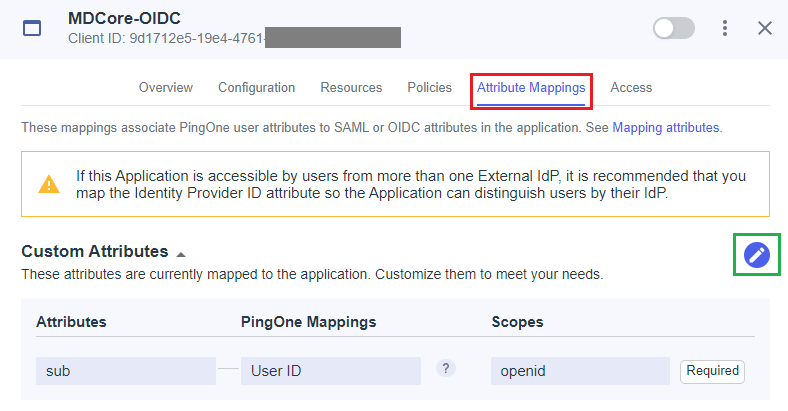
- In
Edit Attribute Mappingspage, clickAddto create a new mapping.
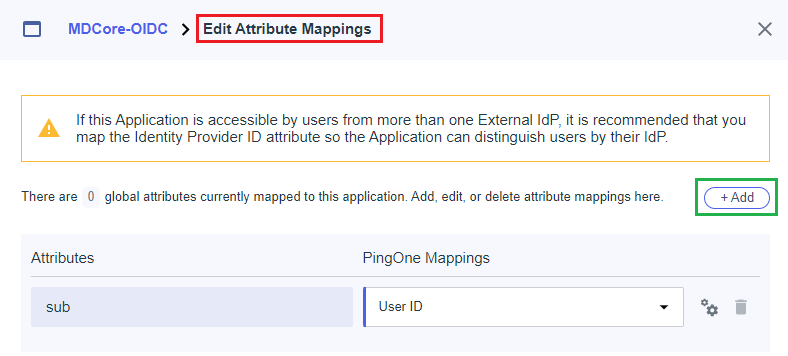
In this step, we create a mapping from the key name used by MetaDefender Core to the one exported by PingOne. For example, we set given_name mapped to Given Name from PingOne. Later, given_name is utilized by MetaDefender Core to identify the logged-in user.
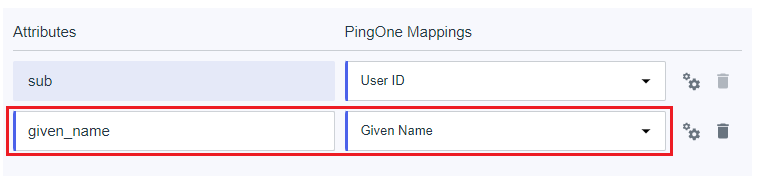
- Enter the attribute name,
given_namein this example, select the itemGiven NameinPingOne Mappings, enableRequiredoption , and clickSaveto complete.
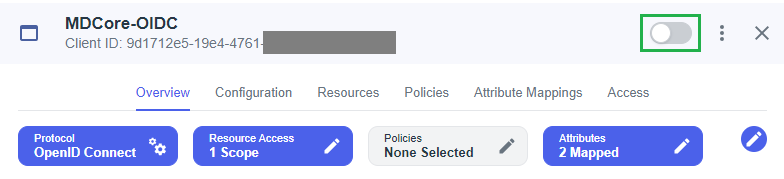
- Enable the new application in PingOne.
Complete configuration in MetaDefender Core
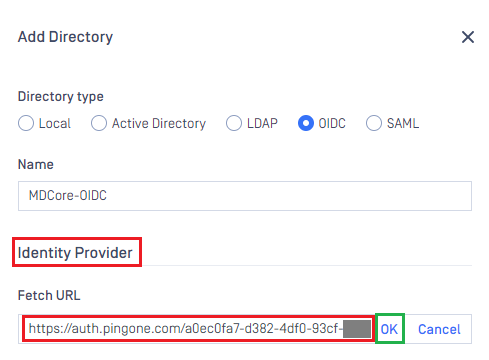
- Switch back to MetaDefender Core. Under
Identity Provider, clickFetch URL, paste value of metadata_url into the box below, clickOK, and wait a moment for MetaDefender Core to check and set PingOne as its IdP.
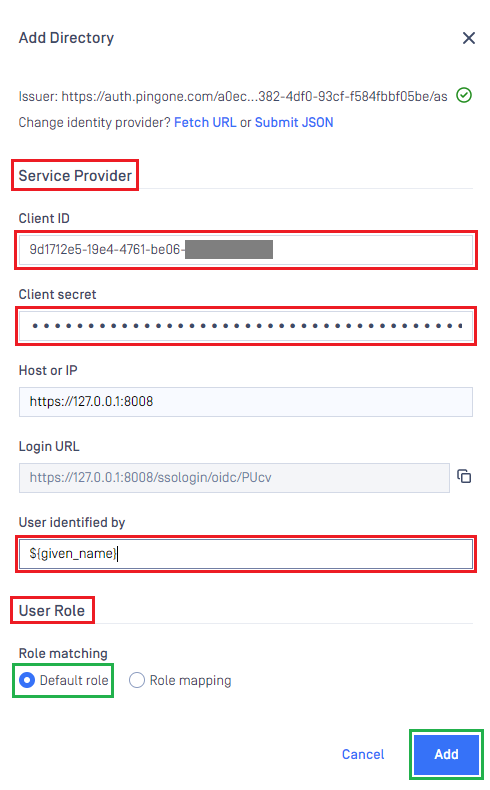
- Under
Service Provider, paste the values of client_id and client_secret into the boxes labeledClient IDandClient Secret, respectively. - Fill in ${given_name} in the box under
User Identified By. - Select
Default roleoption, choose the appropriate role to assign to users underUser Role, and clickAddto complete the settings in MetaDefender Core.
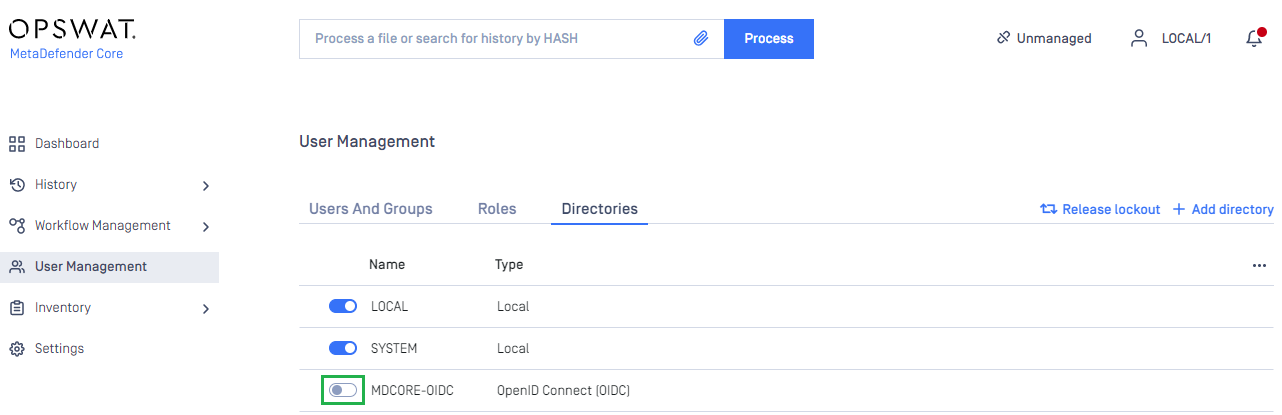
- On
User Managementpage, toggle the new directory, MDCORE-OIDC in this example. A dialog box will appear to confirm the action. OnceEnableis clicked, all sessions will expire immediately.
Test the integration
- On the home screen of MetaDefender Core, click
Login; the user is redirected to PingIdentity login page.
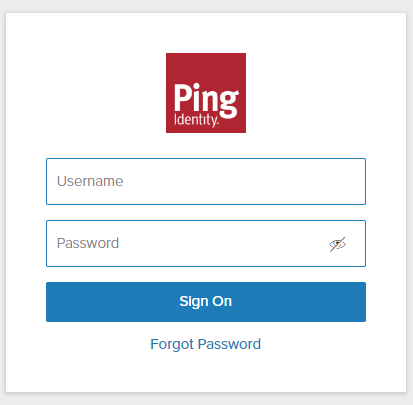
- Sign in using the account registered with PingIdentity.
- If everything goes well, MetaDefender Core dashboard is displayed with the user identity in the top right corner.
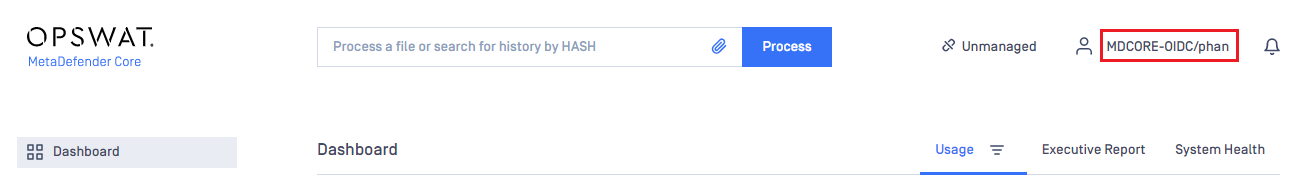
- Otherwise, access backup login page at
<mdcore-host>#/public/backuploginfor trouble shooting.
Type to search, ESC to discard
Type to search, ESC to discard
Type to search, ESC to discard
Last updated on
Was this page helpful?
Next to read:
General configurationDiscard Changes
Do you want to discard your current changes and overwrite with the template?
Archive Synced Block
Message
Create new Template
What is this template's title?
Delete Template
Message

