Title
Create new category
Edit page index title
Edit category
Edit link
Configure EAP-TLS for Cloud RADIUS Authentication
Introduction
This document describes how to set up Windows Group Policy to allow domain machines to automatically perform 802.1x EAP-TLS (certificate authentication) against OPSWAT's cloud-based RADIUS server.
Configuration EAP-TLS for NAC Cloud
Active Directory Certificate Services
- Using the Server Manager dashboard, navigate to Add Roles and Features:
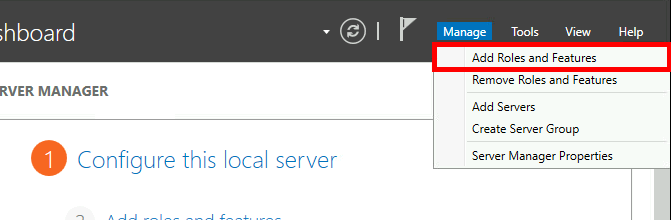
- Click Next
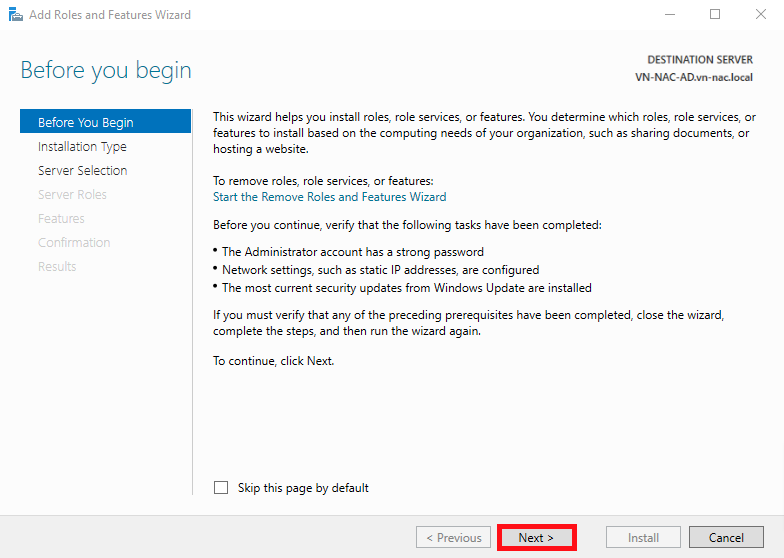
- Select Role-based or feature-based installation On the Installation Type menu then click Next
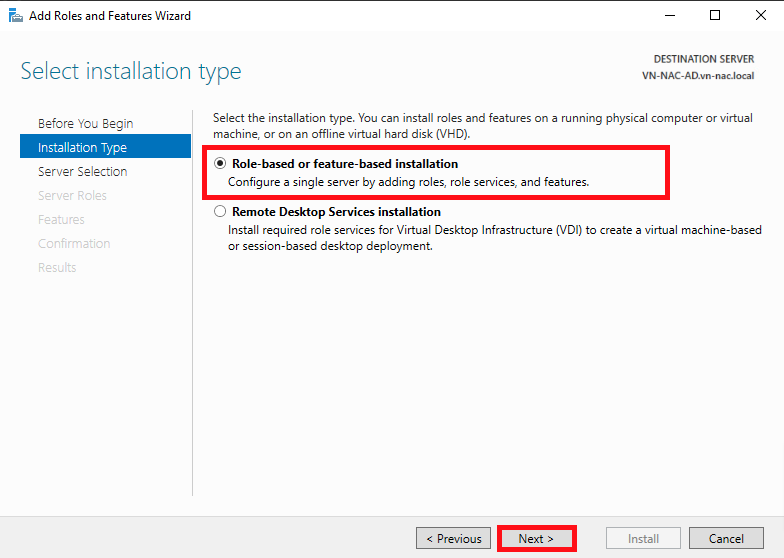
- Select your AD CS server and click Next
- Check the Active Directory Certificate Services box and click Next
- Click Next on the Features menu
- Read the Active Directory Certificate Services description if you want, then click Next
- Check the Certificate Authority box and click Next
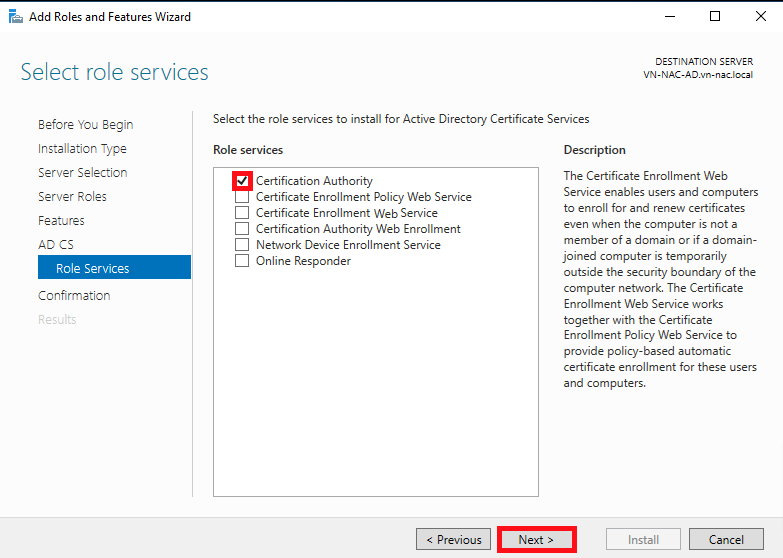
- Check the Restart destination server box to allow it to restart if needed, then click Install
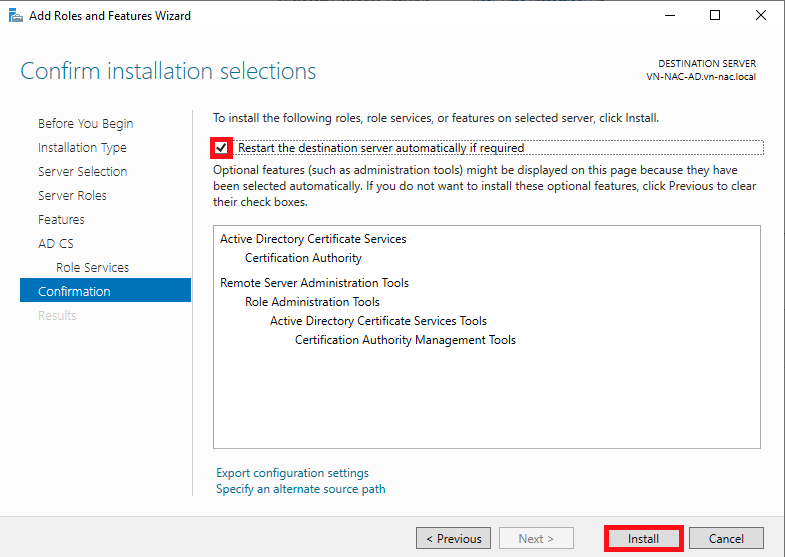
- Open the Server Manager dashboard and navigate to the Post-deployment Configuration
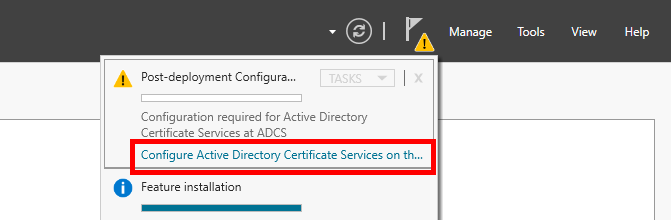
Change Default credentials if you want, then click Next
Select Certificate Authority role and click Next to continue
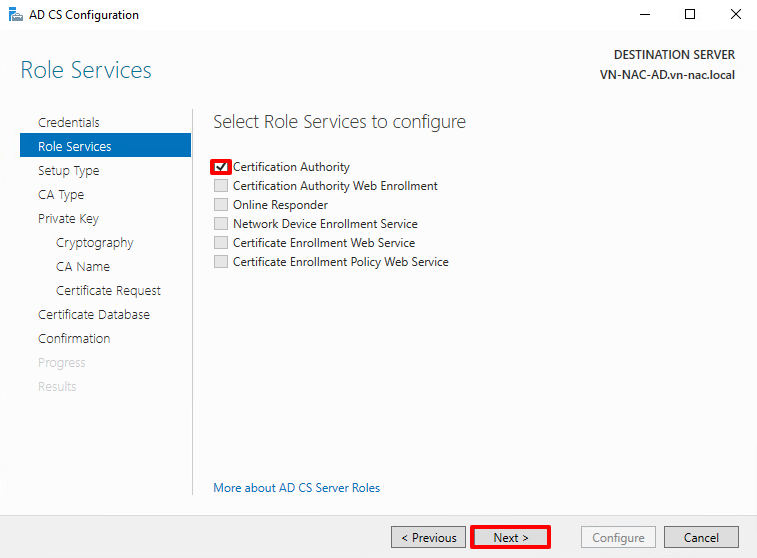
- Choose Enterprise CA and click Next
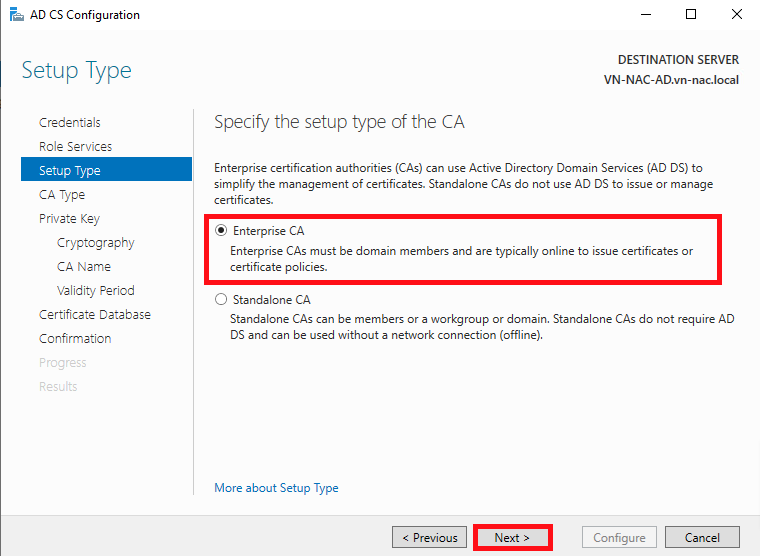
- Select Subordinate CA
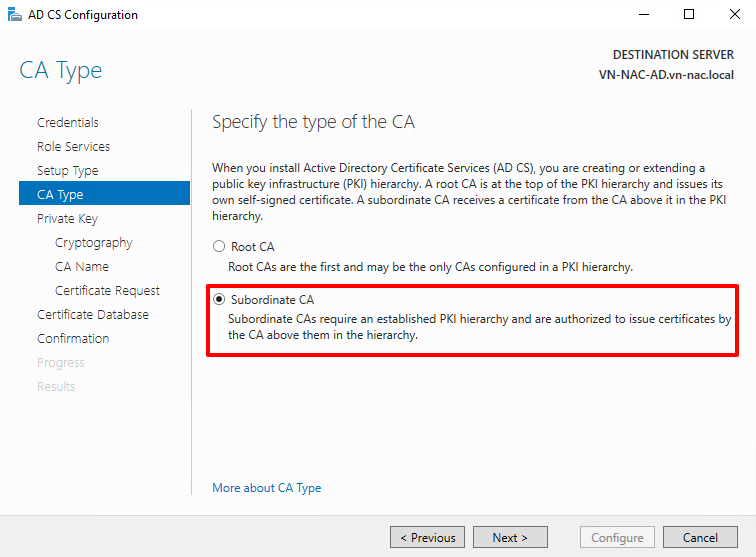
- Create a brand new private key
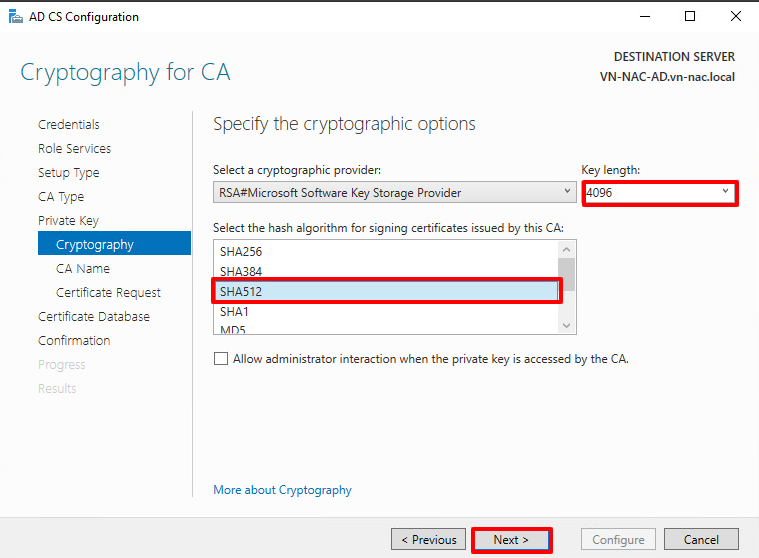
- Choose proper cryptographic options
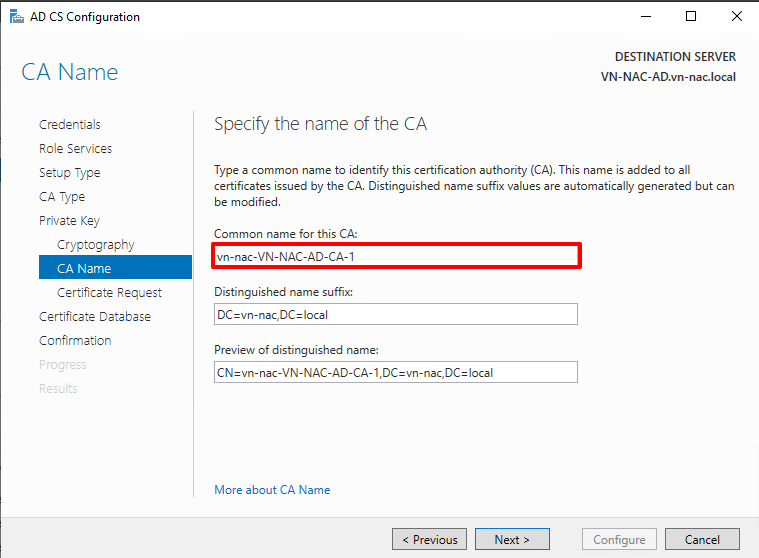
- Specify the name of the CA
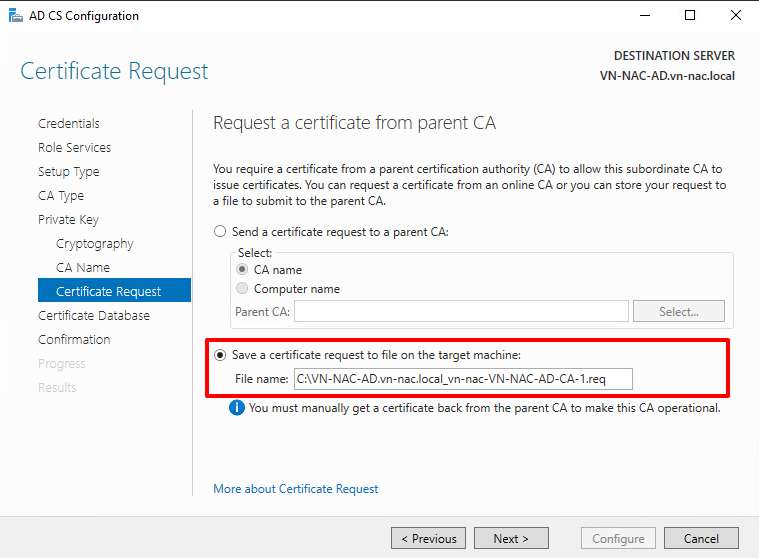
- Choose the option Save the certificate request to file on the target machine
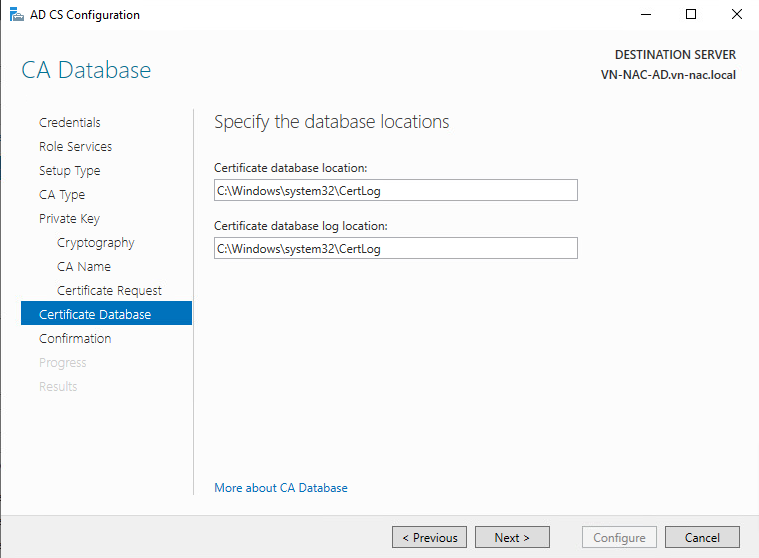
- Specify the database locations
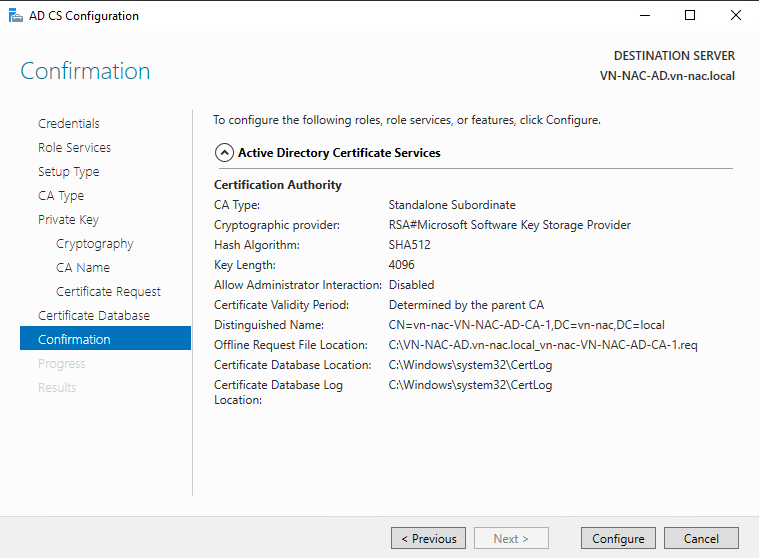
- Check the global configuration and click Configure to run the configuration
- Once the Configuration succeeded click Close
Upload the AD CSR to MetaDefender NAC Cloud
In order for NAC Cloud to securely sign and trust the connection from machines that are connected to the network, users are required to upload the sign request certificate. This certificate is used by NAC Cloud to verify the identity of the machines and establish a trusted connection.
- Log into the MetaDefender IT Access console as an administrator
- Navigate to RADIUS NAC → Click on OPSWAT Cloud RADIUS → Authentication Methods→ EAP-TLS
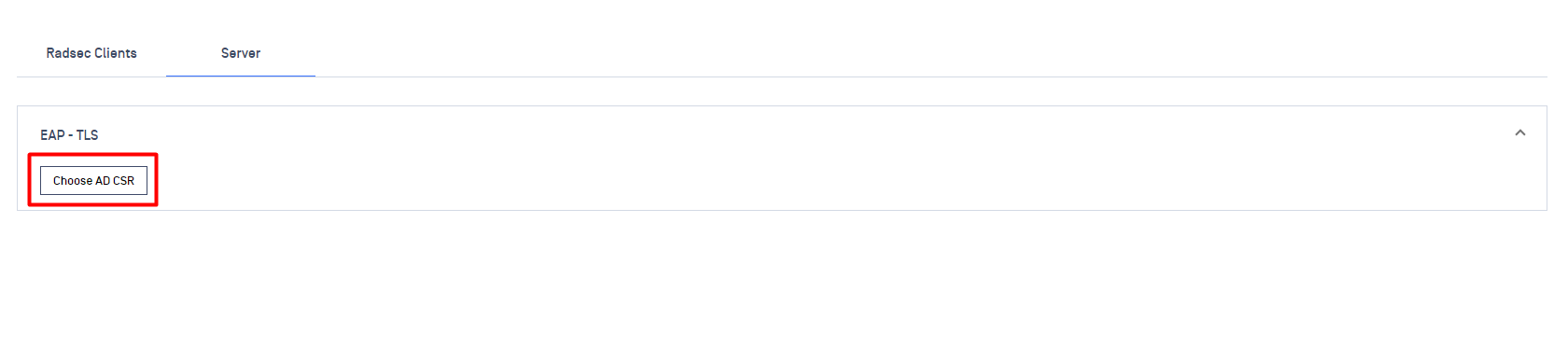
- Click on Choose AD CSR button
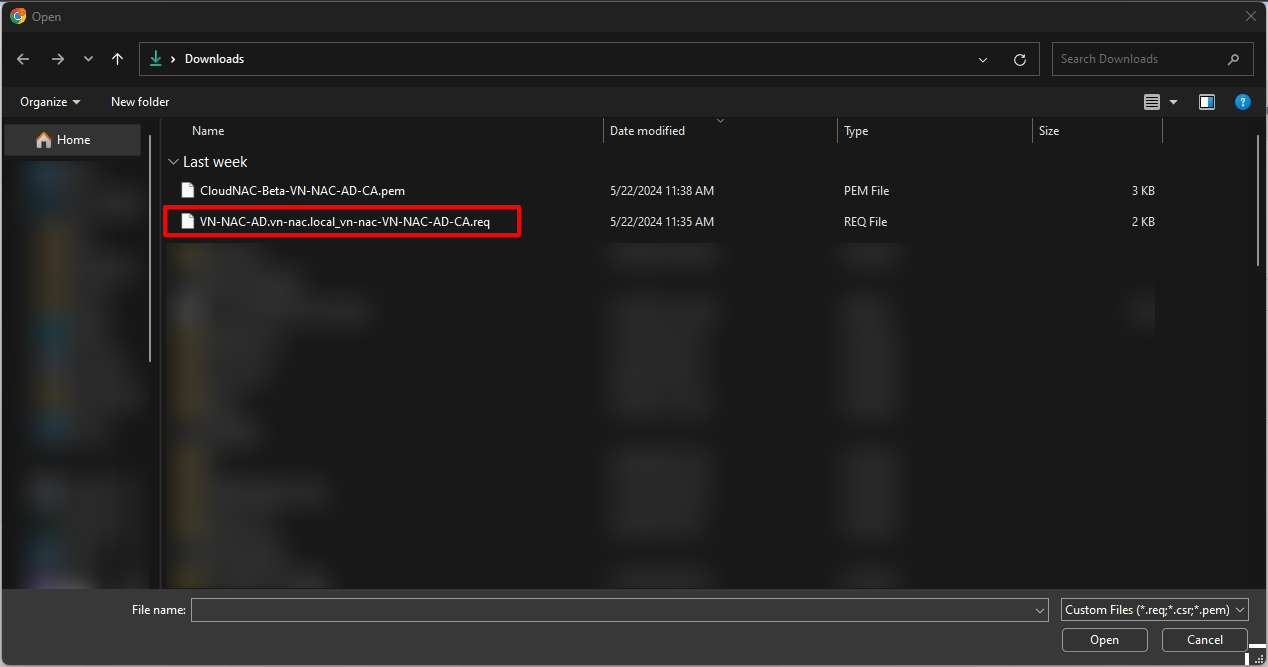
- Select the .req file that generated from the above steps
- The server signed the cert and we'll have the DCA cert available for download. This later will be used to import into the Certification Authority
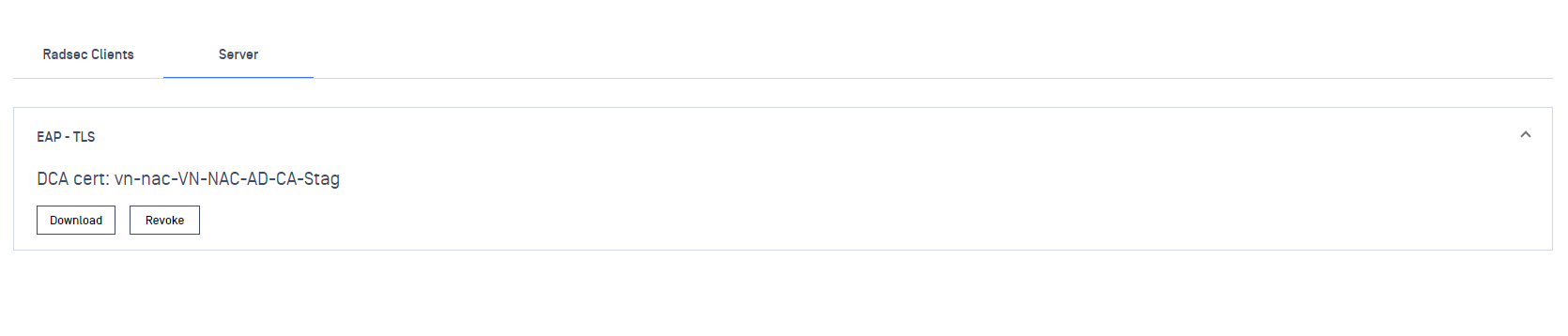
Common configuration for EAP-TLS
Import the CA file to Active Directory
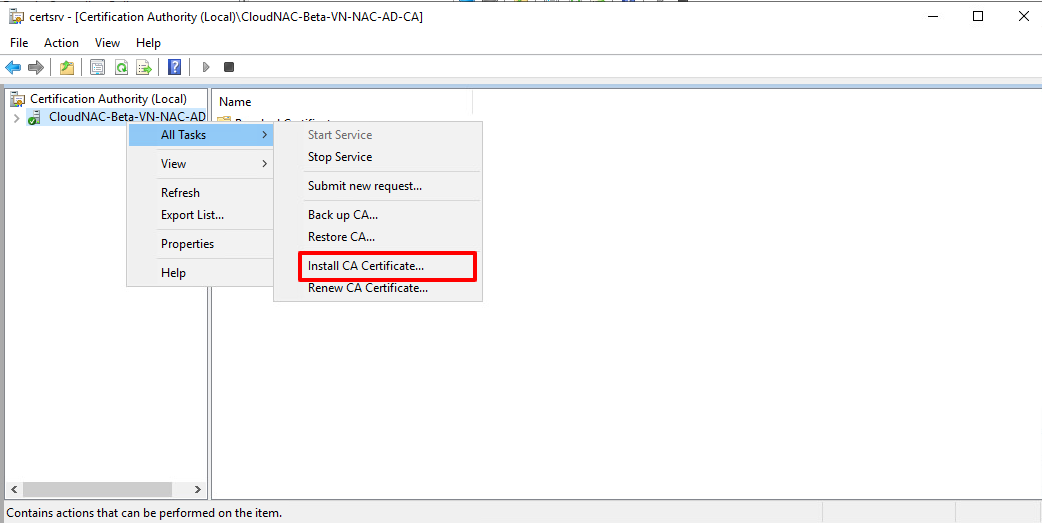
- Download the DCA certificate from this step
- Open Certification Authority tool
- Right click on the Certificate and select All task → Install CA Certificate
- Select the certificate from above
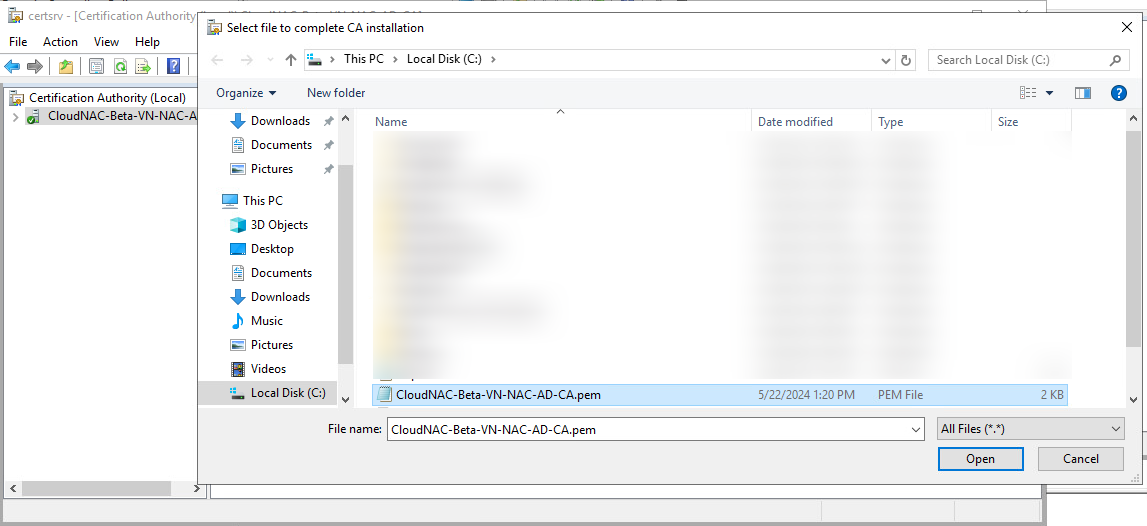
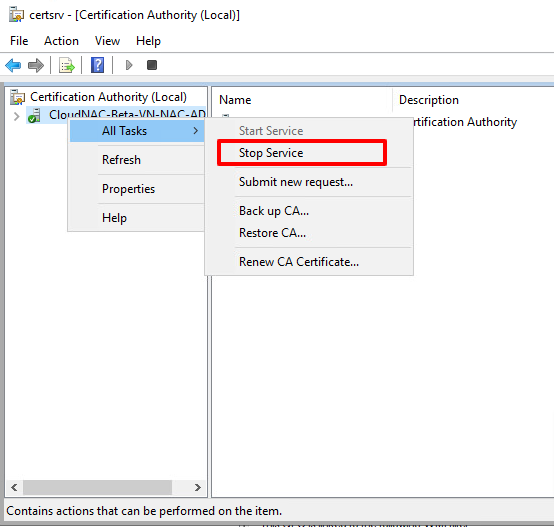
- After install successfully, restart the certsrv by Stop and Start the service
Auto Enroll Certificates with Group Policy
Prepare Certificate Template For Computer and User
Open Certification Authority tool.
Right click on Certificate Templates and then click Manage.
Right-click the Computer template, select Duplicate Template and specify the following:
- Under Compatibility Settings, specify Certification Authority=Windows Server 2003 and Certificate recipient=Windows XP/Server 2003.
- Click the General tab, and change the Template display name to Computer_Auto_Enrollment.
- Click the Security tab, and give "Domain Computers" permissions to Read, Enroll and Autoenroll.
- Additionally, give 'Domain Controllers' permissions to Read, Enroll and Autoenroll. This is required as the DC computer account will request the policy server for validation rather than the logged-in user.
- Select the Subject Name tab, and change the Subject name format to DNS Name.
- Select DNS Name in the subject alternative name.
- Under the Request Handling tab, clear Allow private key to be exported. If the requirement is to be able to export private key, leave this checked.
- Click OK to go back to the template list.
Right-click the User template and select Duplicate Template and specify the following:
- Under Compatibility Settings, specify Certification Authority=Windows Server 2003 and Certificate recipient=Windows XP/Server 2003.
- Click the General tab, and change the Template display name to User_Auto_Enrollment. If the requirement is to Publish the User certificate in Active Directory and Credential Roaming is enabled, ensure to select both Publish certificate in Active Directory and Do not automatically re-enroll if a duplicate certificate exists in Active Directory.
- Select the Security tab, and give "Domain Users" permissions to Enroll and Autoenroll.
- Select the Subject Name tab, and change the Subject name format to Common name.
- Clear Include email name in subject name and clear Email name in the subject alternative name.
- Select User principal name (UPN).
- Under the Request Handling tab, clear Allow private key to be exported. If the requirement is to be able to export private key, leave this checked.
- Click OK to go back to the template list and then close the Certificate Templates Console window.
Issue Certificate Template
Right click on Certificate Template-New-Certificate Template to Issue, and select both Computer_Auto_Enrollment & User_Auto_Enrollment
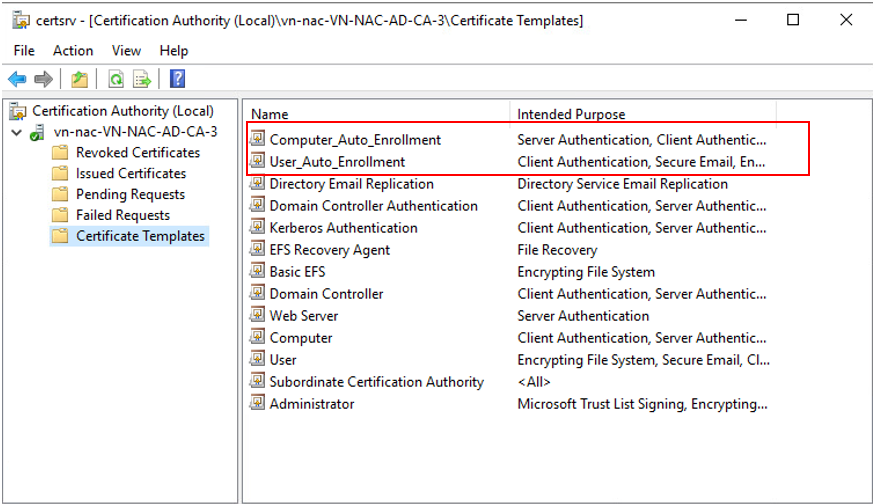
Configuration Of Group Policy
Set the Configuration Model = Enabled in Computer Configuration – Windows Settings – Security Settings – Public Key Policies – Certificate Services Client – Auto Enrollment in Default Domain Policy to enable Certificate Auto Enroll for all domain computers
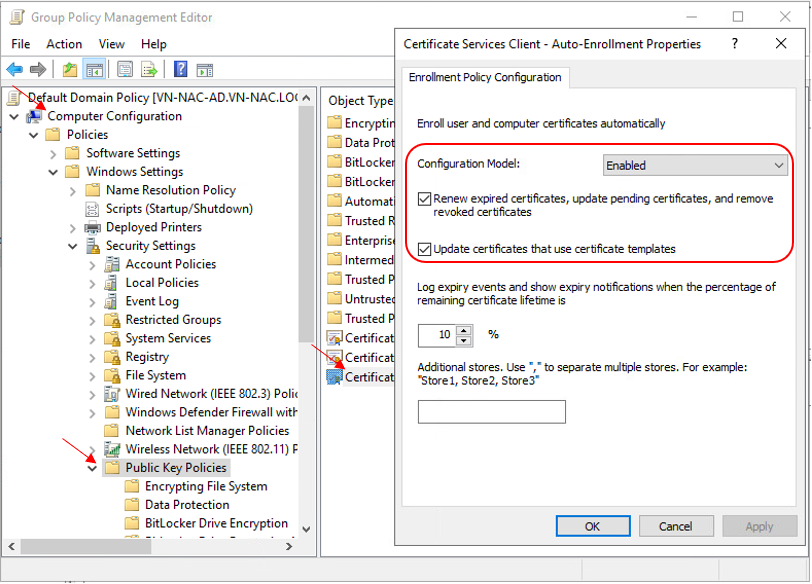
Set the Configuration Model = Enabled in User Configuration – Windows Settings – Security Settings – Public Key Policies – Certificate Services Client – Auto Enrollment in Default Domain Policy to enable Certificate Auto Enroll for all domain users
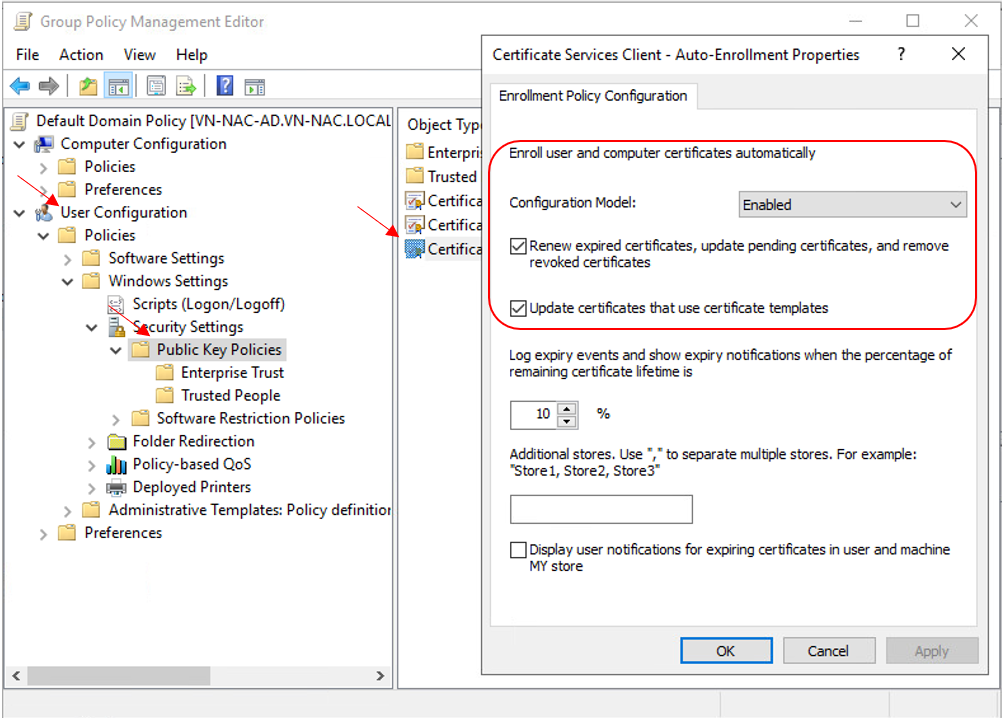
Auto Enroll Certificates With Group Policy For Windows 10
Computer & User Certificate will be generated automatically when Group Policy is updated in the background every 90 Minutes
#can be used to force latest GPO to be applied on users’ workstation immediatelygpupdate /forceDeploy Group Policy for Wireless and Wired Networks
Group Policy for EAP-TLS authentication to a Wireless Network
- Under Computer Configuration – Windows Settings – Security Settings – Wireless Network (IEEE 802.11) Policies
- Enter Policy Name, Description and click Add – Infrastructure
- Enter the SSID Name and click Add
- Select the following
- Authentication = WPA2-Enterprise
- Encryption = AES-CCMP
- Network Authentication Method = Microsoft: Smart Card or Other Certificate
- Authentication Mode = User or Computer Authentication
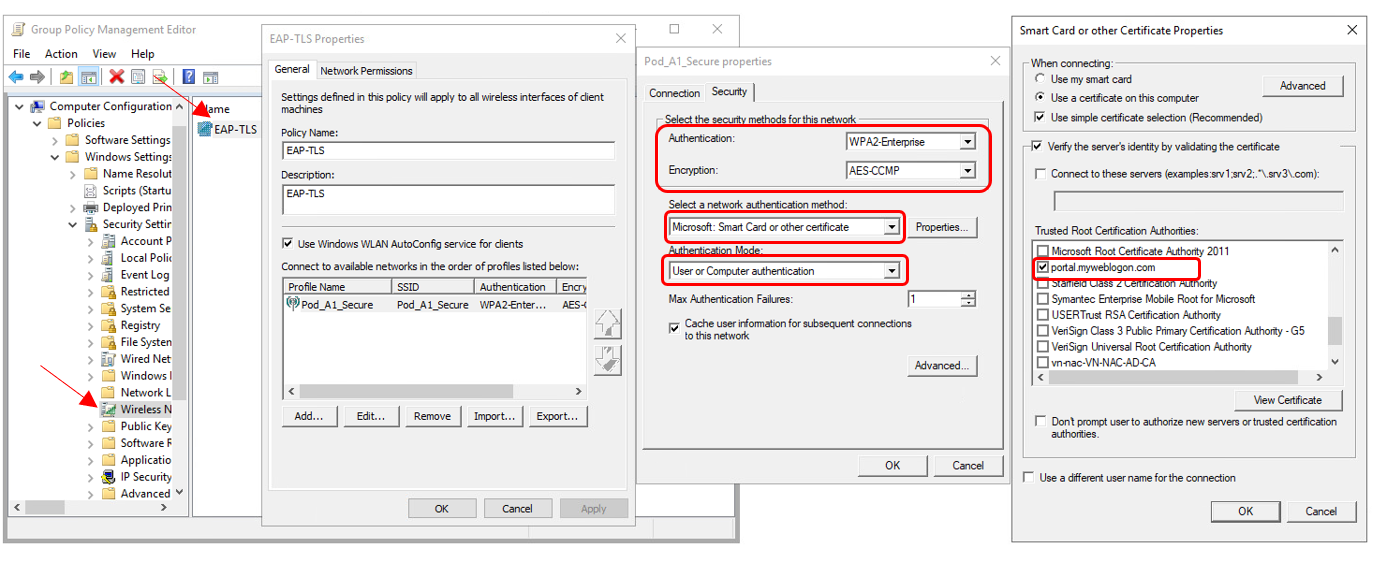
NOTE: If you are using a self-signed RADIUS certificate instead of the default "portal.myweblogon.com" certificate, you should click the "Properties..." button next to the "Select a network authentication method" drop-down on the right-most screen, and choose your self-signed certificate from the list in the window that appears.
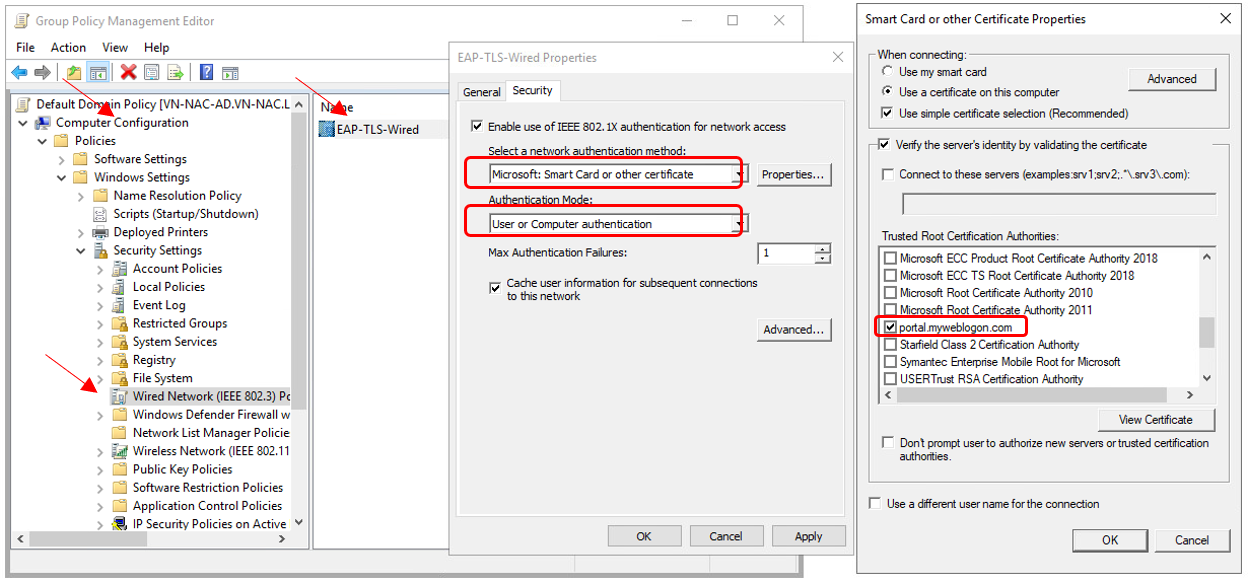
Group Policy for EAP-TLS authentication to a Wired Network
Please follow the same steps as on previous part, but select "Wired Network (IEEE 802.3) Policies" under "Security Settings".
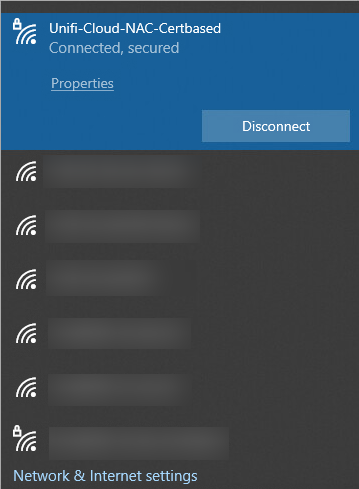
Computer is connected to WIFI automatically when GPO applied
By default, when User open certmgr, a certificate should be available
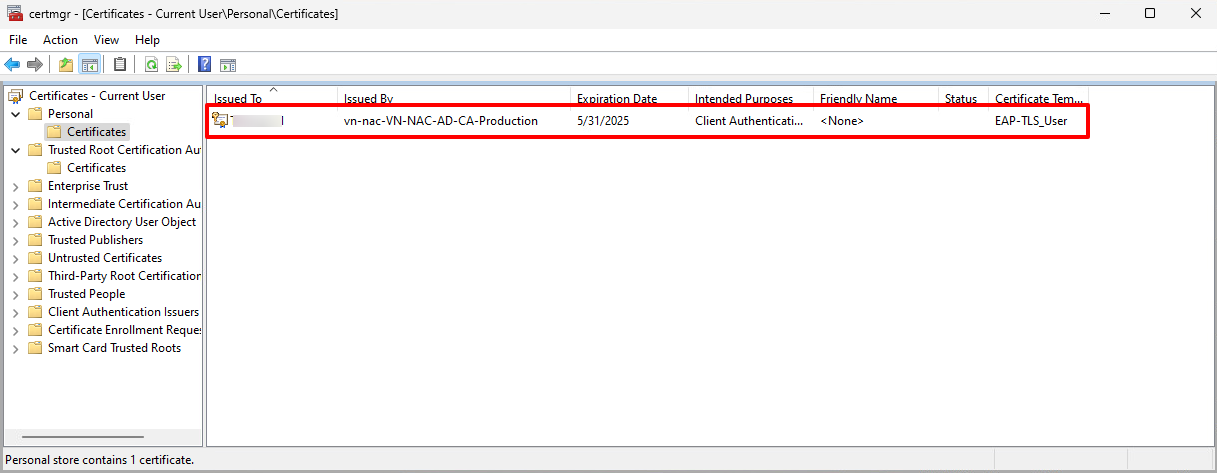
As long as the certificate still available, user will connect to WIFI successfully