What are Rules?
Rules in Metadefender NAC decide which devices can access what parts of your network based on specific conditions you set up. Think of it as creating a checklist - if a device meets all the requirements on your checklist, it gets the access you've defined.
How Rules Work
When a device tries to connect to your network, MetaDefender NAC checks your rules from top to bottom. The first rule that matches the device's characteristics determines what access the device gets.
Example: If you have a rule that says "All company laptops with MD Endpoint installed get full network access," any laptop meeting those conditions will automatically receive full access.
Getting Started with Rules
Step 1: Access the Rules Section
- Log in to your MetaDefender IT Access console
- Click on "RADIUS NAC" in the left menu
- Select the "Rules" tab
- Click "Add New Rule" to create your first rule
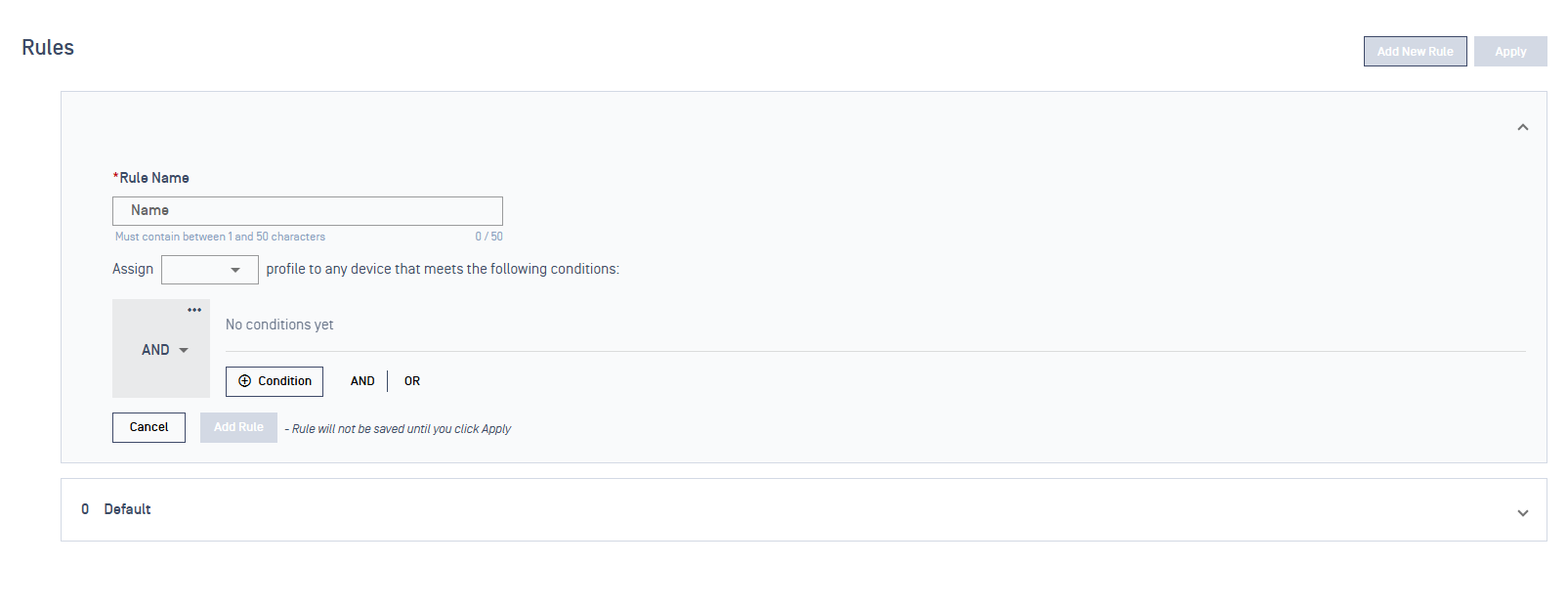
Step 2: Name Your Rule
Give your rule a clear, descriptive name that explains what it does.
Good examples:
- "Company Laptops - Full Access"
- "Guest Devices - Limited Access"
- "IT Department - Admin Access"
Avoid vague names like:
- "Rule 1"
- "Test"
- "New Rule"
Step 3: Choose What Access to Grant
In the "Assign" dropdown, select which Access Profile devices should get when they match this rule.
Building Rule Conditions
This is where you define what devices must have or do to match your rule. The system lets you create from simple to complex conditions.
Understanding Condition Types
Your rules can check three main types of information about devices:
1. Device Information (Endpoint)
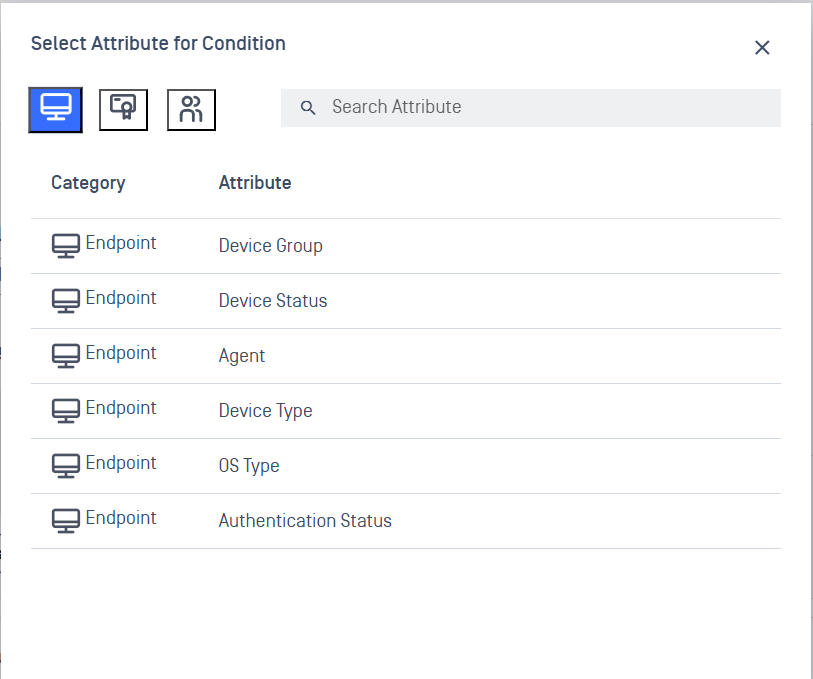
Basic information about the device itself:
- Device Group: Which group the device belongs to
- Device Status: Whether the device is compliant with your security policies
- Agent: Whether your Metadefender Endpoint software is installed
- Device Type: What kind of device it is (laptop, phone, tablet, etc.)
- OS Type: The operating system (Windows, Mac, Android, etc.)
- Authentication Status: Whether the user properly logged in
2. Certificate Information
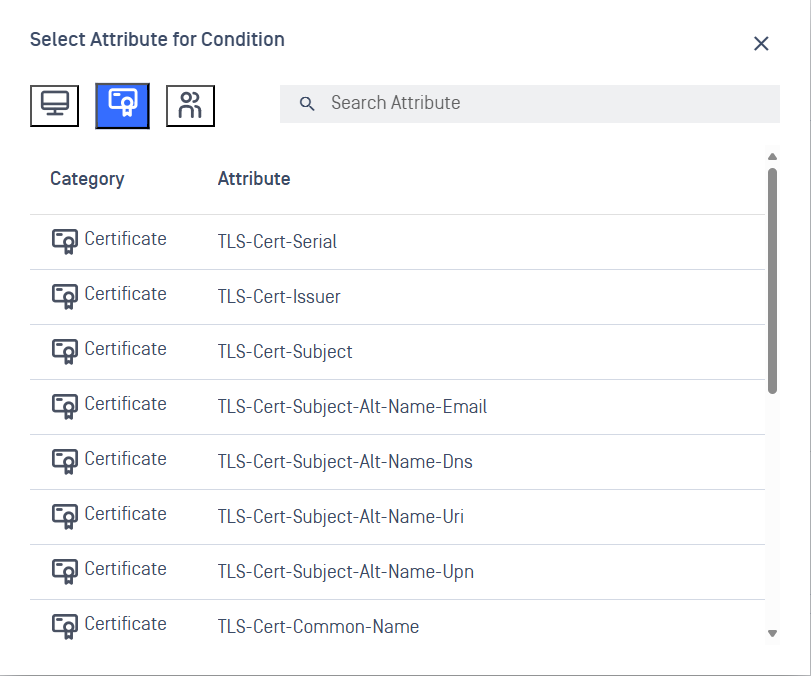
Security certificates the device presents:
- Certificate details: Serial numbers, who issued it, subject information
- Certificate names: Various name fields in the certificate
3. User Directory Information (LDAP)
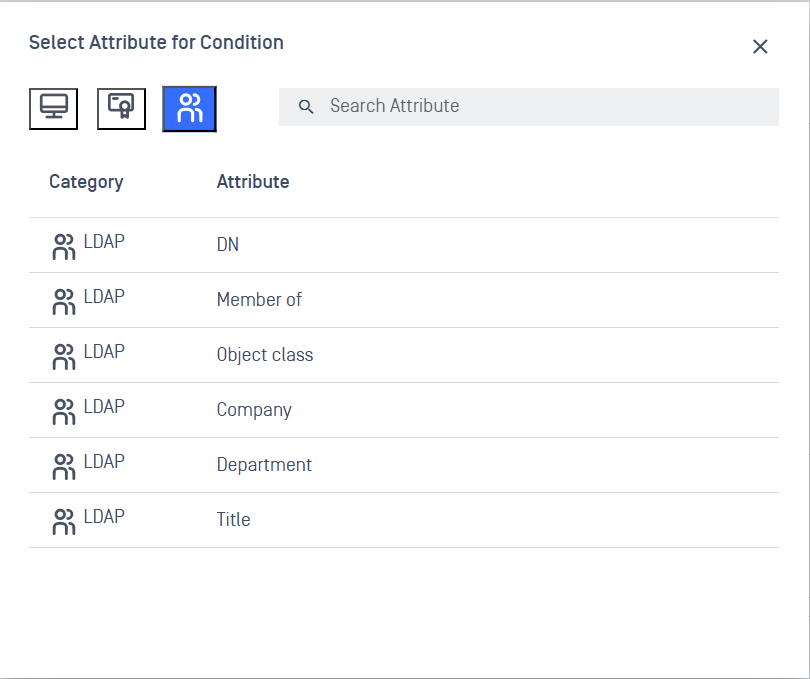
Information from your organization's user directory:
- User Groups: Which groups the user belongs to
- Department: User's department
- Title: User's job title
- Company: User's company affiliation
Important: Assigning a Profile to the Default Rule
Before adding your first custom rule, ensure that the Default Rule has an Access Profile assigned. By default, this rule does not have any profile associated with it, which means:
- You will not be able to save changes to the ruleset until a profile is assigned.
- Devices that do not match any custom rule will fall into the Default Rule, so leaving it unassigned may result in unintended access behavior.
To assign an Access Profile to the Default Rule:
- Navigate to the Rules tab.
- Locate the Default Rule in the list.
- Click to expand it and select an appropriate Access Profile from the dropdown.
- Click Apply to save changes.
Once this is done, you can proceed to create and configure custom rules with conditions.
Adding Your First Condition
Click the "+ Condition" button
Choose an attribute category from the popup:
- Click the computer icon for Device/Endpoint attributes
- Click the certificate icon for Certificate attributes
- Click the people icon for LDAP/User attributes
Select the specific attribute you want to check
Set the condition (equals, contains, etc.)
Enter the value to check for
Creating Simple Rules (AND Logic)
AND means ALL conditions must be true.
Example: Device must be a laptop AND have Metadefender Endpoint installed AND belong to the "Staff" group.
To create this:
- Add condition: Device Type equals "Laptop"
- Add condition: Agent equals "Installed"
- Add condition: Device Group equals "Staff"
All three must be true for the rule to match.
Creating Flexible Rules (OR Logic)
OR means ANY of the conditions can be true.
Example: Device can be either a laptop OR a desktop to get access.
To create this:
- Add condition: Device Type equals "Laptop"
- Click "OR"
- Add condition: Device Type equals "Desktop"
If either condition is true, the rule matches.
Creating Advanced Rules (Combined Logic)
You can combine AND and OR to create sophisticated rules.
Example: Grant network access to devices that meet:
Device criteria: Must be a desktop or laptop with the MD Endpoint installed
User criteria: User must be either:
- In the IT department, OR
- A member of Management, OR
- Have a TLS certificate containing "VN-NAC" AND issued by "VN-NAC-AD-CA
This rule would have the structure as below:
ROOT (AND)├── AND Group (Level 1)│ ├── Device type is (Desktop OR Laptop)│ └── Agent is Installed└── OR Group (Level 1) ├── LDAP attribute Department equals IT ├── LDAP attribute Member of equals Management └── AND Group (Level 2) ├── Certificate TLS-Cert-Subject contains VN-NAC └── Certificate TLS-Cert-Common-Name equal VN-NAC-AD-CAHow to Build:
Initial Setup
Navigate to Rule Creation
- Go to
RADIUS NAC→Rules→Add new Rules
- Go to
Configure Basic Rule Information
- Enter a descriptive Rule name (e.g., "IT-Management-Device-Access")
- Select the option to assign a profile to the Rule
- Note: The default root operator is
AND(can be changed toORif needed)
Building the Condition Structure
Level 1: Device Requirements (AND Group)
Create Primary Device Condition Group
- Click the
ANDbutton at level 1 to create a group condition with AND operator - This group will contain device-specific requirements
- Click the
Add Device Type Condition
- Click
+conditionbutton at level 2 (inside the AND group) - Select condition:
Device type is - Choose multi-select options:
Desktop,Laptop - Note: This allows either desktop OR laptop devices
- Click
Add Agent Installation Requirement
- Click
+conditionbutton at level 2 (inside the same AND group) - Select condition:
Agent is Installed
- Click
Level 1: User Authorization (OR Group)
Create User Authorization Group
- Click the
ORbutton at level 1 to create a group condition with OR operator - This group will contain alternative user authorization methods
- Click the
Add IT Department Condition
- Click
+conditionbutton at level 2 (inside the OR group) - Select condition:
LDAP attribute Department equals IT
- Click
Add Management Group Condition
- Click
+conditionbutton at level 2 (inside the same OR group) - Select condition:
LDAP attribute Member of equals Management
- Click
Level 2: Certificate Authentication (Nested AND)
Create Nested Certificate Group
- Click the
ANDbutton at level 2 (inside the OR group from step 6) - This creates a nested AND condition within the OR group
- Click the
Add Certificate Subject Condition
- Click
+conditionbutton at level 3 (inside the nested AND group) - Select condition:
Certificate TLS-Cert-Subject contains VN-NAC
- Click
Add Certificate Common Name Condition
- Click
+conditionbutton at level 3 (inside the same nested AND group) - Select condition:
Certificate TLS-Cert-Common-Name equal VN-NAC-AD-CA
- Click
Finalize Rule
- Save the Rule
- Click
Add Rulebutton to create the new rule - Verify the rule appears in the rules list
- Click
Common Rule Examples
Example 1: Company Employee Access
Goal: Give full access to company employees with proper security
Conditions:
- User is in "Employees" group AND
- Device has Metadefender Endpoint installed AND
- Device is compliant
Example 2: Guest Access
Goal: Give limited internet access to visitor devices
Conditions:
- Authentication Status = "Authenticated via Guest Access" OR
- Device Group = "Visitors"
Example 3: IT Department Special Access
Goal: Give IT staff administrative access from their work devices
Conditions:
- (Department = "IT" OR User Group = "IT Admins") AND
- Device Type = "Laptop" AND
- Certificate Issuer = "Company CA"
Example 4: Mobile Device Policy
Goal: Allow mobile devices but with restrictions
Conditions:
- (Device Type = "Phone" OR Device Type = "Tablet") AND
- Agent = "Installed" AND
- Device Status = "Compliant"
Managing Your Rules
Rule Order Matters
Rules are checked from top to bottom. The first matching rule wins.
Best Practice: Put your most specific rules at the top, general rules at the bottom.
Example Order:
- IT Admin Full Access (very specific)
- Company Employee Standard Access (specific)
- Guest Limited Access (general)
- Default Block All (catch-all)
Editing Rules
- View Details: Click on a rule to see its conditions
- Move Up/Down: Use arrow buttons to reorder rules
- Enable/Disable: Use the toggle switch to turn rules on/off
- Delete: Click the trash icon to remove a rule
The Default Rule
There's always a "Default Rule" at the bottom. This catches any device that doesn't match your other rules. Make sure to set this to an appropriate access level (usually very limited or blocked).
Troubleshooting Tips
Device Not Getting Expected Access
- Check rule order - Is a more general rule above your specific rule?
- Verify conditions - Are all the conditions actually true for the device?
- Test with simple rules - Start with one condition and add complexity
Rule Too Complex
- Break complex rules into multiple simpler rules
- Use descriptive names to track what each rule does
- Document your logic in the rule name
Performance Issues
- Avoid overly complex nested conditions
- Place most commonly matched rules higher in the list
- Regularly review and clean up unused rules
Best Practices
- Start Simple: Begin with basic rules and add complexity as needed
- Test Thoroughly: Always test new rules with actual devices
- Document Everything: Use clear rule names that explain the purpose
- Regular Reviews: Periodically review rules to ensure they're still needed
- Security First: When in doubt, be more restrictive rather than permissive
Getting Help
If you need assistance with creating rules:
- Start with the examples provided
- Test rules in a safe environment first
- Contact your system administrator for complex scenarios
- Keep rule logic as simple as possible while meeting your security needs
- Or contact OPSWAT support

