- Port Access Authentication with 802.1X
Scenario: A client device connects to port switch was configured 802.1X authentication method. After authentication, client device will be transferred to compliant vlan. We will go through below configuration
- Defined AAA Profile and Radius Server
- Configure Port Uplink and Secure Port Access
- Configure 802.1X on Client Computer
- Information: device Dell EMC switch N2024P , verion: 6.7.1.X
1.1 - Define AAA Profile and Radius Server
aaa accounting dot1x default start-stop radius
aaa accounting delay-start extended-time 300
aaa accounting update newinfo periodic 3
authentication enable
authentication dynamic-vlan enable
dot1x system-auth-control
aaa authentication dot1x default radius
aaa authorization network default radius
aaa server radius dynamic-author
client "IP_Of_NAC_Edge" server-key 7``"Serect Key"
auth-type any
radius server attribute 8 include-in-access-req
radius server auth "IP_Of_NAC_Edge"
name "Default-RADIUS-Server"
key 7"Serect Key"
exit
radius server acct"Serect Key"
name "Default-RADIUS-Server"
key 7 "Serect Key"
exit
radius server vsa send authentication
1.2 - Configure Port Uplink and Secure Port Access
**interface Gi1/0/1**
switchport mode trunk
authentication port-control force-authorized
exit
**interface Gi1/0/2**
switchport mode general
authentication host-mode multi-auth
authentication max-users 2
authentication periodic
dot1x timeout tx-period 15
dot1x max-reauth-req 1
mab
authentication order dot1x mab
authentication priority dot1x mab
switchport port-security
exit
1.2 - Configure 802.1X On Client Computer
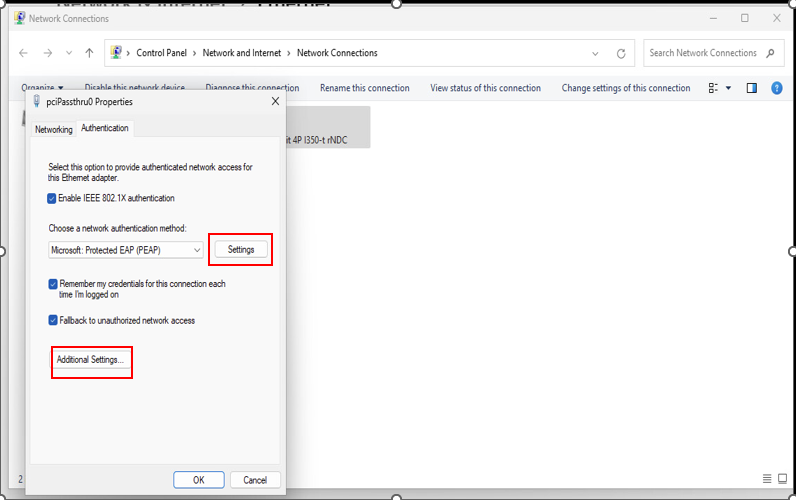
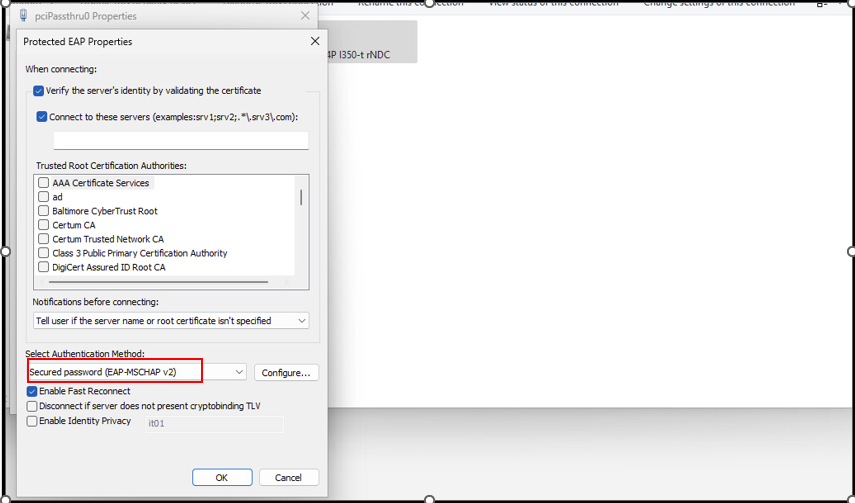
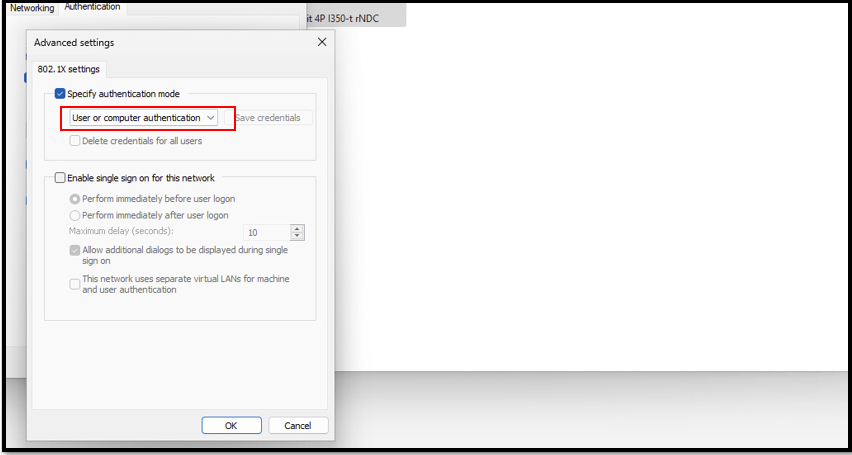
1.3 - Define Access Profille and Rule on CloudNAC Dashboard
We create Access Profile, this profile simply assigns vlan for authenticated client
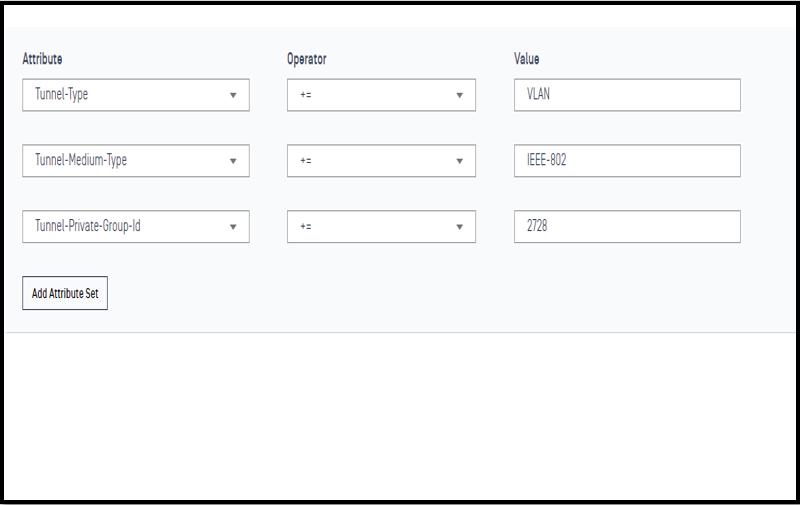
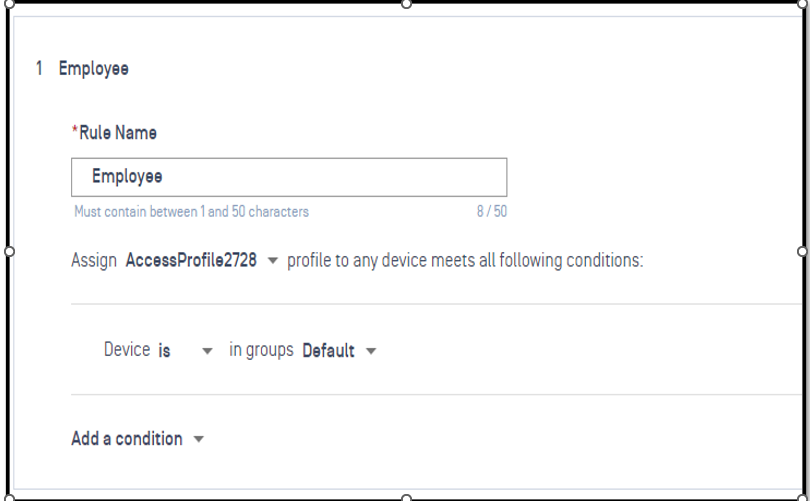
Define Rule
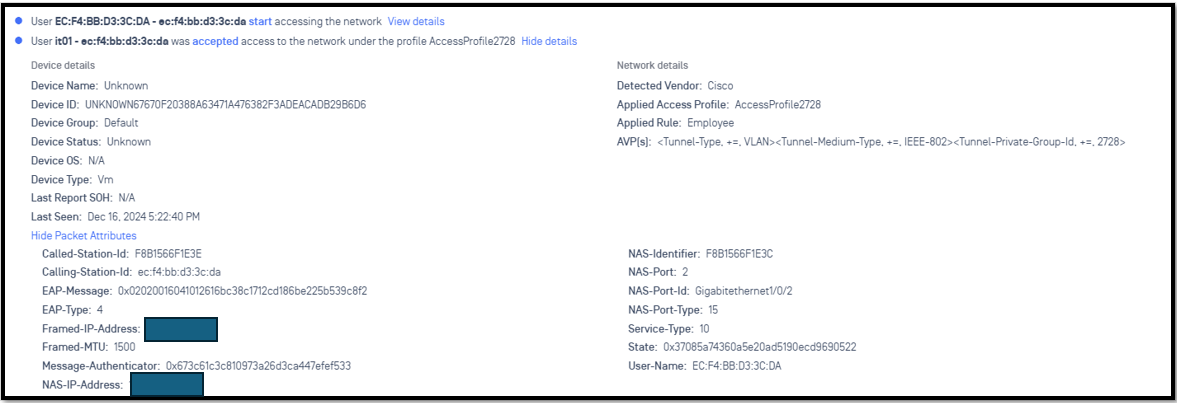
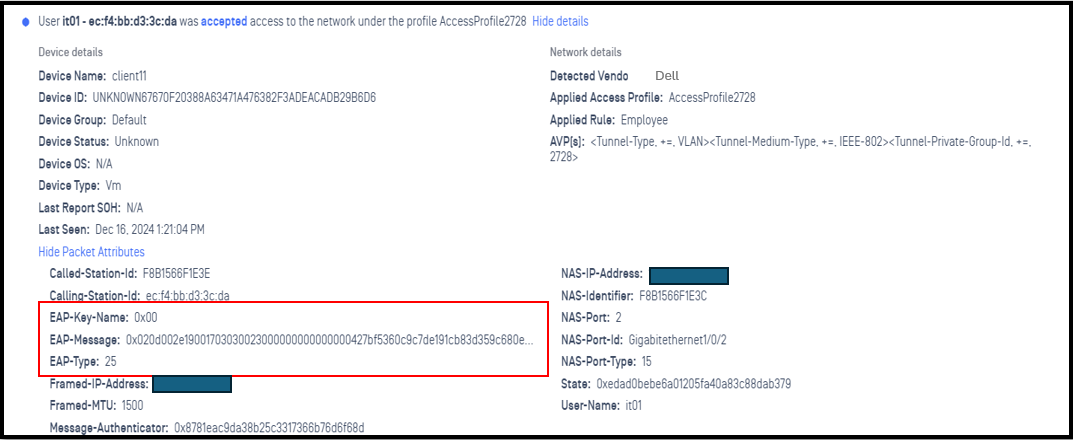
1.4 - Check log Radius
client computer was authenticated via 802.1X PEAP successfully with Active Directory Server
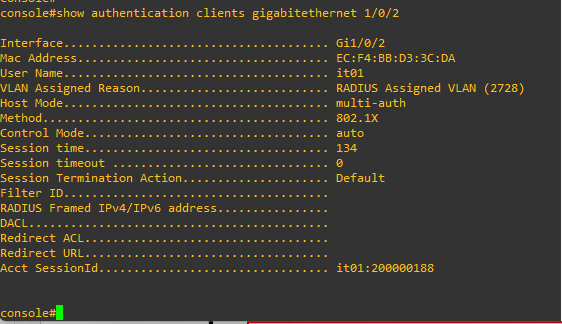
Show log in Dell Switch: "show authentication clients gigabitethernet 1/0/2"
2 - Port Access Authentication with CloudNAC Portal
Scenario: When a client device connects to a switch port, the port will initially be assigned to a quarantine VLAN. In this VLAN, all HTTP traffic will be redirected to the CloudNAC Portal.
The end-user must authenticate successfully, after which the switch port will be assigned to a compliant VLAN, allowing the end-user to access the Internet.
The credentials provided by the end-user will be authenticated using an LDAP/s server. We will have below configuration sections
.Define ACL in Dell Switch
.Define AAA Profile and Radius Server - Read 1.1 Section
.Define LDAP Configuration on CloudNAC Dashboard
.Define AccessProfile and Rule on CloudNAC Dashboard
2.1 - Define ACL in Dell Switch
Nslookup is useful tool to help us identify IPv4/IPv6 subnet that should be listed in our ACL
- Opswat1:
console.metaccess-b.opswat.com - Opswat2:
nac-b.opswat.com - Opswat3:
gears.opswat.com
We created acl and named it sc_quarantine_acl
ip access-list sc_quarantine_acl
10 deny udp any any eq domain
20 deny udp any any eq 67
30 deny udp any any eq 68
40 deny ip anyIP_Of_NAC_Edge0.0.0.0
100 permit tcp any any eq http
CloudNAC supports dACLs. When a client connects to a switch port, access control entries (ACEs) are directly installed on the switch. These ACEs, combined with the ACL sc_quarantine_acl, ensure the client cannot access any resources and HTTP client's traffic will be redirected to the CloudNAC Portal for authentication process. (These ACEs will be shown in later section)
2.2 - Define Access Profile and Rule on CloudNAC Dashboard
Created Access Profile and named is CloudNAC_Portal. In this Access Profile, we are going to create Dynamic ACEs that mentioned before
Tunnel-Type += VLANTunnel-Medium-Type += IEEE-802Tunnel-Private-Group-Id += 1779Cisco-AVPair += ip:inacl#10 = permit ip any ``IP_OF_NAC_EDGE ``0.0.0.255Cisco-AVPair += ip:inacl#20 = permit ip any 3.162.58.0 0.0.0.255Cisco-AVPair += ip:inacl#30 = permit ip any 34.210.21.166 0.0.0.0Cisco-AVPair += ip:inacl#40 = permit ip any 52.36.142.128 0.0.0.0Cisco-AVPair += ip:inacl#50 = permit ip any 52.36.195.176 0.0.0.0Cisco-AVPair += ip:inacl#60 = permit ip any 52.34.232.59 0.0.0.0Cisco-AVPair += ip:inacl#90 = deny tcp any any eq 443Cisco-AVPair += url-redirect=http:// IP_OF_NAC_EDGE? _`#Dont forget question mark at the end`_Cisco-AVPair += url-rediret-acl=sc_quarantine_acl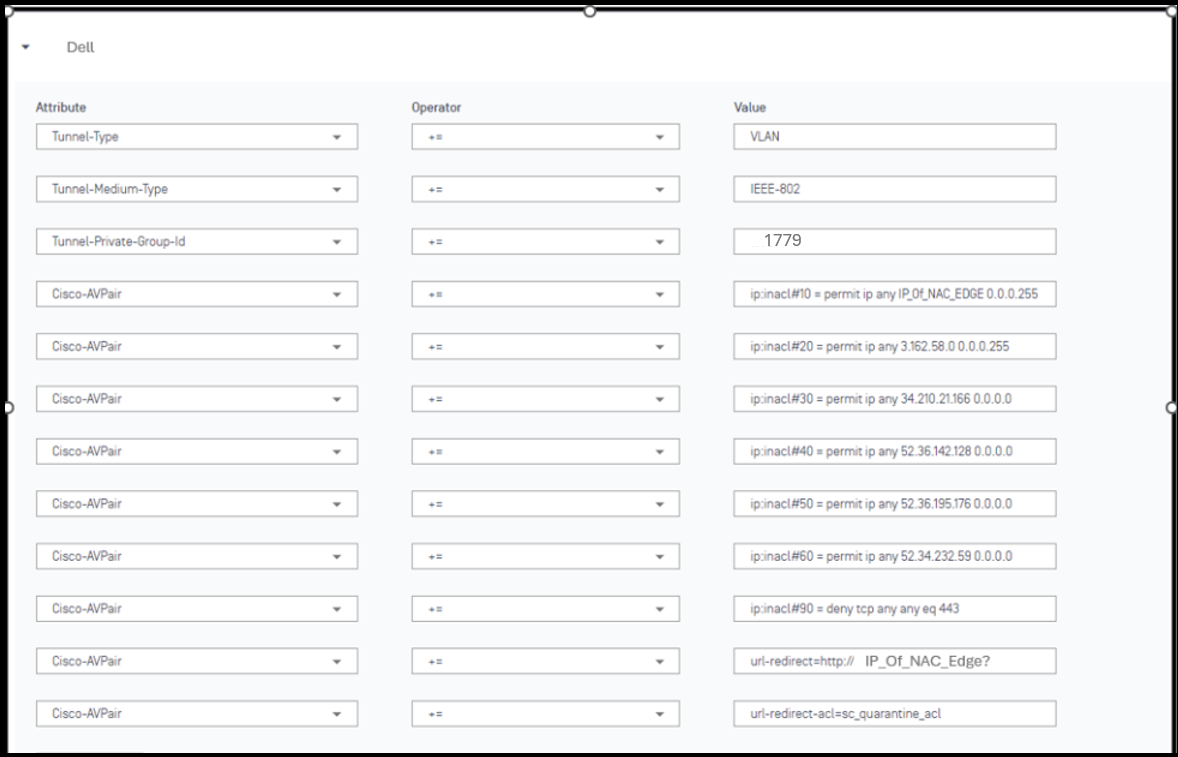
Created Rule Portal Authentication and Employee
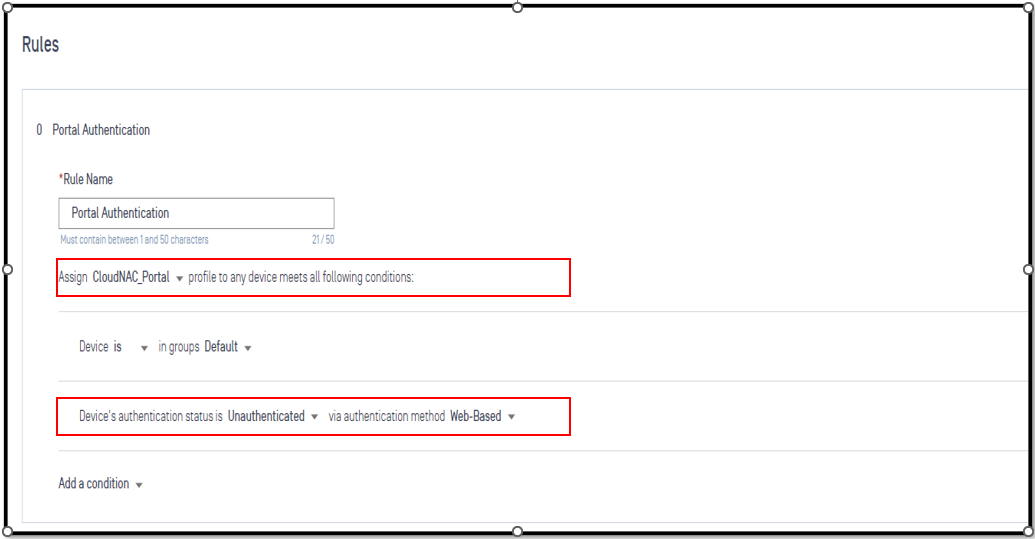
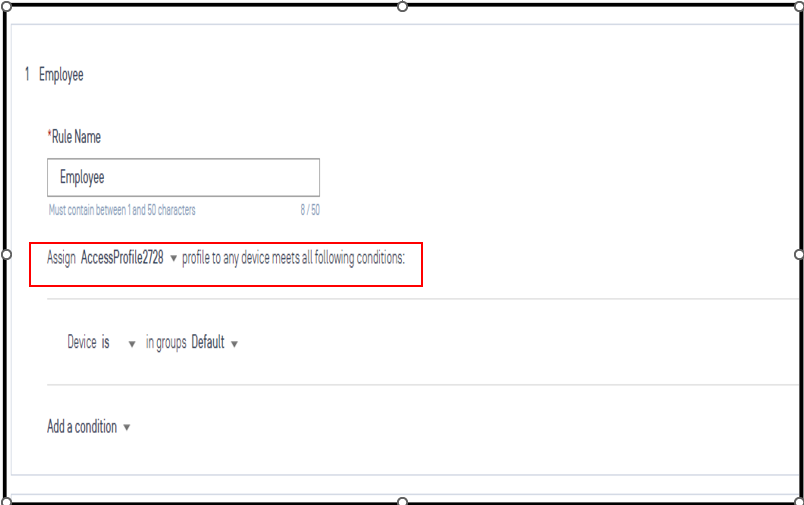
2.3 - Define LDAP Authentication Method
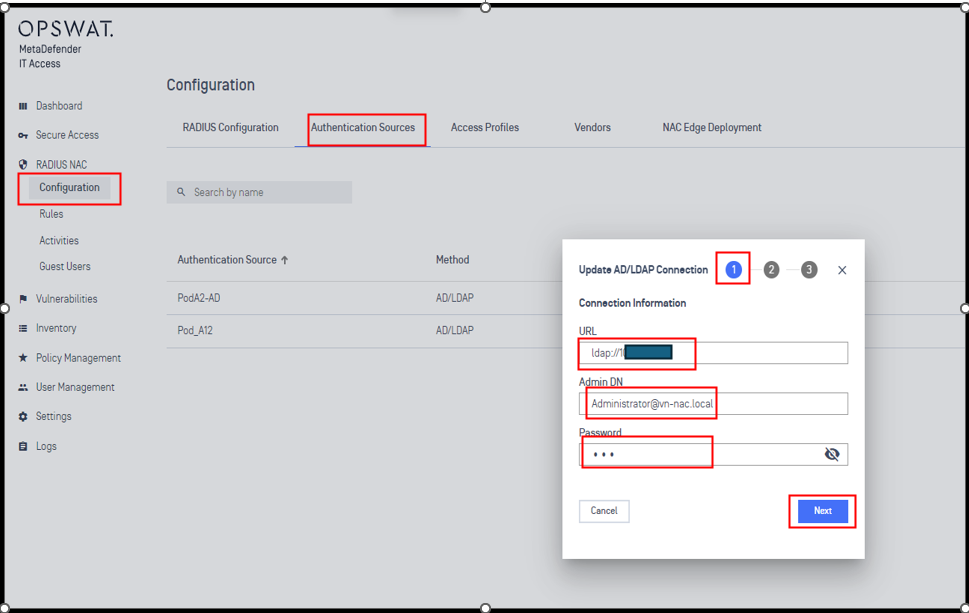
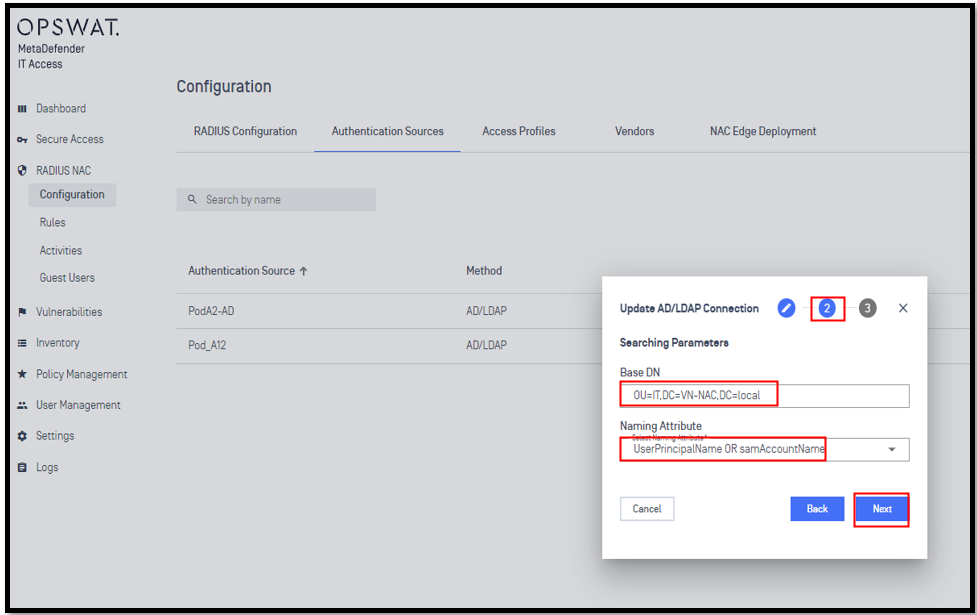
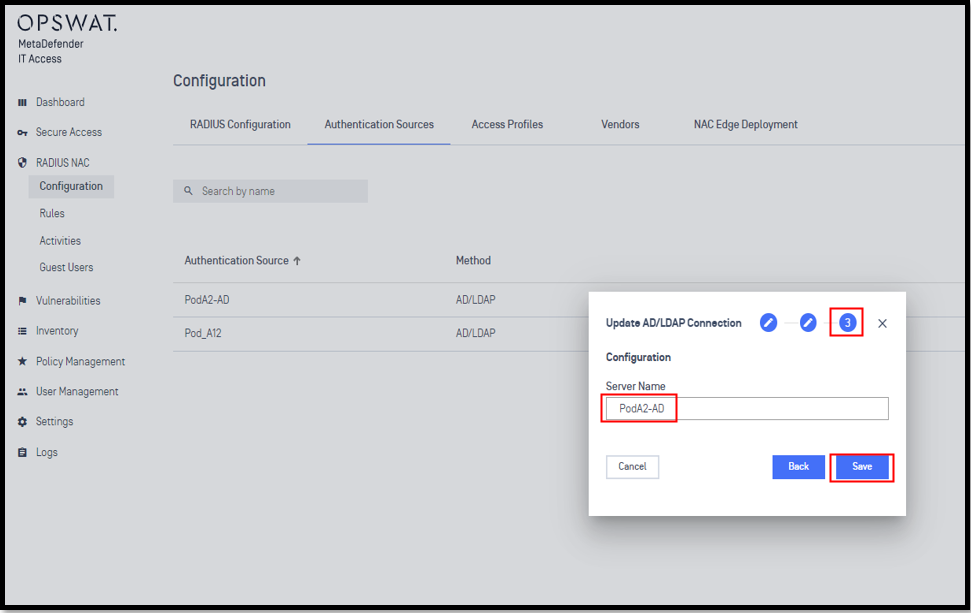
2.4 - Check log Radius
CloudNAC returns profile for client device
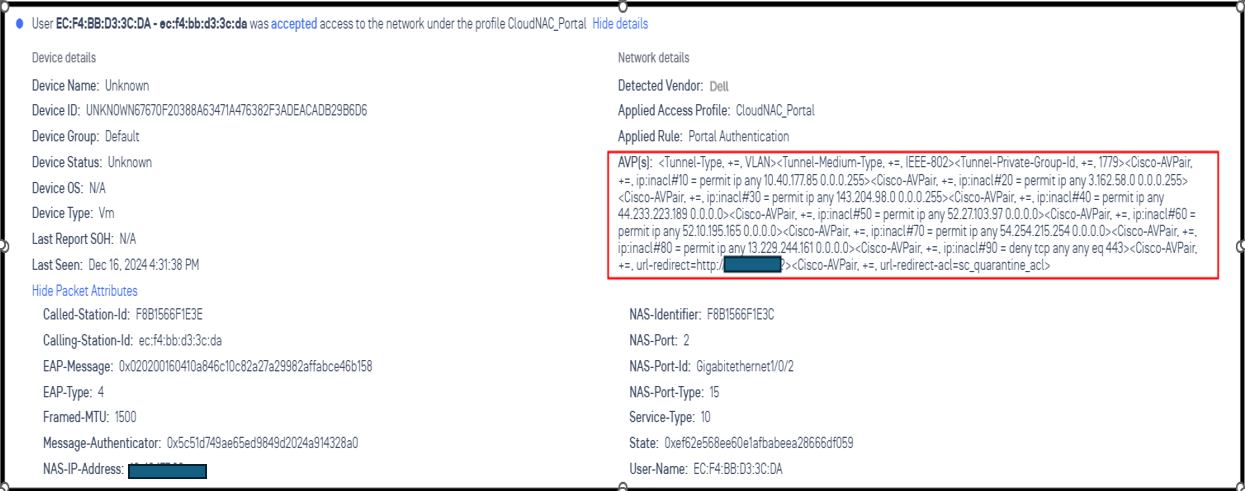
Check log in Dell Switch
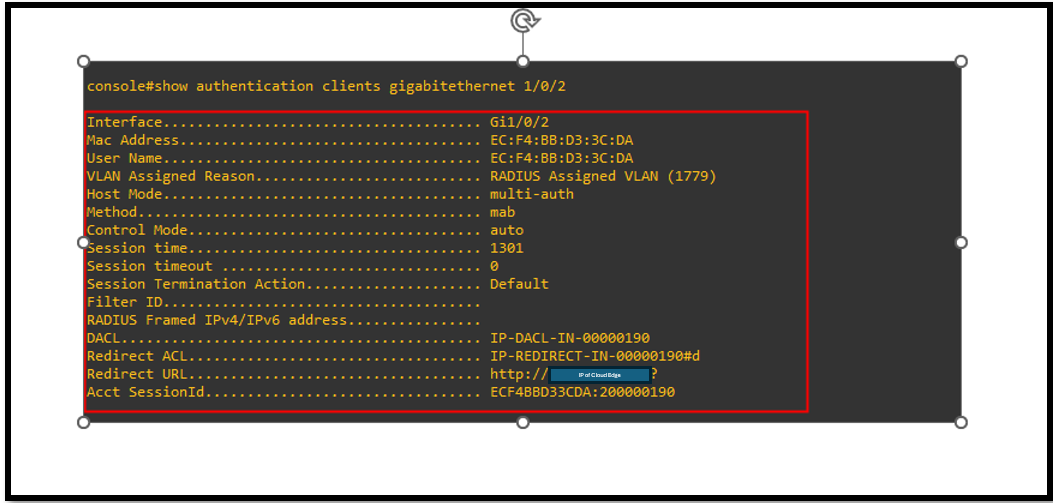
Open web browser on client computer and access http website, http traffic will be redirected to CloudNAC Portal.
Login with credentials authenticated with LDAP, user was assigned another access profile (vlan)