| Type | Detail |
|---|---|
| Problem |
|
| Cause | An invalid setting in Set settings, specific to the affected instance, such as:
|
| Troubleshooting | Events such as "import failed" in MetaDefender Core instances' config history. |
| Solution | Correct invalid settings.
|
After applying Set settings, a MetaDefender Core instance reports "import failed" in its Config History.
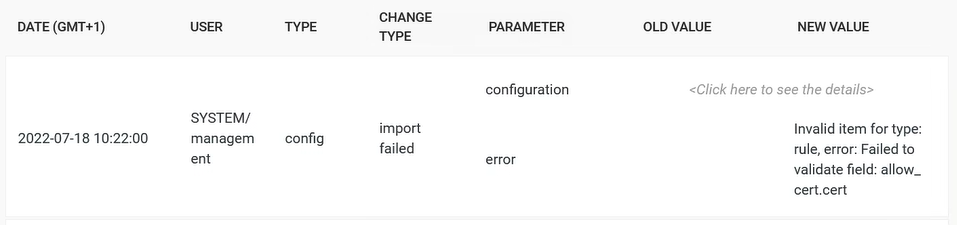
This issue may be caused by an invalid Set setting specific to the affected instance, particularly if not all instances are affected. Specifically, possible invalid settings are:
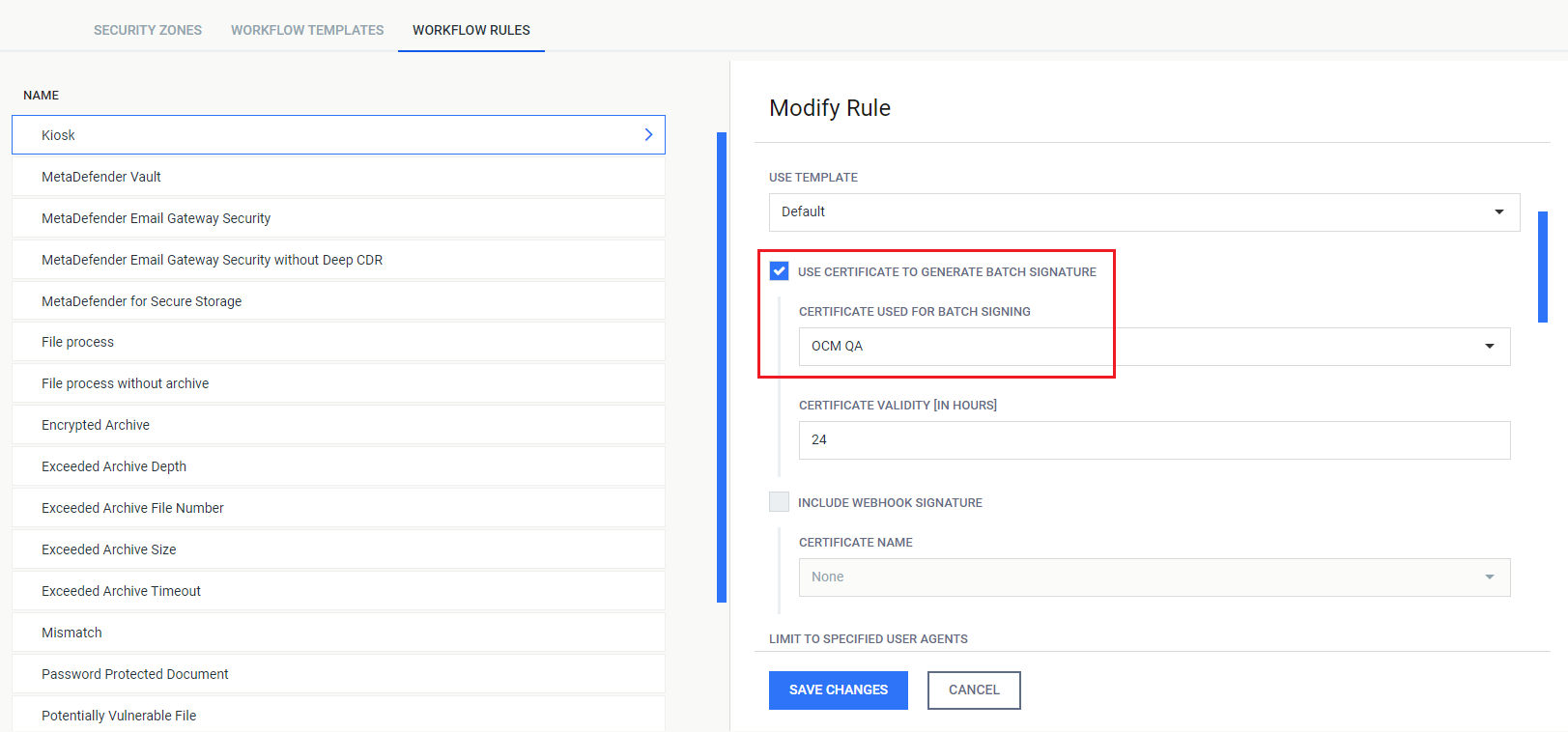
- The Set settings specify a TLS certificate that do not exist on the affected instances, such as in the above example image.
The Set settings specify TLS certificates that do not exist in the affected instances
This is likely the cause if the "import failed" event mentions an invalid item such as allow_cert.cert.
Please check if the certificates specified in the Set settings's allow_cert.cert are present in the affected instance with the same name as specified in the Set settings.
In Set settings, allow_cert.cert corresponds to the Certificate Used for Batch Signing workflow rule.
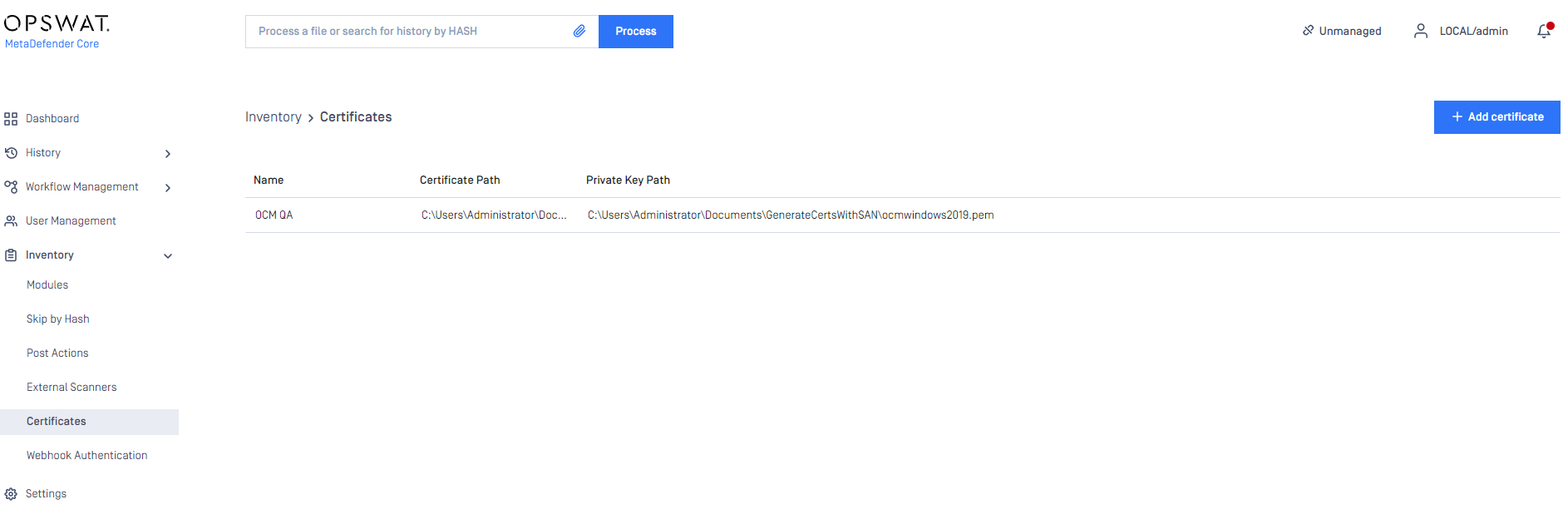
In MetaDefender Core dashboard, you can find the available certificates at Inventory > Certificates in the left navigation menu. Please rename them to match the Set settings if necessary.
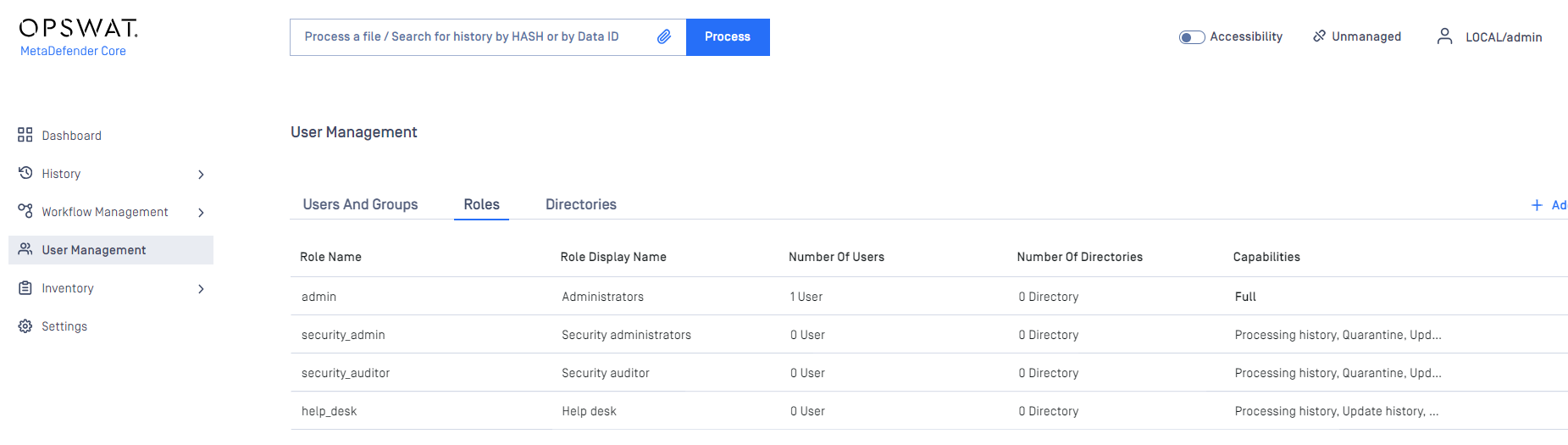
The Set settings specify user roles that do not exist in the affected instances
This is likely the cause if the "import failed" event mentions an invalid item such as scan_allowed .
Please check if the user roles specified in the Set settings's scan_allowed are present in the affected instance with the same name as specified in the Set settings.
In Set settings, scan_allowed corresponds to the Restrict access to following roles workflow rule.
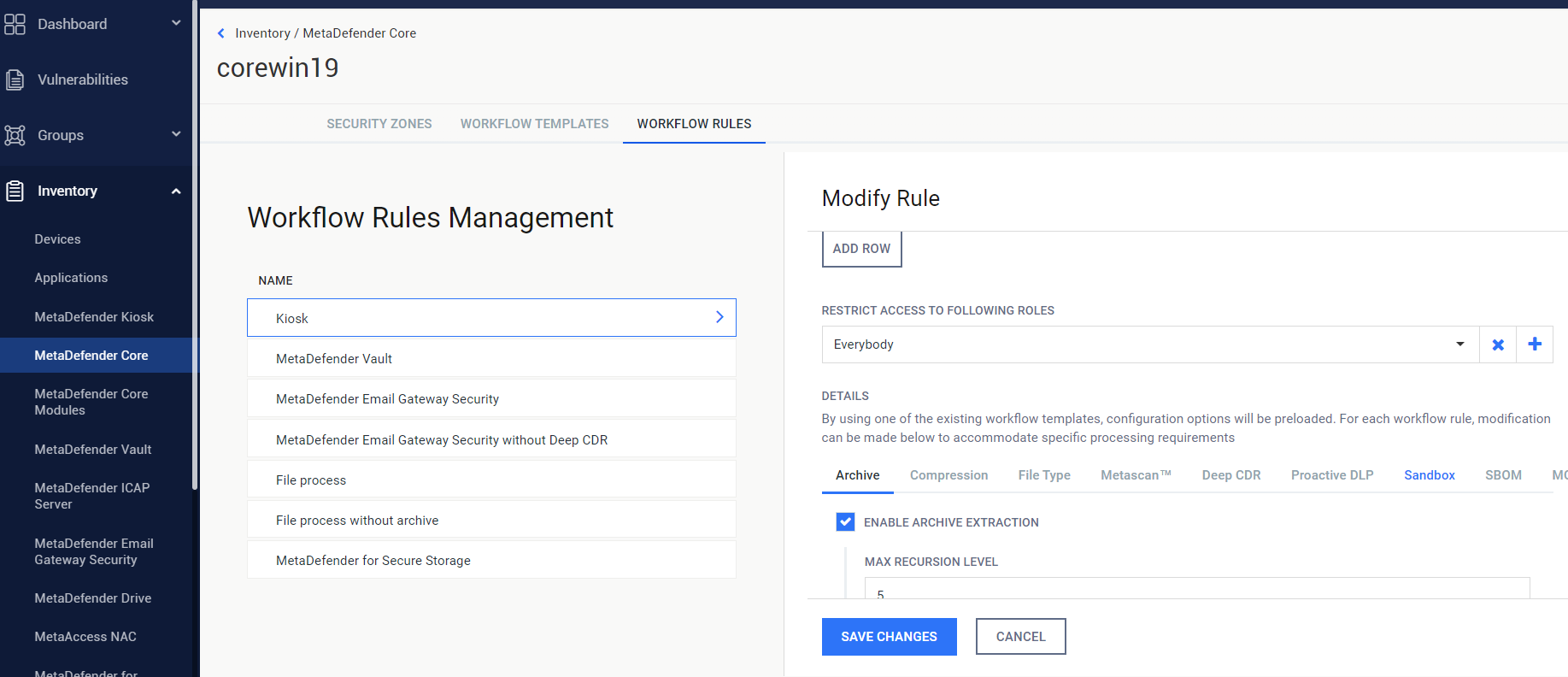
In MetaDefender Core dashboard, you can find the available user roles in User Management > Roles tab in the left navigation menu. Please rename them to match the Set settings if necessary.