Title
Create new category
Edit page index title
Edit category
Edit link
ADFS Proxy with O365 using SAML
OPSWAT MetaDefender IT-OT Access can be easily integrated with ADFS Proxy to ensure that a device is compliant with the organization's security policy before it is granted access to O365. This ensures that the device is not only authenticated by the IdP, but also tested for risks and vulnerabilities such as infections or unpatched versions of operating systems, BEFORE it access an organization's cloud services.
To get started with implementing OPSWAT MetaDefender IT-OT Access integration to enforce device posture check before granting a device to access O365 with ADFS Proxy, you set up SSO between AD FS server and O365 manually. You need the following requirements
- A domain.
- An Active Directory instance.
- Add your domain to Office 365.
- Install Windows PowerShell for Azure Active Directory here.
- Install ADFS server.
- Using Azure AD Connect to enable Single Sign-On to Office 365.
Configuring, installing ADFS server and enabling SSO to Office 365 is beyond the scope of this tutorial. This tutorial uses screenshots from Server 2012R2, but similar steps should be possible on other versions.
Now it's the time you can integrate MetaDefender IT-OT Access with your ADFS by following below steps. You can learn more details for each step here at 3.1.1. How to set it up?
- Step 1. Enable Access Control on your MetaDefender IT-OT Access account
- Step 2. Add protected applications with IdP Method
- Step 3. Configure Access Rules
- Step 4. Update Office 365 Relying Party Trusts in AD FS Server
- Step 5. Edit SSO settings on Office 365
- Step 6: Test your integration
Step 1. Enable Access Control on your MetaDefender IT-OT Access account
- Login to the MetaDefender IT-OT Access console.
- Navigate to Secure Access > Protected Apps.
- Check on the box "Enable Secure Access ".
- Navigate to Integrations and then Device Identity, and enable Enable cross-domain API integration at port xxxx
Step 2. Add protected applications with IdP Method
- The next step is importing an ADFS Signing certificate to MetaDefender IT-OT Access. This allows MetaDefender IT-OT Access to verify users signing though a trusted IdP. Each identity provider has a unique X.509 certificate. Download the ADFS Signing certificate by following these steps:
- Login to Windows Server
- Open Server Manager
- Click Tools
- Click AD FS Management
- Expand Service
- Click Certificates
- Double-click on the "Token-signing" being used to sign your responses
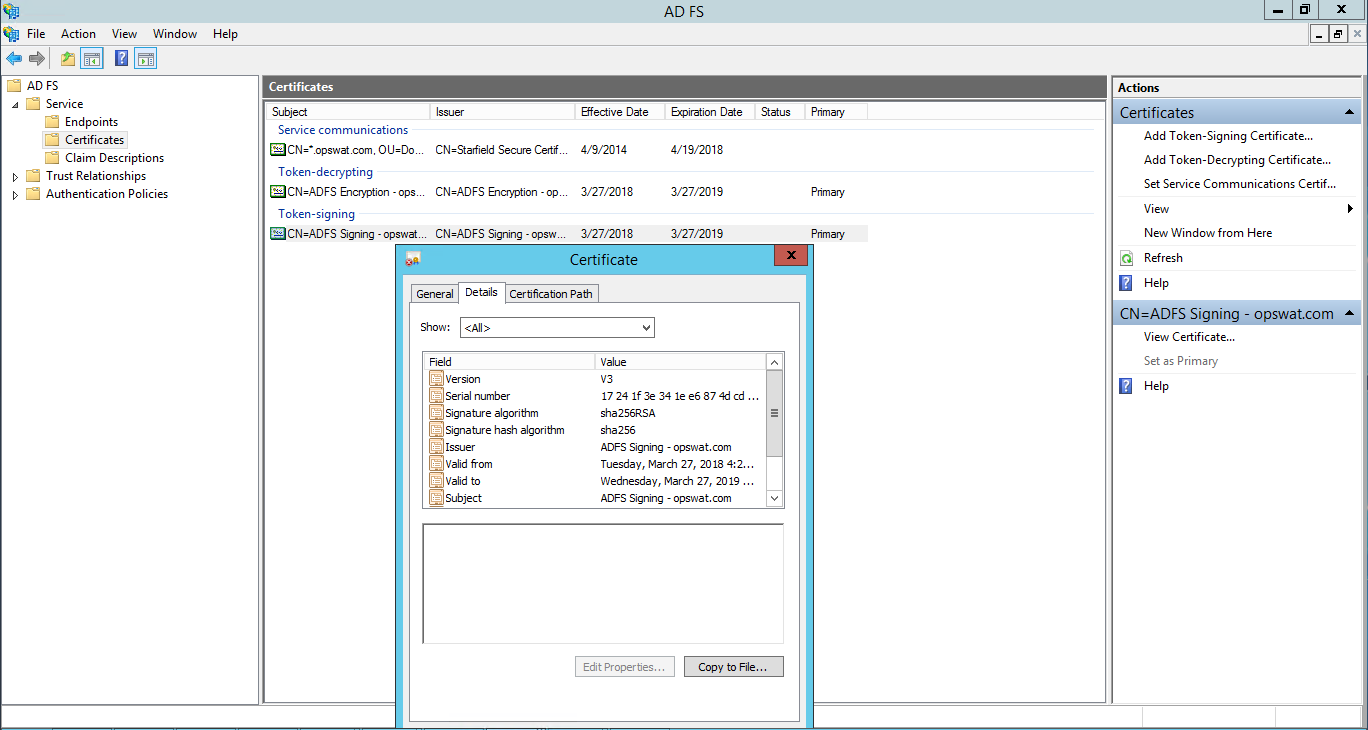
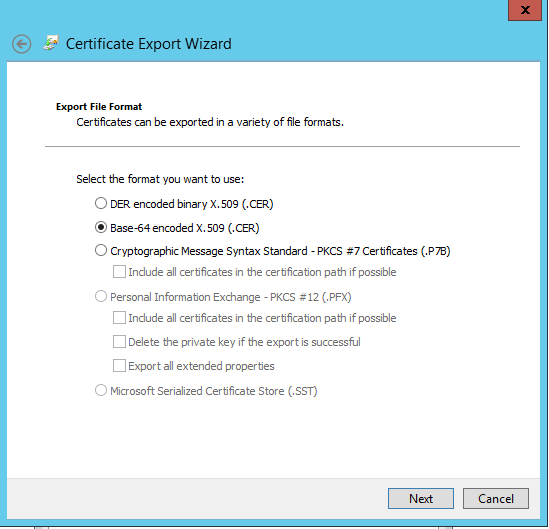
8. Click Copy to File to download the certificate. That should open another box, showing the certificate export wizard. Click Next and you will be asked which format to export the certificate in. Choose Base-64 encoded X.509
Collect Idp Login URL In this case, Idp Login URL is https://login.microsoftonline.com/login.srf
Add the ADFS Identity Provider. If you already have ADFS IdP settings on yourMetaDefender IT-OT Access account, go to 4 to add O365 application.
- Login to the MetaDefender IT-OT Access console
- Navigate to Secure Access and then Access Methods
- On the Identity Providers tab, click "Create New Identity Provider" to add your IdP
- Fill in required fields for the Identity Provider
- IdP Name: an IdP name, for example: ADFS
- IdP Certificate: upload ADFS certificate you downloaded in Step 2.1
Click SAVE.
Add the O365 application:
- Expand the ADFS IdP settings you have just added in Step 2.3 above.
- Navigate to Secure Access and then Protected Apps. Click Add New Application.
- Select IdP Method and choose from the existing IdPs, finding the one you just made. Press Continue.
- Enter required field
- Application: application name, for example: O365
- IDP Login URL: application login URL which you have from Step 2.2
- Login URL: https://login.microsoftonline.com/login.srf
- Logout URL: https://login.microsoftonline.com/logout.srf
- Access Mode: pick an access mode you prefer. See details on the access modes at Step 2. Add protected applications with IdP Method
- Click Add
- After saving your changes successfully, click the Setup Instructions button of the O365 application you have just added and then copy the URL MetaDefender IT-OT Access generated there. This URL is used to replace O365 login URL on ADFS.
- Download the Note: you can add O365 application (step 2.4) when you add ADFS IdP settings.
Step 3. Configure Access Rules
On MetaDefender IT-OT Access console, navigate to Secure Access and then Rules
Click "ADD NEW RULE" to add a new rule for this application OR you can update existing access rules to add this application
With a new access rule, you need to specify how you would like to block/allow access a device from the application
- Rule name: a rule name, for example Block non-compliant devices
- Action: Block or Allow
- Configure conditions to do the action. Details at Step 3. Configure Access Rules
Click ADD RULE
Step 4. Update Office 365 Relying Party Trusts in AD FS Server
- Update Passive Endpoint
- Login to Windows Server
- Open Server Manager
- Click Tools
- Click AD FS Management
- Expand Trust Relationships
- Click Relying Party Trusts
- Double-click on "Microsoft Office 365 Identity Platform" and choose **Endpoints tab
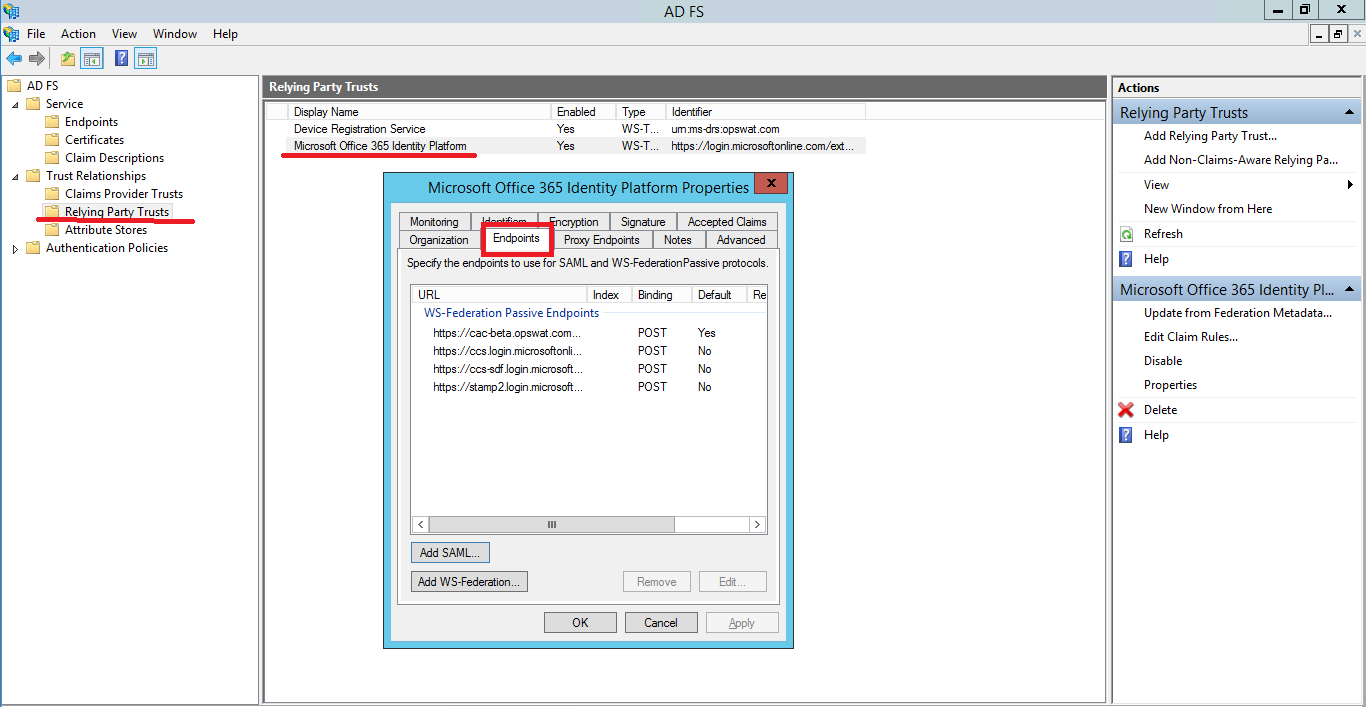
8. Click Add SAML to add new Endpoint
9. Use the URL in step 2.5 as Trusted URL:
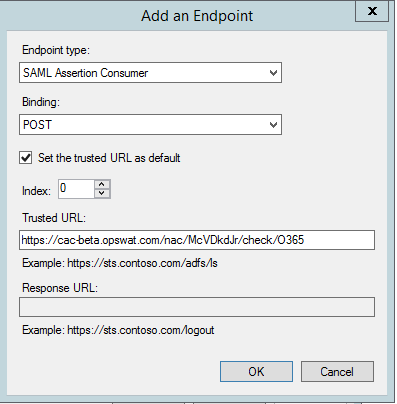
10. Click OK
- Configure the Active Directory claims-provider trust
- Right-click "Microsoft Office 365 Identity Platform" and choose **Edit Claim Rules

2. On the Issuance Transform Rules tab, click **Add Rule
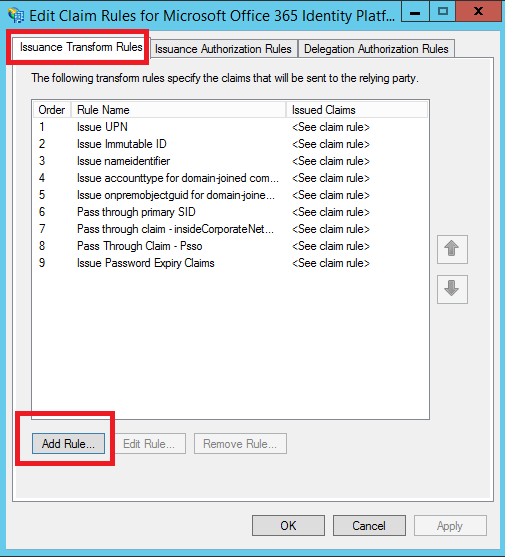
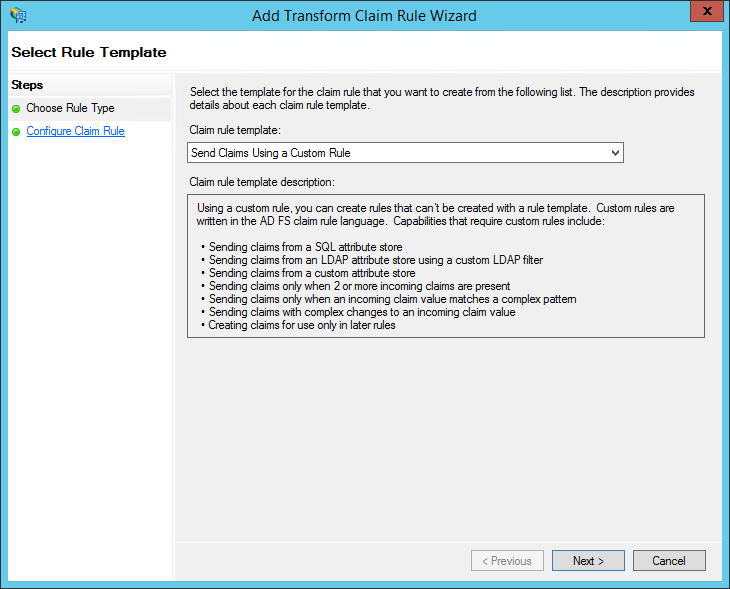
3. In the Claim rule template box, select Send Claims Using a Custom Rule, and then click **Next
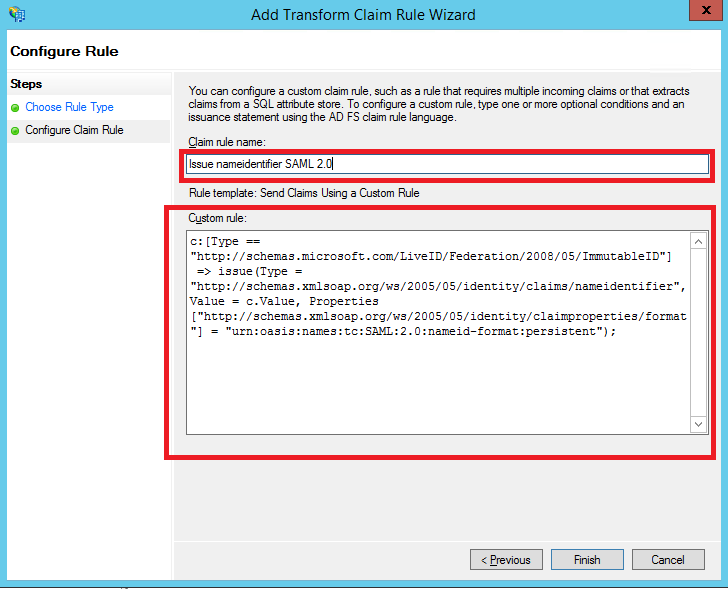
4. In the Claim rule name box type "Issue nameidentifier SAML 2.0", and fill the Custom rule as follow:
c:Type == "[http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"] => issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Value = c.Value, Properties"[http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:2.0:nameid-format:persistent");
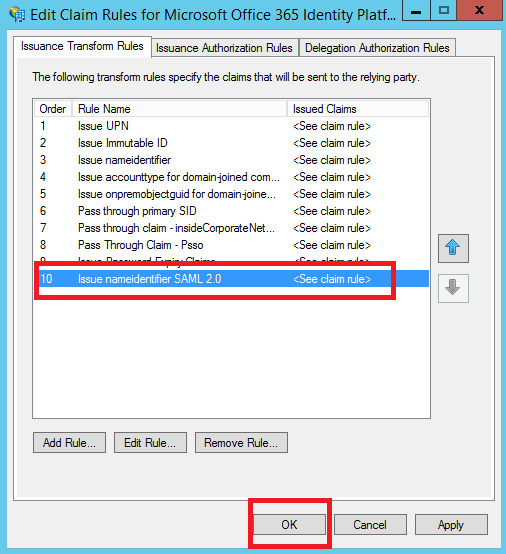
5. Click Finish
6. Click OK
Step 5. Edit SSO settings on Office 365
After install and configure AD FS server, it will enable SSO for your domain, but you need to replace SigningCertificate in SSO setting to work with MetaDefender IT-OT Access
- Login to Azure Active Directory via Windows PowerShell
- Login to a computer installed Windows PowerShell for Azure Active Directory
- Start PowerShell and run Connect-MsolService cmdlet and enter your administrator credentials for your Office 365 domain when prompted
C:\Windows\system32>Connect-MsolServiceBackup current SSO settings
- Run Get-MsolDomainFederationSettings -DomainName <your domain> cmdlet to get current SSO setting
- Get these information
- FederationBrandName
- IssuerUri
- LogOffUri
- PassiveLogOnUri
Update existing current setting
- Run following cmdlet
C:\Windows\system32>Set-MsolDomainAuthentication -DomainName <your domain> -Authentication Managed2. Run Set-MsolDomainAuthentication cmdlet
C:\Windows\system32>Set-MsolDomainAuthentication `-FederationBrandName <FederationBrandName> `-DomainName <Your Domain> `-Authentication Federated `-IssuerUri <Issuer> `-PassiveLogOnUri <Passive Endpoint> `-LogOffUri <LogOffUri> `-PreferredAuthenticationProtocol SAMLP `-SigningCertificate <OPSWAT Certificate in step 2>Note: enter the certificate on a single line without break line
3. Run following cmdlet to verify configuration
C:\Windows\system32>Get-MsolDomainFederationSettings -DomainName <Your Domain>Note: It can take some time for Office 365 to apply new configuration
Step 6: Test your integration
Follow guideline at Step 6: Test your integration to test your integration to verify if it works as your expectation.
DONE! CONGRATULATIONS.

