Title
Create new category
Edit page index title
Edit category
Edit link
Why Does the SHA256 Hash of a File Change in Storage Folder After Mirroring Between MetaDefender MFT Nodes?
- This article applies to all MFT versions.
The files stored in Storage folders are different because they have been encrypted with differing keys, even though the content remains identical..
MetaDefender Managed File Transfer encrypts files after they have been successfully processed using the following algorithm:
- AES (Advanced Encryption Standard) with Cipher Block Chaining (CBC) mode
- PKCS #7 padding
- Cipher block size: 128 bits
- Cryptographic key: 256 bits
- Initialization vector (IV): 128 bits
The cryptographic key is derived from a randomly generated 256-bit passphrase and 64-bit salt (RFC 2898 compliant).
Each MFT node maintains its own unique cryptographic key. Users can generate new keys for key rotation, but only new files are encrypted with the newly generated key; previously uploaded files remain encrypted with the original key.
Mirroring Mechanism
When a file is mirrored from MFT01 → MFT02, the following occurs:
Encryption on MFT01:
- Upon successful upload, MFT01 encrypts the file using its local cryptographic key.
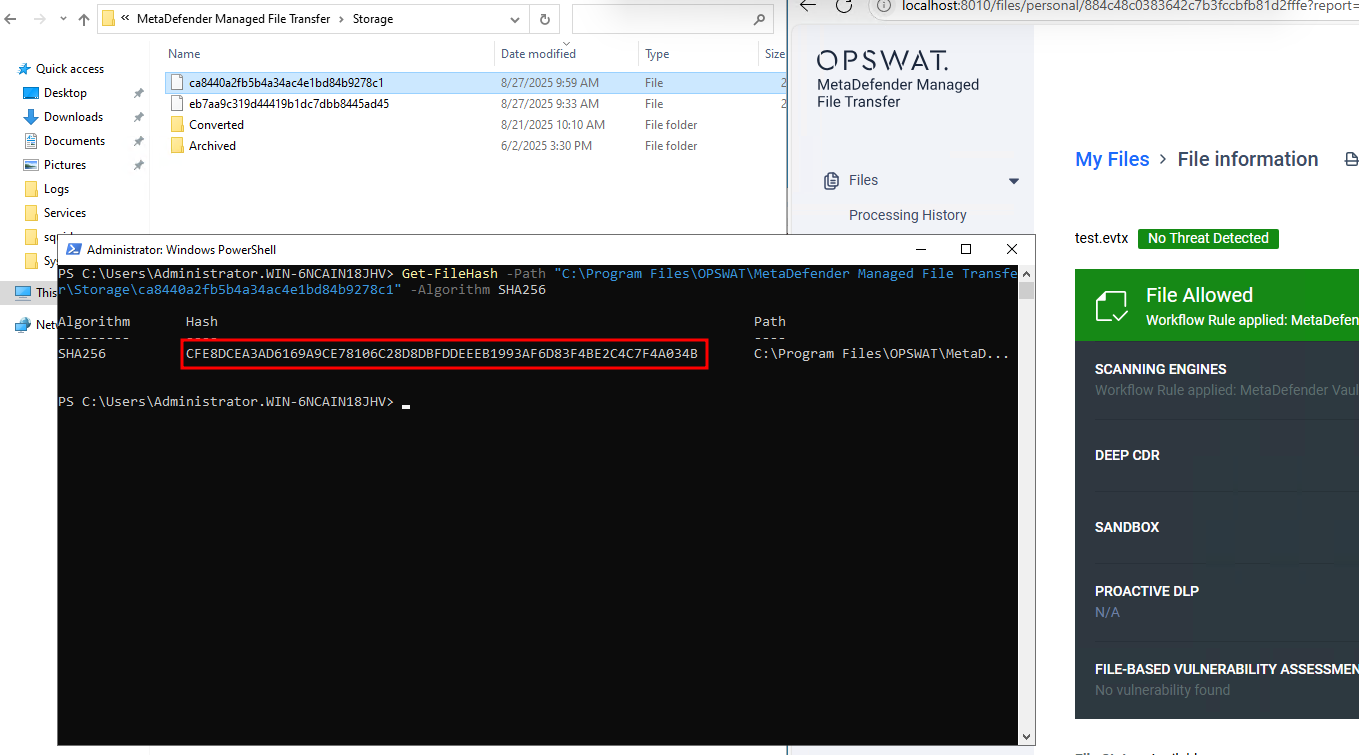
- The encrypted file is stored in
.\Storage\. (e.g in this case the hash is CFE8DCEA3AD6169A9CE78106C28D8DBFDDEEEB1993AF6D83F4BE2C4C7F4A034B)
Decryption for Mirroring:
- During synchronization, MFT01 decrypts the file temporarily to prepare it for transfer. This ensures that the file content remains intact while being transferred to MFT02.
Encryption on MFT02:
- MFT02 receives the plaintext file and encrypts it using its own cryptographic key.
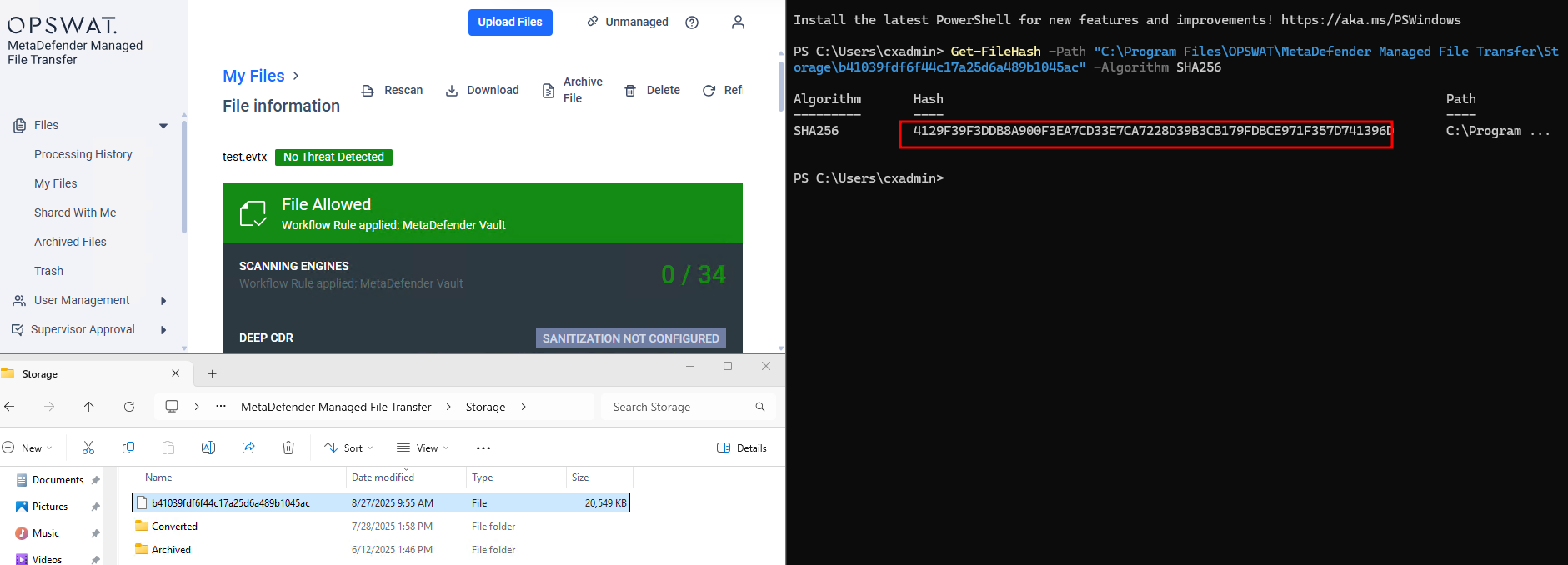
- The newly encrypted file is stored in
.\Storage\on MFT02. Because MFT02 uses a different cryptographic key, the SHA256 hash of the encrypted file will differ from MFT01’s encrypted file, even though the decrypted content is identical. This behavior is expected and by design to maintain node-specific encryption and data security. As a result, the hash of the file in Storage folder on MFT02 is different from MFT01.
Temporary storage is used during these operations (in the .\Data\ folder) to hold the plaintext copy briefly while encryption or decryption occurs. Disk sizing should account for approximately 2× the size of the largest file to ensure successful processing.
If you require further assistance, please follow these instructions on How to Create Support Package?, before creating a support case or chatting with our support engineer.

