Title
Create new category
Edit page index title
Edit category
Edit link
Encryption
By default the product uses a randomly generated cryptographic key to encrypt uploaded files and other secrets.
In order to generate a new cryptographic key please follow these steps:
- Navigate to Settings → Security → Encryption.
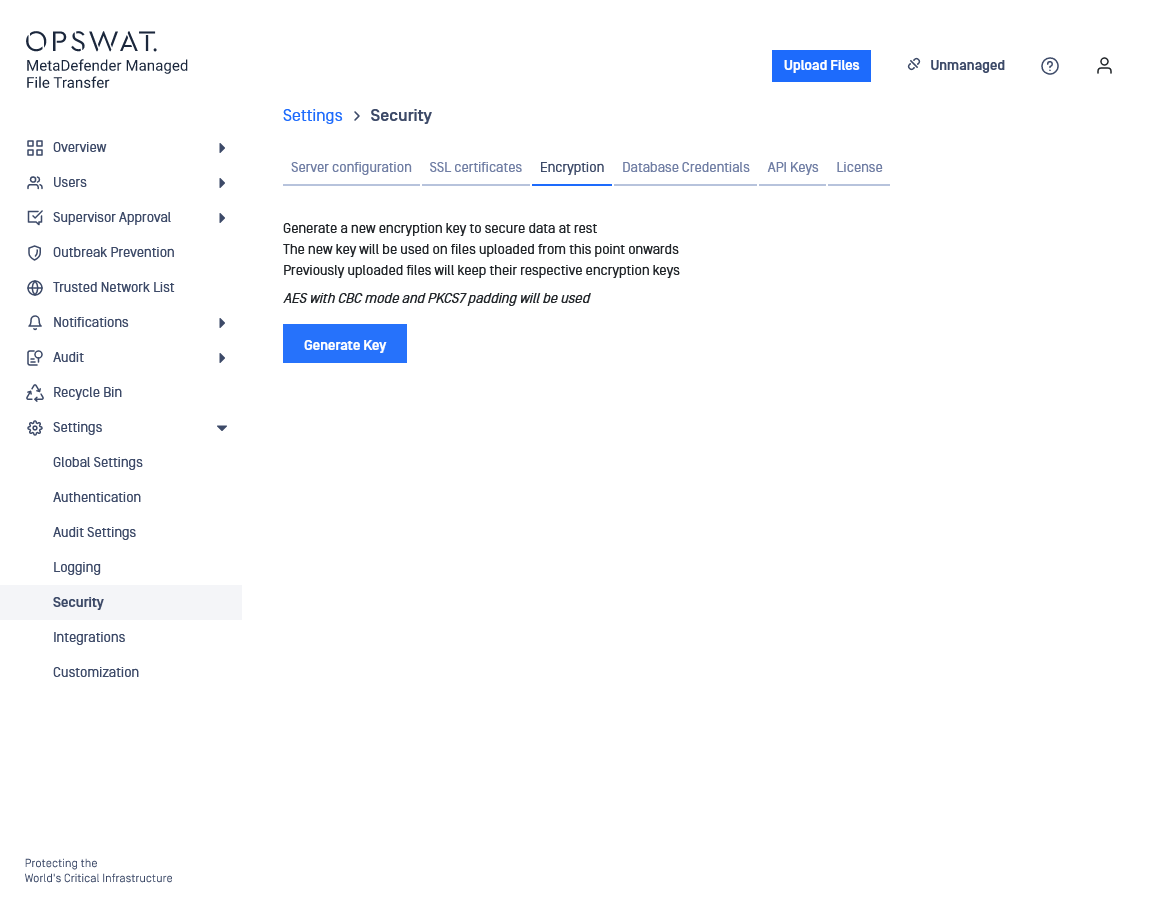
- Click on the Generate Key button.
- A window will appear asking the client to confirm the action.
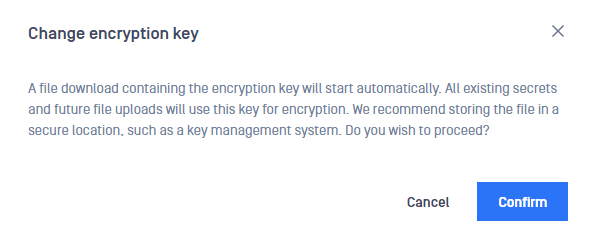
- Selecting Cancel will abort the request and no new key will be generated. Selecting Confirm will lead to step 5.
- The new cryptographic key has been generated. The software will also provide a one time chance to download the generated encryption key in order to store it in a secure place in case it is needed in the future.
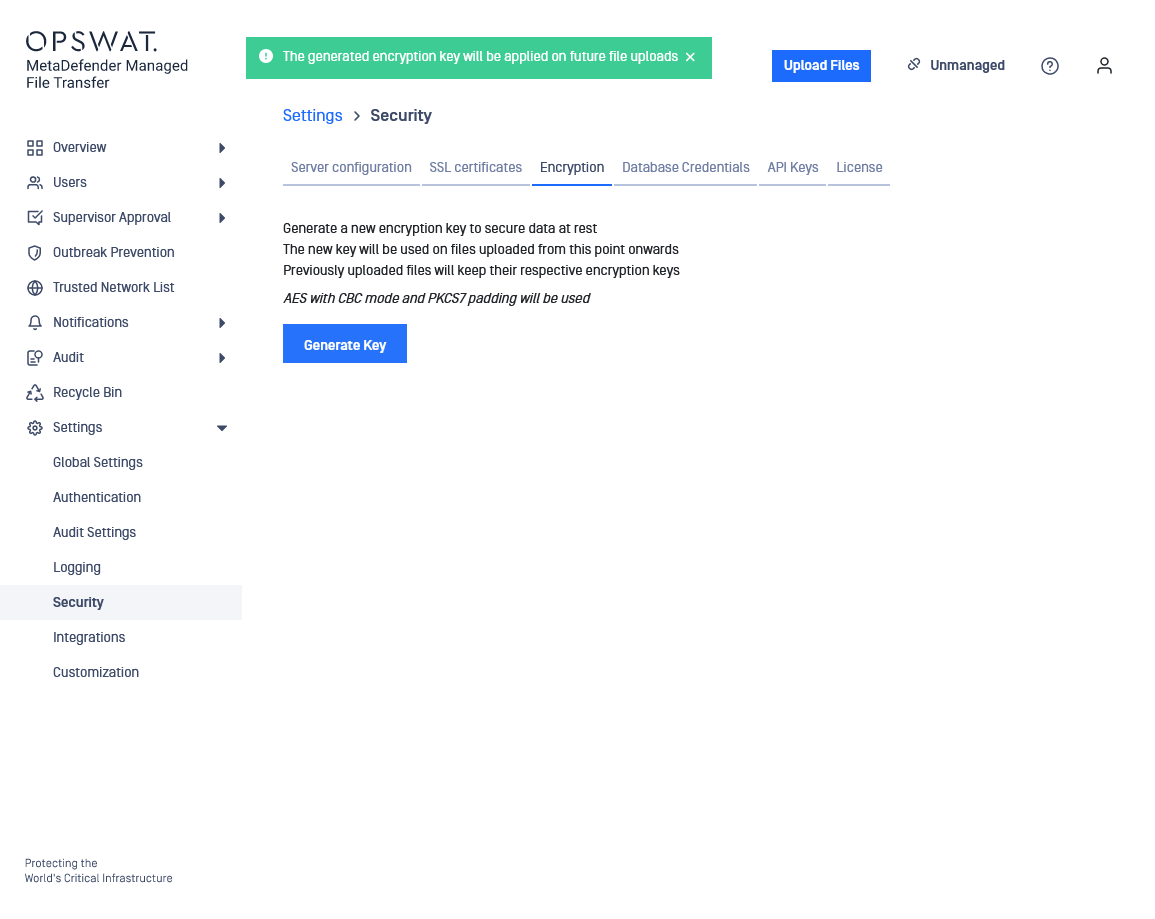
- User agent will prompt the client to store the newly generated key in a file. If the client dismisses this step by mistake, he/she must generate a new encryption key. The previous key will be removed automatically by the system.
The system uses the AES algorithm with CBC mode and PKCS7 padding to generate cryptographic keys. Newly created cryptographic keys are stored in the database as UTF8-encoded hexadecimal characters.
Once a new encryption key is generated, all subsequent file uploads will use the newly created key for encryption. Files that were uploaded prior to the creation of the new key will remain encrypted with the old encryption keys.
It is not possible to manually retire previous encryption keys. The system will automatically remove obsolete keys when all files encrypted with those keys are deleted.
Example
- File1 and File2 are encrypted with key A.
- User generates key B => key A becomes obsolete.
- User uploads File3.
- File3 is encrypted with key B.
- System does a cleanup check and sees that key A is obsolete but it is still used to encrypt files File1 and File2 so the key is not removed.
- User generates key C => key B becomes obsolete like key A.
- User deletes files File1 and File3.
- System does a cleanup check and erases key B (obsolete + no encrypted files). Key A still has one file (File2) encrypted with it so is left alone. Key C has no files encrypted with it but is the active key so it is left alone.

