Title
Create new category
Edit page index title
Edit category
Edit link
Single Sign-On
Single Sign-On (SSO) allows users to log into MetaDefender Managed File Transfer without having to enter the active directory credentials or creating a local account. Enabling SSO is available for Identity Providers (IdP) supporting the OpenID Connect protocol.
On details about challenges integrating with specific products please see SSO Integrations.
For a step-by-step tutorial, refer to:
Requirements
Below are the technical requirements of MetaDefender® MFT supporting SSO.
Technical Details
| SSO Details | |
|---|---|
| Protocol | OpenID Connect |
| Authorization Flow | Authorization Code Flow |
| Required Scopes | openid , profile ,email |
| Response Mode |
|
Claims
Following are the claims used to propagate user details in MetaDefender® MFT by default. Claims are resolved in the following sequence, with the first claim found determining the value for the corresponding user detail.
Either the upn or the name claim is required; when neither exists, authentication will fail.
| User Detail | Claim(s) |
|---|---|
| User Name |
|
| Display Name |
|
| Given Name |
|
| Surname |
|
| Email Address |
|
| Phone Number |
|
| Group Memberships | Empty by default. |
If details can not be populated due to missing claims, their values will be left empty.
Group Memberships
It is possible to provide MetaDefender Managed File Transfer™ group membership details on SSO claims by providing at least one claim for the Group Memberships user detail. The claim should contains a list of group names the user is member of in MetaDefender Managed File Transfer™.
If a group does not exist yet in MetaDefender Managed File Transfer™, it will be created. Group memberships not stated in the claim will be removed.
Names provided for groups in claims are matched against the Group Name detail and not the Display Name value of the MetaDefender Managed File Transfer™ groups.
Configuration
In order to set up single sign-on, go to "Settings" → "Single Sign-On."
Redirection
URL(s) for redirection can be generated on the configuration page of SSO within MetaDefender Managed File Transfer™. The redirection URL's format is the following: <protocol>://<host>:<port>/vault_rest/authenticate-sso
For example if MetaDefender Managed File Transfer™ is being accessed on the address https://my-mft:8010, then the SSO provider will be asked to redirect authentications to https://my-mft:8010/vault_rest/authenticate-sso.
MetaDefender Managed File Transfer™ will always dynamically create the redirection URL based on what address the instance is being accessed on.
| Name | Description |
|---|---|
| Enable SSO | Turn SSO integration on/off |
| Ignore TLS Certificate | Accept requests from the IdP even if the certificate is not fully trusted |
| PKCE Support | Whether to utilize Proof Key for Code Exchange along with the authorization code flow during authentication |
| Load User Profile | Attempt to retrieve user claims by calling the/userinfo endpoint |
| Skip Endpoint Validation | If enabled, the authority of the OpenID endpoints are not validated against the issuer. Acquire this information on the /.well-known/openid-configurationendpoint of the SSO provider. |
| Skip Name Validation | If enabled, the name of the authority will not be validated against the issuer. Acquire this information on the /.well-known/openid-configurationendpoint of the SSO provider. |
| Provider Name | A friendly name that identifies the IdP in Managed File Transfer |
| Authority | The URL of the IdP |
| IP Address Or Domain | The IP or domain of the MetaDefender Managed File Transfer™ instance used to construct the Redirect URL |
| Redirect URI | The constructed redirection URL to copy and provide in the configuration of the SSO provider |
| Client ID | A unique identifier assigned by the identity provider to registered clients |
| Client Secret | A randomly generated sequence issued by the identity provider and used in client authorization |
| Administrator Emails | A list of email addresses used for assigning administrative privileges to their owners ("administrator" role in Managed File Transfer) |
| Automation Coordinator Emails | A list of email addresses used for assigning automation coordinator privileges to their owners ("automation coordinator" role in Managed File Transfer) |
| Integration Scopes (Optional) | A list of optional scopes for making requests to the IdP |
| Additional endpoints (Optional) | Specifies a list of additional base addresses for endpoints |
The above mentioned, by default used claims can be modified in the "Claims Configuration" part of the SSO set up page.
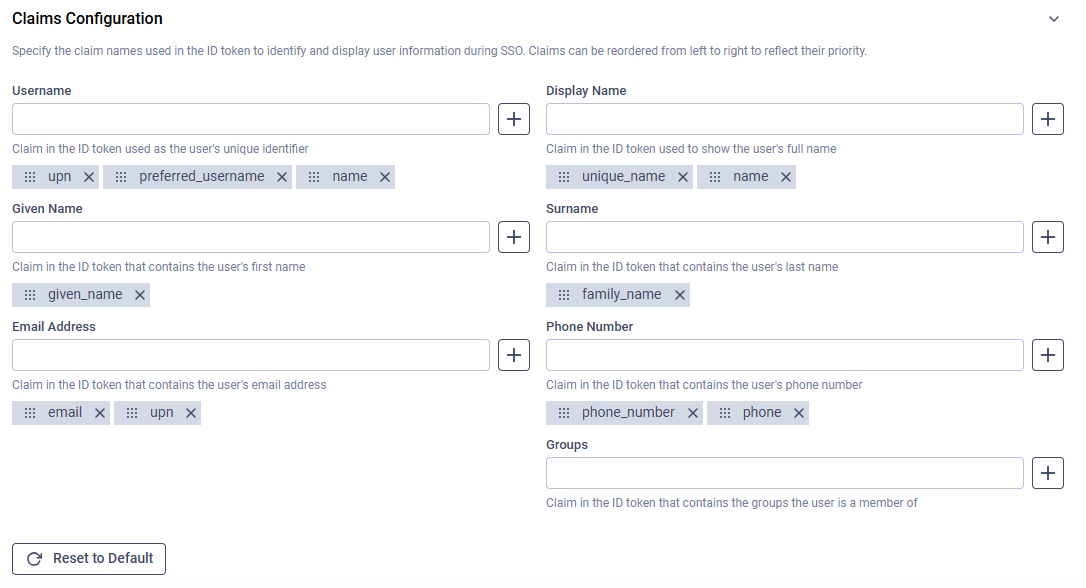
Modern identity providers (e.g., Entra ID) no longer use the upn claim as the email field. To ensure proper user mapping and correct functionality of the Administrator Emails and Automation Coordinator Emails fields, consider adding the preferred_username claim to the Email Address claims.
There is no technical limit to the number of Single Sign-On (SSO) users. Only the license user limit serves as a restriction.
Rate limiting may block authentication with SSO. If this occurs, adjust the rate-limiting settings to suit your needs.

