Title
Create new category
Edit page index title
Edit category
Edit link
Policy
The policy how emails are handled in Email Gateway Security can be configured by the rules under the Security Rules page.
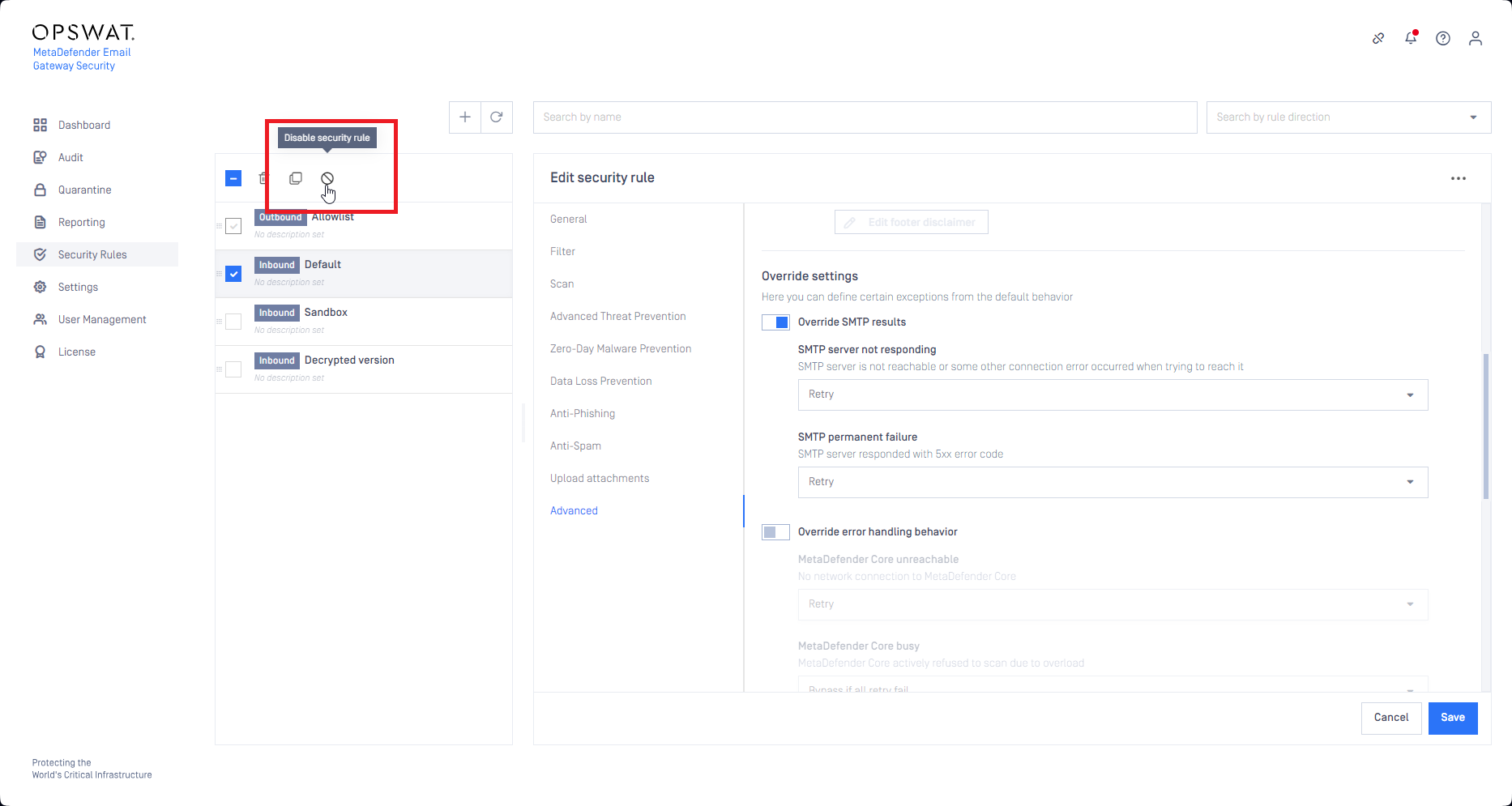
Enable/Disable Security Rules
If you temporarily want to disable one or more Security Rules in MetaDefender Email Gateway Security, select the rule(s) to disable in the list and click the icon. To enable the rule again, select the rule(s) to enable and click the
icon.
Disabling a Security rule can potentially cause emails to be rejected (if no other applicable Security rule can be located).
A disabled rule will still apply when attempting to perform a Rescan of the email.
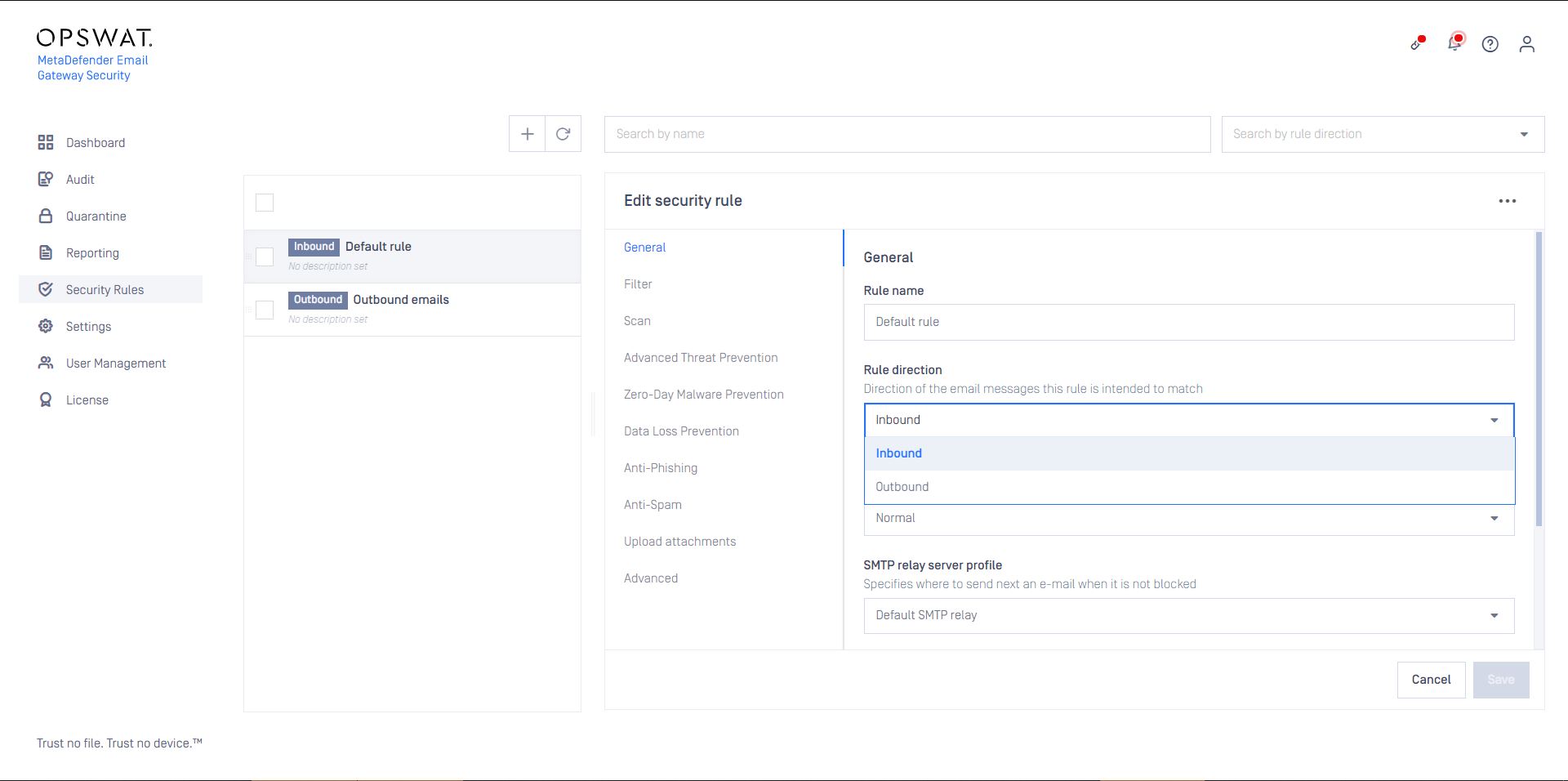
Direction
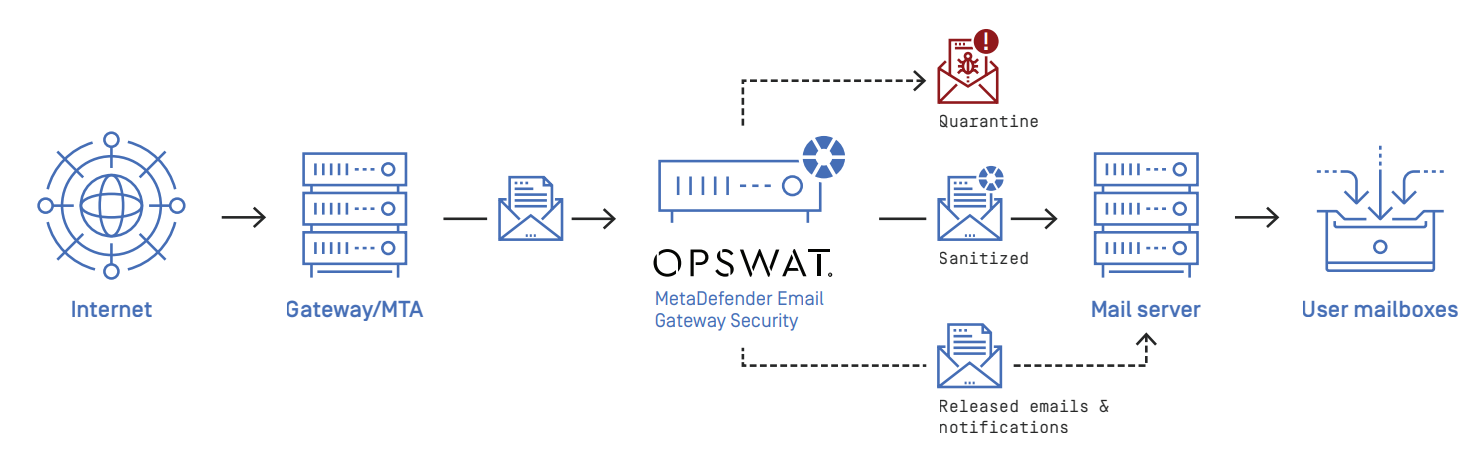
In traditional configurations MetaDefender Email Gateway Security is wedged between the organization's email gateway and mail server (see the image below). In case of inbound email directions the email is received from the email gateway and sent towards the mail server. In case of outbound directions the email is received from the mail server and sent towards the email gateway.

The direction of the email flow can be mapped to security rules in Email Gateway Security with defining:
- Where emails are coming from, and
- Where emails should be sent next after processing.
To configure direction for a certain security rule:
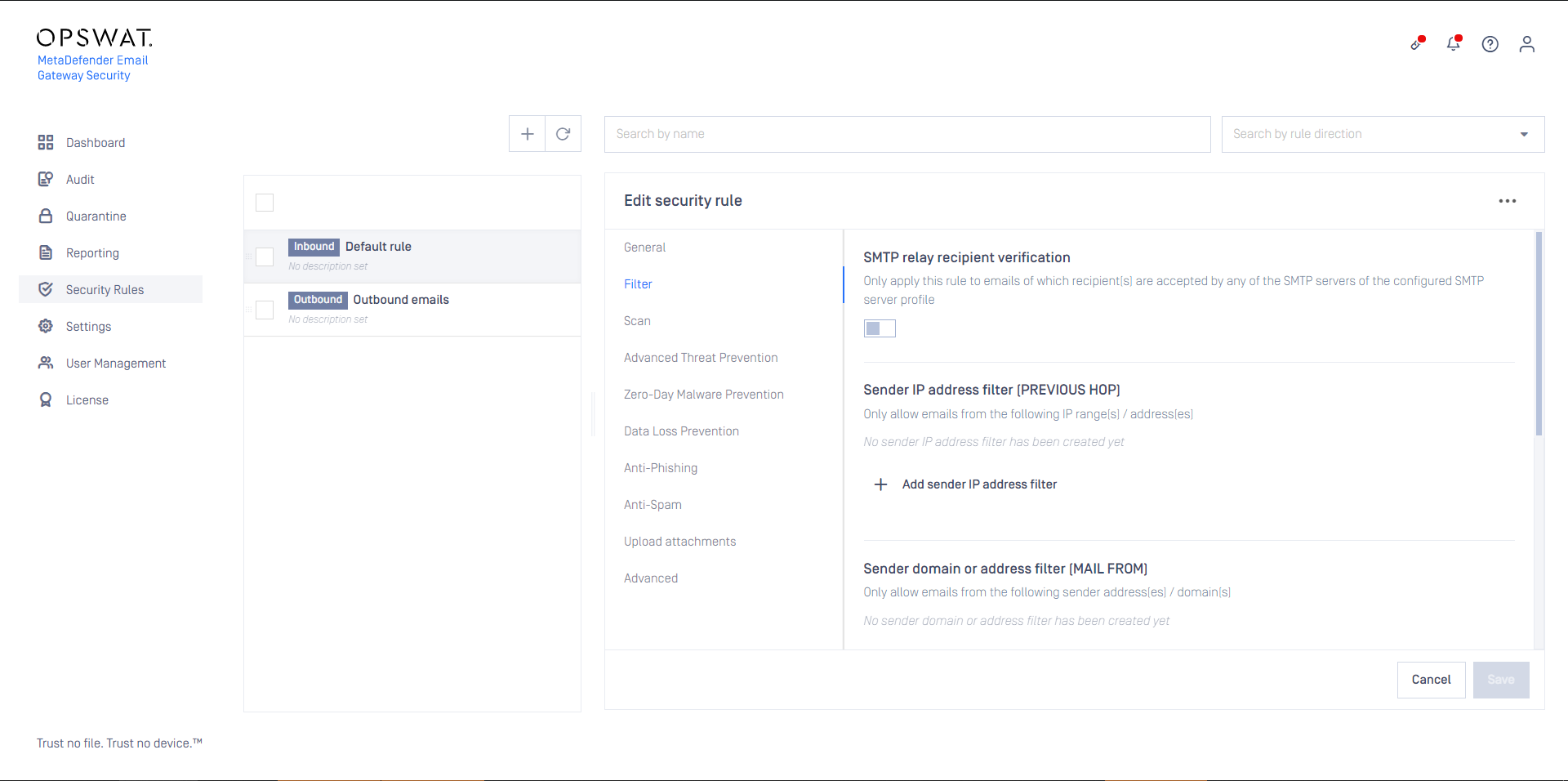
- Apply appropriate filter settings for the Security rules >rule/ FILTER / Sender IP address filter (PREVIOUS HOP) to define where emails matching this rule are coming from.
This option makes Email Gateway Security to ensure that it will be able to forward the accepted emails upon completed processing.
When this option is not enabled, and the recipient of the email is not accepted by any SMTP servers of the server profile, then the email will end up in a retry loop, and finally in permanent failure.
When this option is enabled with no further filtering, then for each email the first rule will match, that will be able to forward that email.
- Select the appropriate SMTP destination in Security rules >rule/ GENERAL / SMTP relay server profile to define where emails matching this rule should be sent next after processing. For further details about server profiles see Configuration/Server profiles.
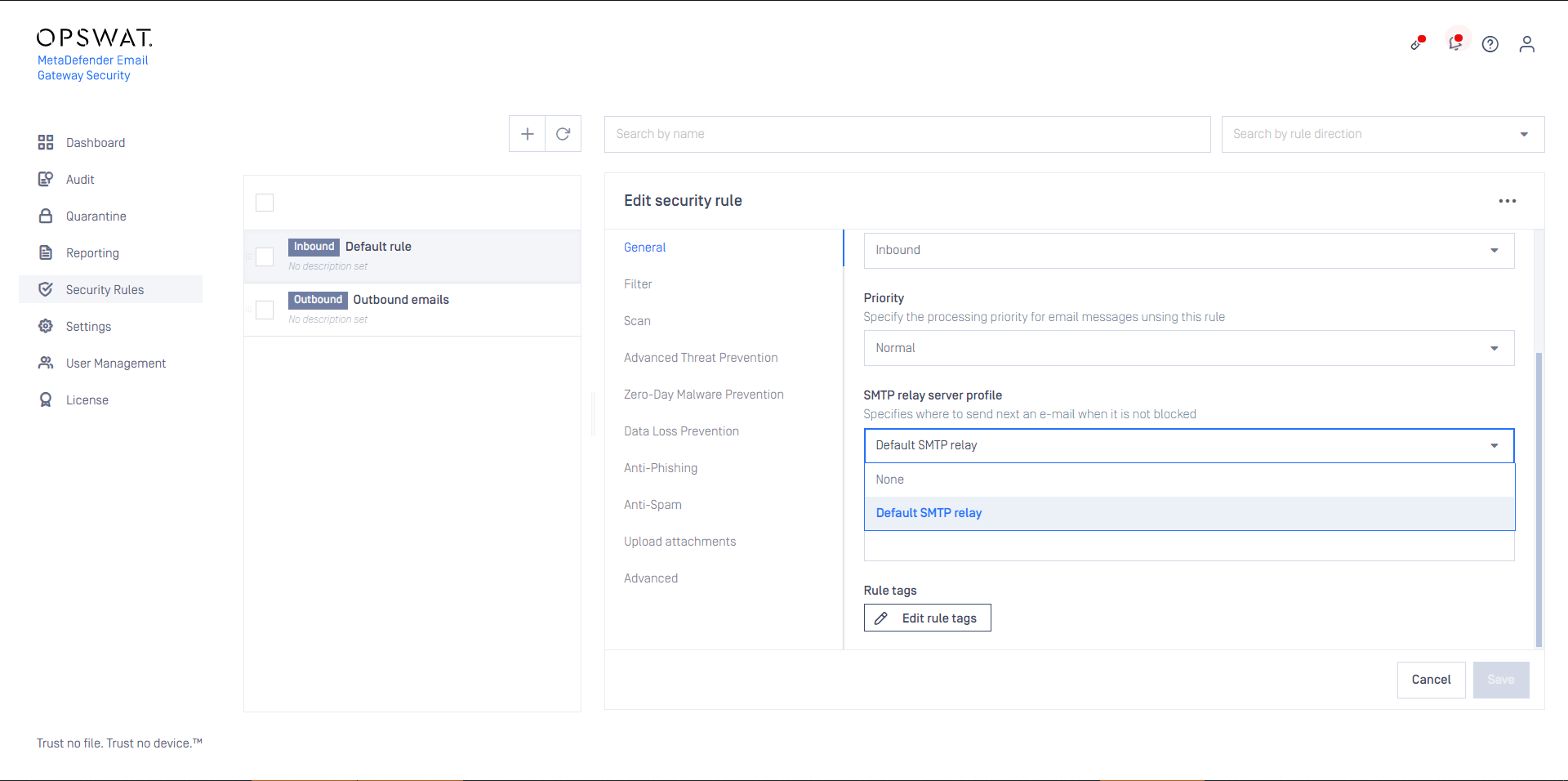
When the filter and the SMTP relay are set appropriately to match emails coming from or going to a certain direction, then the Security rules >rule/ GENERAL / Rule direction can be set accordingly to Inbound or Outbound depending on the direction of the email flow.
DKIM signing
These options enables signing of emails with DKIM (DomainKeys Identified Mail), both for inbound email (ARC) and outbound (DKIM)
As a prerequisite DKIM certificates need to be configured under Settings > Security > Certificates.
Inbound direction: Authenticated Received Chain (ARC)
In most of the cases Email Gateway Security acts as an intermediate email processing server between the original sender and the intended recipient. As Email Gateway Security is not the original sender the SPF check will fail on the recipients side. Email Gateway Security usually modifies emails (adds custom headers, and with Deep CDR and Proactive DLP it often modifies the email bodies and attachments) and as a result the DKIM verification will fail at the recipient.
Authenticated Received Chain is an email authentication system designed to allow an intermediate mail server to sign an email's original SPF and DKIM authentication results. This allows a receiving service to validate an email when the email's SPF and DKIM records are rendered invalid by an intermediate server's processing.
With ARC, an intermediate processing server can digitally sign the SPF/DKIM results of the preceding server and its own modifications to the email with DKIM-like signatures.
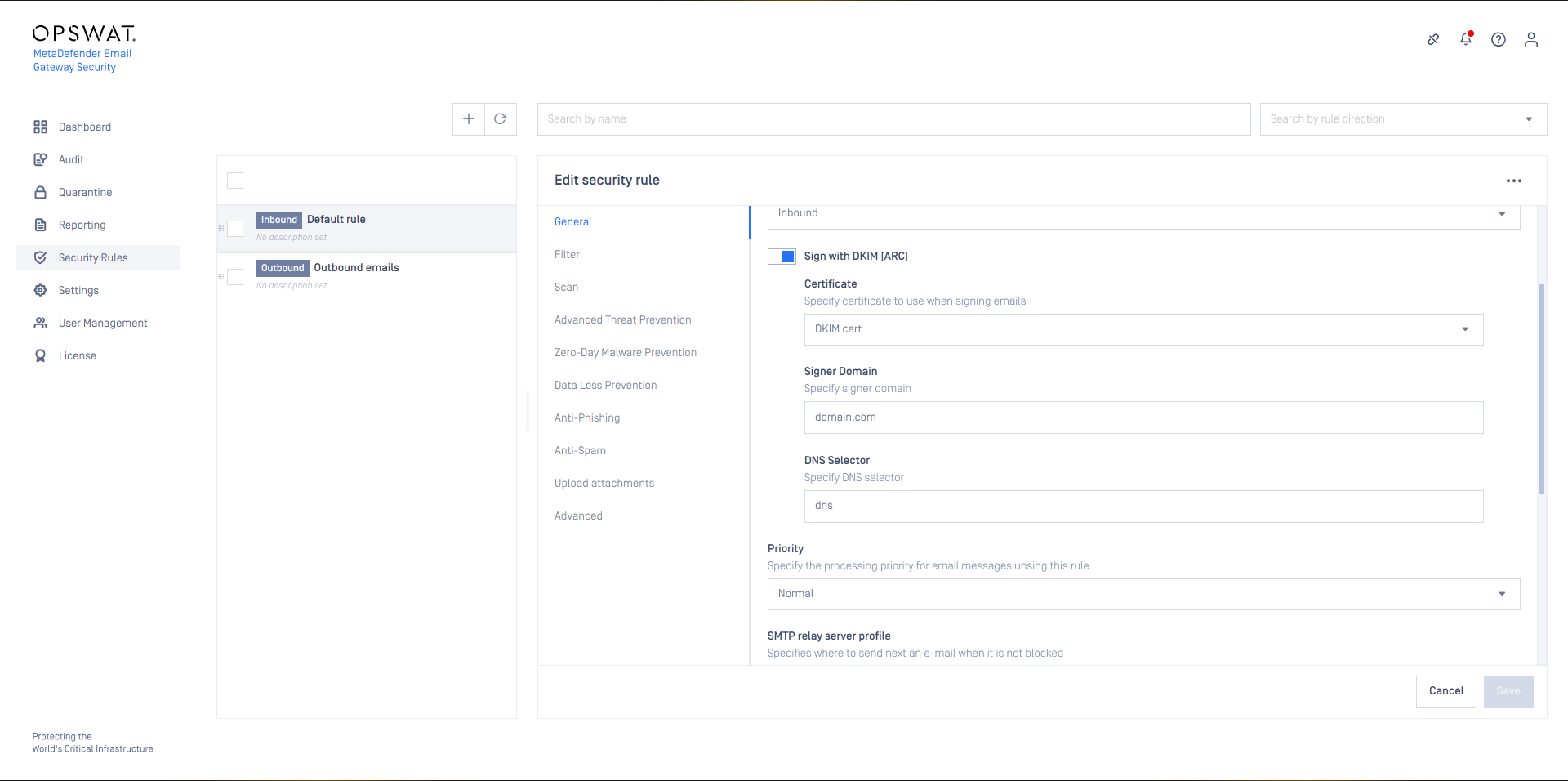
- Certificate: Certificate in Settings > Security > Certificates to be used to create the DKIM/ARC signatures.
- Signer Domain: The domain for which to create the DKIM-like ARC signature. The next email processing server will look up the public keys in the DNS records of this domain to verify Email Gateway Security's ARC signature.
- DNS Selector: Specifies the DNS location of the public key. Receiving servers use this selector to find the public key.
Outbound direction: DKIM signing
If your mail server does not attach a DKIM signature to your email, or if you make modifications to the email in MetaDefender Email Gateway Security you can opt to sign it here.
- Certificate: Certificate in Settings > Security > Certificates to be used to create the DKIM/ARC signatures.
- Signer Domain: The domain for which to create the DKIM signature. The next email processing server will look up the public keys in the DNS records of this domain to verify Email Gateway Security's DKIM signature.
- DNS Selector: Specifies the DNS location of the public key. Receiving servers use this selector to find the public key.
- Optionally, if your previous mail server did add a DKIM signature, then you can remove that, before adding the new one by checking Remove existing DKIM signature before signing.
Priority
Email Gateway Security supports the following three priority queues when processing emails:
- High,
- Normal and
- Low.
The system will always give priority to emails with higher security rule priority.
Processing of Low priority emails will start or continue only if there are no High and/or Normal priority emails waiting for processing.
The default priority for each rule is Normal.
Email History
The priority of the email is displayed in Operating/Email History. The following icons represent each priority:
- High: ↑
- Low: ↓
For Normal priority there is no icon in the Email History.

Rule order
Several security rules can be created that may target different messages from different sources going to different recipients. However, care must be taken how these rules are set up and ordered, as there is a first match and a no match policy (see the next two sections).
Specific rules should come first while generic rules should go at last.

The order of the rules can be set by drag and drop using the ⋮⋮⋮ icon in front of the rule entry (when the drag and drop is active, the mouse pointer changes to
First match policy
If there are more matching rules in the system, then the email message will be accepted/rejected and processed according to the security policy of the first matching rule in the list.
No match policy
If there is no matching rule in the system (or no rule at all), then the email message will be rejected.
Deleting all security rules from the system results all email messages being blocked.
Security rule configuration
Filtering
Recipient verification
When SMTP relay recipient verification is enabled for the rule, then Email Gateway Security will attempt to initiate sending an email to the recipient via the SMTP servers of the SMTP server profile configured for the rule (GENERAL / SMTP relay server profile).
The rule is applied to the email only, if the connection initiation succeeds.
For details see Configuration/Recipient verification.
Sender IP address conditions
Sender IP addresses are the addresses of infrastructure elements in the deployment, from which MetaDefender Email Gateway Security is allowed to receive emails according to this rule.
In case of a traditional setup, for example, sender is the email gateway for inbound messages and the mail server for outbound messages.
| Type | IP address or subnet | |
|---|---|---|
| Match type | EQUALS | |
| Examples | IP | 10.0.0.1 |
| Examples | IP range | 10.0.0.0/24 |
There is OR relation among entries in sender IP address conditions.
Sender domain or address conditions
Sender filter makes possible to apply security rule based on from what email address the email was sent. The value is taken from the SMTP communication’s MAIL FROM command that holds an email address.
When using this filter please be aware of the fact that spoofing the sender of the email is a very easy task. A more secure way to use this filter would be for OUTBOUND emails only along with filtering to the sender IP.
Field details
| Value type | email address |
|---|---|
| Field type | .NET Regex |
| Match type | regular expression match |
| Examples |
|
To avoid unexpected matching, special regular expression characters must be taken into consideration.
For example:
- The
.(dot) in a regular expression matches any character. This means that.+@opswat.comcan matchtest@opswat1com. If you want to match explicitly for a dot you should escape it like this:.+@opswat\.com - The
^(hat) and$(dollar) characters match the beginning and end of the string respectively. The regular expressiontest@opswat\.commay unexpectedly matchthis_is_test@opswat.combesidestest@opswat.com. To matchtest@opswat.comexplicitely, use the regular expression^test@opswat\.com$.
For more details see .NET Regular Expressions.
There is OR relation among the sender domain or email address conditions.
Recipient domain or address conditions
Recipient conditions can help to restrict emails matched by the rule to specific recipients. The value is taken from the SMTP communication’s RCPT TO command that holds an email address.
Recipient domain or email address conditions can also help to counter emails sent to invalid recipients; that do not even exist at an organization or among the partners, for example.
This kind of defense may protect against unnecessary overloads or even against malicious attacks.
Field details
The field details are identical to the field details of the sender domain or address conditions (for details see the Sender domain or address conditions section).
Email header conditions
Email header conditions help to define email processing based on the email headers rather than SMTP properties (for example as email and SMTP properties are sometimes not in-line, e.g. email From and SMTP MAIL FROM may be different).
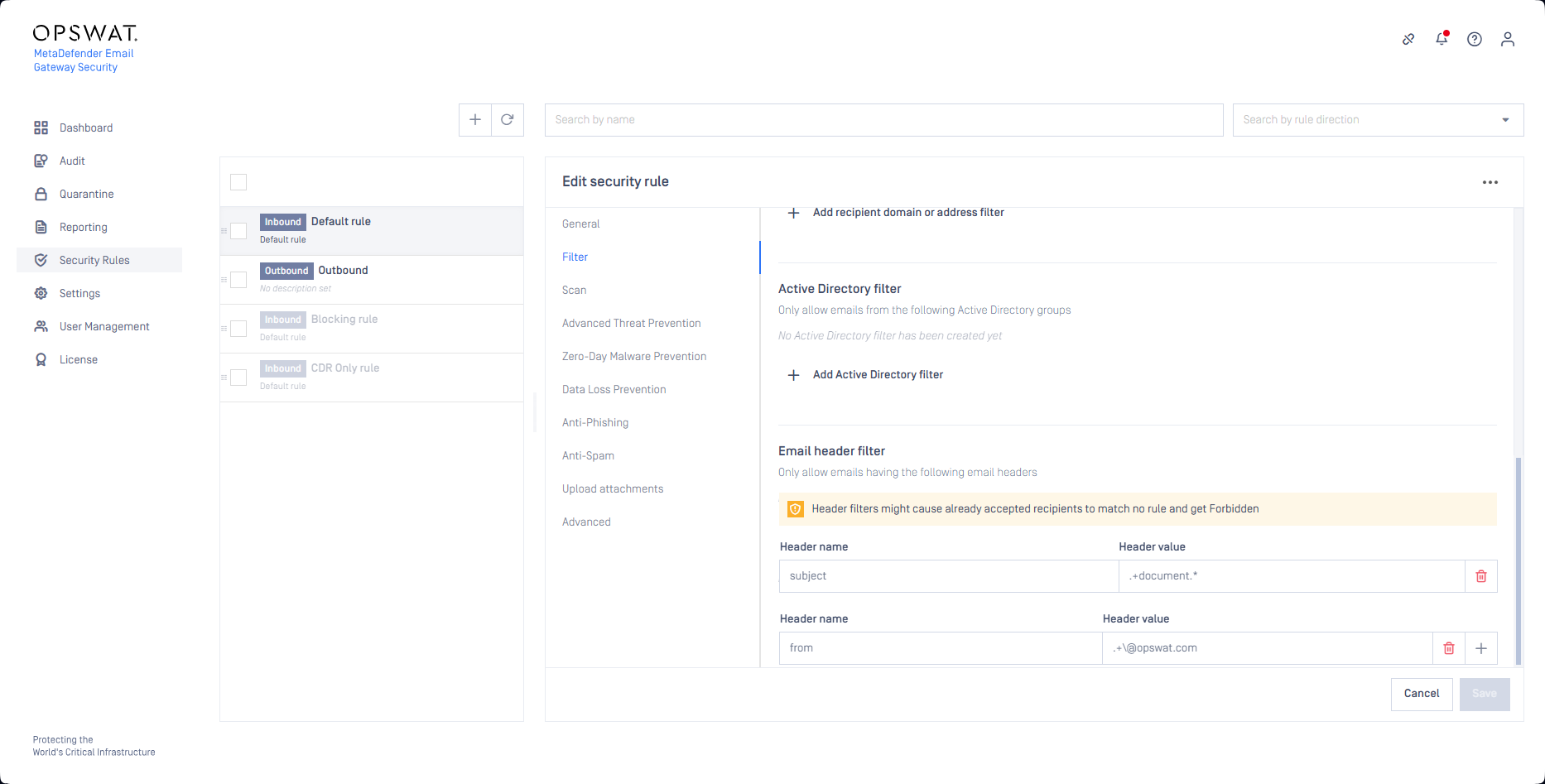
Header filters might cause already accepted recipients to finally match no rule. When there is no matching rule, the email (for the recipients that have no matching rule) can not be processed and delivered. Such messages are retained in Email Gateway Security's Email History with the classification Forbidden.
For details see the Forbidden subsection in Permanent failure statuses and Failed and Forbidden emails.
Field details
There is OR relation among the email header conditions.
Header name
| Value type | RFC 5322 field name |
|---|---|
| Field type | text |
| Case sensitivity | case insensitive |
| Match type | EQUALS |
| Examples |
|
Header value
| Value type | RFC 5322 unstructured |
|---|---|
| Field type | .NET Regex |
| Case sensitivity | case insensitive |
| Match type | regular expression match |
| Examples |
To avoid unexpected matching, special regular expression characters must be taken into consideration.
For example:
- The
.(dot) in a regular expression matches any character. This means that.+@opswat.comcan matchtest@opswat1com. If you want to match explicitly for a dot you should escape it like this:.+@opswat\.com - The
^(hat) and$(dollar) characters match the beginning and end of the string respectively. The regular expressiontest@opswat\.commay unexpectedly matchthis_is_test@opswat.combesidestest@opswat.com. To matchtest@opswat.comexplicitly, use the regular expression^test@opswat\.com$.
For more details see .NET Regular Expressions.
Regular expressions for the header value are always treated with case insensitive.
For example hello as the header value pattern will match both hello and Hello even when case insensitive option is not applied.
SMTP relay
After processing, emails must be forwarded by Email Gateway Security to an SMTP destination so that recipients can receive them.
For each security rule the SMTP destination can be set in Security rules >rule/ GENERAL / SMTP relay server profile to define where emails matching this rule should be sent next after processing. For further details about server profiles see Configuration/Server profiles.
Rule actions
It is possible to add disclaimers and/or tags to all emails processed by a specific security rule.
Rule disclaimer
To add a disclaimer to all emails processed by this specific rule, enable the option Security rules >rule/ GENERAL / Rule disclaimer and configure the disclaimer content using the disclaimer editor.
Rule tags
To add one or more tags to all emails processed by this specific rule, click on the option Security rules >rule/ GENERAL / Rule tags and complete the configuration in the tag editor.
Security policy
The security policy of a certain rule is defined by the settings on the SCAN, ADVANCED THREAT PREVENTION, ZERO-DAY MALWARE PREVENTION, ANTI-PHISHING, UPLOAD ATTACHMENTS and ADVANCED tabs.
Scan
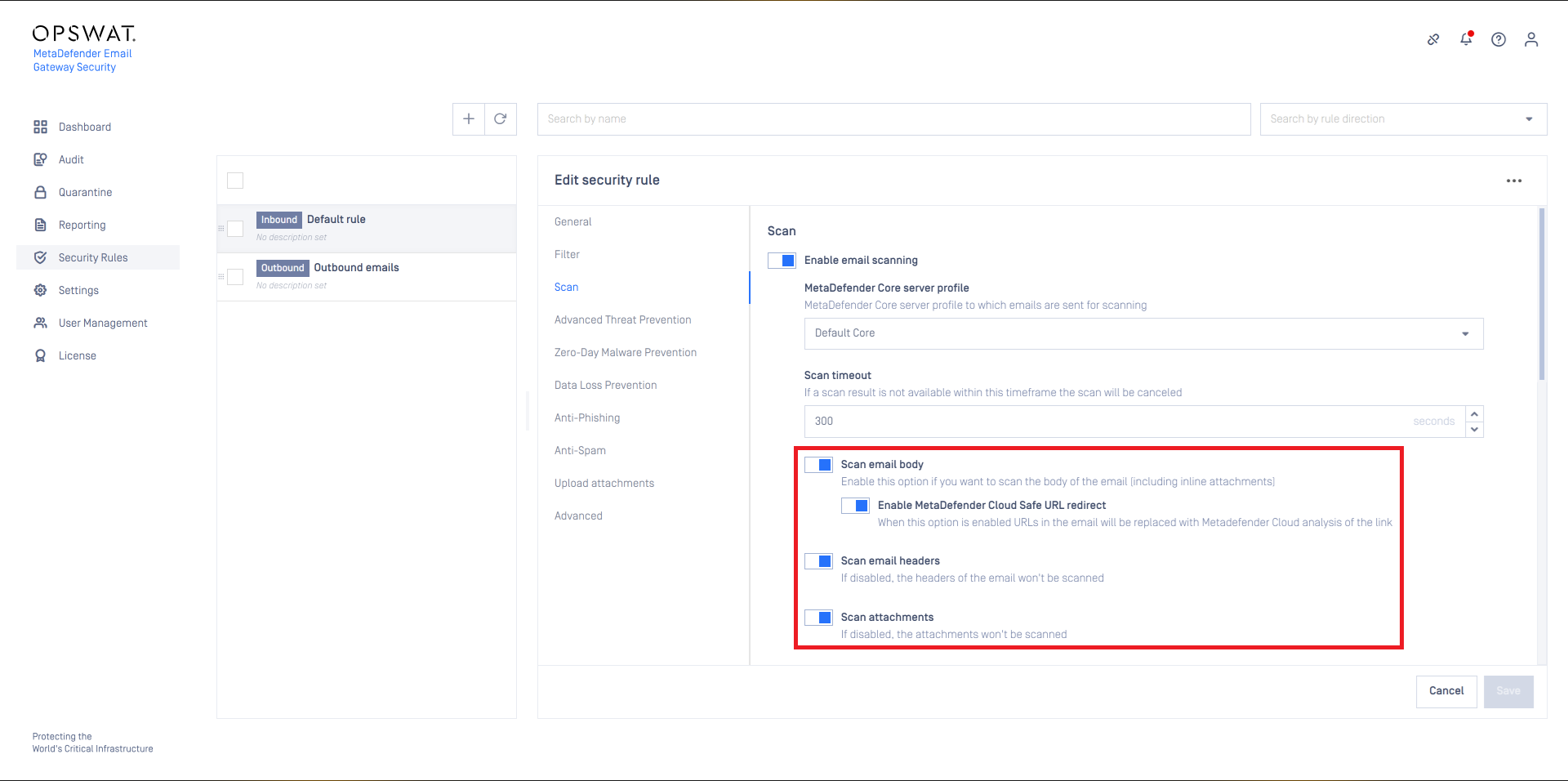
On the Scan tab of a certain rule it can be defined if emails matching this rule must be scanned at all, or not.
MetaDefender Core server profile
A MetaDefender Core server profile to which emails are sent for malware scanning and zero-day malware prevention. For further details see Configuration/Server profiles.
Scan email headers, body and attachments
Email Gateway Security is capable to process email headers, body and attachments, thus find malicious or sensitive content not only in attachments, but even in the body or headers.
Scan email body will scan the body (both the HTML and the plain text body) including all the inline, embedded attachments (inline attachments are the non-text elements embedded into the HTML email body, e.g. inline images).
If Enable MetaDefender Cloud Safe URL redirect is turned on, all links in the email body will be redirected through MetaDefender.comSafe URL redirect service for URL reputation check.
For the MetaDefender Cloud Safe URL redirect feature to work properly, MetaDefender Cloud’s Reputation API must be licensed.
For demonstration purposes, however, a limited number of Reputation API calls are available for free of charge.
Scan attachments can toggle scanning the regular (non-inline) attachments.
An email with an embedded (inline) image attachment:
An email with a regular attachment (in Thunderbird):
Attaching scan results
For certain use-cases it may be beneficial to attach the MetaDefender Core scan results to the email. This is supported by enabling the Attach scan results option.
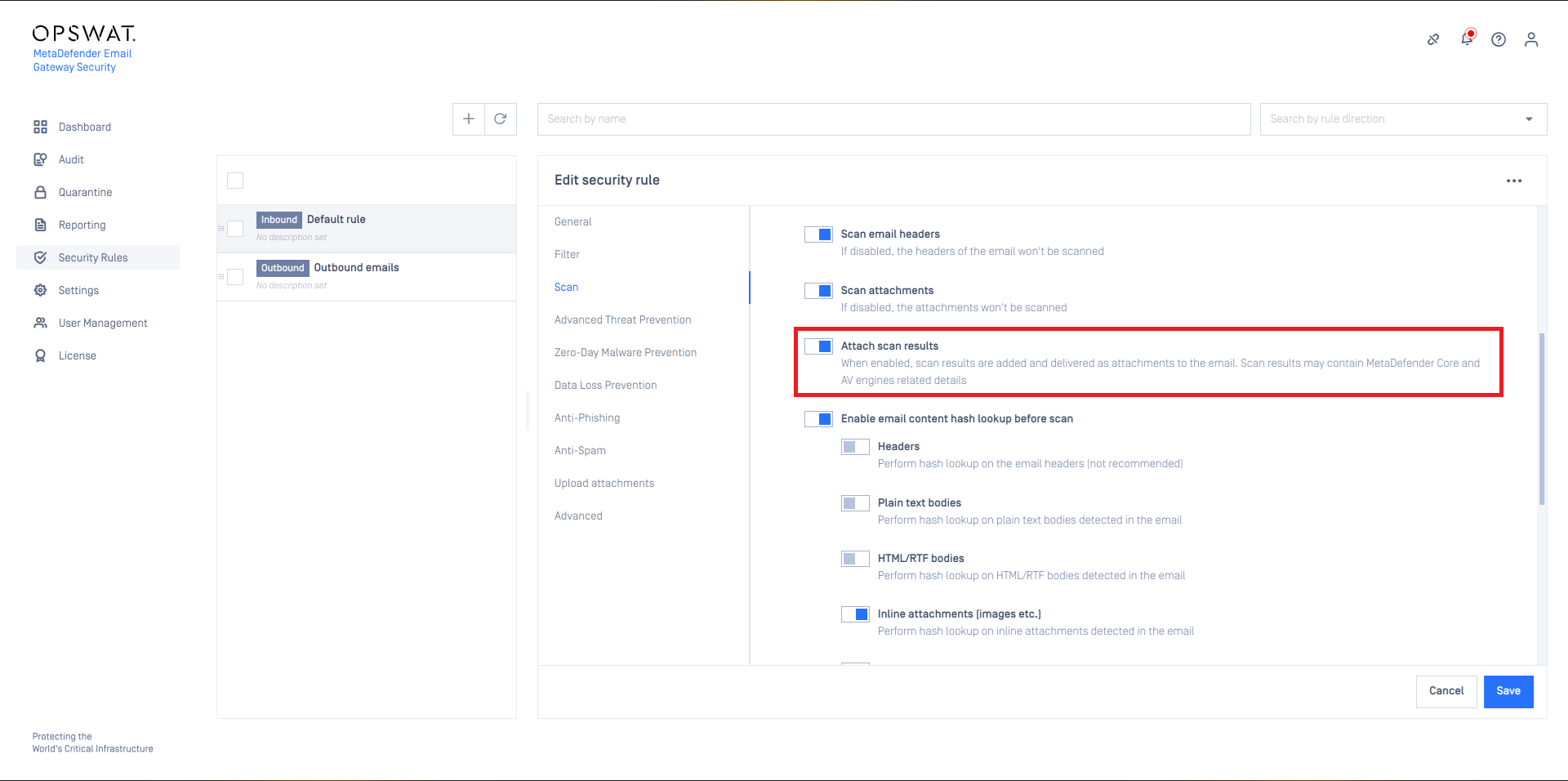
Hash lookup
To shorten email processing time Email Gateway Security can be configured to perform hash lookups to MetaDefender Core and MetaDefender Cloud (whatever is set as the MetaDefender Core type server profile for the rule).
If the email header, body or attachment is found by the hash, then it won't be sent to MetaDefender Core / Cloud for scanning or processing. This way the scanning and processing time can be saved.
MetaDefender Core / Cloud will return the cached scan results and the cached processed version of the header, body or attachment.
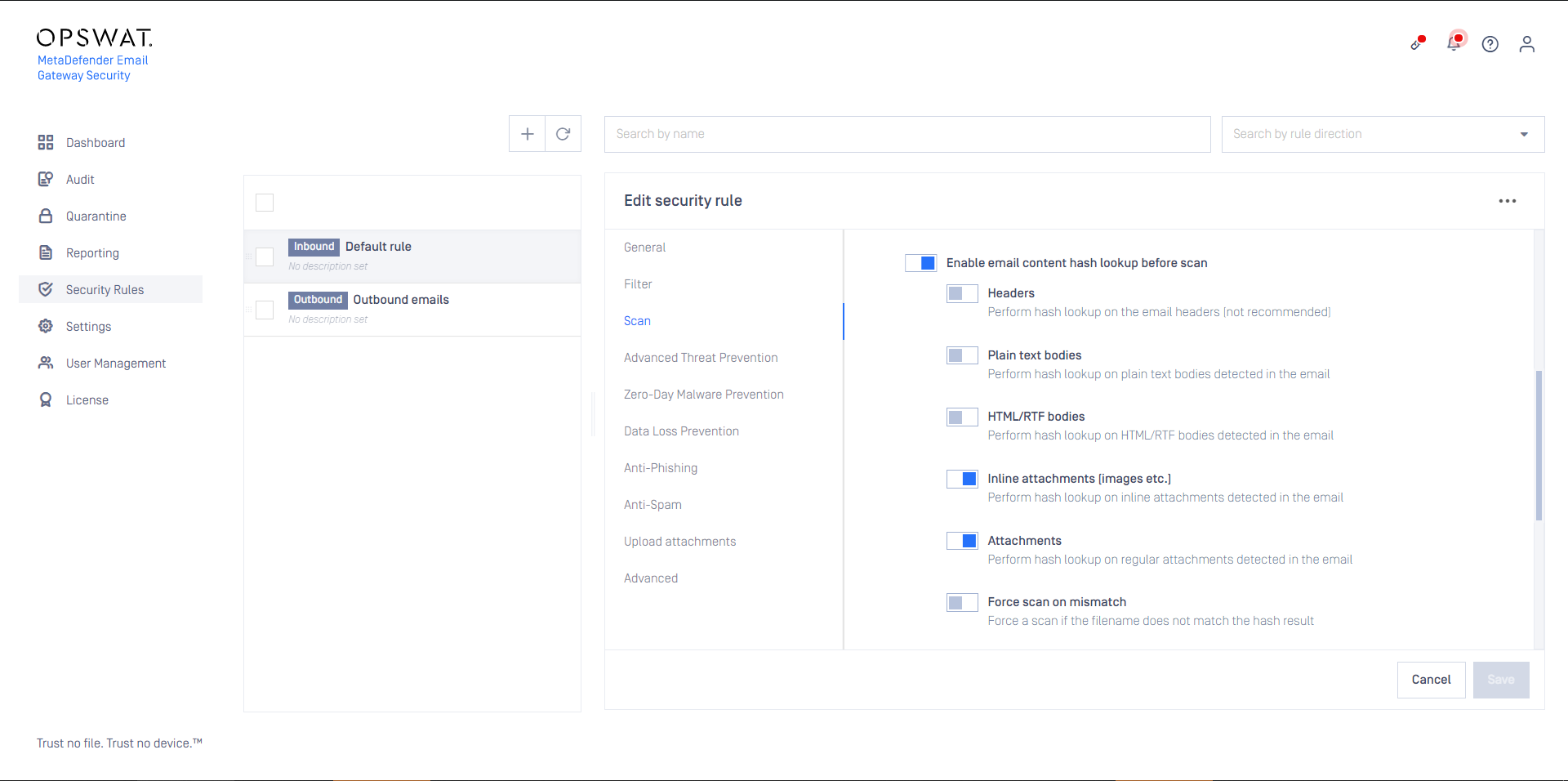
Email headers are always different, but bodies and attachments can be the same among separate emails (for example in case of a newsletter that is sent to hundreds of recipients within an organization). Email Gateway Security comes with reasonable defaults to do hash lookup on attachments (both inline and non-inline attachments).
Hash lookups give a benefit only when parts of the email were previously scanned and exist in the cache.
If the email part does not exist in the cache, then the time of the hash lookup adds to the time of the processing and as so for such a case the total processing time will be longer than without the hash lookup.
Enabling Force scan on mismatch the hash lookup will be omitted when the actual file name and the cached file name do not match. In this case the header, body or attachment will be forcibly scanned, even if the result already exists in the cache based on the hash of the file. For further details see Configuration/Email History/Malware scan details.
Advanced Threat Prevention
Using multiscanning, Email Gateway Security can utilize even 20 anti-malware engines to prevent advanced, unknown threats.
On this tab it can be configured what Email Gateway Security should do if its Advanced Threat Prevention feature found malware in one or more components of the email.
If Quarantine original email is enabled, then the original copy of the email is put into the Operating/Quarantine regardless of how Handling of the email is set.
Handling of the email may be:
- Block email: the email is blocked. If Notify recipients if email is blocked is enabled, then a notification will be sent to the recipients. For further details see Configuration/Alert, notification and quarantine report emails.
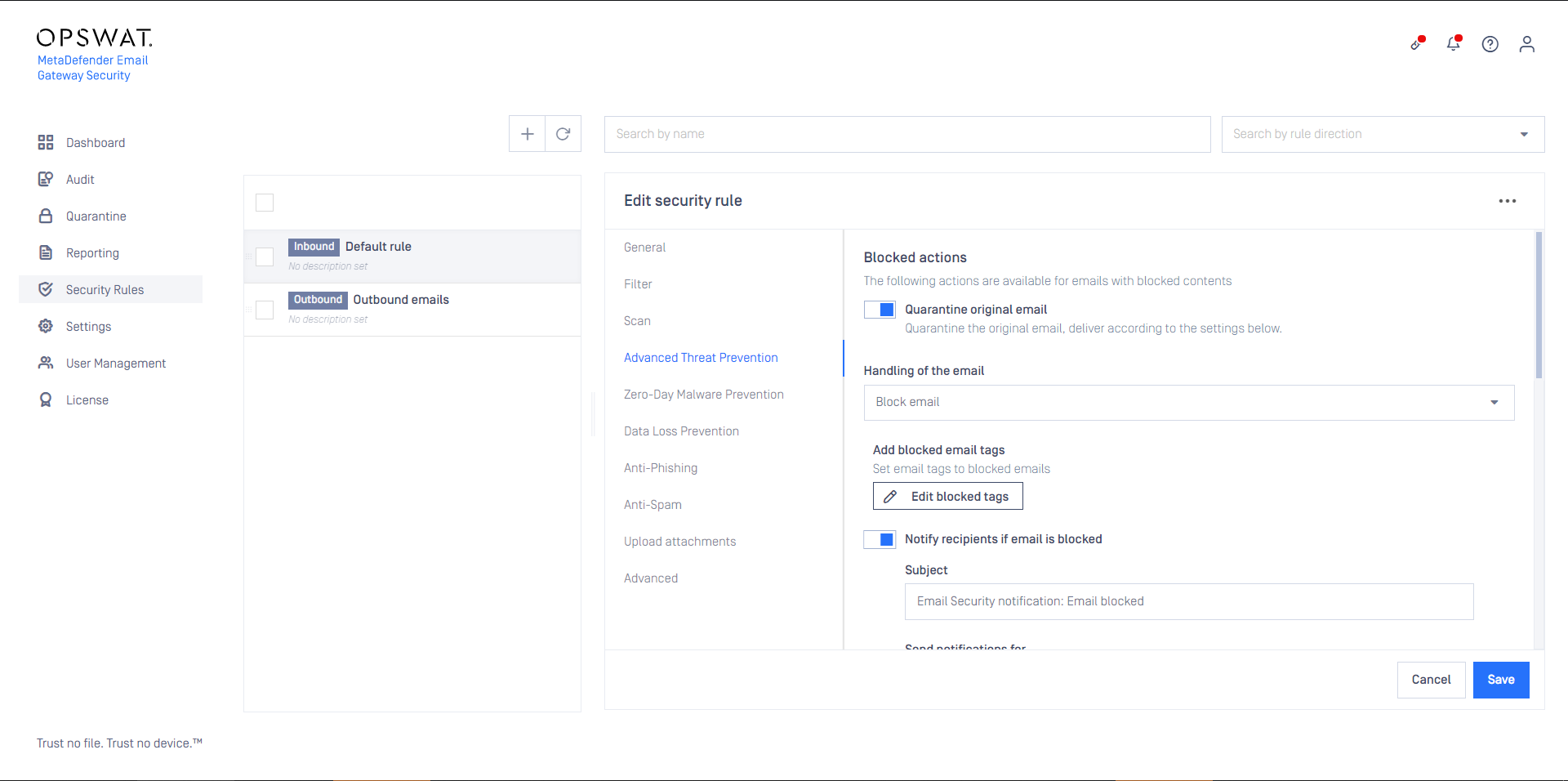
- Delete blocked contents: the blocked contents (e.g. infected attachments) are removed from the email. The remaining is delivered.
- Deliver blocked contents: the email is delivered containing the potentially malicious (infected) contents.
For Delete blocked contents or Deliver blocked contents options Email Gateway Security provides customization to remove attachments.
Selecting Deliver blocked contents will deliver potentially malicious contents to recipients.
If Email Gateway Security is set to Notify recipients if email is blocked then notifications may be limited to the case of emails with password protected attachments. To do so set Send notifications for to Only emails with password protected attachments.
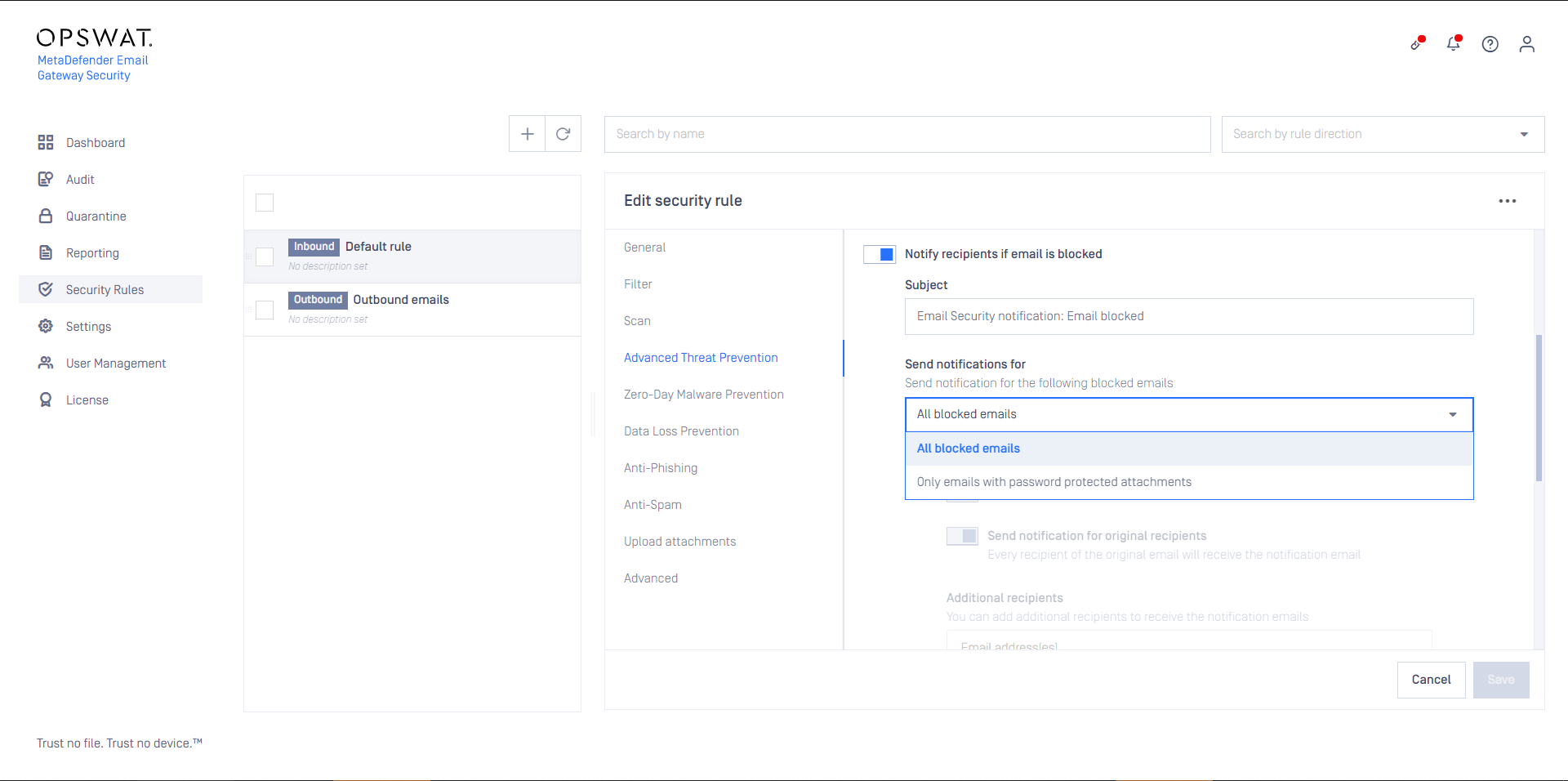
Blocked notifications
It is possible to send the recipient a blocked notification when an email is blocked and put in quarantine. The options available for the notifications are:
Subject
Allows customization of the notification subject.
Send notification for original sender
Send the notification to the original email sender (recommended for outbound emails).
Send notification for original recipient(s)
Send the notification to the original email recipients (recommended for inbound emails).
Additional recipients
Allows sending the notification to a set to fixed recipients, such as an administrator etc.
Action permissions
When sending a blocked notification it is possible to permit the recipient to perform actions on the quarantined email.
The following permissions are supported:
- Rescan emails: Allows the recipient to initiate a rescan of the content. This is useful, for example, when an email contains password protected attachments. The use can specify the password(s) and allow MetaDefender Email Gateway Security to scan the decrypted content
- Anti-malware rescan: Similar to Rescan emails except that anti-spam and anti-phishing checks are skipped. This way false positive spam or phishing emails can be delivered while anti-malware measures (Multiscanning, Deep CDR, Sandbox, etc.) still apply.
- Delete emails: Allows the recipient to permanently delete the email from the Quarantine. This could be allowed for, for example, spam emails that the recipient does not wish to receive or keep.
- Deliver original emails: Allows the recipient to deliver the quarantined (unscanned) email. This permission is not recommended since it could potentially deliver malicious content to the recipient.
- Release request: Allows the recipient to request the release of an email. An email that has been requested for release will obtain the 'Release request' classification which informs the administrator that a recipient wants his email released.
In order for an administrator to be informed of release requested emails an administrator Quarantine Report can be created, filtering on the Release Request classification. For more information, see Configuration/Quarantine reports.
Notification email headers
Add the custom headers (X-headers) defined here to the notification email.
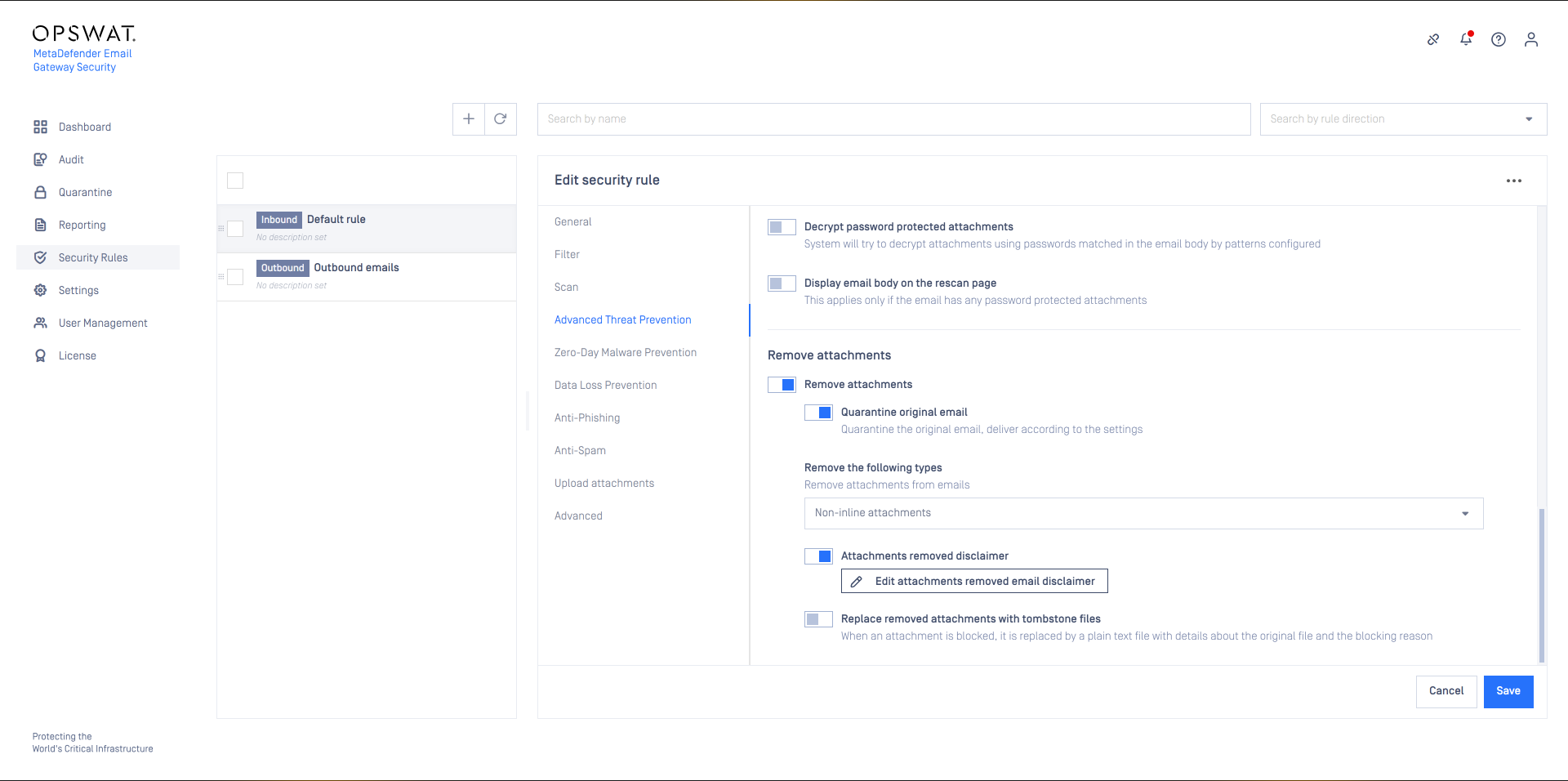
Encrypted attachments
Email Gateway Security supports functionality to automatically attempt to decrypt attachments by analyzing the email body for possible password(s). To enable this functionality, select the option Decrypt password protected attachments.
Email Gateway Security use regular expressions to find the password in the email body. These regular expressions can be configured under Settings > General / Attachment password patterns.
For details see Attachment password patterns.
In case password(s) cannot be located in the email body, a notification email can be sent (Handling of the email is set to Block email) or disclaimer can be added (Handling of the email is set to Delete blocked contents) to the email, allowing the recipient to provide the password and rescan the email.
Sometimes it is the email body that contains the instructions how the password needs to be formulated. For this use-case Email Gateway Security can display the email body in the rescan page. To use this feature, enable the Display email body on the rescan page option.
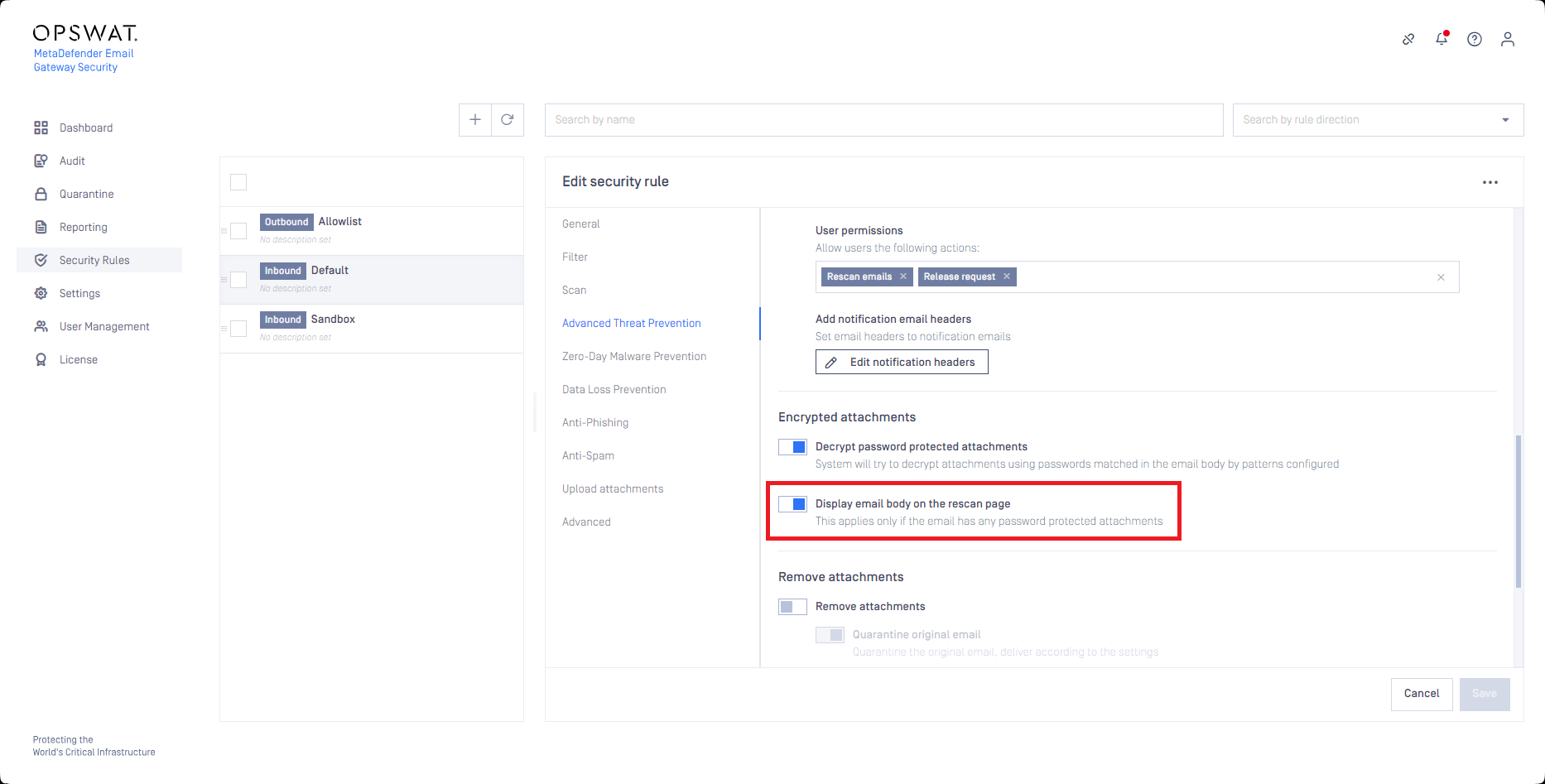
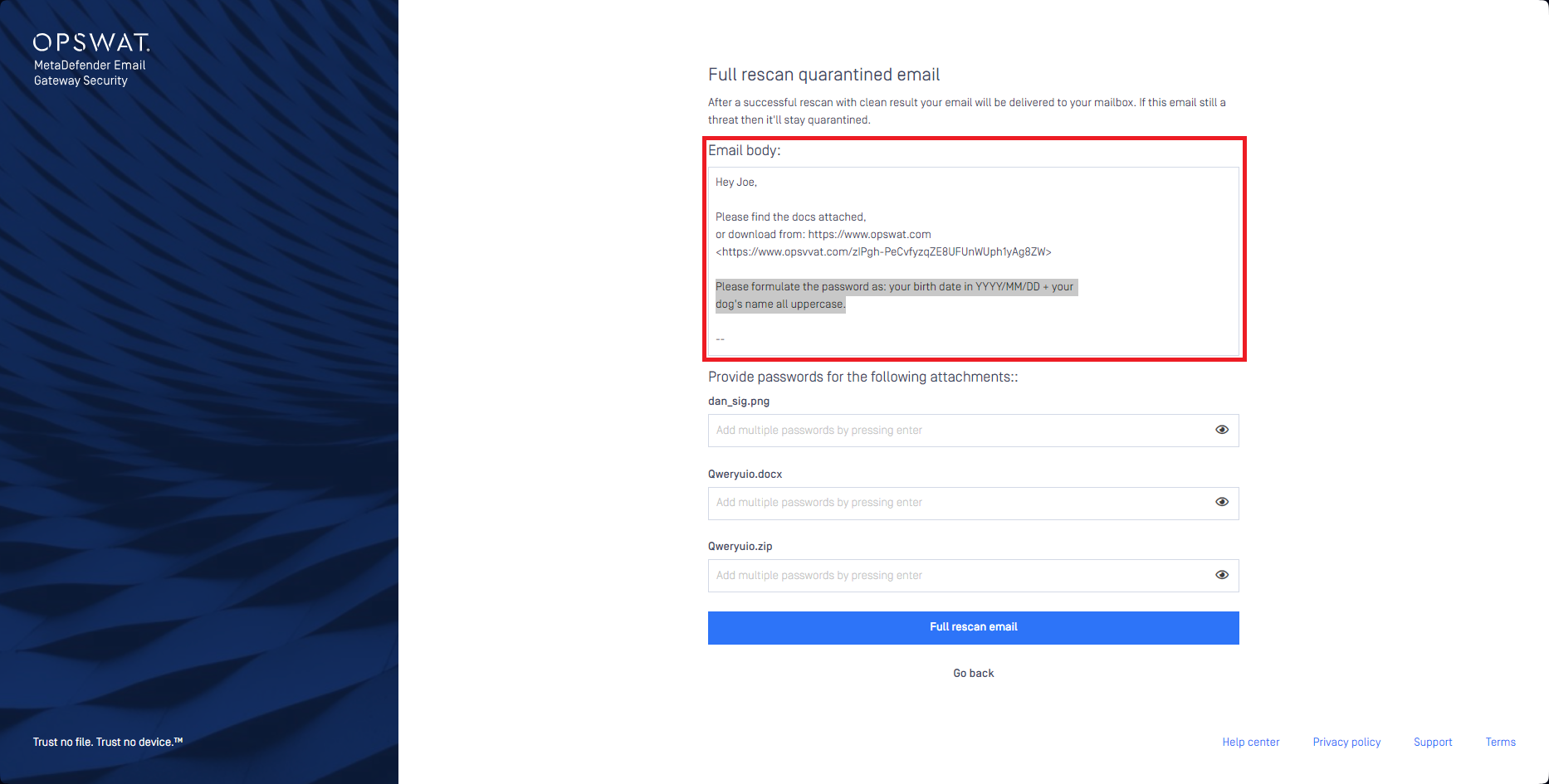
Use the Encrypted disclaimer to customize the message added to the email requesting a rescan (not applicable when Block Email is selected as Handling of the email action)
Password storage
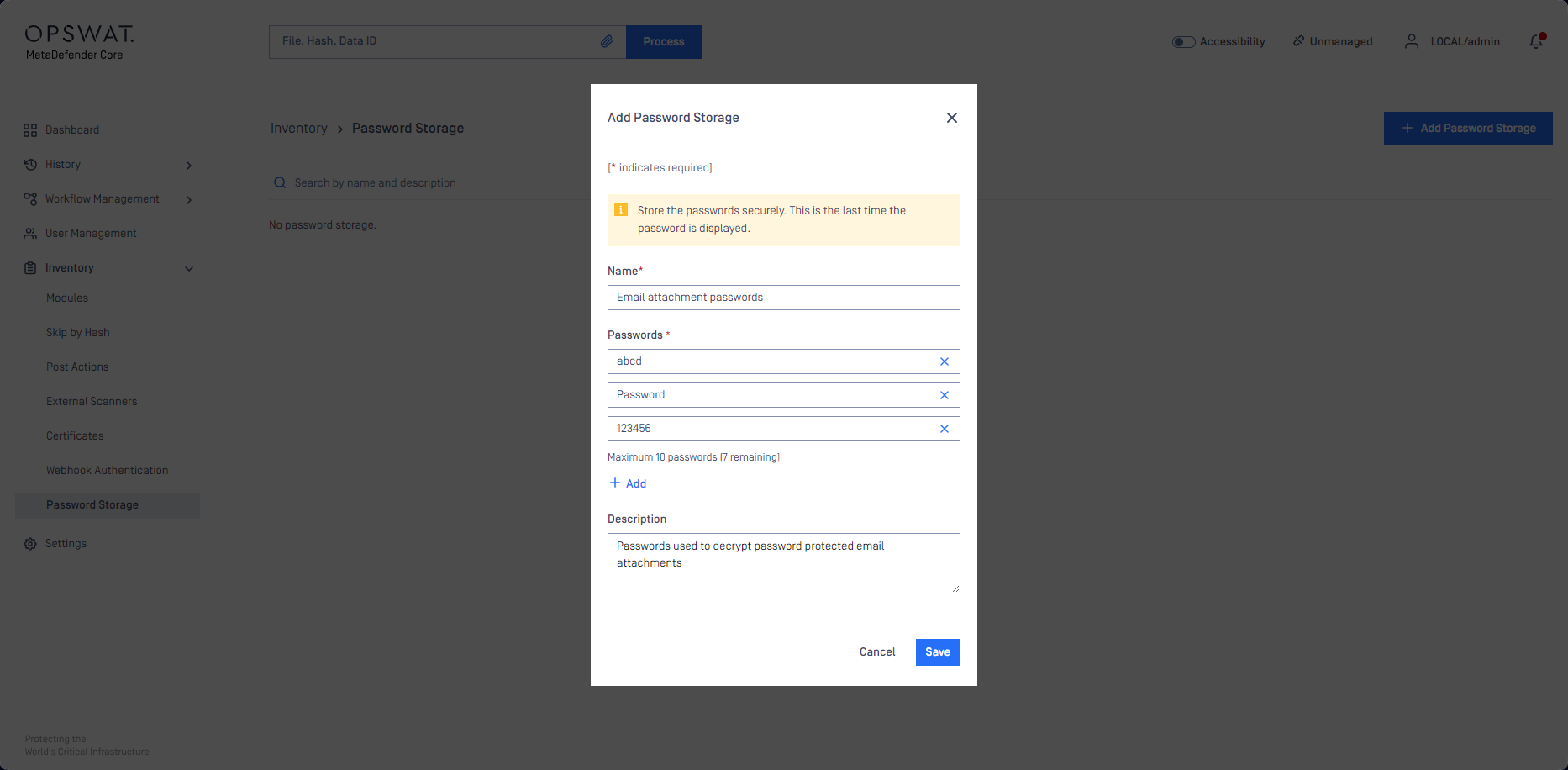
From MetaDefender Core version 5.12.0, password storage is supported in Core workflows. When Email Gateway Security is integrated to Core using a workflow where password storage is configured, then Core will attempt to decrypt encrypted attachments using the passwords configured in the Core workflow. This way encrypted attachments may be processed automatically without the need to extract the password from the email body or to request the password from the recipient.
Password storage requires two steps to work with MetaDefender Core workflows:
- Define one or more password storage(s) under Inventory > Password Storage in Core
- Link the password storage(s) to the workflow under Workflow Management > Workflows / [Workflow] / Archive / Password storage
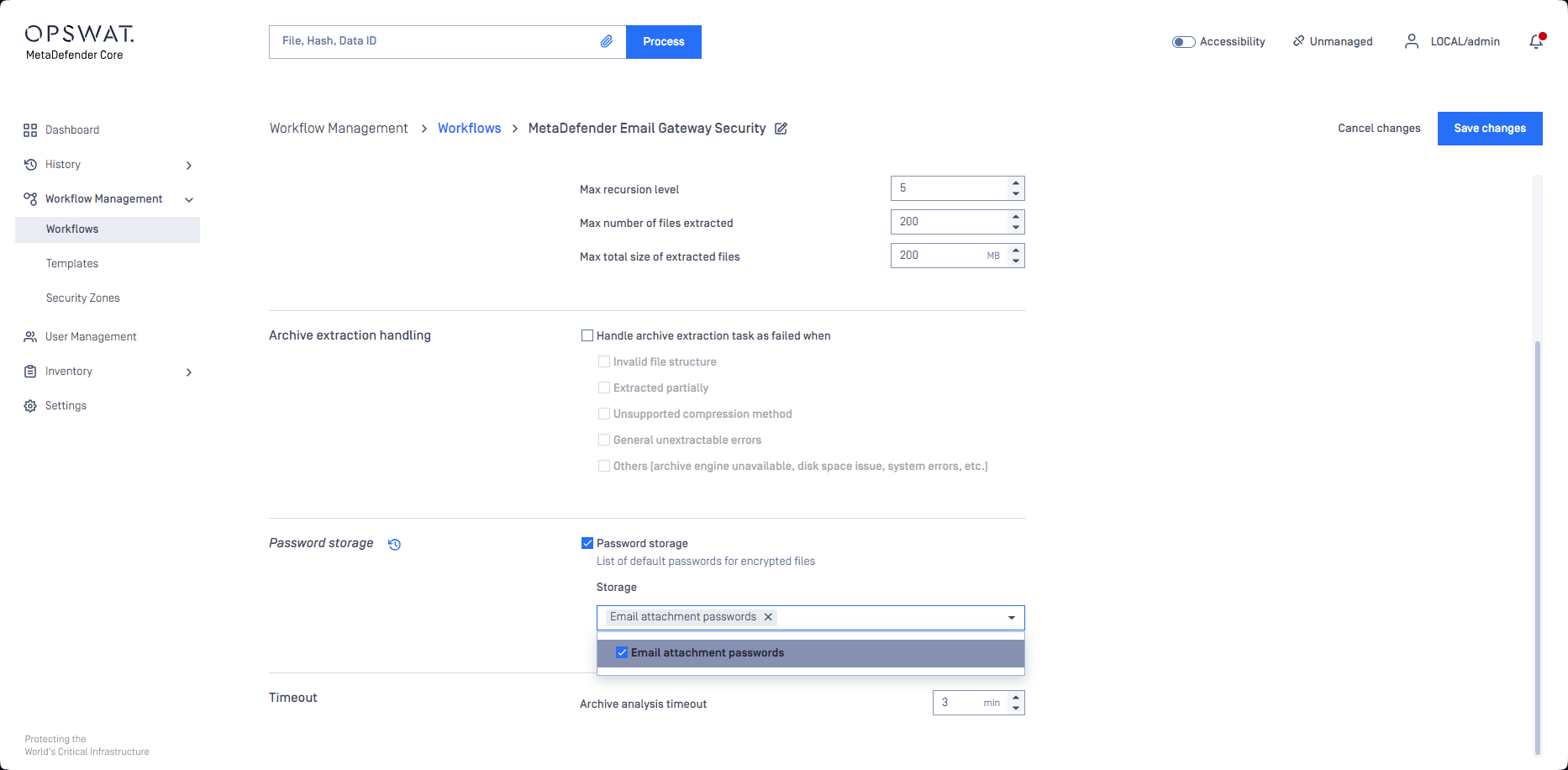
For details see the Password storage for handling encrypted file section in MetaDefender Core 5.12.0 Release notes.
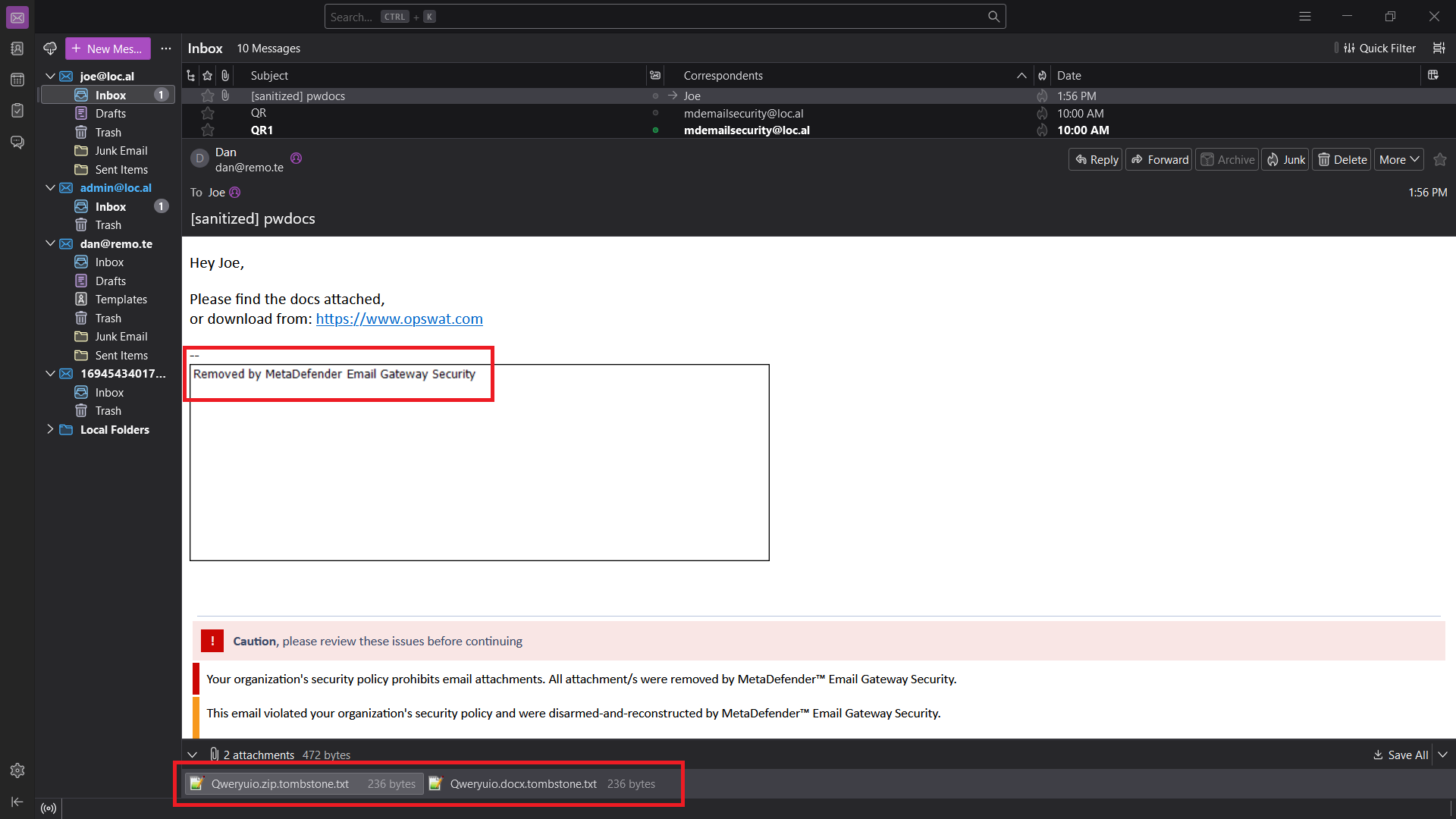
Tombstone files
For the use-cases where Email Gateway Security might remove attachments:
- Handling of the email is set to Delete blocked contents or
- Remove attachments is enabled
it is supported to replace the removed attachment (both inline and regular attachments) with a tombstone file.
A tombstone file is a small plain text placeholder file to replace the original, blocked attachment.
File name format: <original attachment file name>.tombstone.txt
Contents:
{ "data_id":"<data id of original file scan result processed by MetaDefender Core>", "file_info": { "sha256": "<SHA256 hash of original file>" }, "process_info": { "blocked_reason": "<blocked reason to indicate why original file was blocked>" }}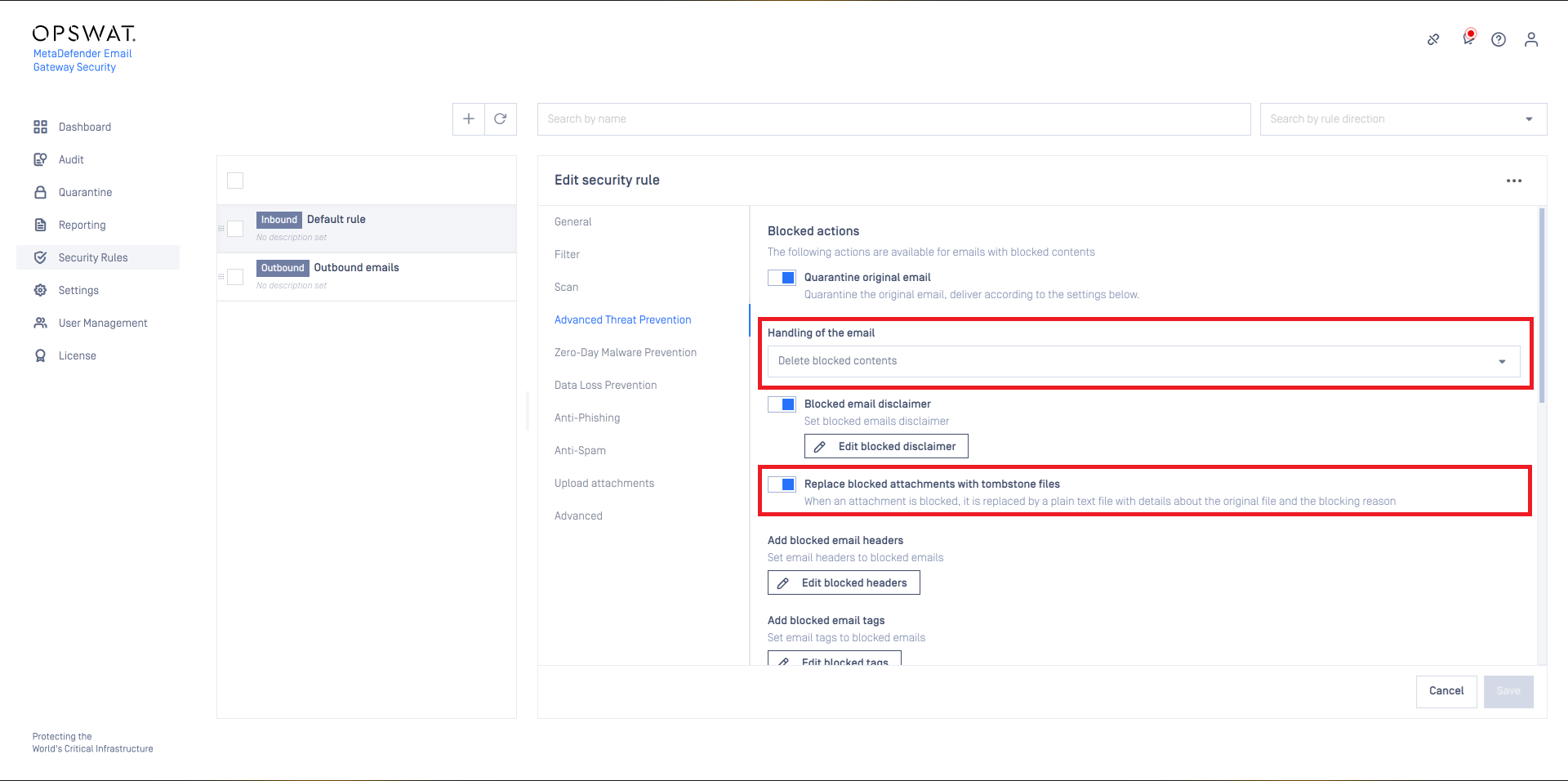
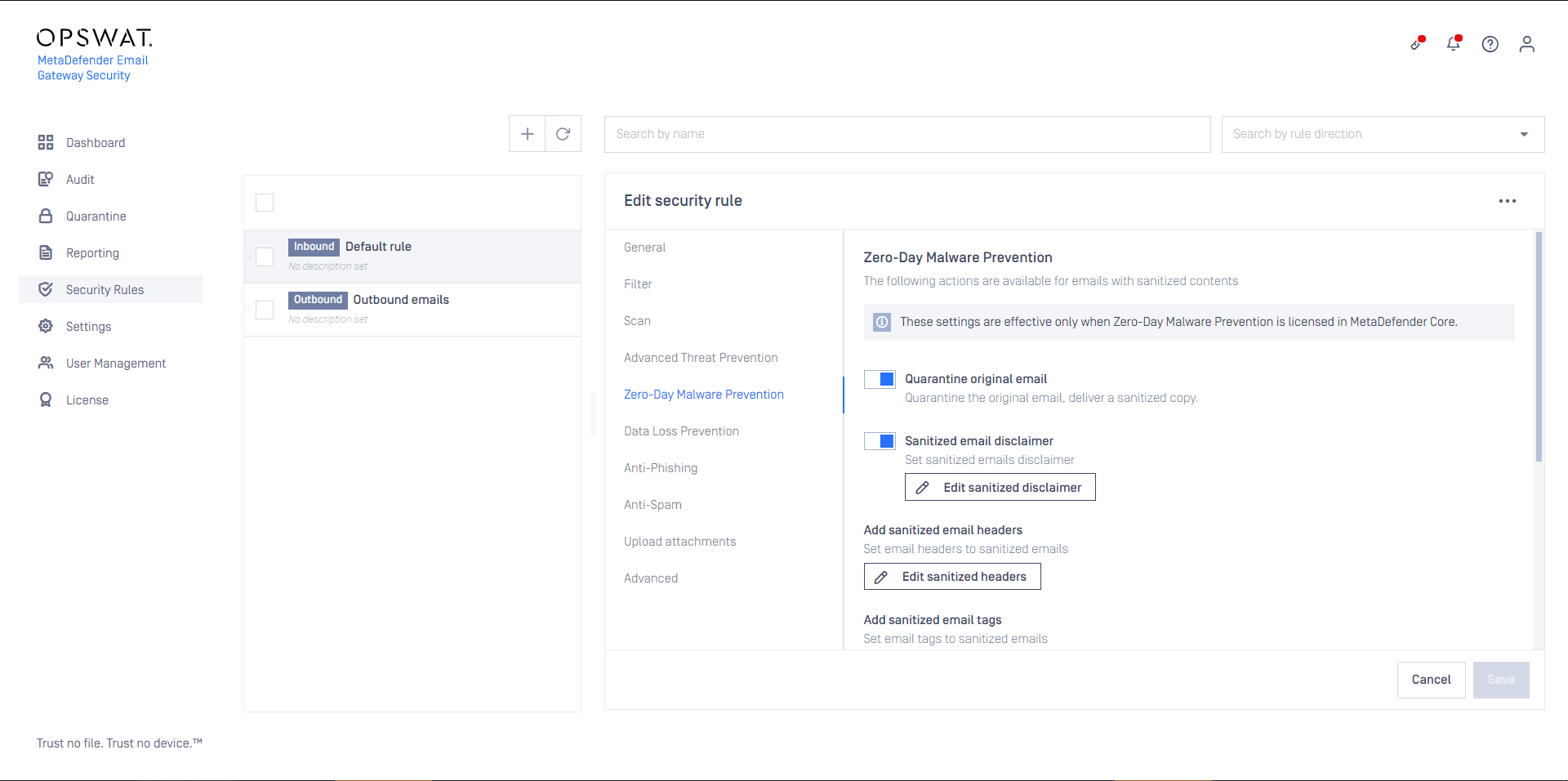
Zero-Day Malware Prevention
Using content disarm and reconstruction, Email Gateway Security can prevent zero-day malware in over 100 common file types.
The content disarm and reconstruction capabilities can be configured for each MetaDefender Core server. For further details see Configuration/Server profiles.
On this tab it can be configured what Email Gateway Security should do if its Zero-Day Malware Prevention feature applied disarm and reconstruction to one or more components of the email.
If Quarantine original email is enabled, then the original copy of the email is put into the Operating/Quarantine.
Overriding sanitization behavior
Sanitization can fail for two reasons in Email Gateway Security:
- The Deep CDR engine fails to sanitize the file (the file type version is not supported or the engine has other trouble)
- The email body is converted by the Deep CDR engine to a file type that is not supported as email body (e.g. the plain text body is converted to pdf).
Only the following email body file type conversions are allowed in Email Gateway Security:
- txt
txt - html
html - html
txt
Any other email body file type conversion set in the Deep CDR engine will cause a sanitization failure.
By default Email Gateway Security removes all the bodies and attachments for which the sanitization failed from the email to be delivered.
The default behavior can be customized enabling the Override sanitization behavior option and selecting the cases for which Email Gateway Security should deliver the original copy of the body or attachments in case of a sanitization failure.
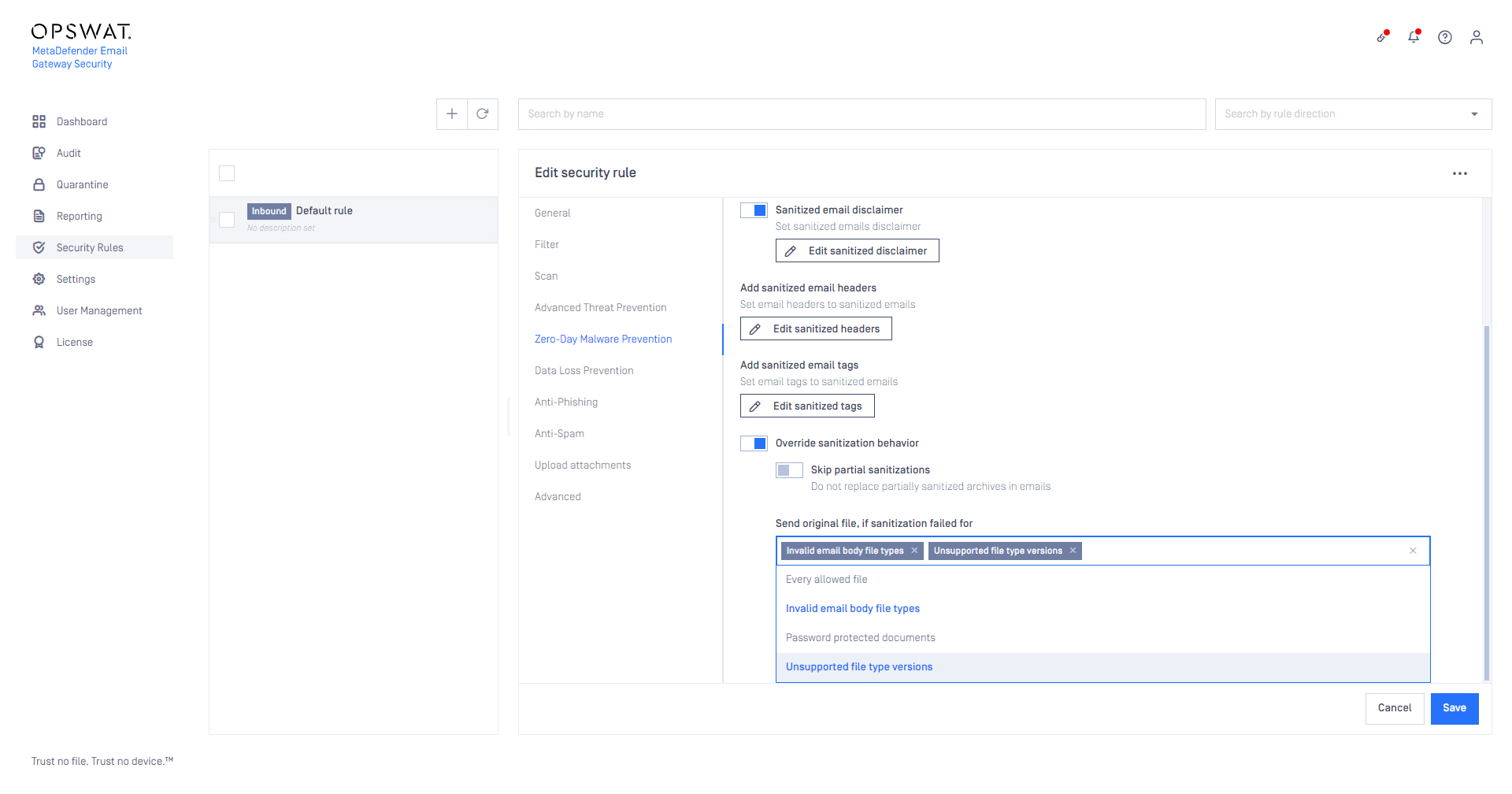
Data loss prevention
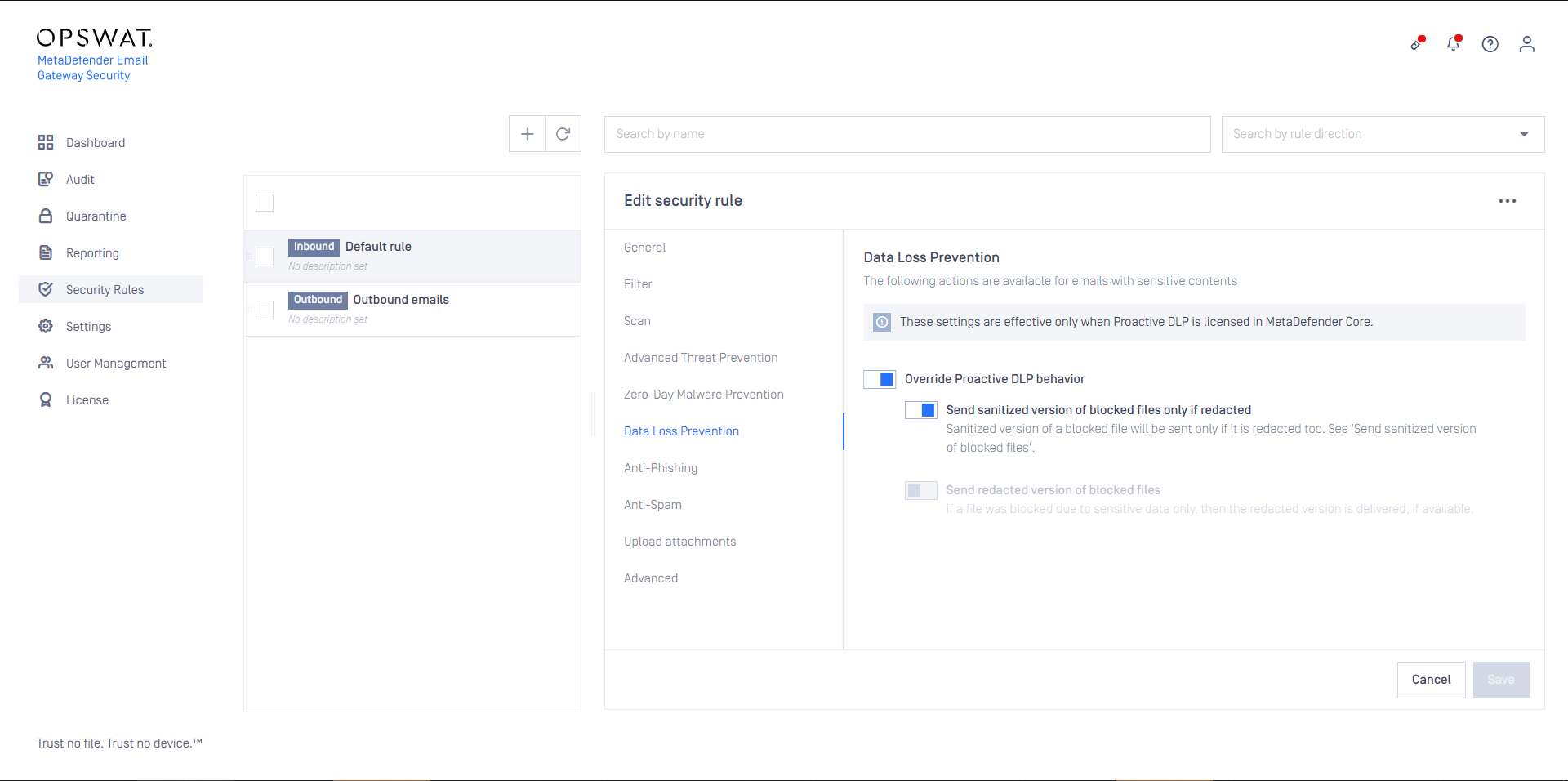
When Proactive Data Loss Prevention is licensed (see Installation/Licensing), certain behavior of the technology can be modified on this tab.
Enabling Send sanitized version of blocked files only if redacted can influence the setting under Zero-Day Malware Prevention / Override sanitization behavior / Send sanitized version of blocked files. A sanitized version is sent only, if it could have been successfully redacted, too.
As of today, Proactive DLP can detect sensitive data in PowerPoint presentations (.ppt), but can not redact.
If both Send sanitized version of blocked files and Send sanitized version of blocked files only if redacted then the sanitized version won’t be sent for .ppt files as they can not be redacted.
Enabling Send redacted version of blocked files will deliver redacted email contents - when redaction is available for the file type - if they were blocked due to sensitive data only.
Malware infected contents won’t be delivered even when this option is enabled.
Anti-phishing and anti-spam
Email Gateway Security provides cutting edge anti-spam and anti-phishing protection. Spam and phishing are handled by the same component so the settings are quite similar. For specific settings see the two subsections at the end of this section.
Probability level
The anti-spam and anti-phishing component use the Probability level setting to tell the component what it should treat as Possible spam or Possible phishing (for details see Operating/Email classifications) and what is known Spam or Phishing (for details see Operating/Email classifications).
Email Gateway Security can assign the following probability levels to spam and phishing emails:
- 0: not a spam or phishing,
- 1-8: possible spam or phishing (the higher the number, the higher the probability),
- 9: known spam or phishing.
The levels 0 and 10 are not configurable.
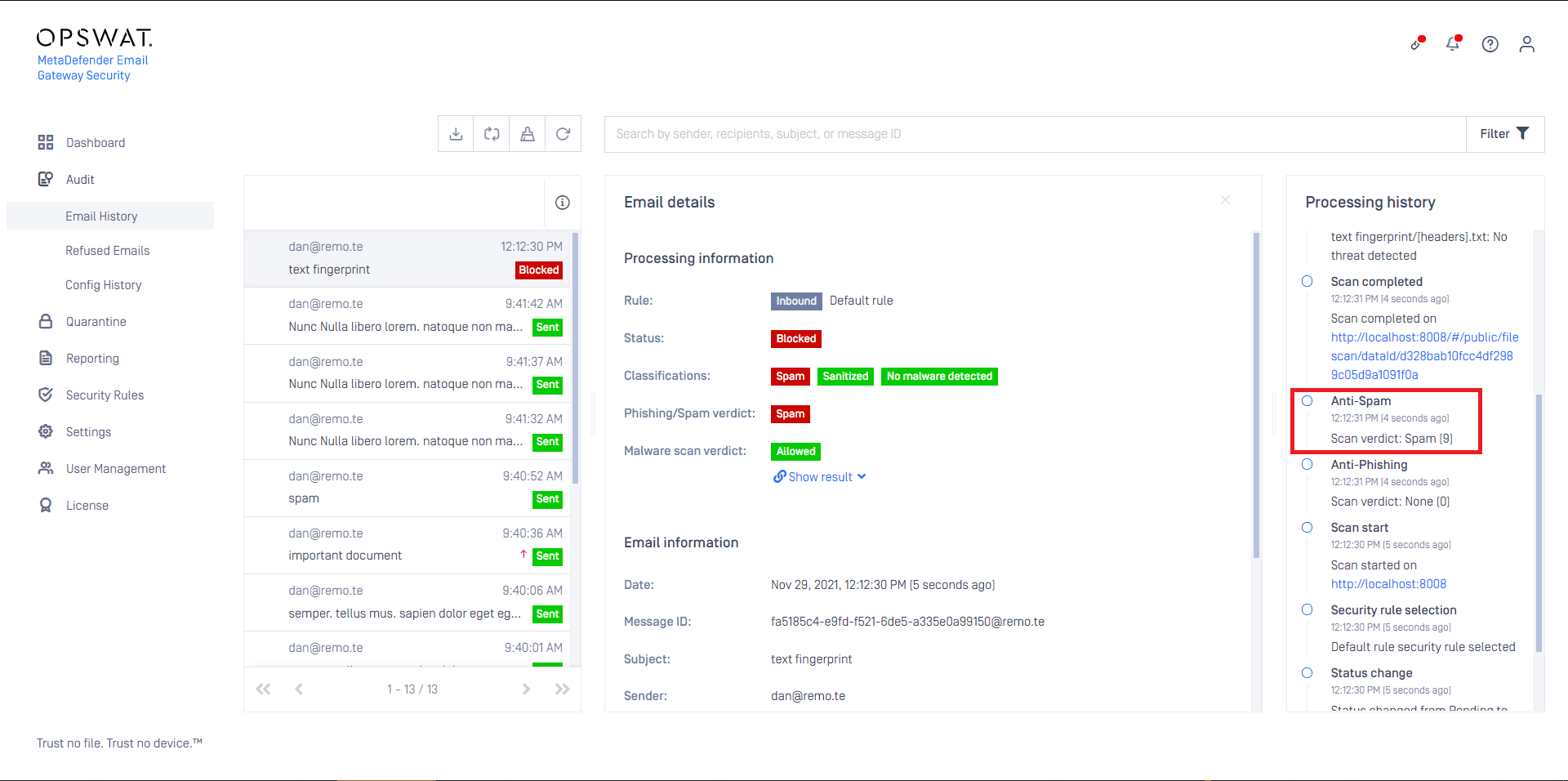
In the example below Email Gateway Security assigned the spam probability level 9 to the email.
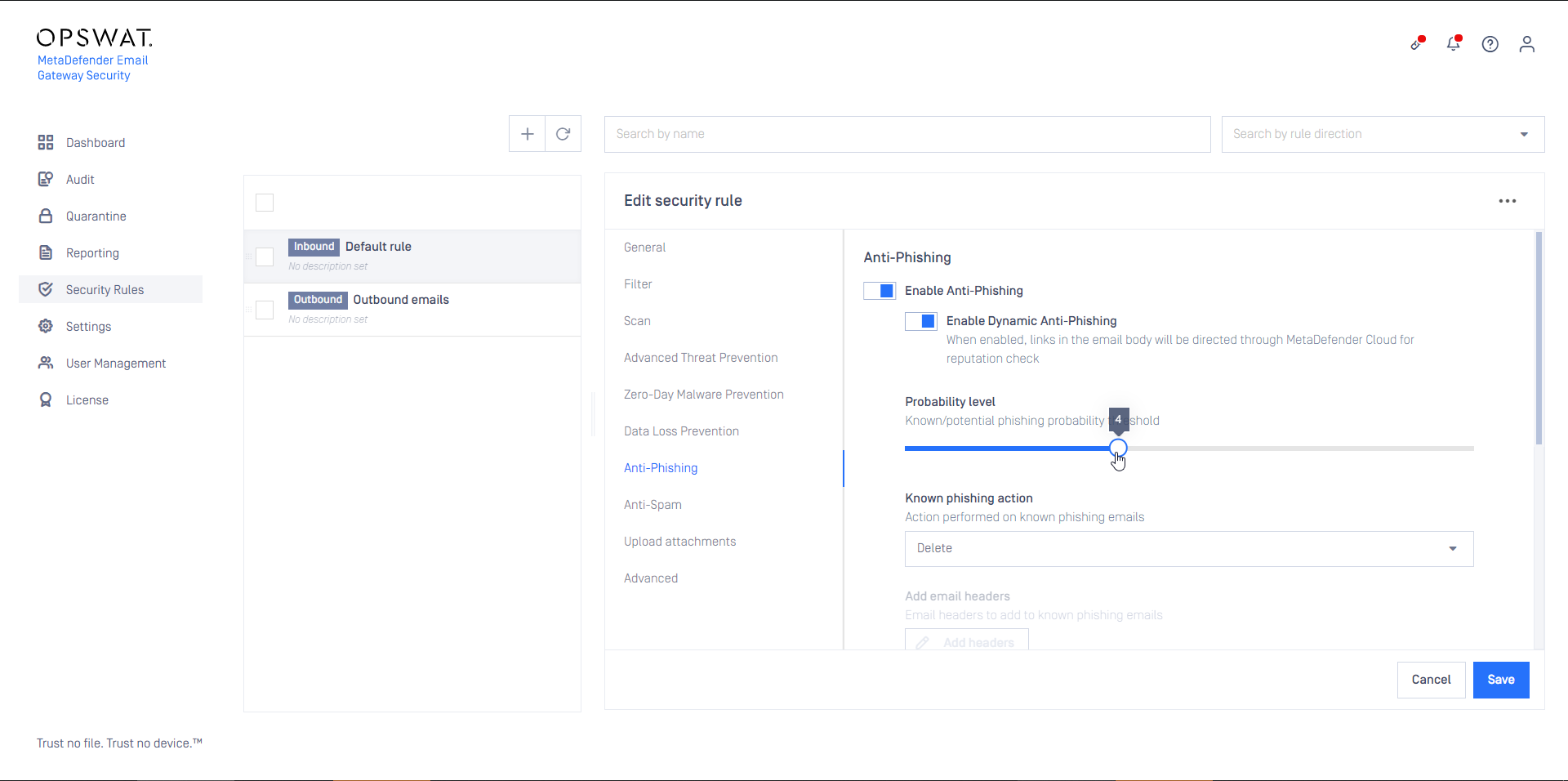
In the example below the Probability level is set to 4.
It means, that
- all email that’s probability level is higher or equal than 4, will be treated as known Phishing, while
- all email that’s probability level is lower than 4 will be treated as Possible phishing
- (all email that’s probability level is 0 will be treated as not phishing)
If the Probability level is set to 9, then only emails with probability level 9 will be treated as known Spam or Phishing. Emails with levels 1-8 will be treated as Possible spam or Possible phishing.
Actions for known or potential phishing and spam
Based on the probability level, Email Gateway Security can be configured to handle known and potential spam or phishing in different ways.
The following actions are available:
| Action | Description |
|---|---|
| Reject | Perform an IP reputation check and if turns out to be a (potential) spam or phishing sender, then reject the email on the SMTP level. The email will show up in Audit > Refused Emails. |
| Delete | Receive the email, perform an IP reputation and/or content check, and if turns out to be a (potential) spam or phishing, then delete it. The email will show up in Audit > Email History with some additional details as if it was rejected and with the appropriate classifications added (for details see Operating/Email History and Operating/Email classifications). |
| Quarantine | Receive the email, perform an IP reputation and/or content check, and if turns out to be a (potential) spam or phishing, then quarantine it (just like infected emails). The email will show up in Quarantine with the appropriate classifications added (for details see Operating/Quarantine and Operating/Email classifications). |
| Deliver | Receive the email, perform an IP reputation and/or content check, but even if it turns out to be a (potential) spam or phishing, deliver it (just like clean emails). The email will show up in Audit > Email History with the appropriate classifications added (for details see Operating/Email History and Operating/Email classifications). |
| Add headers | If the known or potential action is set to Deliver, then headers can be added to the email for each case. These headers can indicate for example to the receiving side that a (potential) phishing has just been received. |
Blocked notifications
It is possible to send the recipient a blocked notification when a spam and/or phishing email is put in quarantine. The options available for the notifications are identical as for Advanced Threat prevention (see above).
Disclaimers
It is supported to amend an email detected as known spam or - phishing or potential spam or - phishing with a disclaimer if the processed version of the email finally gets delivered. Such an email may get finally delivered if the action is set to Deliver; or the action is set to Quarantine and the email gets delivered after a Full rescan or an Anti-malware rescan. The idea behind this behavior is that this way recipients can be alerted about the potential risks in spam and phishing emails even after being delivered by a rescan.
Disclaimers won't be appended to the email when the email is released, forwarded or downloaded from the Quarantine.
For details see the Full rescan email and Anti-malware rescan email sections in Supported functions; and Disclaimers.
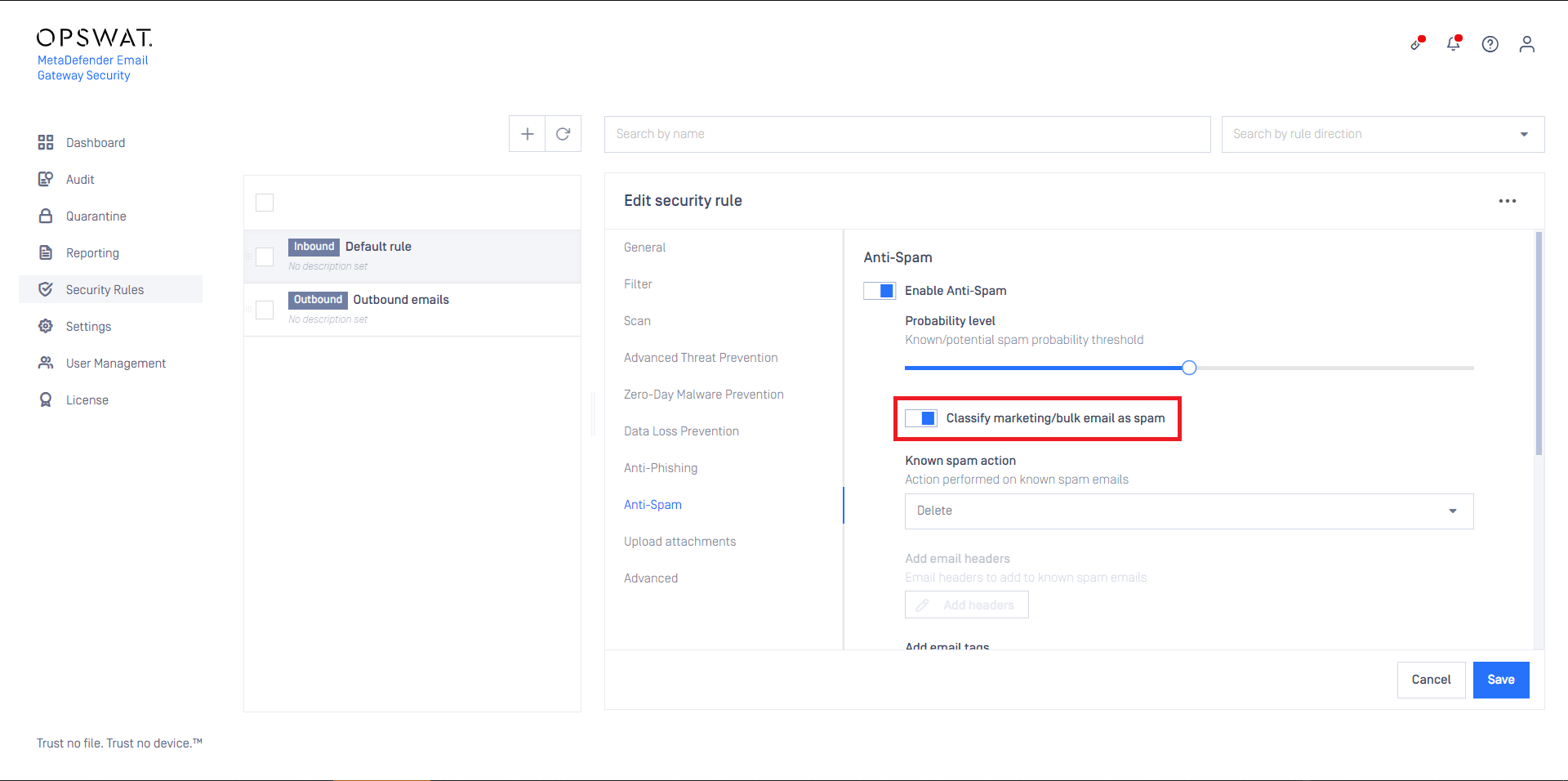
Anti-spam specific settings
Email Gateway Security’s ant-spam component can detect some kind of graymail, too. Enabling Classify marketing/bulk email as spam will instruct Email Gateway Security to treat email detected as marketing and bulk as spam and handle it according to the anti-spam settings.
Anti-phishing specific settings
SPF lookup
It is possible to enable/disable the Sender Policy Framework (SPF) verification as a part of the Anti-Phishing feature. For more information on SPF, see Sender Policy Framework.
SPF lookup will never be attempted if an email originates from an internal/private IP address, regardless if the option is enabled or not.
DKIM signature validation
DKIM signature validation can be enabled/disabled depending on preference and infrastructure.
If the mail flow includes any 3rd party software modifying the email content in any way before reaching MetaDefender Email Gateway Security, this might break the email's DKIM signature and produce a validation failure. In this case, simple omit the DKIM validation by disabling this option.
URL reputation lookup
With this option enabled Email Gateway Security checks the reputation of the URLs extracted from the email body. If any URL is found malicious then the email gets classified as Phishing and treated according to the settings for known phishing emails.
The URL reputation lookup uses the URL reputation services of MetaDefender Cloud. An appropriate MetaDefender Cloud subscription is needed for this capability to work.
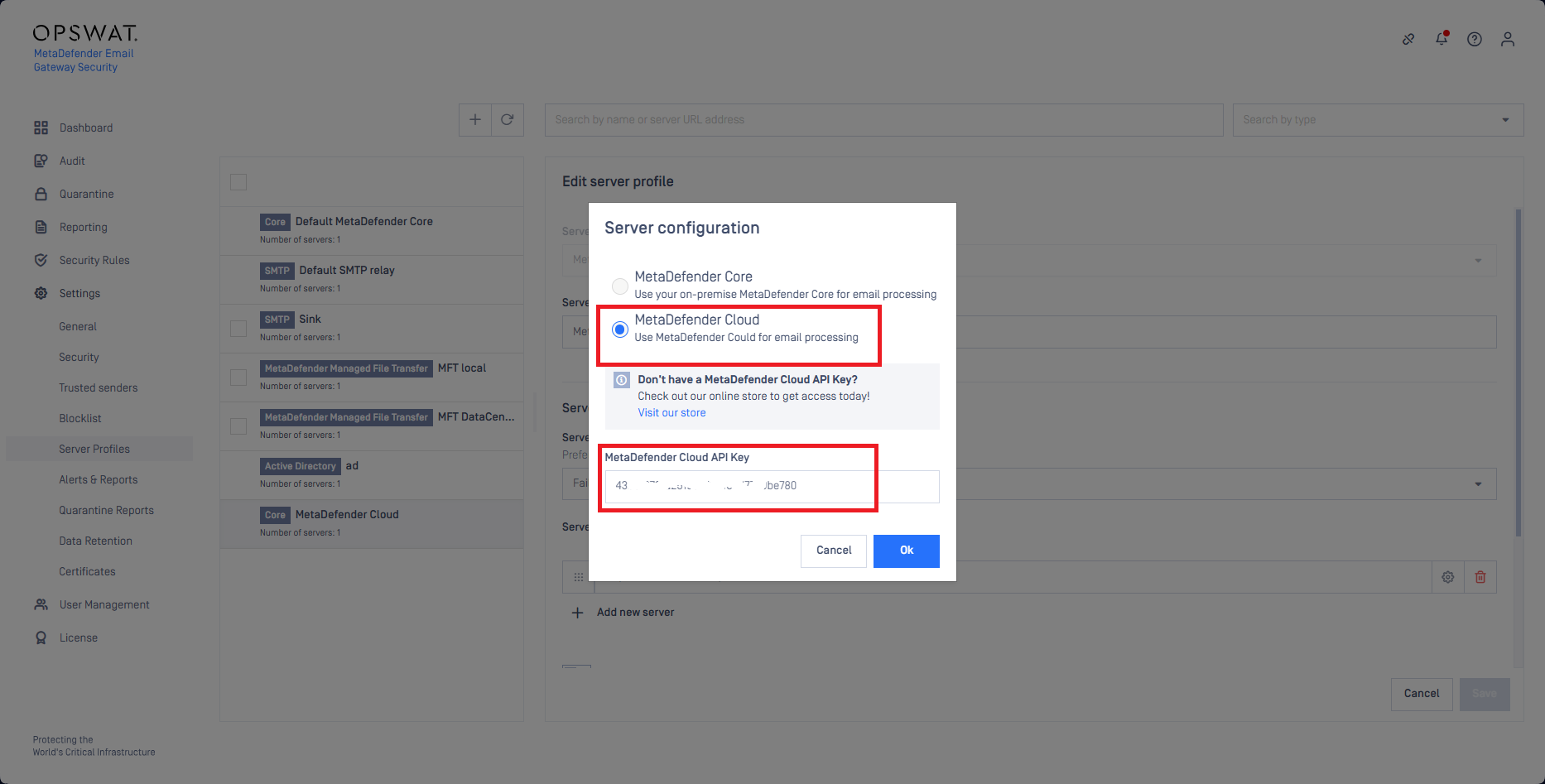
The MetaDefender Cloud subscription is connected to the URL reputation lookup capability through a MetaDefender Core type server profile that has one of its servers configured as MetaDefender Cloud.
The MetaDefender Cloud subscription is connected to the URL reputation lookup capability through a MetaDefender Core type server profile.
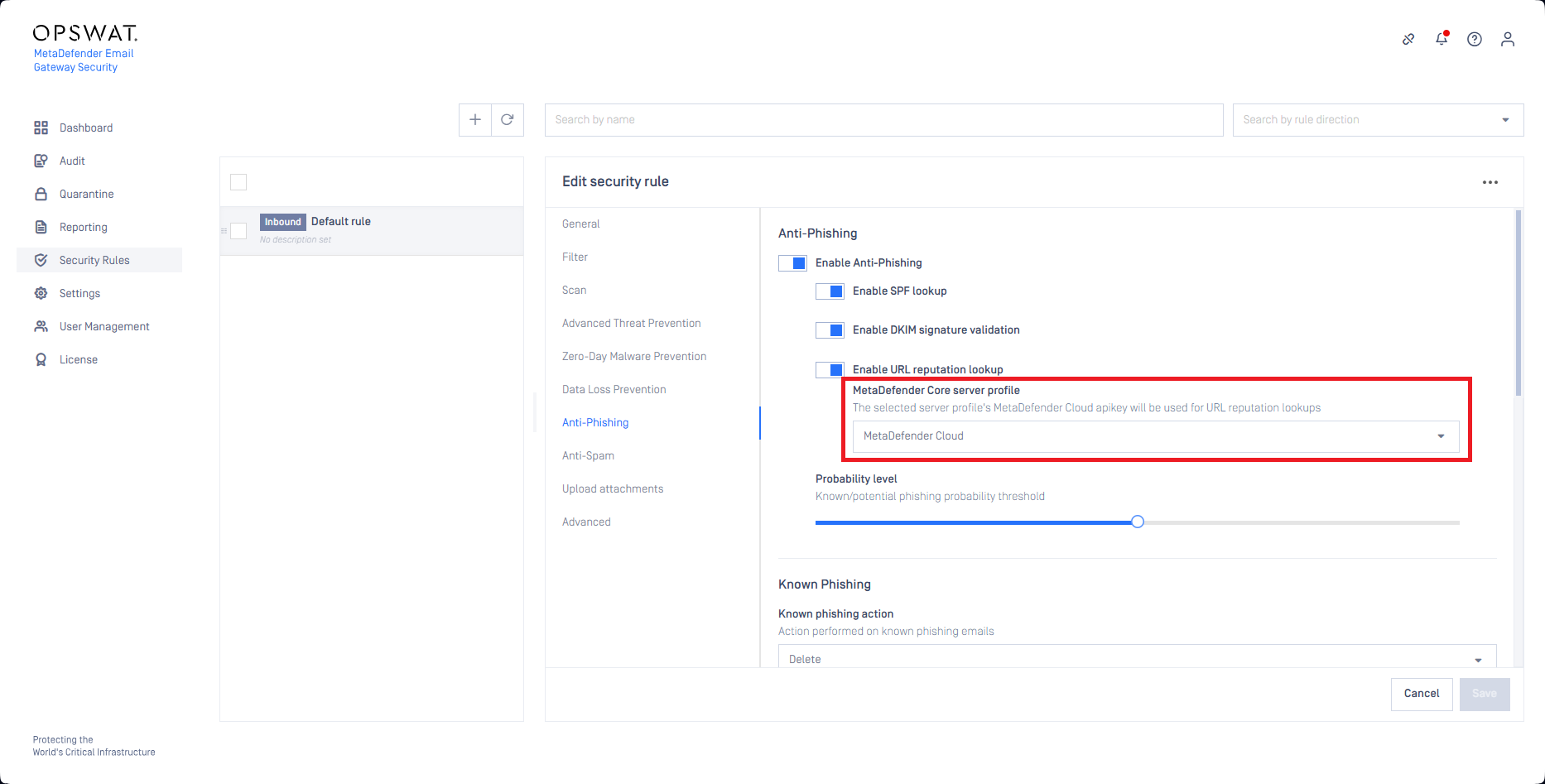
This server profile has to have its type as MetaDefender Core. At least one of its servers must be MetaDefender Cloud.
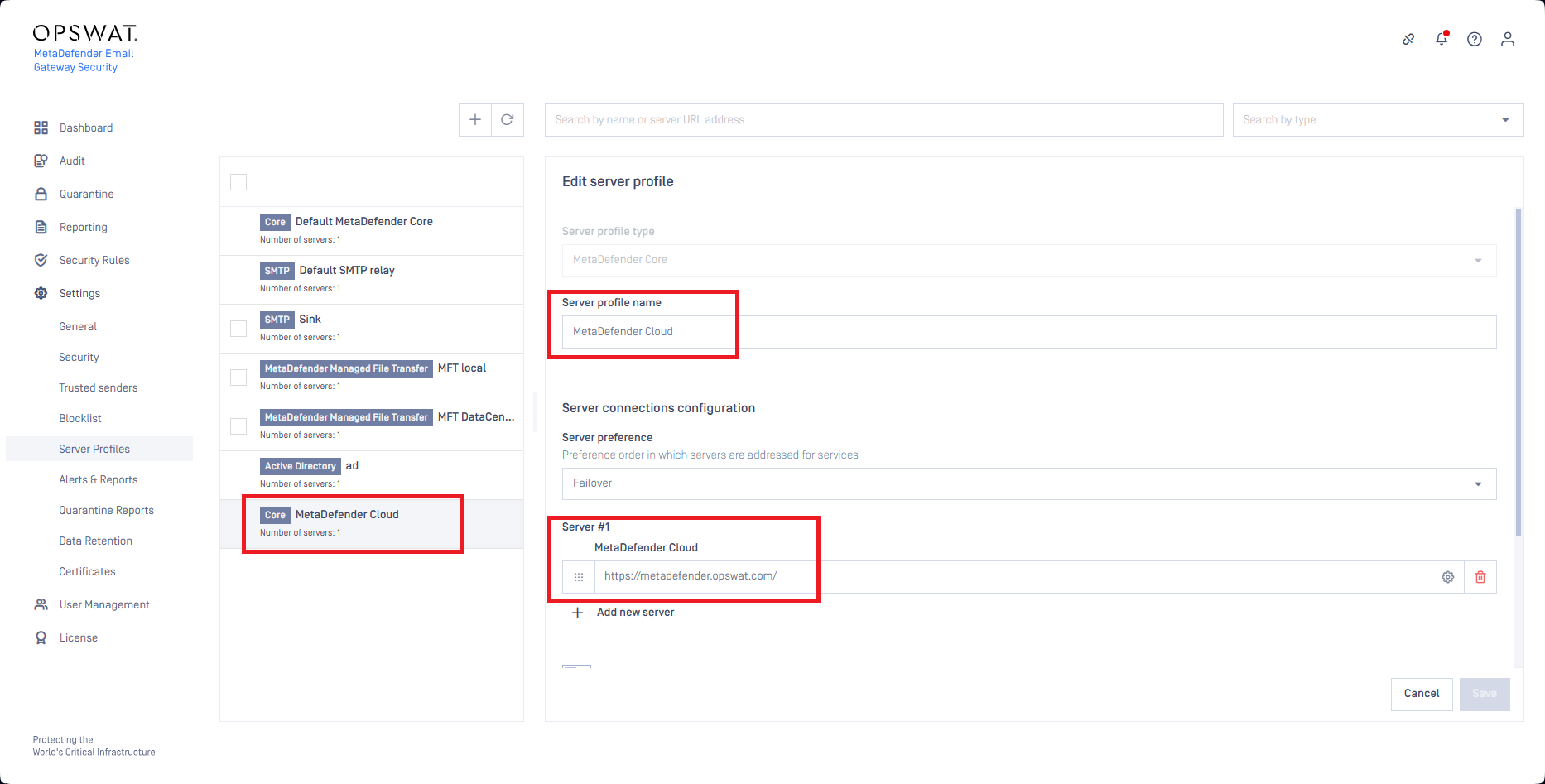
At least one of the servers of this server profile must be MetaDefender Cloud.
Authenticated Received Chain (ARC)
In most of the cases Email Gateway Security acts as an intermediate email processing server between the original sender and the intended recipient. As Email Gateway Security is not the original sender the SPF check will fail on the recipients side. Email Gateway Security usually modifies emails (adds custom headers, and with Deep CDR and Proactive DLP it often modifies the email bodies and attachments) and as a result the DKIM verification will fail at the recipient.
Authenticated Received Chain is an email authentication system designed to allow an intermediate mail server to sign an email's original SPF and DKIM authentication results. This allows a receiving service to validate an email when the email's SPF and DKIM records are rendered invalid by an intermediate server's processing.
With ARC, an intermediate processing server can digitally sign the SPF/DKIM results of the preceding server and its own modifications to the email with DKIM-like signatures.
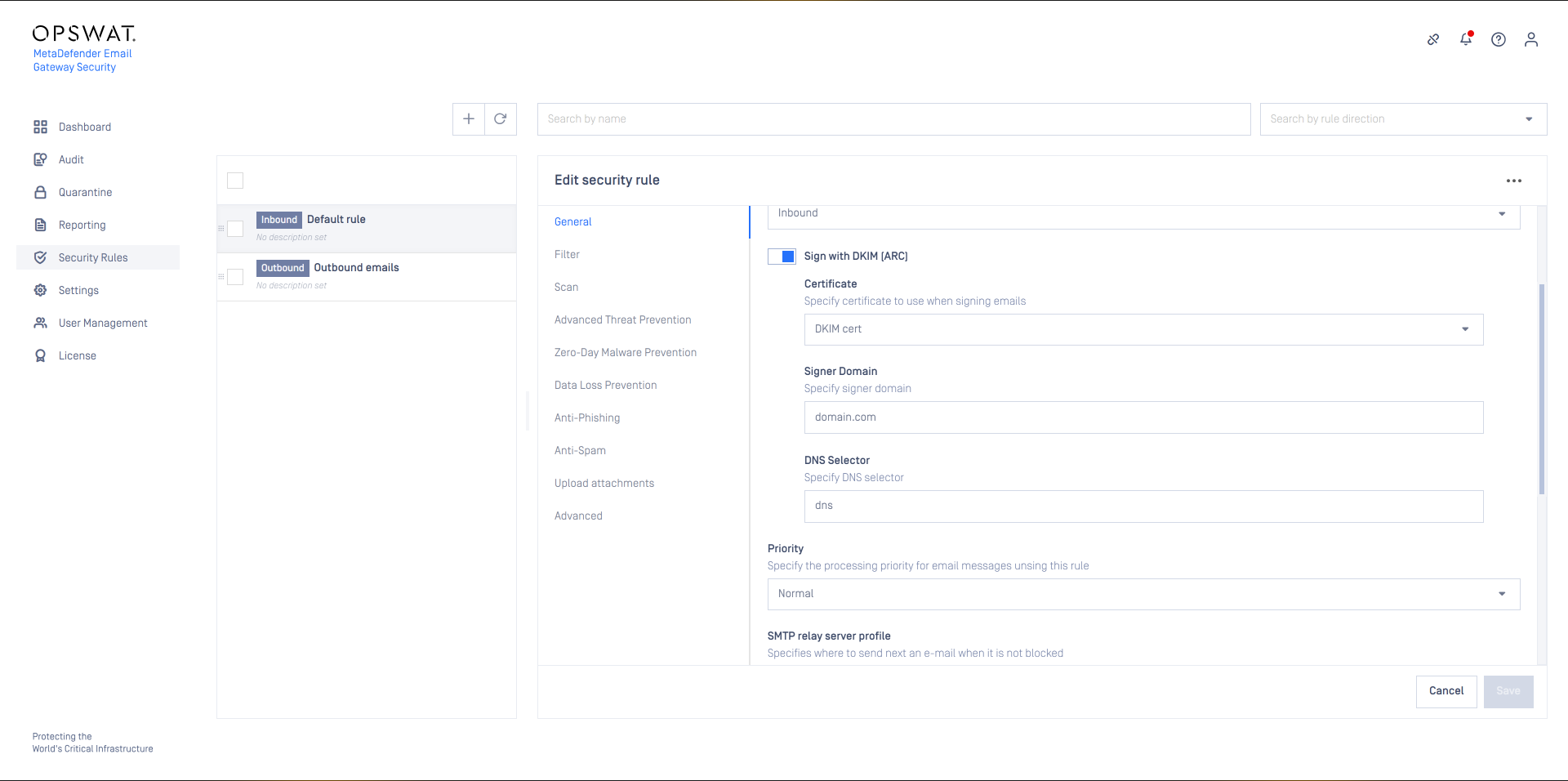
To enable ARC, go to Security Rules > rule / General and enable the Sign with DKIM (ARC) option.
As a prerequisite DKIM certificates need to be configured under Settings > Security > Certificates.
- Certificate: Certificate in Settings > Security > Certificates to be used to create the ARC signatures.
- Signer Domain: The domain for which to create the DKIM-like ARC signatures. The next email processing server will look up the public keys in the DNS records of this domain to verify Email Gateway Security's ARC signatures.
- DNS Selector: Specifies the DNS location of the public key. Receiving servers use this selector to find the public key.
Upload attachments
Prerequisites
Configuring the Upload attachments capability requires some technical understanding of MetaDefender Managed File Transfer.
For details about MetaDefender Managed File Transfer see https://onlinehelp.opswat.com/mdmft/.
For details about integrating Email Gateway Security and Managed File Transfer see Integrations/Integration with MetaDefender Managed File Transfer.
The Upload attachments capability requires a MetaDefender Managed File Transfer server profile to be configured and set for the MetaDefender Managed File Transfer server profile value. For details see Configuration/Server profiles.
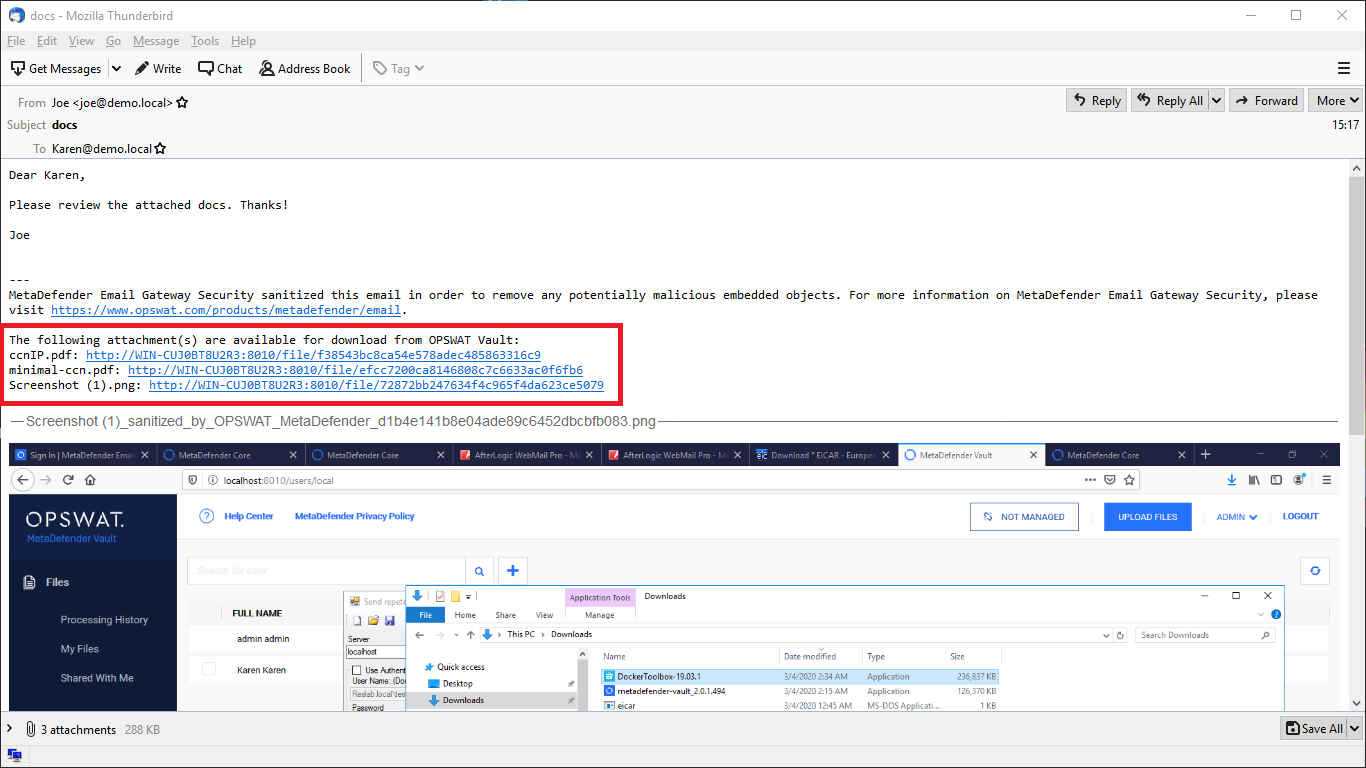
Attachment notice
Setting the Attachment notice a custom notification text can be configured to be appended to emails notifying recipients about where they can access their files in MetaDefender Managed File Transfer.
The Attachment notice works the same way as other disclaimers do. For details see Configuration/Disclaimers.
You should not remove %[]mft_list[]% from the notification texts as it would lead to missing URLs. For details see Configuration/Disclaimers.
Upload blocked attachments
By selecting this option, the original copy of every attachment which was blocked will be uploaded to MetaDefender Managed File Transfer.
Upload sanitized attachments
By selecting this option, the sanitized copy of every attachment which was sanitized will be uploaded to MetaDefender Managed File Transfer.
To upload the original copy of the sanitized attachments see Configuration/Policy.
Upload partially sanitized attachments
By selecting this option, the original copy of every attachment which was partially sanitized will be uploaded to MetaDefender Managed File Transfer.
This requires the 'Distinguish partial archive sanitization result' option checked in the MetaDefender Core rule used to scan content with. See MetaDefender Core > 3.6.2. Workflow template configuration for more information.
Upload original of sanitized attachments
By selecting this option, the original copy of every attachment which was sanitized will be uploaded to MetaDefender Managed File Transfer.
If both Upload original of sanitized attachments and Upload attachments that failed sanitization are enabled –and the sanitization fails– then the original file will be uploaded only once.
Upload attachments that failed sanitization
By selecting this option every attachment where the sanitization failed will be uploaded to MetaDefender Managed File Transfer.
If both Upload original of sanitized attachments and Upload attachments that failed sanitization are enabled –and the sanitization fails– then the original file will be uploaded only once.
Upload bypassed attachments
By selecting this option every attachment that was bypassed (for details see Operating/Bypassing) by Email Gateway Security will be uploaded to MetaDefender Managed File Transfer.
Upload allowed attachments
By selecting this option every attachment which was allowed will be uploaded to MetaDefender Managed File Transfer.
Please note that if an attachment is allowed but gets sanitized then it won't be uploaded if only the Upload allowed attachments option is set.
If you want to upload these kind of attachments you should have Upload original of sanitized attachments enabled.
Options
Skip supervisor approval
Enable this option to skip supervisor approval of attachments that were uploaded to MetaDefender Managed File Transfer (MFT). Supervisor approval adds an extra layer of security by requiring a supervisor or designated authority to approve file availability file transfers or data sharing activities in MFT before they proceed.
Skip supervision capability is available in MetaDefender Managed File Transfer 3.9.1 and newer.
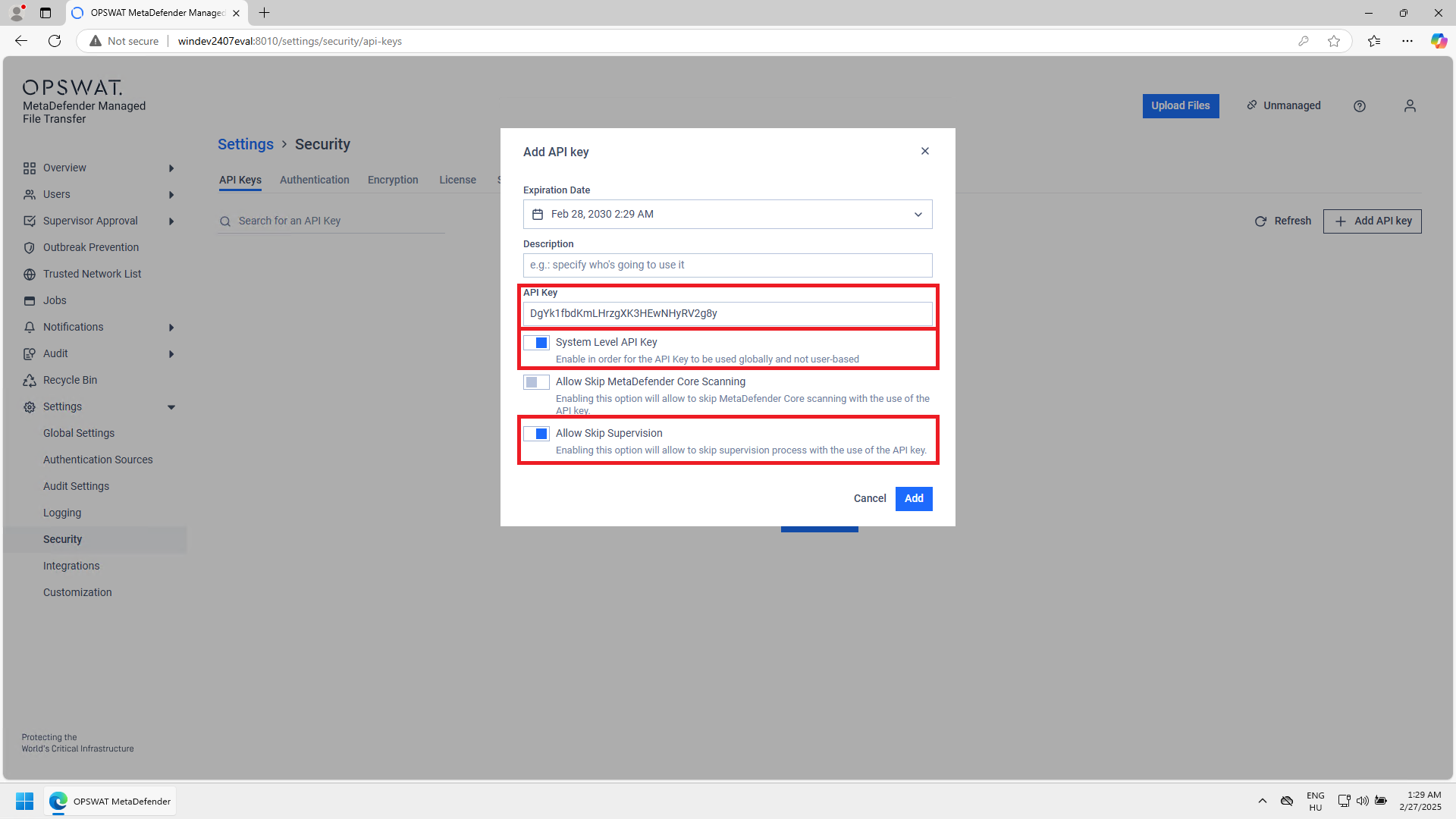
For this functionality to work, Email Gateway Security must be integrated to MFT using a System Level API Key that has set Allow Skip Supervision enabled.
This is how such an API key is defined on the MFT side (for details see For details see https://www.opswat.com/docs/mdmft/end-user-guide/supervisor-approval and https://www.opswat.com/docs/mdmft/configuration/api-keys):
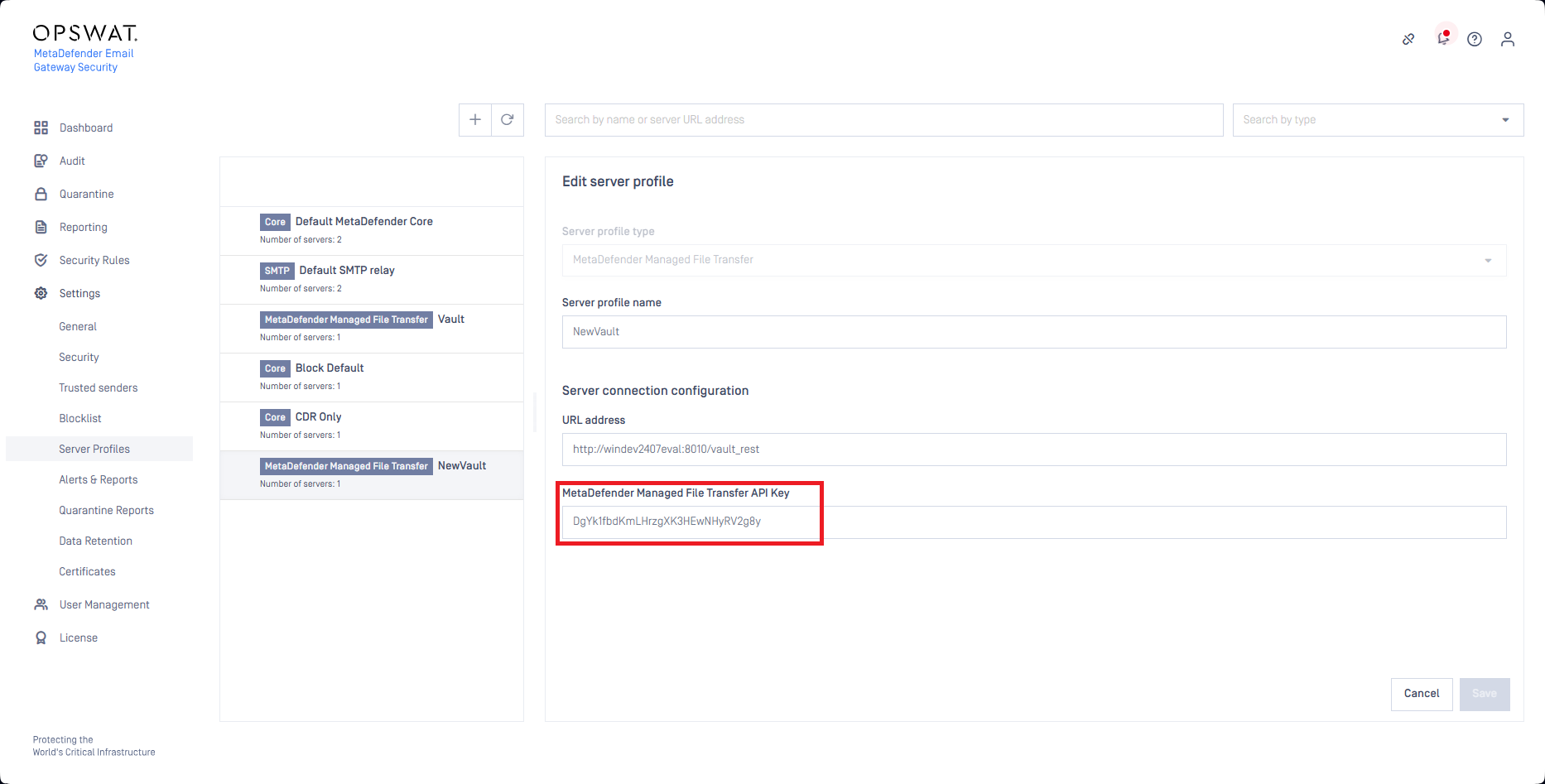
This is how such an API key is used with a MetaDefender Managed File Transfer type server profile (for details see Server profiles):
Remove uploaded attachments from email
By enabling this option every attachment which was successfully uploaded to MetaDefender Managed File Transfer will be removed from the email. If uploading an attachment fails the removal will be skipped.
Blocked files will be removed regardless this setting if the action for blocked contents is to Delete blocked contents.
Include scan result
By enabling this option, Email Gateway Security will upload the scan results to Managed File Transfer besides the attachment as metadata. As a result Managed File Transfer will know the verdict of the scan and can make the file available immediately.
Create subfolders in MetaDefender Managed File Transfer
When this option is enabled, a subdirectory is created for each attachment category (e.g. password protected attachments, sanitized attachments, original copy of sanitized attachments, etc.) in MetaDefender Managed File Transfer.
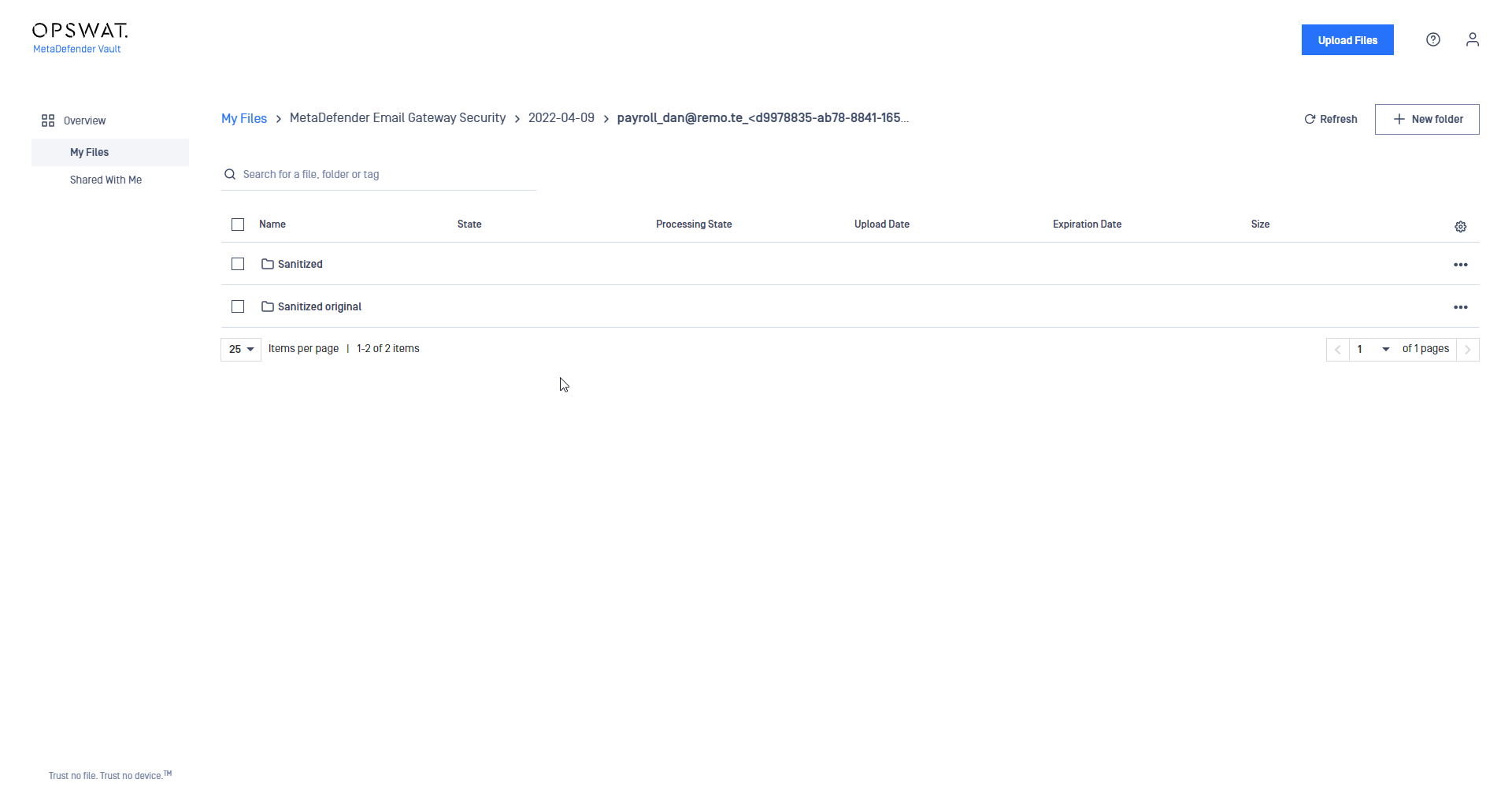
The attachment categories are the same as the upload options under the Upload attachments tab in the security rule.
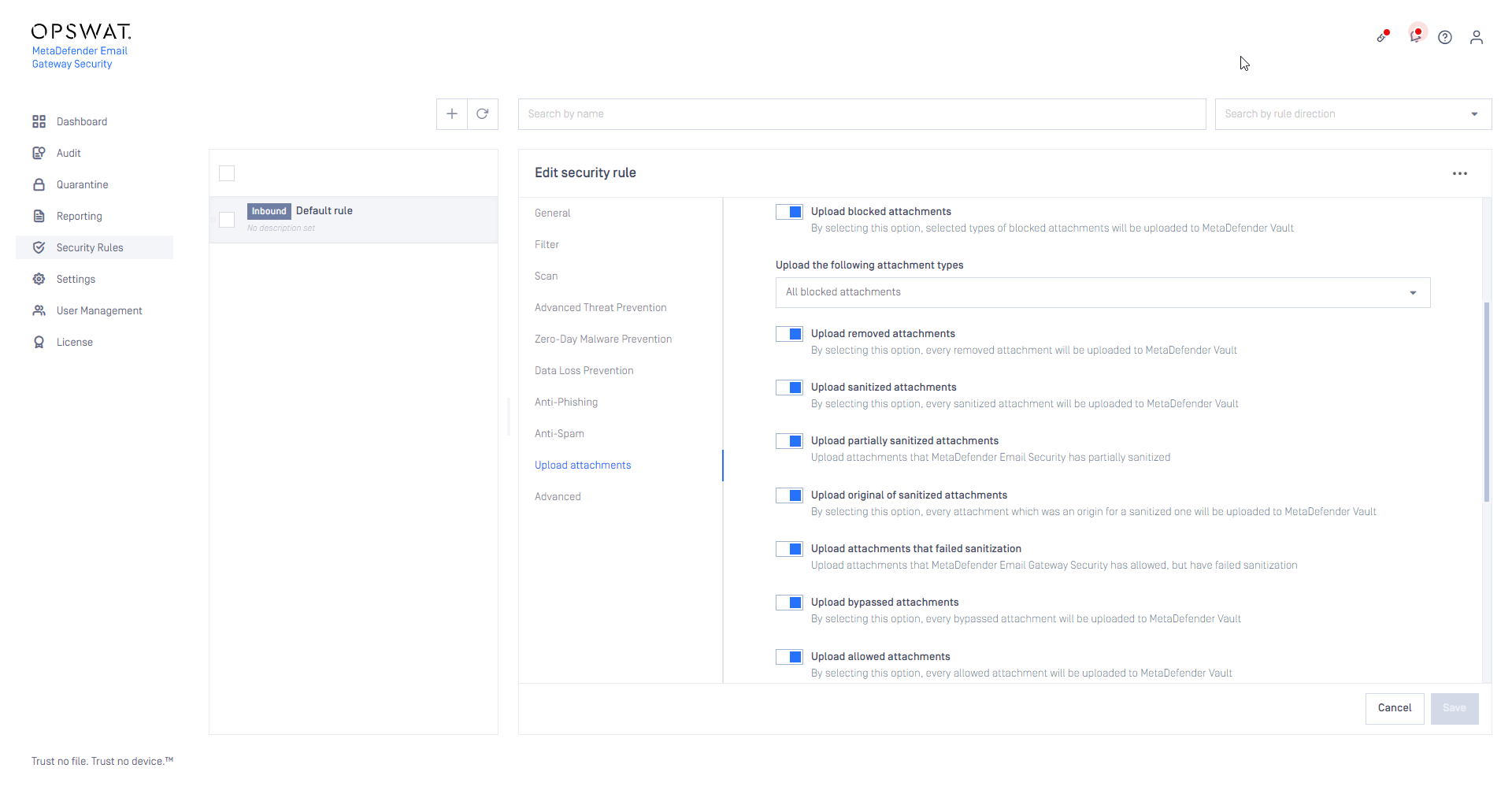
Account impersonation options
Based on the email addresses, the files will be uploaded to the recipients' own MFT accounts (when the account exists on the MetaDefender Managed File Transfer at all). This feature requires appropriate permissions (impersonation) on MetaDefender Managed File Transfer.
The account on MetaDefender Managed File Transfer that is assigned to the API key specified in the MetaDefender Managed File Transfer server profile (see Configuration/Server profiles) set for the Email Gateway Security rule that matched the email.
When there are multiple recipient email addresses for an email that do not have the corresponding account on MetaDefender Managed File Transfer, or Always upload to default account is set; then the files will be uploaded to the default account for each email address for each email.
A separate subdirectory is created for subsequent email addresses named as counter values (1, 2, ...).
A temporary account created on MetaDefender Managed File Transfer. These accounts can be accessed using a PIN.
The PIN length and the account expiry window can be configured in the Upload attachments tab or the security rule.
The PIN can be made available to the recipients using the mft_name or mft_user disclaimer variables. For details see Disclaimer variables.
This PIN then needs to be used on the MetaDefender Managed File Transfer login page for Guest accounts. When the upload might end up in creating a guest account, then the recipients' attention needs to be called to this fact and the way how they can authenticate on MetaDefender Managed File Transfer.
For each email and for each recipient email addresses a dedicated guest account will be created on MetaDefender Managed File Transfer.
This might result a huge number of guest accounts created on MetaDefender Managed File Transfer.
| Option | Details |
|---|---|
| Impersonate when possible, otherwise upload to default account | For accounts existing on the MetaDefender Managed File Transfer with the recipients' email addresses, the attachments will be uploaded to the appropriate MetaDefender Managed File Transfer accounts. In other cases the attachments will be uploaded to the default account. |
| Impersonate when possible, otherwise upload to guest account | For accounts existing on the MetaDefender Managed File Transfer with the recipients' email addresses, the attachments will be uploaded to the appropriate MetaDefender Managed File Transfer accounts. In other cases the attachments will be uploaded to a dedicated guest account for each email address. |
| Impersonate when possible, otherwise skip upload | For accounts existing on the MetaDefender Managed File Transfer with the recipients' email addresses, the attachments will be uploaded to the appropriate MetaDefender Managed File Transfer accounts. In other cases the attachments won't be uploaded, but delivered with the email normally. |
| Always upload to guest account | Attachments will be uploaded to a separate guest account for each email address. |
| Always upload to default account | Attachments will be uploaded to the default account. |
Impersonation works for the email address one@local but the address two@local will fall back to the default account admin.
Advanced
Signed email settings
These settings allow you to override the default behavior when handling signed and/or encrypted emails (S/MIME, PGP). By default, Email Gateway Security will not modify (add disclaimers, sanitize etc.) signed email to ensure that the email signature remains intact. By disabling the option Do not modify S/MIME and PGP signed emails, any signed emails will be modified and potentially render the signature invalid.
Additional recipients
This feature allows you to add additional recipients to every email processed by this security rule. Any recipients added in the list will receive a BCC copy of all emails processed.
SMTP sender or recipient rewriting
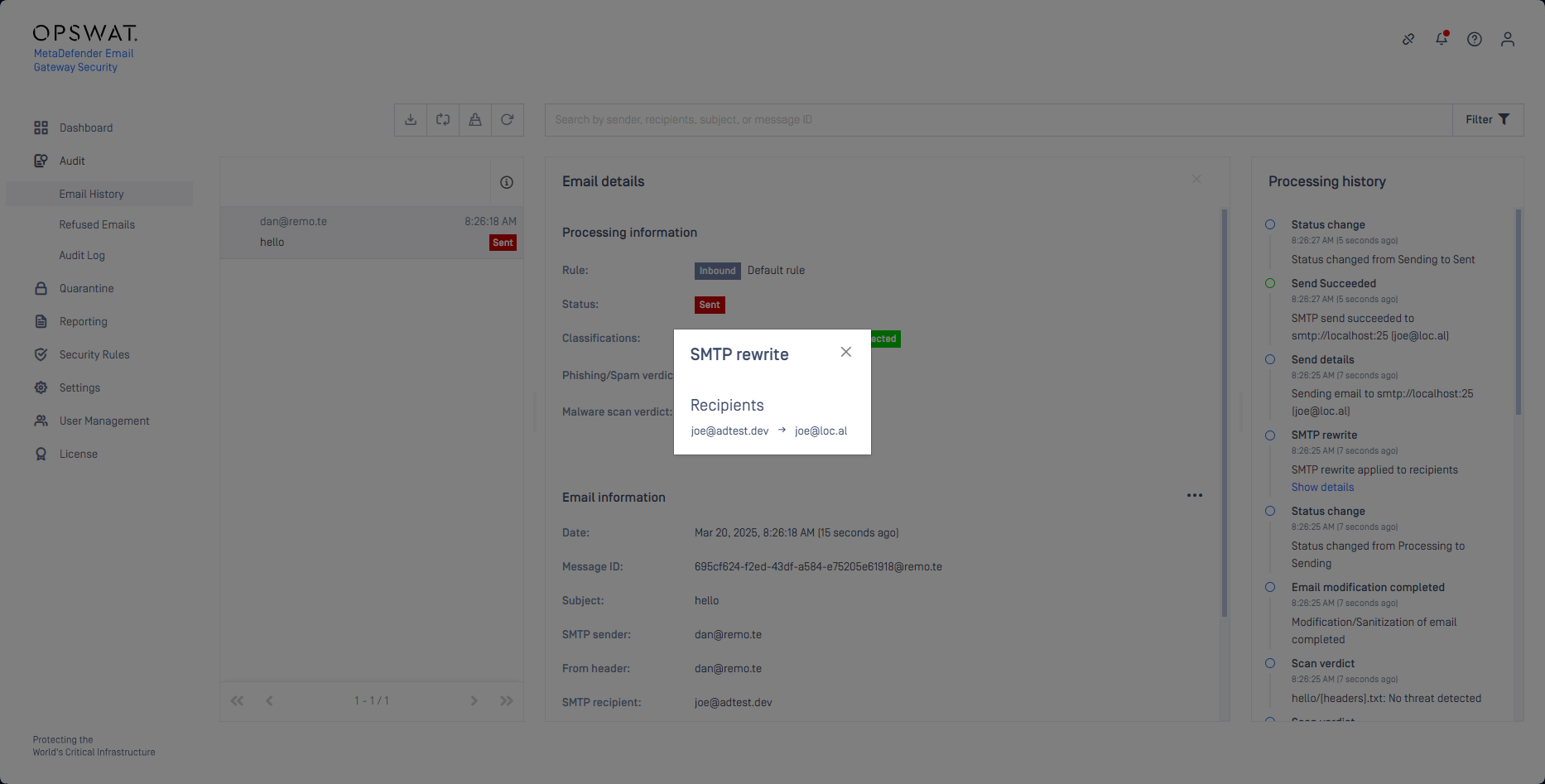
With this configuration it is supported to replace the domain part of the email addresses in the MAIL FROM and/or the RCPT TO SMTP commands to the configured value(s) during the SMTP submission to the SMTP relay configured for the rule.
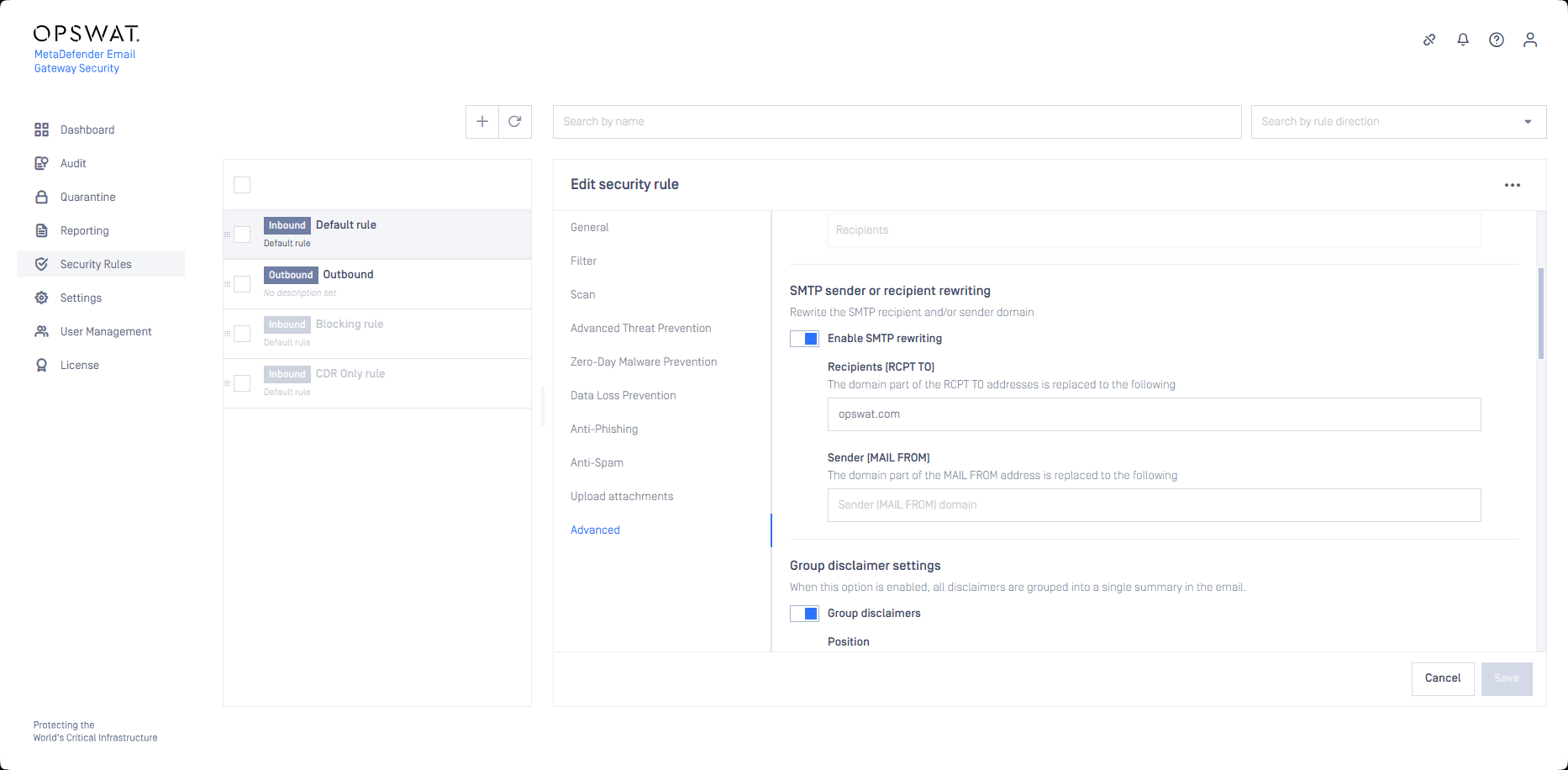
The From, To and Cc email headers are kept unchanged. This means that the final recipient will see the original values of these headers.
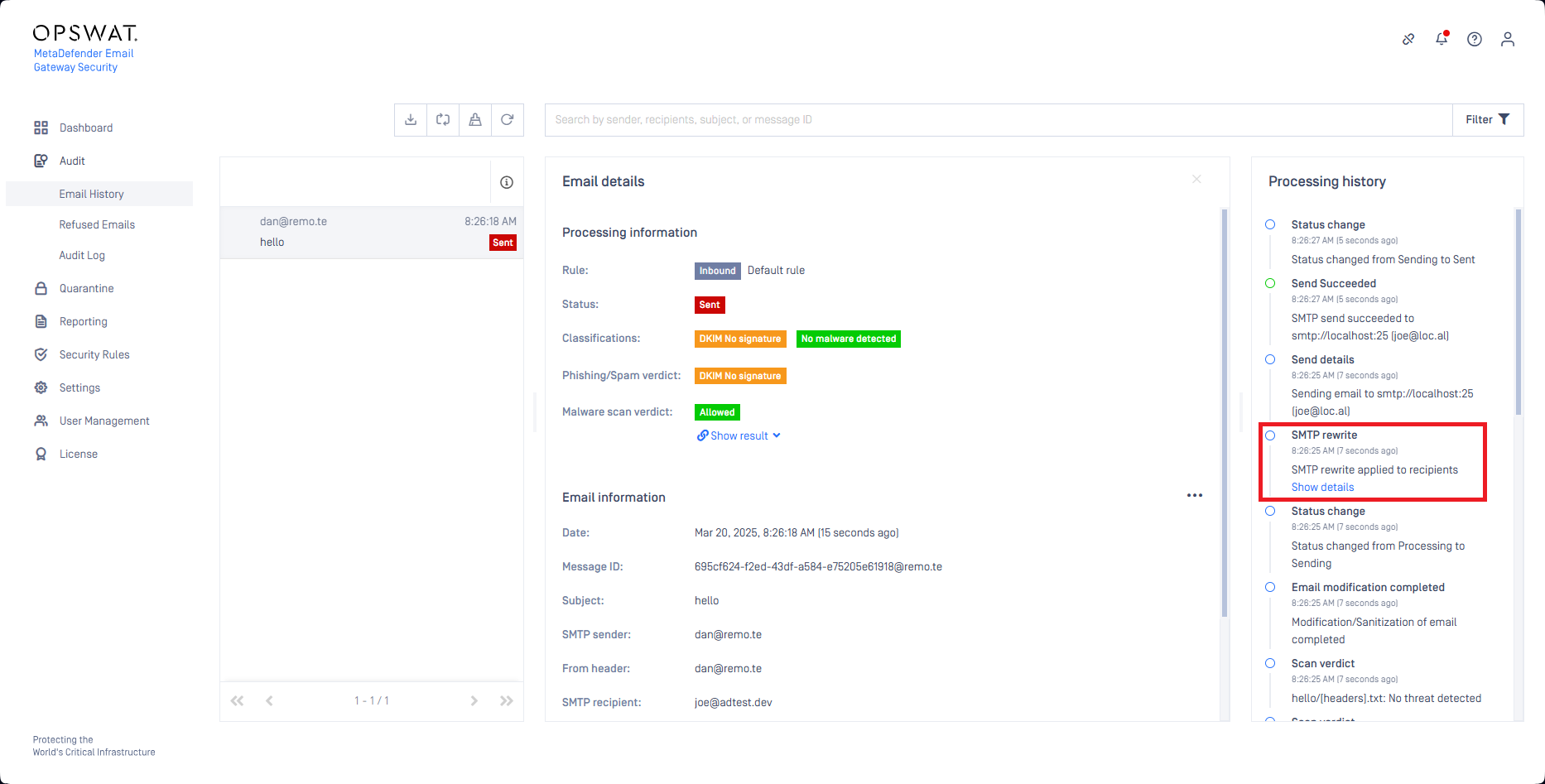
SMTP rewriting events are logged to the product log on INFO level.
Also, the Processing history of the Email details show an entry for the SMTP rewriting. For details see Email details.
Group disclaimer settings
This options allows grouping of any disclaimers into a section (above or below email body content). This provides a less intrusive way of displaying information in multiple disclaimers for the recipient. An additional footer disclaimer can also be added to each email processed by the security rule.
Override settings
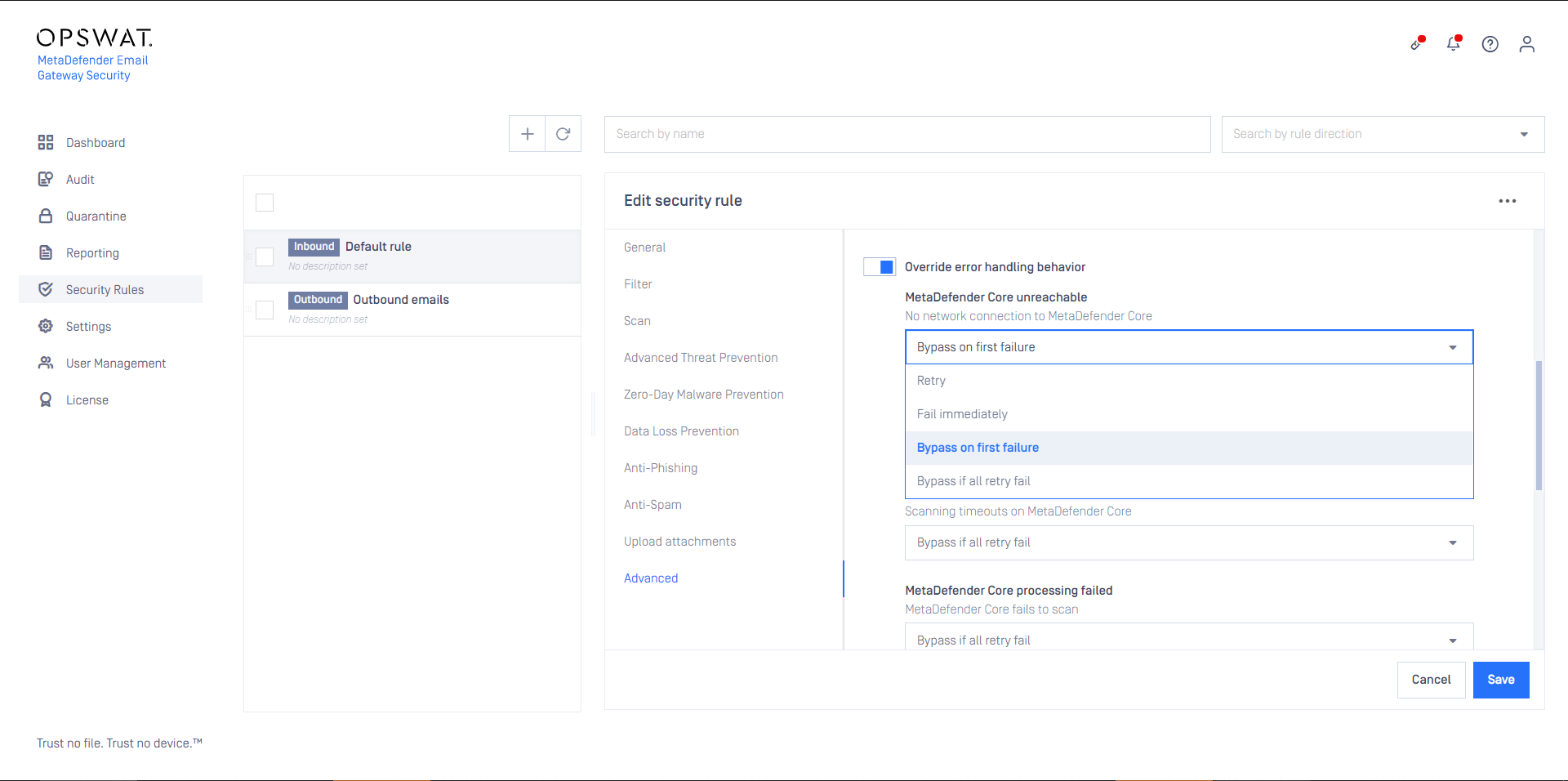
The override settings policy define certain exceptions from the default behavior for SMTP relays & MetaDefender Core scanning.
Email Gateway Security can be configured to retry to process emails. If an option is set to Retry, Bypass if all retry fail or Quarantine if all retry fail, then the retry mechanism under Settings > General / Email is applied.
For details see Configuration/Settings.
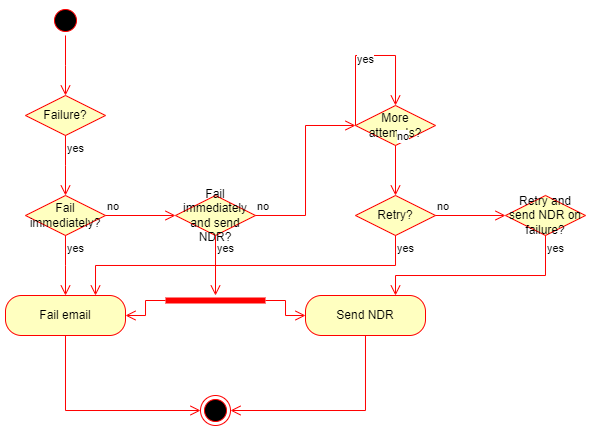
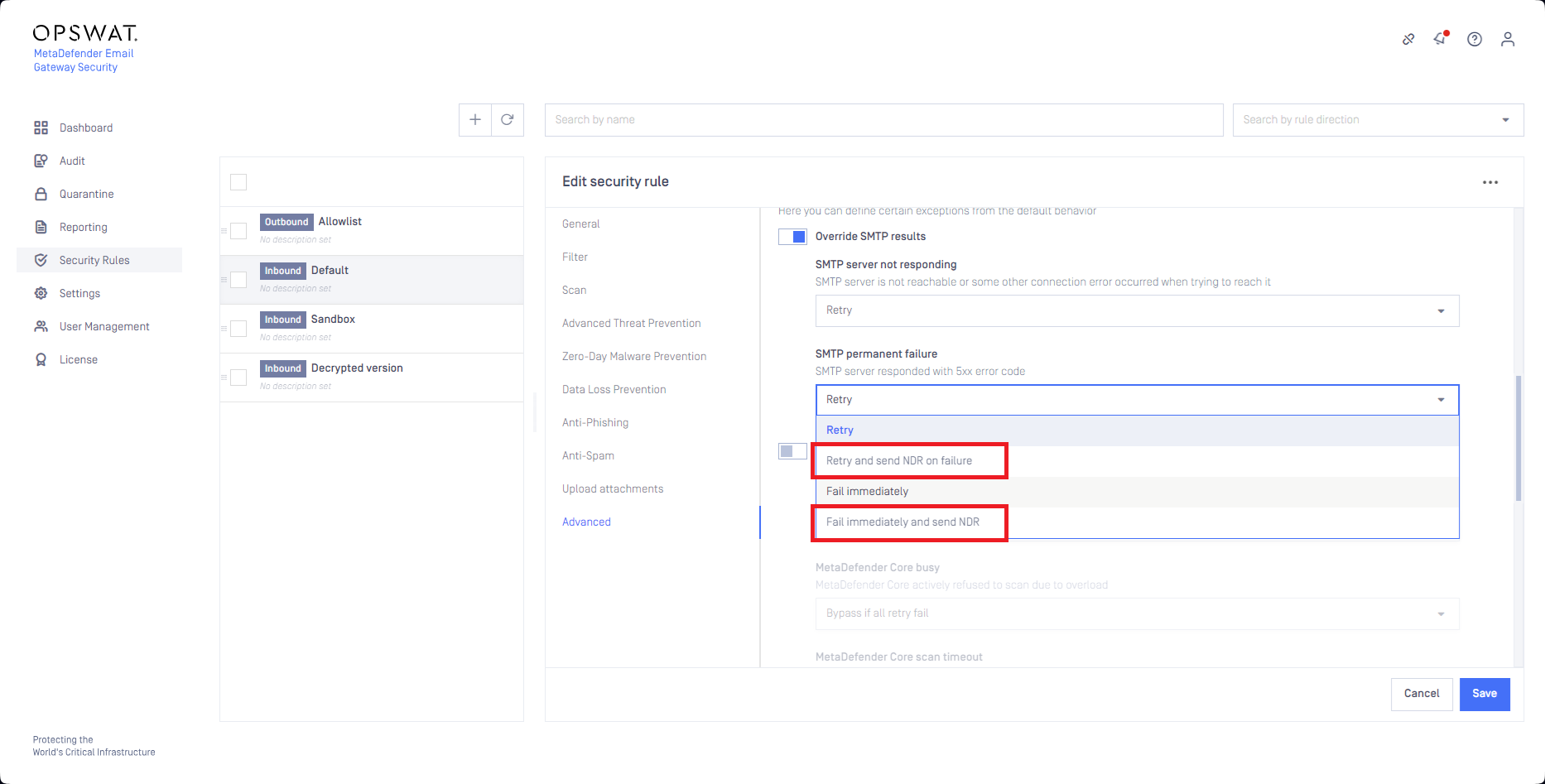
The decision tree for the retry mechanism under Override SMTP results:
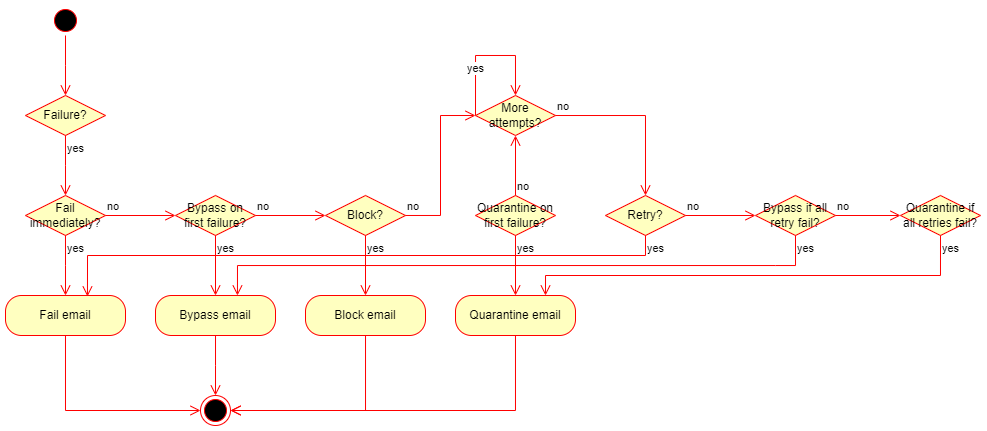
The decision tree for the retry mechanism under Override error handling behavior:
If Bypass on first failure or Bypass if all retry fail is configured for certain settings, and the email gets bypassed finally, then the original, potentially harmful email is delivered.
The recipient may be notified about the fact of bypassing. To do so set the Bypass email disclaimer. For details see Configuration/Disclaimers.
When Retry and send NDR on failure or Fail immediately and send NDR is configured for Override SMTP results / SMTP permanent failure and a non-delivery report email (NDR) is sent finally, there is a risk that Email Gateway Security will become the sender of backscatters or will be abused for reverse NDR attacks (when attackers intentionally cause huge amounts of backscatters to the victim to overload the victim's infrastructure). Victims of backscatters and reverse NDR attacks may have the sender server's IP listed by blocklisting services.
Anti-Spam processing failed
Email Gateway Security has a special option in case when the Anti-Spam processing fails. Setting the option to Ignore the anti-spam result is ignored and the email is processed as if the anti-spam check would have found the email clean.

