Title
Create new category
Edit page index title
Edit category
Edit link
How to Enable Secure Email Relay in MetaDefender Managed File Transfer (MFT)?
This article applies to all MetaDefender Managed File Transfer releases deployed on Windows systems.
When configuring SMTP settings in MetaDefender MFT, it is important to understand when to enable or disable SSL/TLS based on your mail server’s encryption requirements.
Some SMTP servers support STARTTLS, which upgrades an unencrypted connection to a secure one, while others use Implicit TLS, which requires encryption from the beginning. Selecting the wrong setting may cause connection failures or authentication errors.
This article explains when to enable or disable SSL/TLS in MetaDefender MFT.
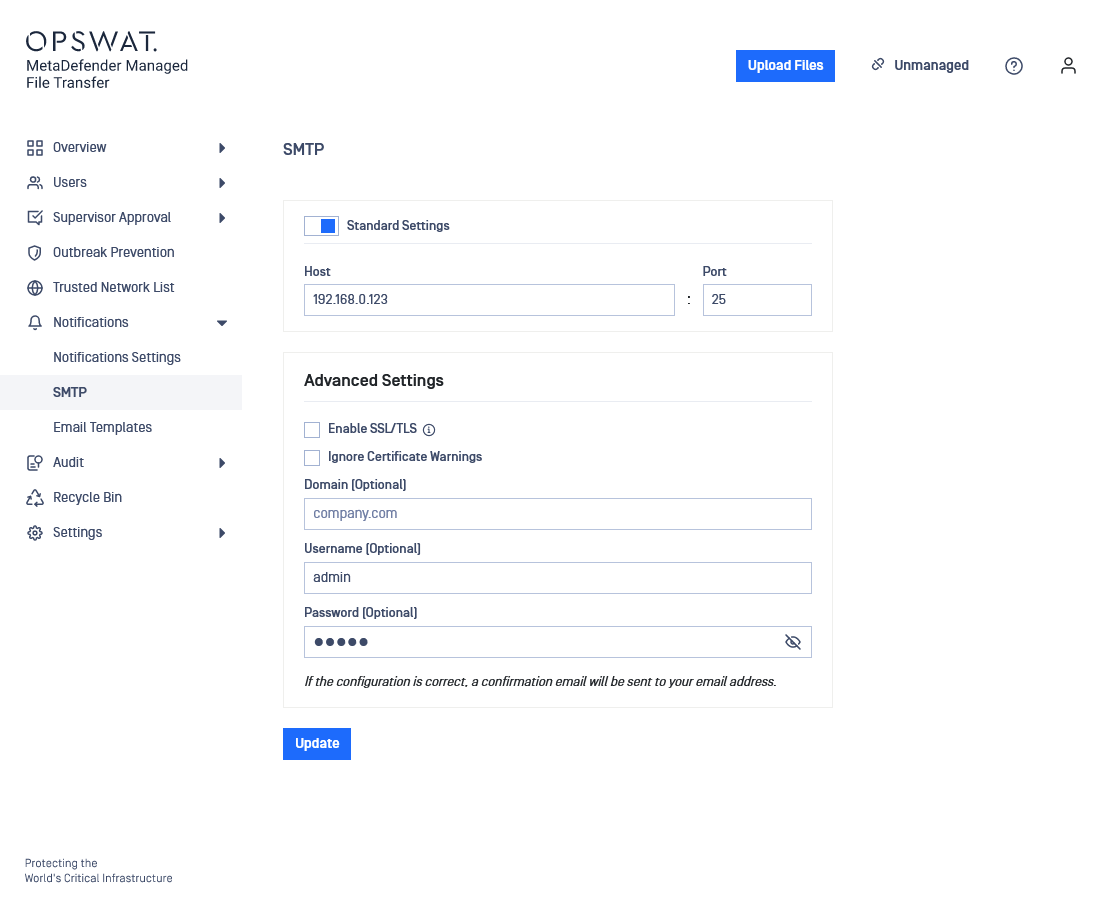
SMTP Encryption Types and Configuration
| Encryption Type | SMTP Port | Enable SSL/TLS in MFT |
|---|---|---|
| STARTTLS | 587 | OFF |
| Implicit TLS | 465 | ON |
Understanding the Configuration Logic
STARTTLS (Port 587)
- The connection starts as unencrypted.
- Once the SMTP server responds, the client sends a STARTTLS command to request encryption.
- Since encryption is initiated later in the process, Enable SSL/TLS should be OFF in MetaDefender MFT.
Implicit TLS (Port 465)
- The connection is encrypted from the beginning.
- There is no unencrypted communication before TLS starts.
- Since encryption is always enforced, Enable SSL/TLS should be ON in MetaDefender MFT.
For detailed SMTP server configuration in MetaDefender MFT, please refer to the official documentation: MetaDefender MFT SMTP Configuration Guide
In the unlikely event that you have followed the instructions above but are Unable to enable secure email relay in MetaDefender Managed File Transfer, please open a Support Case with the OPSWAT team via phone, online chat or form.

